Whitepaper: Are You Stuck in the Past with Your RIM Program and Software?
by Jasmine Boucher, BMgt, CIP
SAGESSE VOLUME VII WINTER 2022 – AN ARMA CANADA PUBLICATION
Introduction
Many knowledge workers are introduced to records and information management (RIM) as a task that is completed from the side of their desk. Often the reason behind this is due to the lack of an official records management program or dedicated staff members. The exposure to RIM for these professionals can be limited and the value, often is yet to be discovered.
In this paper we will discuss the historic challenges (for some the current challenges) that record and information managers have faced in implementing software, understanding the next steps for progress, and the business case for implementation. After reading this you should be better positioned to understand the core RIM issues that may exist in your organization, be able to perceive a better future, and present options to your business. The goal for this white paper is to help those who are either just starting in RIM or struggling to gain approval for a formal RIM program and software implementation.
Historic Challenges of Records Management
Records and information management is a profession that for some individuals or organizations has seen little-to-no change, not because change did not exist but because they were either unaware of or did not see the value of progression and innovation in processes and technology. For some individuals there was concern that their jobs would be made irrelevant or they would no longer be required. Others did not see financial value in improvement, and yet for some the field just did not interest them or they did not seek to understand it. ISO standard 15489-1: 2016 defines Records Management (RM) as “the field of management responsible for the efficient and systematic control of the creation, receipt, maintenance, use and disposition of records, including the processes for capturing and maintaining evidence of and information about business activities and transactions in the form of records.” (ISO)

Many organizations still do not have any sort of formal records management program. Historically if there was a program it typically focused on the management of paper files. In some organizations the records group would act as a central filing group. They would receive a document, classify it, and then file it. When and if needed that document would then be retrieved and sent to the requestor. At the end of the lifecycle the records management group would take the steps to apply the disposition process (although for many this step may not occur on time or at all). Even with the transition to an electronic age, for many users, that simply meant adding an additional step… printing it off.
If we look back to the definition as stated by ISO Standard 15489-1 there is a lot more to records management than storing, retrieving, and disposing of documents. For many years it seems that some organizations were limited in their understanding of records management and simply ignored the other facets whether it be creation and capture, receipt and maintenance, or processes surrounding the records (in terms of retaining documents).
Many organizations faced challenges with even the smallest portions of records management that they did consider. Some of these challenges include:
- Storage space (physical & electronic)
- Inconsistent classification systems
- Numerous save locations
- Several repositories
- Duplication of documents
- Access rights
- Versioning confusion
For those organizations that are not up to date with RIM standards and legislation today, this is not only a historical problem, but one that is plaguing their current activities. In addition, these challenges have only increased with the massive volumes of information created and collected today plus the multiple formats on which it is stored. For organizations that do not have a formal records management program or system in place, records management is simply the storage of documents and not the processes of creation, collaboration, and approval in many current RIM programs.
Today, people within these organizations are beginning to see the issues, discover the problems, and start to consider and adapt to an innovative way of managing their information assets. Becoming innovative according to the Cambridge Dictionary is “(the use of) a new idea or method”. (Cambridge Dictionary). Innovation is not simply “going digital”, and it is not merely changing process from one medium to another, it is about reinvention, thought leadership, and strength through efficiencies. For those organizations that consider network folders as electronic records and information management, who have no consistent capture methods, no audit history, no classification system or retention schedule that is organizationally expansive, and no methodology for disposition – they have a long way to go before they have what would be considered a formal RIM program in place. Just because you save something electronically does not make it better and it does not make it “managed”. Without processes, procedures, and controls, there is no record integrity. In an uncontrolled electronic workplace users ask questions like the following:
- What is the correct version?
- Who worked on it last?
- Where is it saved?
- Does it need to be saved in two places?
- Was there an emailed copy?
- Why can’t I find the signed version?
- Why was this created?
- Was this saved in the wrong location?
RIM professionals look at other issues such as:
- Does this add business value?
- Do people reference this?
- What is the retention schedule rule(s) that is associated?
- Is this copy signed and official?
- How should I classify this for retention?
- Is it ready for disposition?
- Are there holds that are related?
- Why was this given to me?




While many organizations have identified that RIM is a vital function, there are many that have not yet determined it to be critical or worth investing resources in. For these organizations some see the value internally but cannot get either departmental or management buy-in. Other companies feel that deploying software will be a quick fix and solve any existing RIM problems.
Often these organizations either do not have a formal position (FTE) for these RIM tasks, or the position exists but has no official backing or the organizational strength to make the required changes.
A key factor here is education. Many knowledge workers still see RIM as being the management of physical files, not the complete process that information goes through within the organization. Identifying issues is the first step to being able to move forward and gain traction.




The role of records and information managers today is completely different from the past. Today it has become more complex, misunderstood, and more important than ever before. This is because the role has grown and evolved, requires more departmental input, and has perhaps more importance then in the past with the growing requirements of legislation, freedom of information, and organizational differentiation.
Understanding Your Next Steps
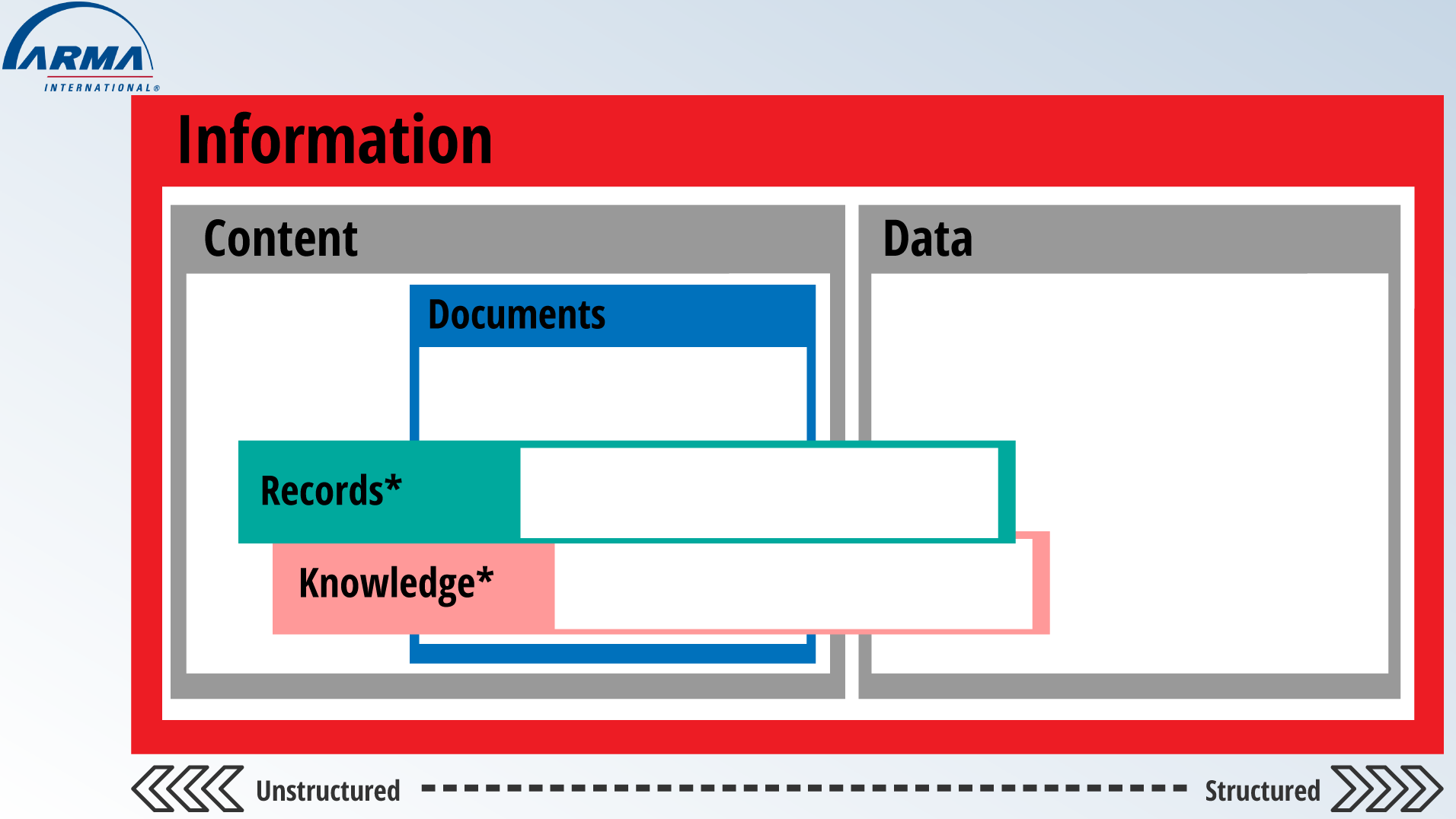
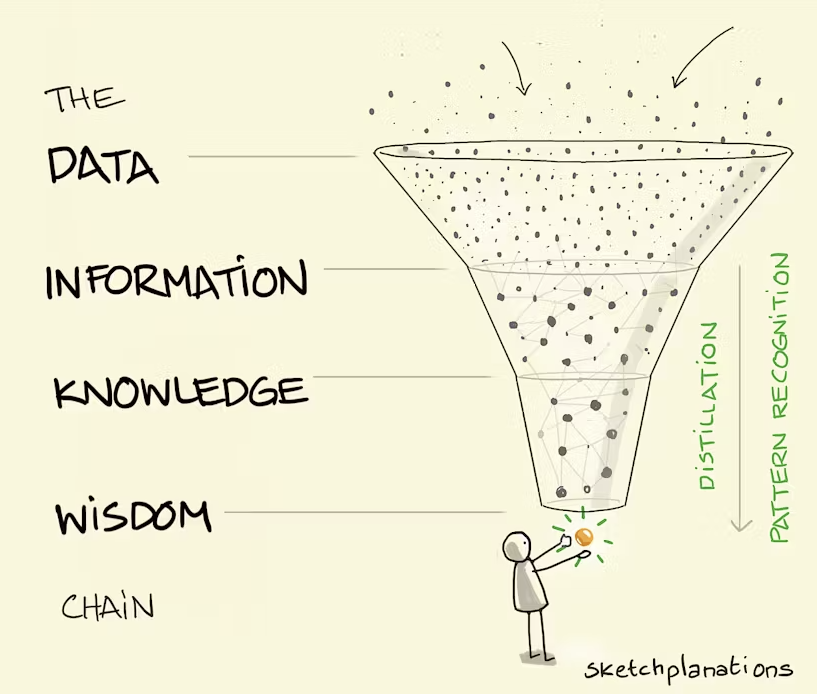
To fully understand records management we need to first define it. We have already defined what records management is, but fundamentally we need to first define what a record is to then determine what records management is required for. There are many definitions of a record, from those in a dictionary defined simply as “to set down in writing” or “to give evidence of” (MerriamWebster) to some that are more specific. ISO has defined a record as “information created, received, and maintained as evidence and as an asset by an organization or person, in pursuit of legal obligations or in the transaction of business.” (ISO). In addition to the many definitions of what a record is there is also terminology that changes between organizations, countries, and simply personal preference. Records are not simply documents; they are so much more than that.
Records include things like images, videos, as well as data and information.




A records and information management program and the software associated is no longer a nice-to-have or add in, it is essential for business operations for many industries. Programs have been created to educate new records managers, associations have seen growth, and subject matter experts have emerged. People are beginning to spend more time interested in the subject, going into more depth, and paying attention to the implications of it. As more non-industry individuals and software providers alike see the value that RIM provides and understand more of the concept, the software that is available improves.
Historically, for many organizations RIM has been seen as a business cost, one that was necessary but did not bring revenue or value to the organization. While there are many ways to quantify the value that it brings these had often been overlooked or found irrelevant until such a time as there was an issue. Today, it can now be seen as an opportunity, something that could provide an organization with a competitive edge. With a better quality of information comes better decisions, and with increased volume and variety comes the necessity to have a better strategy surrounding RIM. One could say that RIM as a field and profession has expanded, but perhaps it’s not an actual expansion of RIM but rather a better understanding of what it is supposed to be by more business professionals and organizations.
Implementing a Software Solution
The ISO definition of records management has four key components: creation, receipt, maintenance, as well as use and disposition with processes surrounding them all. With each of these components we can look for ways to innovate using software tools. For example, if we look at creation, we are now discussing software tools with artificial intelligence and the use of smart templates and forms. In receipt we could discuss electronic creation from birth, automated import, as well as generalized information gathering. Maintenance brings things like automatic reporting, on-demand visualization, and clear audit history. While for retention and disposition we look to automatic classification, programmed calculation of retention periods, consistent approval processes, and clear disposition reports that are automatically generated.
Going forward companies should strive to be able to manage their information of all formats in an efficient and effective manner. If you are looking to improve the manner in which your organization conducts electronic document management, there are several key factors that should be considered.
- Version Control – being able to save and access multiple versions within a single document
- Single Save Location – saving in only one place
- Searchability – ease of finding data regardless of your position
- Accessibility – access to your information from anywhere at any time
- Access Control – keeping data secured
- Audit trail – visibility into the document’s lifecycle
- Customization – people don’t think the same way, thus shouldn’t have to work the same way




A truly beneficial system will enable organizations to benefit from both significant document management capabilities and records management requirements. If you are looking to improve the methods in which you conduct automated and electronic records management these are a few functions that should be considered.
- Manage Retention Rules – these should be managed within the software
- Automation – ensure that processes are automated wherever possible
- Association – based off criteria, the classification and rules should be applied to records
- Calculation – based off classification, the system should calculate the retention period
- Holds – allowing information to be held for a different period based off requirements
- User Responsibility – no one knows the documents better then the users themselves
- Lifecycle Management – management from birth to death within one system
- Disposition – proper procedure for approval and disposition when ready
Even with this in place, education is still critical for RIM professionals, end users, and senior management. Employees can be your greatest strength in RIM; however, they cannot do what they do not know. Records manager often state things like “my users won’t do that” or “I can’t leave them responsible – it will never be done”. My response is always the same, “they will not help you if they do not know how and do not understand the value.” It is amazing what can happen when you educate and then put your trust in your coworkers, they are more capable than you are often led to believe.
Records and information managers are now even more important. They need to have a business perspective and be able to manage the lifecycle of information assets from creation to disposition. They need to have methods for managing different types of records without interruption to the business, and they need to educate the users about the management of information, what it means, and how it can add value to the organization.
The Business Case for Software Implementation
According to the 2020 Industry Watch produced by AIIM “58% of organizations realize they need to move up the information management value chain from simply mitigating risk and cost to creating value.” (AIIM) From this report, over half of the organizations already realize they have an issue that needs to be corrected, they just need to be presented with an option on how to do it. This same report indicates there are three main steps that can be taken to begin digital transformation:
- Identify your organizations current state
- Do a review of the organizational environment
- Document the future state
With this in mind you can move forward with a business case, gain executive buy in, and plan for the future. Be sure that you are not only resolving today’s problems but also looking at the problems of tomorrow, this how is your project is going to be a long-term success.
The benefit of implementing RIM software is clear to those of us are pushing for change. Some of the benefits include:
Time & Efficiency → Financial Gain
Having an RIM software helps to reduce the amount of time that the end users waste looking for information, validating its accuracy, and allows for regular tasks to be completed faster.
Staff Effectiveness → Human Turnover Reduction
By allowing staff to spend more time on the tasks that they are actually hired to complete and are within their skillset they are typically more content with their role. This results in a happier workforce that is retained longer.
Compliance → Risk Mitigation
An RIM software properly implemented can help to mitigate a substantial amount of risk whether it is during regular and external audits or ensuring compliance with internal policies. In addition it makes responding to information requests more efficient and allows staff to become more effective with their time.
Competitive Advantage → Positioning & Value Added
Competition within industries today is extremely fierce, going “digital” is no longer a method of ensuring a successful position within an industry. By having an effective RIM system this can help to ensure that customer service is as efficient as possible, there are no unforeseen delays caused by information requests or audits, and the company as a whole is running smoothly. RIM will not make a business successful, but it can help to provide the necessary competitive edge in comparison to other organizations.
Context → Improved Decision Making
Risk is also mitigated as it provides information to individuals at their fingertips which helps to ensure that informed decisions are made for the organization as a whole. Having the additional context that wouldn’t have been available otherwise within the timeframe required can ensure that the full picture is drawn out before critical decisions are made.
Although it may be clear to some, many of us still need to provide compelling evidence that implementing RIM software adds value to the organization. Creating a business case is the opportunity that you have to tell your company that yes this is required to move forward.




For a successful business case, you should take the following steps:
- Clearly define the issue
- State the benefits & identify the risks
- List the options
- Calculate costs
- Identify the resources required
- Establish a timeline
- Create a draft project plan
- Plan for Change Management
The biggest hurdle that you will likely encounter is securing executive buy-in. This is a large concern for most individuals pushing for the change. Without buy-in you have no project and thus no way to begin moving forward and improving your program through software implementation.
Buy-in is essential and how you position the project is going to be one of the biggest factors to ensure success. Here are some other ways to ensure that your project is given the green light:
- Connect your project to other corporate goals.
- Define how the project will impact other business areas and the impact that it will then have on customers.
- Identify and create a risk mitigation strategy.
- Relate your project to senior management and how it will directly enable their teams.
- Plan for the system rollout, change management initiatives, and financial implications.
In summary, RIM as a profession has evolved significantly since the 1970s as a result of electronic records replacing paper. However, there is still a long road ahead for it to be in the forefront of all people’s minds. Individuals in positions of authority are beginning to understand the implications of poorly managed records and information and the value that could be gained through proper RIM. It is more important than ever that people are educated in information management in order to help them truly understand the meaning and value that it brings. Finally, ensuring that you can move forward internally and adopt innovation with full support of the executive team is vital to the success of any project.
Corporate Overview & Biography




Indixio specializes in IT solution services for intelligent information management through two main channels, enterprise content management (M-Files) and geospatial information management (custom built solutions). Indixio was established in the year 2000 with the primary clients being in government, education, transportation, and utilities. Indixio is staffed with a highly skilled team from sales and support through development, looking to effectively deploy and implement desktop, web, and mobile solutions that are fully integrated for business.
As a premier and authorized service provider, as well as a Certified Delivery Partner of M-Files Indixio continually pushes the envelop of what is possible with custom modules, add-ins, and integrations that add significant business value. After discovering a gap in the industry Indixio developed a custom module that is additional to M-Files for Records Management, this module allows leveraging the power of M-Files while being able to efficiently apply records management requirements. From managing retention rules, automating the application of those rules, administering holds, and determining the retention period of documents this module does it all.
The Indixio head office is located near Montreal with a satellite office in Alberta. Indixio serves customers all across Canada and the United States. With over twenty years of experience providing consulting services and IT solutions Indixio has helped organizations better manage their information and successfully complete and implement their projects. Indixio has one simple vision: simply your work by making information more accessible than ever before. At Indixio, we believe in outstanding customer service and exceptional technical support.
About the Author




Jasmine Boucher BMgt, CIP
Technical Account Manager
Indixio Inc.
jboucher @ indixio.com
Jasmine draws the line between customer needs and system requirements. With a belief that success is a requirement not a possibility Jasmine truly looks out for the best interests of all around her. As a past records management coordinator for a municipality she leverages her experience to ensure that customers are on route to success not only immediately but also in the long term.
Holding a degree from Athabasca University in Management and a CIP Certification from AIIM, Jasmine has not only the business experience but also the education and guiding principles to ensure for successful deployments of RIM systems.
Jasmine currently works with organizations across Canada to improve their document and records management capabilities through the deployment of M-Files. Ensuring that both the needs of the end users and the RIM professionals are met.