Sagesse: 2019 Edition Volume IV
Winter 2019 Sagesse Publication
- 2019 Introduction to Sagesse.
- Ethical Concerns in the Provision of eHealth Services. By Meagan Collins, Nicole Doro, Ben Robinson, & Ariel Stables-Kennedy. Recipients of $1,000 in the 2018 ARMA Canada Essay Contest.
- IT & Modern Public Service: How to Avoid IT Project Failure and Promote Success. By Scarlett Kelly. Recipient of $600 in the 2018 ARMA Canada Essay Contest.
- Defending Traditional Rights in the Digital Age: Ktunaxa Nation Case Study. by Michelle Barroca, BA, MAS.
- Politique relative aux messages électroniques et son adoption. Par Barb Bellamy, CRM et Anne Rathbone, CRM.
- Email Policy and Adoption. by Barb Bellamy, CRM & Anne Rathbone, CRM.
- Thank you to John Bolton! by Alexandra Bradley, CRM, FAI
- Are we There Yet? Introduction to the SharePoint & Collabware Implementation at the First Nations Summit. by Sandra Dunkin, CRM, IGP & Sam Hoff
- Quand est-ce qu’on arrive? Introduction à l’implémentation de SharePoint & Collabware au First Nations Summit Society. Par Sandra Dunkin, CRM, IGP & Sam Hoff
- A Record of Service: The First Canadian Conference on Records Management “A Giant Success.” by Sue Rock, CRM
Biographies
Michelle Barroca (BA, MAS) is an independent recorded information management consultant from the Kootenay region of BC. Michelle graduated from UBC’s School of Library, Archival, and Information Studies with a Master of Archival Studies degree in 2000. Shortly after university, she was hired as the City of Burnaby’s first records manager and archivist, and later worked at the City of Kelowna as the Records and Information Coordinator. For nearly a decade, Michelle has operated FY Information Management Consulting and provides services to various local governments and First Nations organizations, including the Ktunaxa Nation Council.
Barb Bellamy, CRM,has over 30 years of experience in Records and Information Management for the Utility and Energy industries. She currently specializes in Information Management Consulting and Acquisition and Divestment work within Suncor. Barbara is a Certified Records Manager and holds a bachelor’s degree in Business Administration.
Alexandra (Sandie) Bradley, CRM, FAI has been a records and information manager for over 40 years, and a member of ARMA for 35 years. Through her chapter, regional and international roles within ARMA, she is a mentor and teacher, researcher, writer and advocate for our profession. She is a Certified Records Manager and was made a Fellow of ARMA International (Number 47) in 2012. She is a member of the Vancouver Chapter, is currently a member of the Sagesse Editorial Board and also the Content Editorial Board for ARMA International.
Megan Collins holds her MA and Honours BA from Brock University in Political Science and is presently a MLIS student at Western University. She is currently completing a co-op posting working as an information management officer with the Federal Government. Her research interests include information policy, knowledge management, Big Data, privacy and surveillance.
Nicole Doro holds her MA and Honours BA in English and Critical Theory from McMaster University, and is presently a MLIS student at Western University. She is currently completing an Instructional and Research co-op at McMaster University. Her research interests include open access, institutional repositories, as well as privacy and surveillance.
Sandra Dunkin (MLIS, CRM, IGP) is the Records & Information Management Coordinator at the First Nations Summit (FNS) where she also has responsibility for IT. She is the project manager for the SharePoint implementation at the FNS and is also currently the out-going Chair of the Information Governance Advisory Committee for the First Nations Public Service Secretariat.
Sam Hoff is a Senior Consultant at Gravity Union. He is passionate about providing user experience focused solutions to meet document and records management needs. Having backgrounds in both the technical and human sides of technology and business, he has been focused on Enterprise Content Management and Records Management solutions based on SharePoint for the past seven years.
Scarlett Kelly holds both Master of Public Administration (MPA) and Master of Library and Information Studies (MLIS). Her research focuses on IT project management, strategic planning, information/data policy, and change management. Currently a Research Specialist at Canada Revenue Agency, Scarlett is gaining valuable experience in legal and business research.
Anne Rathbone has 22 years experience in the public sector establishing, implementing and maintaining records and information management programs. She earned her Certified Records Manager (CRM) designation in 2010. Currently, Anne is the Records Management Coordinator for the Sunshine Coast Regional District.
Ben Robinson is a poet, musician and librarian. In October 2017, Bird, Buried Press published his first poetry chapbook “Mayami.” In 2018 he was named the Emerging Artist in the Writing category at the Hamilton Arts Awards. He is currently preparing an article for publication on policing and security in the public library.
Sue Rock, CRM is a records management consultant with a diverse workload including records management assessments, records audits, classification systems and retention schedules. She ghost writes policies, procedures, memos, letters, debates, rebuttals, opinions, guidelines, action checklists and presentations. Sue’s educational background comprises a Bachelor of Arts, Université d’Ottawa, and a Professional Specialization Certificate in International Intellectual Property Law co-sponsored by both the University of Victoria, Canada and St. Peter’s College Oxford, England. She is a Past President, ARMA
Calgary Chapter, and a Chapter Member of the Year award winner. Her publications include “A Record of Service: Bob Morin, CRM” ARMA Canada Sagesse, “RIM’s Role in the Technology Lifecycle”, ARMA International, “Managing Privacy Conflicts Across Borders – Vendor Awareness and Action”, Security Shredding & Storage News, and team lead for ARMA International Guideline “Records Management for Information Technology Professionals.” Sue is owner of The Rockfiles Inc. and an operating partner of Trepanier Rock ™, with specific focus on ensuring records management principles are embedded
into information management technology solutions.
Ariel Stables-Kennedy holds a BSc in Kinesiology from the University of Waterloo and is currently completing her MLIS at Western University in London, Ontario. Her research interests include instructional design, the information literacy learning needs of STEM students, and information ethics.
Sagesse: Journal of Canadian Records and Information Management an ARMA Canada Publication Winter, 2019 Volume IV, Issue I
Introduction
Welcome to ARMA Canada’s fourth issue of Sagesse: Journal of Canadian Records and Information Management, an ARMA Canada publication.
Sagesse Editorial Team
The Sagesse Editorial Board would like to take this opportunity to gratefully acknowledge and thank John Bolton who was a founding member of Sagesse: Journal of Canadian Records and Information Management. John resigned mid 2018 after making many invaluable contributions to this publication. His impact on Sagesse and the RIM and IG community are significant. Sandie Bradley has captured some of his brilliance in an article titled “Thank you to John Bolton!” in this issue.
The Editorial Board would like to welcome Sandra Dunkin, MLIS, CRM, IGP to the editorial team. Sandra brings a wealth of ARMA and workplace experience, from her work on the ARMA Vancouver Chapter, the ARMA Canada team as Program Director, to her work at First Nations Summit. Sandra has already demonstrated her commitment and dedication to the Sagesse team performance. She also has an article in this edition – see “Are We There Yet?”
2018 University Contest
There’s a new addition to Sagesse’s 2019 edition and we are excited to share that in 2018, ARMA Canada and the Sagesse Editorial Board held an essay contest for graduate students enrolled in graduate information management programs in a number of Canadian universities. The article that best met the theme, Canadian Issues for Information Management, received $1,000 while the runner up received $600.
We are honoured to announce that the team of: Meagan Collins, Nicole Doro, Ben Robinson and Ariel Stables-Kennedy from the University of Western Ontario were the $1,000 recipients with their article “Privacy and Ethical Concerns in the Provision of eHealth Services.” Their article explores an ethical analysis of data collection policies of Canadian live eHealth service providers and comments to what extent they conform to the Canadian Medical Association’s Code of Ethics.
Scarlett Kelly, from Dalhousie University, was the $600 recipient with her article “Information Technology and Modern Public Service: How to Avoid IT Project Failure and Promote Success.” Scarlett looks at a global scan that indicates that IT projects may have as high as an 85% failure rate discussing it from the point of view of the people involved, IT processes and the product to deliver to users.
Congratulations to our students!
To our readers, prepare to be captivated with the content, writing and research in these articles as well as the others in this edition.
2019 Sagesse Articles
Continuing with Sagesse’s tradition of providing thought provoking content, this 2019 issue features the following articles:
- Michelle Barroca, BA, MAS, provides a case study in her article “Defending Traditional Rights in the Digital Age: Ktunaxa Nation Case Study,” of Ktunaxa Nation’s experience with using business and cultural records to legally defend traditional rights in opposing permanent development in a culturally significant and ecologically sensitive area in British Columbia’s southeast quadrant.
- Barb Bellamy, CRM and Anne Rathbone, CRM, discuss the challenges an organization faces in establishing an email policy and the compliance issues the employees need to embrace in “Email Policy and Adoption.” They provide an excellent array of tools to assist this process by using catch phrases, branding and gamification. This paper has been translated into French.
- Alexandra (Sandie) Bradley, CRM, FAI, features an article that pays tribute to and provides the biography of John Bolton, CRM. John was a founding member of Sagesse: Journal of Canadian Records and Information Management, and his wisdom was a guiding light while a member of this team. In “Thank you to John Bolton,” she describes his RIM journey and the many accomplishments he achieved in his
- “Are We There Yet?” an article by Sandra Dunkin, MLIS, CRM, IGP and Sam Hoff, ECM Consultant, explores a SharePoint implementation project conducted at the First Nations Summit while underscoring the lessons learned, missteps, failures and eventual successes. Also addressed are the challenges of change management, user training and adoption and various upgrades as users engage with SharePoint. This paper has also been translated into
- Who doesn’t enjoy an ARMA Canada Conference? Sue Rock’s, CRM, article “A Record of Service: The First Canadian Conference on Records Management “A Giant Success,” looks back at the very first ARMA Canada conference, held in beautiful Banff, Alberta in February 1980. Discover how some of ARMA Canada traditions were developed and have evolved over the years.
Please note the disclaimer at the end of this Introduction stating the opinions expressed by the authors in this publication are not the opinions of ARMA Canada or the editorial committee. We are interested in hearing whether you agree or not with this content or have other thoughts or recommendations about the publication. Please share and forward to: sagesse@armacanada.org
If you are interested in providing an article for Sagesse or wish to obtain more information on writing for Sagesse, visit the ARMA Canada’s website – www.armacanada.org – see Sagesse.
Enjoy!
ARMA Canada’s Sagesse’s Editorial Review Committee:
Christine Ardern, CRM, FAI, IGP; Alexandra (Sandie) Bradley, CRM, FAI; Sandra Dunkin, MLIS, CRM, IGP; Stuart Rennie, JD, MLIS, BA (Hons.); Uta Fox, CRM, FAI, Director of Canadian Content.
Disclaimer
The contents of material published on the ARMA Canada website are for general information purposes only and are not intended to provide legal advice or opinion of any kind. The contents of this publication should not be relied upon. The contents of this publication should not be seen as a substitute for obtaining competent legal counsel or advice or other professional advice. If legal advice or counsel or other professional advice is required, the services of a competent professional person should be sought.
While ARMA Canada has made reasonable efforts to ensure that the contents of this publication are accurate, ARMA Canada does not warrant or guarantee the accuracy, currency or completeness of the contents of this publication. Opinions of authors of material published on the ARMA Canada website are not an endorsement by ARMA Canada or ARMA International and do not necessarily reflect the opinion or policy of ARMA Canada or ARMA International.
ARMA Canada expressly disclaims all representations, warranties, conditions and endorsements. In no event shall ARMA Canada, its directors, agents, consultants or employees be liable for any loss, damages or costs whatsoever, including (without limiting the generality of the foregoing) any direct, indirect, punitive, special, exemplary or consequential damages arising from, or in connection to, any use of any of the contents of this publication.
Material published on the ARMA Canada website may contain links to other websites. These links to other websites are not under the control of ARMA Canada and are merely provided solely for the convenience of users. ARMA Canada assumes no responsibility or guarantee for the accuracy or legality of material published on these other websites. ARMA Canada does not endorse these other websites or the material published there.
Privacy and Ethical Concerns in the Provision of eHealth Services
by Meagan Collins, Nicole Doro, Ben Robinson, and Ariel Stables-Kennedy
Introduction
The development of the internet and the advancement of digital technologies have resulted in life-saving access to information, especially within the medical industry. Whereas, before the introduction of these technologies, individuals would need to visit a doctor’s office for their health-related questions, they can now consult resources themselves on the internet. A study showed that 83% of internet users around the world have searched for health information1. In 2012, the number of Canadians who regularly used the internet to search for medical and health- related information at home was over 65%, making it the sixth most common use of the internet in Canada2. Along with increased access to medical information, Information Communication Technology (ICT) is also an integral tool in the field of health services known throughout Canada as eHealth.
eHealth is defined as blending the internet, telecommunications, and information technology with medical services provision3. According to the Government of Canada, the incorporation of eHealth into the mainstream medical treatment framework has been a significant priority for Canada over the past 20 years4. Since 2010, Canada has budgeted $20 billion towards the creation of a national health infostructure allowing for advances in several aspects of healthcare service models5. Integrated technologies now allow patients to receive medical care through telemedicine applications, a major benefit for those who live in rural areas or who are homebound. It also provides a more convenient service model by allowing patients affected by rare medical disorders to receive service from distant specialists6. The recognized benefits of this system have resulted in 53% of Canadian primary-care physicians using some form of electric medical reporting technologies, up from 14% in 20007. While the improvements to medical services were widely accepted as significantly beneficial, eHealth adoption also allowed for many potential advances in Health Informatics (HI).
HI “involves the application of information technology to facilitate the creation and use of health-related data, information and knowledge8.” As well, HI serves two functions in the eHealth model. First, it is designed to improve the experience of clinical practitioners through information and knowledge management. Second, it has also helped to improve the accessibility of health information for caregivers, patients and the public9. This emphasis on HI and the resulting data collection within these medical services has led to an increase in concerns surrounding the ethics of data collection in this particularly sensitive field10.
This study aims to add to the international discussion by performing an ethical analysis of the data collection policies of Canadian live eHealth service providers and to what extent they conform to the Canadian Medical Association’s (CMA) Code of Ethics. In addressing this question, this paper will begin with a brief overview of related work in the field of data privacy pertaining to medical information to situate this study within the overall discourse on the topic.
Next, the reasoning for using the CMA’s Code of Ethics as an ethical framework and the general methodological approach will be further explained. After exploring the results of the examination of the Privacy Policies and Terms of Use agreements of several eHealth service providers, the discussion will focus on the efficacy of current policy provisions and potential future research areas within this topic.
Literature review
Research analyzing the ethics of the eHealth industry began to emerge in the early 2000s.
The early literature was primarily theoretical, mostly addressing the possible implications of eHealth services and technologies as an emerging trend within the field. The progression of work in this area has grown to include more practical analyses, in addition to the theoretical studies on eHealth, as concerns about privacy, data collection, equality and quality of medical care have become more prominent. Prior studies that address data collection can be organized into four main categories. This paper will provide some background on the literature that focused on:
- the importance of protecting privacy and confidentiality in eHealth services as an ethical imperative for the industry;
- the need to have ethical standards and frameworks in place to regulate the collection and use of data in eHealth services;
- how the industry defines “health data” and how this impacts ethical data collection and use, and
- the integration of eHealth data and social media
Ethical Imperative of Privacy and Consent
Early research looked at the integration of ICT in the health field and discussed the potential implications of these technologies for patient privacy and confidentiality. Dyer framed the need for privacy as a tenet of the ethical code of the American Medical Association and discussed the emergence of eHealth technology as a threat to the patient-physician bond, which shifted to a physician-customer model11. Following this concern, other scholars focused on the need for privacy in order to ensure patients trust and understand the health system that their physicians operate within in order to feel safe providing sensitive but accurate information12 13 14 15. Chaet et al. addressed a further complication of this issue in their discussion of the potential breach of patient privacy through the use of third-party platforms stating, “websites that offer health information may not actually be as anonymous as visitors think; they may leak information to third parties through code on a website or implanted on patients’ computers16.”
Research on this topic has often been split between a focus on the need for collected information to be de-identified for the purposes of protecting individual anonymity while also emphasizing the need for flexibility in data collection to allow for advanced analysis of sensitive information for the benefit of improving the service delivery of our universal healthcare system17. Other studies look at embedding privacy in the very design of these online platforms to ensure protection of patient privacy but also to manage the custody of data and consent18.
Need for Ethical Provisions and Regulation
Studies that focused specifically on the ethical imperative of privacy within the medical services field are often related to other studies that speak to the need for regulations or ethical codes to be embedded within the eHealth framework. Wadhwa and Wright specifically address the issue that the ethics of the medical industry have always been evolving, and the move towards an eHealth model is just another example of a period when society needs to update its ethical understandings of the practice for the digital age19. Soenens was among the earlier voices on this issue stating the importance of ensuring the tenets of the Hippocratic Oath remains ingrained in eHealth services20. Other literature in this area looks beyond system design to examine physicians themselves as important privacy actors. Derse and Miller argue that physicians should only use eHealth systems that are transparent about their privacy policies and meet acceptable ethical standards of patient confidentiality21.
Another branch of research looks at the role state regulators play in the eHealth system.
Studies conducted on this topic have sought to examine how state privacy regulations in the European Union (EU) and the United States (US) have been characterized as barriers to the continued success and advances of eHealth systems22. They have also addressed the lack of regulation and the power of third-party organizations to control the management of personal health data23. Additional studies have explored the ownership of patient data in third-party platforms and the effect this has on whether medical data can be used for informed improvements to the medical care system for the benefit of the overall public good, especially in countries with publicly funded healthcare like Canada24.
Defining Health Data and Securitization
Along with analyzing medical data regulation, other studies addressed the secondary issue of how to understand and define personal health data from a regulatory perspective.
Kleinpeter highlights how recent digital devices enable the constant collection of personalized health data at an unprecedented level25. This type of collection makes it difficult for legislators to determine which types of data to regulate and how to regulate them. It would be important to make the distinction between data collected during an individual patient’s diagnosis versus anonymized data for the purpose of medical research. There may even be some types of patient data that should be legally prohibited to collect altogether.
Some critics have noted that the lack of clarity regarding ownership of this data makes it especially difficult to regulate ethically. For example, Lee noted that, “Unlike victims of breaches of financial data, to whom reparations can be made, victims of breaches of private health data cannot be ‘made whole’; information cannot be ‘taken back.’26”
eHealth, Social Media, and Medical Advertising
The growth of social media platforms has become a more common theme within eHealth data discourse. As more social media components are added to eHealth services and patients are encouraged to engage, individuals are sharing their health stories and providing their medical data to commercial platforms more regularly. Even when these platforms are managed by public healthcare systems, this increased sharing of health information makes the privacy issues much more complicated. While taking a largely positive view of social media sites and eHealth services, Winkelstein also echoes some of this concern27. Other studies have specifically analyzed third-party platforms and discussed how the ethical gaps in their processes should be addressed28. The literature has also addressed situations where health data has been released with informed consent but is later provided to a third-party organization which combines that data with non-health-related data in order to be able to do targeted advertising based on a patient’s particular health conditions29.
This extensive body of work, along with the structured literature review performed by Khoja, Durrani and Nayani shows that ethical and legal issues within the field of eHealth studies are, and will likely continue to be a significant research area30. Up until now, this research has tended to focus on the United States, the United Kingdom and Europe and has been largely theoretical in nature, analyzing and critiquing the system as a whole rather than undertaking in- depth analyses of individual services. As such, this study provides a unique perspective on the ethical discourses in eHealth by focusing specifically on the data collection and terms of use practices of major eHealth services within the Canadian healthcare system.
Theoretical Framework
The CMA Code of Ethics will serve as the ethical framework for this investigation of the chosen eHealth services. Specifically, the “Privacy and Confidentiality” codes from the CMA’s Code of Ethics were used to measure each platform on a pass-fail basis. This Code of Ethics was chosen as the framework because of its geographic and political relevance, as it “constitutes a compilation of provisions that can provide a common ethical framework for Canadian physicians31.” As physicians operating within the Canadian healthcare system are required to follow this code, it will be used as a framework to evaluate the recent evolution of this service model. As the CMA Code of Ethics was last updated in 2004 and deemed “still relevant” after a review in March of 2018, this study will include recommendations for future adaptation and revision32.
Methods
Since the objective of this research is to evaluate eHealth services and their publicly available privacy policies, the researchers located the platforms through popular online search methods. All searches were performed through Google, as it is the most popular search engine among Canadians and as such, likely where users will turn for their online health information33. The search queries used to locate the eHealth platforms were “Canada online health chat,” “Canada telehealth services,” “Canada live health chat,” “virtual doctor Canada,” “online doctor Canada free,” and relevant hits that appeared within the first one to three pages were selected.
Only services that facilitated conversations (including chats or teleconferences) between trained healthcare providers, whether that was a doctor, Registered Nurse, or Registered Nurse Practitioner, were considered. Mental health helplines that featured live chats were also considered, as these platforms had similar capabilities for live chat and thus, have potential implications for the privacy of users’ personal health data. Ultimately, 18 platforms were chosen for consideration based on this search criteria: GOeVISIT, National Eating Disorder Information Centre (NEDIC), sexualhealthontario, Dialogue, Ontario Telemedicine Network (OTN), Livecare, Viva Care, Maple, Equinoxe LifeCare (EQ Care), YourDoctors.Online, Medicuro, Mental Health Helpline, youthspace.ca, Toronto Distress Centre Online Chat and Text Service (ONTX), Medeo, MDKonsult, Akira, and Ask The Doctor.
The chosen inclusion criteria allowed for both mobile applications and websites (which may license to third-party vendors) to be considered. Although technically the term “telehealth” encompasses both telephone calls as well as digital health services, telephone health services (i.e. voice calls) were excluded to narrow the scope of the project. Platforms that offered services such as video chats were included provided these services were not the sole eHealth service available on that platform. All chosen platforms had a live, online communication exchange component, whether via a pre-arranged appointment for a text conversation, a videoconference (ex. Maple) or by waiting in a queue for the next available professional (ex. youthspace.ca, Mental Health Helpline).
First, each service was examined to determine its funding model (private, public, or non- profit), if advertisements were used, if the patient was charged a fee for the service, or if the services were funded through the existing provincial healthcare system. Each service’s social media presence was also examined to determine whether they promoted their social media channels to users, required their users’ social media information or provided the option to sign-in to the service using existing social media accounts. Next, the accessibility of each platform’s privacy information was evaluated. The researchers took note of the presence (or lack thereof) of the Privacy Policy on the home page, and if the Privacy Policy or Terms of Use discussed how data were collected and used. The reading level of the Privacy Policy and the Terms of Use were also evaluated using the Flesch-Kincaid readability assessment embedded in Microsoft Word.
This reading test approximates a grade level required to understand a document, based on average sentence length and the average number of syllables per word. For example, a score of 8.0 implies that someone in 8th grade could understand the document34. Finally, each platform’s Privacy Policy was compared to each of the CMA’s “Privacy and Confidentiality” Codes to see if it was compliant35.
A potential source of error for this study is that the authors do not have authoritative documents for these organizations and services. For example, some services did not appear to have privacy documents, user agreements, or explicit methods of funding after extensive searching by the researchers, however, this does not mean that those documents do not exist; they are simply inaccessible to the public. The fact that the authors of this study who have significant training in digital literacy and researching suggests that these documents are also likely inaccessible to the general population using these services.
Results
Business Model
As demonstrated in Figure 1, the majority of eHealth services were privately owned and operated (12). Beyond this, the other funding models included ownership by a non-profit organization receiving government funding (4) and publicly funded services (2).
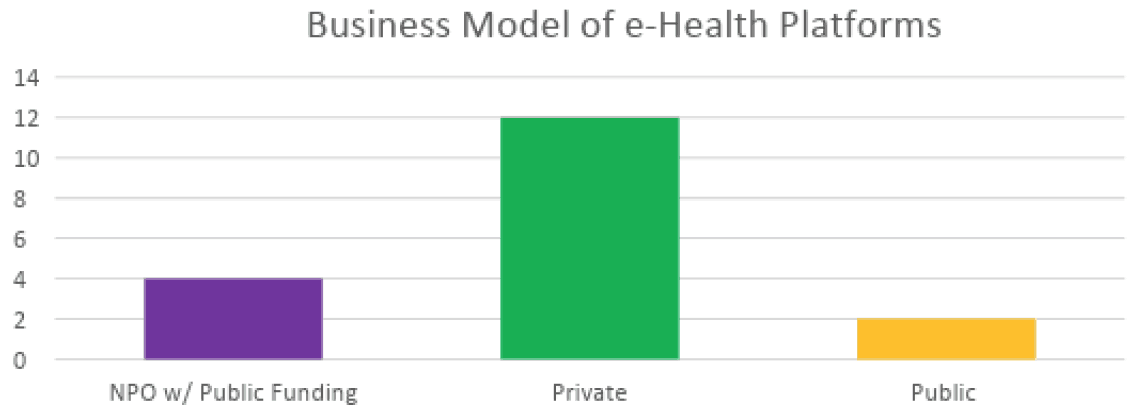
Figure 1: Business models of the surveyed eHealth services
All of the publicly funded and non-profit eHealth services examined for this study were free to Canadian users. While some private eHealth services were free, most charged a fee for access to their product. Two models emerged: a pay-per-visit model and a membership-based model. The mean cost of accessing a pay-per-visit eHealth service was $42.89 Canadian dollars (CAD) while the median cost was $45 CAD. Alternatively, subscription-based models ranged from $15 CAD to $150 CAD per-month per-member.
Only two services, Livecare and Viva Care, both privately owned and operated, utilized advertisements.
User Data Collection
Private eHealth services collected both active and passive data more frequently than public or non-profit eHealth services.
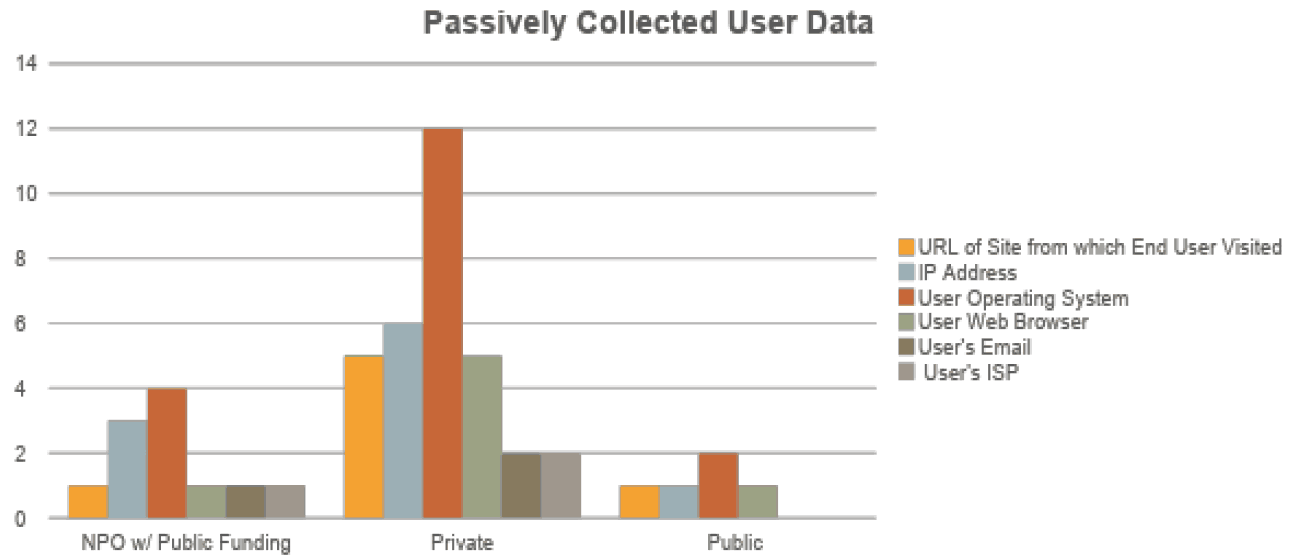



Figure 4: Frequency measurement of passively collected user data, grouped by business model.
Actively Collected User Data
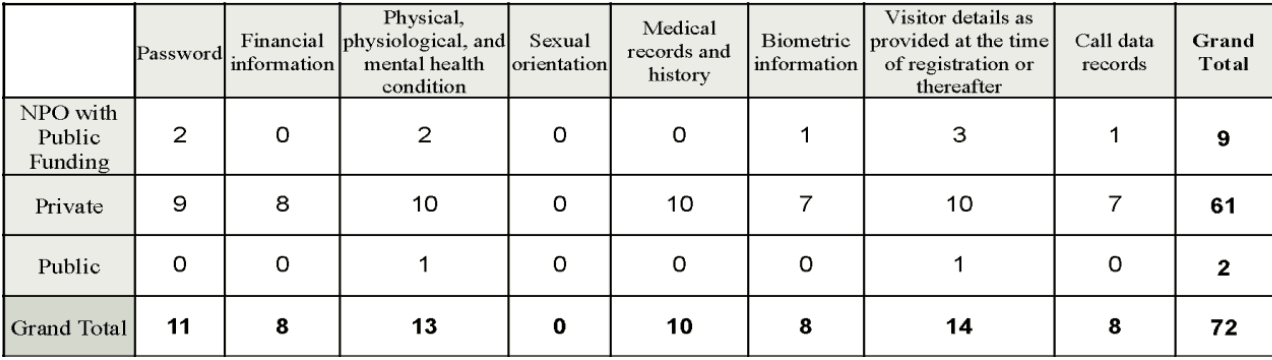



Figure 5: Frequency measurement of actively collected user data, grouped by business model.
Social Media
Only one service (YourDoctors.Online) allowed for sign-in through a third-party social media application. While the use of social media by these eHealth services could simply be viewed as a marketing or communication tactic, having users connect their social media accounts with these services may also present a further opportunity for data collection. One service directly requested social media information from users (GOeVisit) and two had an app available for download through a Google Play or an Apple account (Livecare and Maple) which would then be connected to other social media information (i.e. Google +).
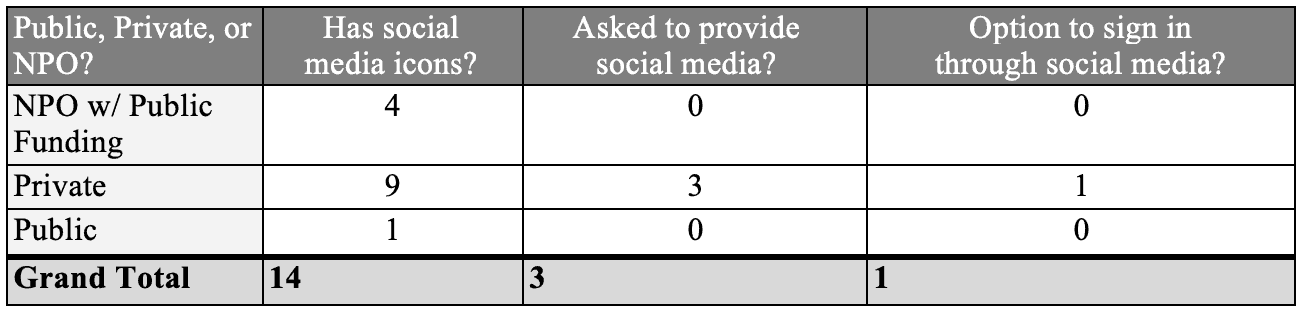



Figure 6: Depth of social media engagement that services presented, grouped based on business model.
Privacy Policy, Terms of Use, and the Flesch-Kincaid Reading Level Test
Seventy-two percent of the services had privacy policies that were accessible from the home page. Sexualhealthontario, MDKonsult, and Ask The Doctors had neither a Privacy Policy nor a Terms of Use agreement.
The measures of central tendency for the Privacy Policies and Terms of Use show that both provisions tended to be similarly difficult to read and were often written above a high school reading level. Privacy policy scores and measures of central tendencies were calculated based on the 14 services that had privacy policies. Sexualhealthontario, youthspace.ca, MDKonsult, and Ask The Doctor did not have privacy policies and thus were factored out.
Terms of Use scores and measures of central tendencies were calculated based on the 13 platforms that had Terms of Use agreements. Sexualhealthontario, Medicuro, Mental Health Helpline, MDKonsult, and Ask The Doctor did not have Terms of Use agreements.
One service, GOeVISIT, had some problematic data policies, such as the note that the service uses both FaceTime and Skype which are not bound by the Health Insurance Portability and Accountability Act (HIPAA) in the United States and that their data were stored by Rogers. This service did, however, make note that they employ a Privacy Officer. Whether or not the Privacy Officer offsets the possibility for data leakage is a point for ethical consideration.
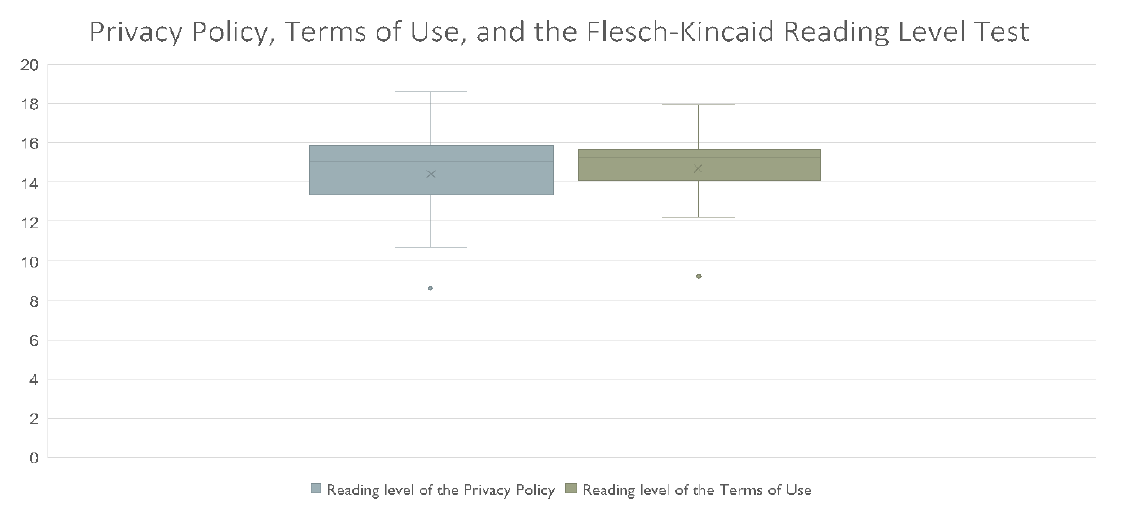



Privacy Policy: Range = 8.6-18.6, median =15.1 and mean = 14.4; Terms of Use: range = 9.2- 17.9, median=14.7 and mean =15.4.
Canadian Medical Association Code of Ethics
In order to analyze compliance to the CMA’s Privacy Policy, the authors analyzed each service’s Privacy Policy and Terms of Use agreement to locate the following ethical code provisions (depicted in Figure 8): protection of personal health information, awareness of patient rights, avoidance of public discussion, disclosure of information to third parties only with consent, action to take steps to inform patients about responsibility to third parties, and providing patients with a copy of medical records upon request. Each item was coded as “one” if the provision was satisfied by the service or coded as “zero” if the provision was not met for any reason (either the item was not addressed in the Privacy Policy or Terms of Use Agreement or the documents were not accessible).
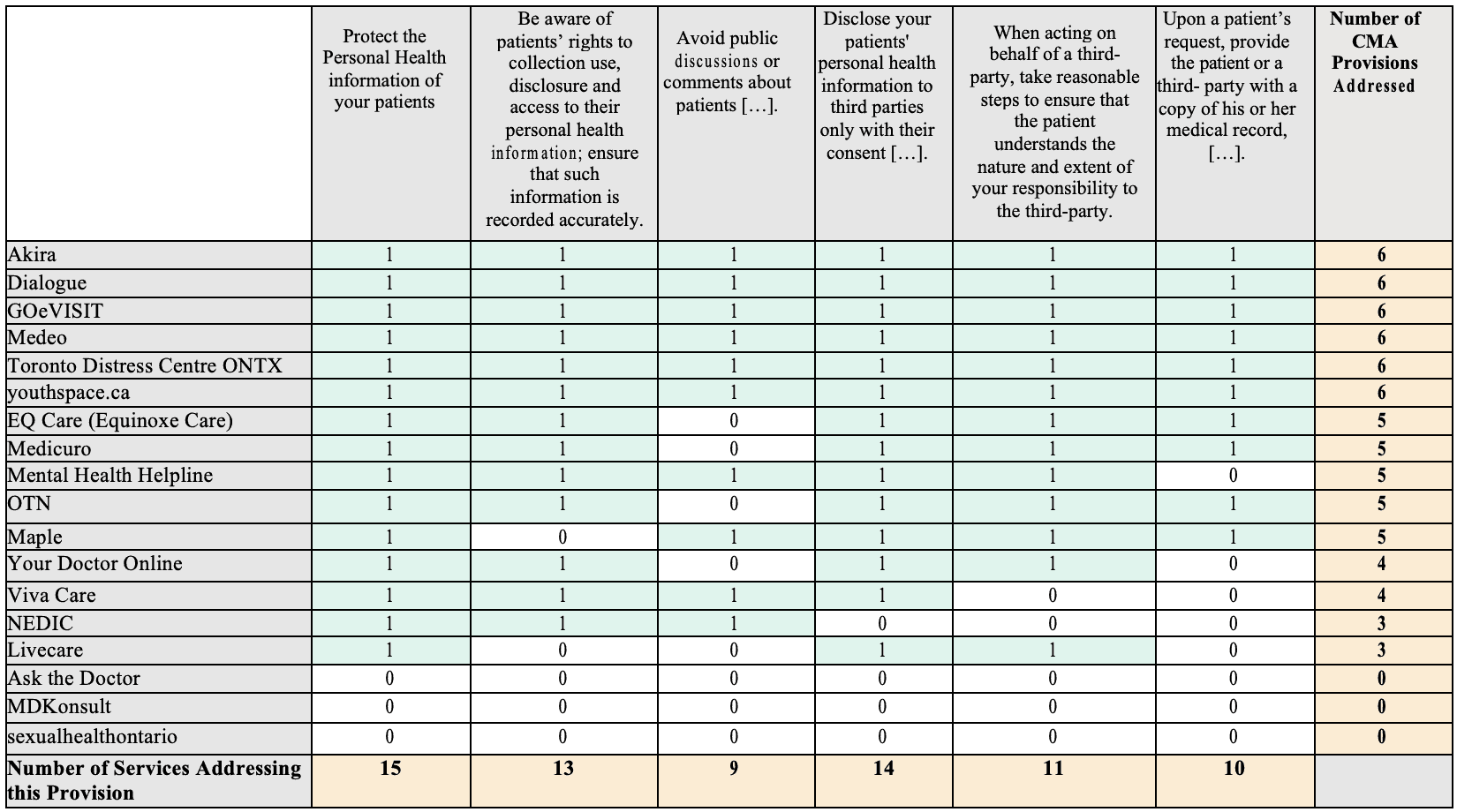



Mean CMA adherence = 4.17 provisions, Median= 5 provisions.
Discussion
CMA’s Privacy and Confidentiality Codes
Of the 15 services surveyed which had an explicit privacy policy, six of these met the CMA’s provisions for Privacy and Confidentiality, while the remaining nine services had privacy statements that met at least half of the CMA provisions. It is important to note that when a service-provider’s policy did not make explicit mention of one of the CMA provisions, it was read as though the service provider was not abiding by the code. While the absence of a provision in the privacy policy does not necessarily mean that the service provider is not abiding by the CMA provisions, this absence is instructive. These policies tend to be quite lengthy and thorough, and so for the clarity of these policies all privacy measures taken ought to be stated explicitly.
As for adherence to specific CMA codes, the services that were examined had a policy that affirmed their general commitment to “Protect the personal health information of [their] patients36.” This code is quite general but the unanimous adherence suggest at the very least, a basic understanding and engagement with privacy concerns. Likewise, all but one service explicitly affirmed that they would only disclose personal information with consent or as required by law and would notify patients of any breaches.
The two codes which were most often unobserved (five of 15 services not mentioning them) were avoiding public discussion of sensitive information and providing patients with a copy of their medical record upon request. LiveCare (Private) and NEDIC (Non-Profit Organization) each failed to explicitly address three of the CMA’s six codes, the most of any of the services with available privacy policies. It is important to note that there seems to be little discernible difference between public or not-for-profit organizations and private companies when it comes to observance of the CMA’s Privacy and Confidentiality Codes.
Business Model
As with any organization, understanding the funding model is intrinsic to understanding how it functions. Our primary concern regarding the funding models was borne out of the popular internet maxim, “[i]f you are not paying for it, you’re not the customer; you’re the product being sold37.” Of particular concern was the issue that if there was not a clear revenue stream for a service, then perhaps the personal health data of users was at risk of being sold.
While a service may appear to be free for the user, there is the possibility that the owners of the applications may attempt to generate revenue in other ways that the consumer is implicated in but unaware of. Even for these ostensibly “free” private healthcare services, there must be some sort of revenue stream, and if there is no cost for the user, then it is possible the selling of user data could be a source of income. Leontiadis et al.38 found that 77% of the top free mobile applications were supported through targeted ads which required access to personal information, and that 94% of these applications also requested network access, which could potentially result in data being leaked. Since free applications tend to request more privacy permissions than paid applications, it is important to understand how the current advertisement model works.
Of the eHealth services that were surveyed, two were publicly funded, run directly by the Ontario government and offered free of charge (Ontario Mental Health Helpline and Sexual Health Ontario). In these situations, the funding models were quite clear. Beyond these publicly administered services, there were four services which were run by independent, not-for-profit organizations (NEDIC, Toronto Distress Centre, youthspace.ca and OTN). Of these four not-for- profits, OTN is the only one that is funded exclusively by the provincial government. The other three services are funded with a mix of grants (public and private), private donation, and corporate sponsorship including Dove, Bell Canada and RBC for NEDIC, Hydro One Inc. and TD Bank Group for the Toronto Distress Centre and Canada Post for youthspace.ca39 40 41.
The remaining 12 services surveyed were privately funded, for-profit organizations. Of these 12, seven of the services (Maple, EQ Care, YourDoctors.online, Medicuro, MDKonsult, Akira, Ask the Doctor) charged patients a clear fee for each consultation ranging between $15 and $150. Dialogue has a similar fee-based model except, in this case, the fees are paid by the employer. Similarly, the fees for Livecare and Medeo are paid by healthcare providers in order to have access to “resources and support to help [them] maximize revenue42.” Lastly, Viva Care and GOeVisit are private companies which provide service to any patients with provincial healthcare coverage. While there is no direct fee for Canadian residents to use GOeVisit, non- Canadians can also access the service for $49.95 per consultation43. Advertisements were relatively rare with only the privately-operated Livecare and Viva Care utilizing them.
While the presence of a clear revenue stream does not preclude the selling of a user data, a lack of evidence of fee or grant based revenue streams should raise a red flag.
Accessibility of Privacy Information
As previously mentioned, the protection of personally identifiable health-related information has traditionally been held to very high standards. There are strict regulations surrounding storing and keeping physical and digital health records by medical practitioners and the advent of new technologies like telehealth and eHealth present new challenges to sensitive health information and its protection. While the policies surrounding physical medical charts might be quite straightforward, things begin to get more complex with eHealth and the inclusion of video conference recordings or chat logs.
When dealing with any sensitive information, the disclosure of privacy policies is critical to the patient’s understanding of what will be done with their information. Having a Privacy Policy and Terms of Use document visible on the homepage of a website signals to the consumer that their privacy is being considered and that the service provider is aware of the serious responsibility that comes with access to such information. While simply having a Privacy Policy and Terms of Use document does not mean that data is necessarily being dealt with appropriately, it does reflect a certain level of awareness and sensitivity.
Of the 18 surveyed services, 12 had both a Privacy Policy and a Terms of Use document, two, Medicuro, Mental Health Helpline, had only a Privacy Policy, one, Youthspace.ca, had a Terms of Use and the remaining three, MDKonsult, askthedoctor, sexualhealthontario had neither. While the presence of one, either a Privacy Policy or a Terms of Use, may be sufficient to ensure patient privacy, services that lacked any visible policies whatsoever were quite concerning.
As stated above, Derse and Miller stressed the importance of physicians only engaging with eHealth services which had defined privacy policies in order to be sure that their patients’ information would remain confidential44. This recommendation for discretion over eHealth services applies to patients as well, since a number of eHealth services examined (namely MDKonsult, Ask the Doctor and sexualhealthontario), do not disclose what will be done with the patient’s information. It is important to note that publicly funded organizations are not necessarily more forthcoming about their data use compared to private organizations as sexualhealthontario, which is a provincial government program, and lacks a privacy policy entirely.
Reading Level of the Privacy Policy and Terms of Use
An important facet of ensuring privacy policies are accessible is the reading level of the Privacy Policy documents themselves. Having a Privacy Policy and Terms of Use that can be easily found on a service’s website will not be very helpful to users if the documents are full of legal jargon that they cannot understand. Of the documents available, both the mean and the median reading level hovered around grade 14-15 or second-third year of university. While 54% of Canadians between the ages of 25-64 have a post-secondary degree, and could presumably read at this level, a discernible portion of the population would still have difficulty trying to understand these policies45.
Without the ability to read and understand these documents it is difficult for individuals to make informed decisions about their healthcare and the use of their health data. This, of course, is assuming that individuals with a post-secondary education will make it to the privacy policy in the footer of these websites. Many of these sites have sleek and eye-catching designs which require the user to scroll past long pages outlining the benefits of their services, with videos that grab the user’s attention, in order to find the privacy policies at the bottom of the webpage.
Social Media
The majority of the services that were surveyed have social media buttons linking to their various accounts. While the presence of these services on social media and their request (implied or explicit) for users to follow them is not problematic, the request for greater connection between the patient and the healthcare provider increases the amount of data that could possibly be breached.
This is especially pertinent for the services which explicitly involved third-party social media applications. YourDoctors.Online allowed for users to sign-in using an existing Facebook or Gmail account. This is problematic as it links the sensitive health data already held by YourDoctors.Online to further personally identifiable information. Similarly, both Livecare and Maple had apps downloadable through Google Play or Apple accounts again linking the existing data these services hold about a user to data from other online services. These two apps also present additional privacy concerns as they have access to information on your device including images, general storage, camera, and microphone which are implicated in gathering sensitive health information on the platform.
While it does not utilize social media specifically, GOeVisit facilitates its live consultations using Facetime or Skype. The involvement of these third parties is explained in their Privacy Policy which states:
…you assume all risks associated with disclosing your information through Skype™. You understand that, while Skype™ does not warrant that it complies with the HIPAA Security Rule, Skype™ does state that it uses well-known standards-based encryption algorithms to protect Skype™ users’ communications against unauthorized persons. You acknowledge that you have had the opportunity to review information about Skype™’s privacy, available here and its security, available here46.
While GOeVisit is compliant with each of the CMA’s six codes, sensitive health data could still be at risk when it comes into contact with third parties like Skype. Though companies like Skype use encryption, the fact that they are not in the business of securing health data specifically raises ethical concerns about the security of that data.
As more and more parties become involved in healthcare provision, the already complex issue of privacy in eHealth service becomes even more complicated. As seen above in the Skype statement, it is often assumed that the patient has taken the time to read the Privacy Policies and Terms of Use documents for the third parties involved in providing eHealth service, even if the links to these documents are not prominently displayed. Not only does a user have to locate and understand the service provider’s Privacy Policy and Terms of Use (if they are available), they must do the same for each of the third-party applications involved.
Further Research
While this study was primarily limited to a Canadian context, eHealth services are becoming more popular around the world. Further research could compare the situation in Canada with eHealth service in other countries. Investigating the difference between eHealth service in a public healthcare setting like Canada and a private system like the United States would be of particular interest. Specifically, in countries with private healthcare systems, citizens who would otherwise have to pay for healthcare may be more likely to turn to a free healthcare application. Studying the data collection and privacy policies of popular eHealth applications in these countries would also be of interest.
Additionally, another direction for future research could include a study that is qualitative in nature which seeks to explore what users of these services understand as personal health data. Such a study could explore understandings of the confidentiality of sensitive health data through the lens of a post-privacy society where data sharing is more prevalent.
Conclusion
In investigating the data we collected on 18 live eHealth chat services hosted in Canada, we came to a number of conclusions about the state of privacy in Canadian eHealth service.
First, that eHealth platforms which had a public-facing Privacy Policy made at least some reference to the CMA’s Privacy and Confidentiality codes. These codes were just updated in 2018 and we believe that they are a helpful starting point for any eHealth services in Canada to begin addressing their Privacy Policies. As such, we recommend that existing and future eHealth service providers strive to meet each of the six codes if they do not already.
We were concerned about the possible sale of patient data by service-providers, and we were encouraged to find that each of the services that we researched had a clear funding model in place. Though this does not necessarily mean that patient data is well protected, we did not have any immediate concerns about the sale of data.
Perhaps the greatest barrier we identified for patients in understanding how their health data would be used was a lack of accessible privacy policies. We separated this notion of accessibility into two parts, the first being the presence of policy documents that can be found on the homepage of the website. While the majority of service-providers had both Privacy Policies and a Terms of Use documents that were easily accessible, it was concerning that three services had no public-facing policy documents whatsoever.
The second part of accessibility relates to reading levels required to read and comprehend these policies. The mean reading level required to read the policy documents accessed was between Grade 14-15 meaning that the roughly 46% of Canadians between the ages of 25-64 who do not have a postsecondary education may be unable to fully understand these documents. We recommend that organizations which are interested in having patients understand their privacy policies, ensure that they are written in plain language and easily understood.
Finally, the integration of social media applications and other third-party service- providers like Skype and Facetime into eHealth services raised ethical concerns for us. While eHealth providers in Canada are bound by strict regulations these third-parties do not necessarily have the same responsibilities. When third-party involvement is unavoidable, we recommend that the primary eHealth provider be as open as possible about privacy policies.
Works Cited
blue_beetle. 2010. “User-driven discontent.” MetaFilter. Accessed 2018 March. https://www.metafilter.com/95152/Userdriven–discontent#3256046.
Boyer, C. 2012. “The Internet and Health: International Approaches to Evaluating the Quality of Web-Based Health Information. In C. George, D. Whitehouse, & P. Duquenoy, eHealth: Legal, Ethical and Governance Challenges.” 245-274. Berlin: Springer.
Canada’s Health Informatics Association. 2012. ” Health Informatics Professional Core Competencies.” Canada’s Health Informatics Association. November. https://digitalhealthcanada.com/wp-content/uploads/2017/03/Health-Informatics-Core- Compet.
Canadian Medical Association. 2018. CMA Policy: CMA Code of Ethics (Update 2004). March.
Accessed March 2018. https://www.cma.ca/Assets/assets- library/document/en/advocacy/policy- research/CMA_Policy_Code_of_ethics_of_the_Canadian_Medical_Association_Update_ 2004_PD04-06-e.pdf
Carey, M. 2001. “The Internet Healthcare Coalition: eHealth Ethics Initiative.” Journal of the American Dietetic Association 101(8), 878.
Chaet, D., R. Clearfield, J. E. Sabin, and K. Skimming. 2017. ” Ethical practice in Telehealth and Telemedicine.” Journal of General Internal Medicine, 32(10), October: 1136–1140.
Denecke, K., P. Bamidis, C. Bond, E. Gabarron, M. Househ, A. Lau, and M. Hansen. 2015. “Ethical Issues of Social Media Usage in Healthcare.” Yearbook of Medical Informatics, 10(1), 137-147.
Derse, A. R., and T. E. Miller. 2008. “Net Effect: Professional and Ethical Challenges of Medicine Online.” Cambridge Quarterly of Healthcare Ethics, 453-464.
Di lorio, C. T., and F Carinci. 2013. “Privacy and Health Care Information Systems: Where is the Balance?” In eHealth: Legal, Ethical and Governance Challenges, by C. George, D. Whitehouse and P. Duquenoy, 77-105. Berlin: Springer.
Distress Centres. 2016. “Distress Centres 2016 Annual Report.” Distress Centres. Accessed March 2018. https://static1.squarespace.com/static/5a03516264b05fad2cec401c/t/5a15e64871c10b644 b17793e/1511384651949/DC-Annual-Report-2016.pdf.
Dobby, Christine. 2013. “More than 90% of Canadians Can’t Get Enough of Google Poll.” Financial Post. January 07. Accessed 2018. http://business.financialpost.com/technology/more-than-90-of- canadians-cant-get – enough-of-google-poll.
Duquenoy, P., Mekawie, N. M., & Springett, M. 2012. “Patients, Trust and Ethics in Information Privacy eHealth.” In eHealth: Legal, Ethical and Governance Challenges, by C. George, Whitehouse and P. Duquenoy, 275-295. Berlin: Springer.
Dyer, K. A. 2001. “Ethical Challenges of Medicine and Health on the Internet: A Review.”
Journal of Medical Internet Research, April-June.
Eysenbach, G., G. Yihune, K. Lampe, P. Cross, and D. Brickley. 2000. “Quality management, certification and rating of health information on the Net with MedCERTAIN: using a medPICS/RDF/XML metadata structure for implementing eHealth ethics and creating and rating of health information on the Net…” Journal of Medical Internet Research, 2E1.
Fleming, D. A., K. E. Edison, and H Pak. 2009. “Telehealth ethics.” Telemedicine Journal and e- Health: The Official Journal of the American Telemedicine Association, 797-803.
Geangu, I. P., D. A. Gârdan, and O. A. Orzan. 2014. “Medical Services Consumer Protection in the Context of eHealth Development.” Contemporary Readings in Law and Social Justice 6 (1): 473-482.
GOeVisit. 2018. “How it Works.” Accessed March 2018. https://goevisit.com/how-it-works Government of Canada. 2010. “eHealth.” Government of Canada. August 9.
https://www.canada.ca/en/health-canada/services/health-care-system/ehealth.html Information and Communications Technology Council. 2009. “eHealth in Canada Current
Trends and Future Challenges.” Information and Communications Technology Council. April. https://www.ictc–ctic.ca/wp- content/uploads/2012/06/ICTC_eHealthSitAnalysis_EN_04-09.pdf.
Kaplan, B., and S Litewka. 2008. “Ethical challenges of telemedicine and telehealth.” Cambridge Quarterly of Healthcare Ethics, 401-416.
Khoja, S., H. Durrani, and P. F Nayani. 2012. “Scope of Policy Issues in eHealth: Results From a Structured Literature Review.” Journal of Medical Internet Research, E34.
Kleinpeter, E. 2017. “Four Ethical Issues of “E-Health”.” Irbm, 245-249.
Lee, L. M. 2017. “Ethics and subsequent use of electronic health record data.” Journal of Biomedical Informatics, 143-146.
Leontiadis, I., C. Efstratiou, M. Picone, and C Mascolo. 2012. “Don’t kill my ads! Balancing privacy in an ad-supported mobile application market.” 12th Workshop on Mobile Computing Systems & Applications. San Diego, CA: HotMobile ’12.
Liang, B., T. L. Mackey, and K. M. Lovett. 2011. ” eHealth Ethics: The Online Medical Marketplace and Emerging Ethical Issues. Ethics in Biology, Engineering and Medicine.” 253-265.
Livecare. 2018. ” Home.” https://www.livecare.ca/connect
Michalopoulos, S. 2016. “E-health and the ‘fine line’ of big data.” Euractiv. December 15. https://www.euractiv.com/section/health-consumers/news/special-report-e-health-and- the-fine-line-of-big-data/.
Microsoft. 2018. “Test your document’s readability.” Office Support. Accessed March 2018. https://support.office.com/en-us/article/Test-your-document-s-readability-85b4969e- e80a-4777-8dd3-f7fc3c8b3fd2# toc342546558
MyCare MedTech Inc. 2018. “Privacy Policy.” https://goevisit.com/privacy-policy NEDIC. 2014. “Funding and Community Partners.” http://nedic.ca/about/funding-and-community-partners.
NEED2. 2016. “Funders.” https://need2.ca/funders/.
Razmak, J., and C. H. Bélanger. 2017. “Comparing Canadian physicians and patients on their use of e-health tools.” Technology in Society, 102-112.
Rippen, H., and R. Ahmad. 2000. “e-Health Code of Ethics.” Journal of Medical Internet Research, April: E9.
Rodwin, M. A. 2010. “Patient data: property, privacy & the public interest.” American Journal of Law & Medicine, 586-618.
Samavi, R., and T. Topaloglou. 2008. “Designing Privacy-Aware Personal Health Record.” In ER Workshops, 12-21. Berlin, Heidelberg: Springer. Soenens, E. 2008. “Identity Management Systems in Healthcare: The Issue of Patient Identifiers.” IFIP AICT 298: The Future of Identity in the Information Society, 55-66.
StatCounter. 2018. “Search Engine Market Share in Canada.” March. http://gs.statcounter.com/search-engine-market-share/all/canada.
Statistics Canada. 2013. “Canadian Internet use survey, Internet use, by age group, Internet activity, sex, level of education and household income.” Statistics Canada. October 28. http://www5.statcan.gc.ca/cansim/a26?lang=eng&retrLang=eng&id=3580153&&pattern=&stByVal=1&p1=1&p2=31&tabMode=dataTable&csid=.
—. 2017. “Education in Canada: Key results from the 2016 Census.” Statistics Canada. from https://www.statcan.gc.ca/daily-quotidien/171129/dq171129a-eng.htm.
Wadhwa, K., and D. Wright. 2012. “eHealth:Frameworks for Assessing Ethical Impacts.” In eHealth: Legal, Ethical and Governance Challenges, by C. George, D. Whitehouse and Duquenoy, 183-210. Berlin: Springer.
Webster, P. C. 2010. “Canada’s ehealth software “Tower of Babel”.” Canadian Medical Association Journal, December 14.
Whitehouse, D., and P. Duquenoy. 2008. “Applied Ethics and eHealth: Principles, Identity, and RFID.” IFIP AICT 298: The Future of Identity in the Information Society, 43-55.
Winkelstein, P. 2012. “Medicine 2.0: Ethical Challenges of Social Media for the Health Profession.” In eHealth: Legal, Ethical and Governance Challenges, by C. George, D. Whitehouse and P. Duquenoy, 227-243. Berlin: Springer.
Geangu, P., D. A. Gârdan, and O. A. Orzan. 2014. “Medical Services Consumer Protection in the Context of eHealth Development.” Contemporary Readings in Law and Social Justice 6 (1): 473-482.
Statistics Canada. 2013. “Canadian Internet use survey, Internet use, by age group, Internet activity, sex, level of education and household income.” Statistics Canada. Accessed October 28. https://goo.gl/sbzMVZ.
Geangu, Gârdan, & Orzan, 2014, p.
Government of Canada. 2010. “eHealth.” Government of Canada. Accessed August 9.https://goo.gl/JFX5bS.
Webster, P. C. 2010. “Canada’s ehealth software “Tower of Babel”.” Canadian Medical Association Journal, 182 (18). Accessed March 2018. http://www.cmaj.ca/content/182/18/1945
Chaet, D., R. Clearfield, J. E. Sabin, and K. Skimming. 2017. ” Ethical practice in Telehealth and ”
Journal of General Internal Medicine, 32(10), October: 1136–1140.
Razmak, J., and C. H. Bélanger. 2017. “Comparing Canadian physicians and patients on their use of e-health tools.” Technology in Society Volume 51: 102-112.
Canada’s Health Informatics Association. 2012. ” Health Informatics Professional Core Competencies .” Canada’s Health Informatics Association. Accessed November 2018. https://digitalhealthcanada.com
Information and Communications Technology 2009. “eHealth in Canada Current Trends and Future Challenges.” Information and Communications Technology Council p. 5. Accessed April 2018. https://goo.gl/cGgg9q
Khoja, , H. Durrani, and P. F Nayani. 2012. “Scope of Policy Issues in eHealth: Results From a Structured Literature Review.” Journal of Medical Internet Research Volume 14, Issue 1 p.E34.
Dyer, K. A. 2001. “Ethical Challenges of Medicine and Health on the Internet: A Review.” Journal of Medical Internet Research 3(2) E23.
Duquenoy, P., Mekawie, N. M., & Springett, M. 2012. “Patients, Trust and Ethics in Information Privacy eHealth.” In eHealth: Legal, Ethical and Governance Challenges, by C. George, D. Whitehouse and P. Duquenoy, 275-295. Berlin: Townsend, A., Leese, J., Adam, P., McDonald, M., Li, L. C., Kerr, S., & Backman, C. L. (2015). “eHealth,
Participatory Medicine, and Ethical Care: A Focus Group Study of Patients’ and Health Care Providers’ Use of Health-Related Information.” Journal of Medical Internet Research, 17(6), e155.
Fleming, D. A., Edison H. A, and Pak, A. 2009. “Telehealth ethics.” Telemedicine Journal and e-Health, (15)8 p. 797-803.
Kaplan, B., and Litewka, S. 2008. “Ethical challenges of telemedicine and telehealth.” Cambridge Quarterly of Healthcare Ethics, (17), Issue 4 p. 401-416.
16 Chaet, et al. 2017. p.1136–1140.
Whitehouse, D., and P. Duquenoy. 2008. “Applied Ethics and eHealth: Principles, Identity, and RFID.” IFIP AICT 298: The Future of Identity in the Information Society, 43-55.
Samavi, R., and T. Topaloglou. 2008. “Designing Privacy-Aware Personal Health Record.” In ER Workshops, 12-Berlin, Heidelberg: Springer.
Wadhwa, K., and D. Wright. 2012. “eHealth:Frameworks for Assessing Ethical Impacts.” In eHealth: Legal, Ethical and Governance Challenges, by C. George, D. Whitehouse and P. Duquenoy, 183-210. Berlin: 20 Soenens, E. 2008. “Identity Management Systems in Healthcare: The Issue of Patient Identifiers.” IFIP AICT 298: The Future of Identity in the Information Society, 55-66.
Derse, A. R., and T. E. Miller. 2008. “Net Effect: Professional and Ethical Challenges of Medicine Online.”Cambridge Quarterly of Healthcare Ethics 17(4) 453-464.
Di lorio, C. T., and F. Carinci. 2013. “Privacy and Health Care Information Systems: Where is the Balance?” In eHealth: Legal, Ethical and Governance Challenges, by C. George, D. Whitehouse and P. Duquenoy, 77-105. Berlin: Springer.
Boyer, C. 2012. “The Internet and Health: International Approaches to Evaluating the Quality of Web-Based Health Information. In C. George, D. Whitehouse, & P. Duquenoy, eHealth: Legal, Ethical and Governance Challenges.” 245-274. Berlin:
Rodwin, M. A. 2010. “Patient data: property, privacy & the public interest.” American Journal of Law & Medicine, 586-618.
Kleinpeter, E. 2017. “Four Ethical Issues of “E-Health”.” IRBM, 38(5) 245-249.
Lee, L. M. 2017. “Ethics and subsequent use of electronic health record data.” Journal of Biomedical Informatics, Volume 71 143-146.
Winkelstein, P. 2012. “Medicine 2.0: Ethical Challenges of Social Media for the Health Profession.” In eHealth: Legal, Ethical and Governance Challenges, by C. George, D. Whitehouse and P. Duquenoy, 227-243. Berlin: Springer.
Liang, B., T. L. Mackey, and K. M. Lovett. 2011.” eHealth Ethics: The Online Medical Marketplace and
Emerging Ethical Issues. Ethics in Biology, Engineering and Medicine,p 253-265; Denecke, K., P. Bamidis, C. Bond, E. Gabarron, M. Househ, A. Lau, and M. Hansen. 2015. “Ethical Issues of Social Media Usage in Healthcare.” Yearbook of Medical Informatics, 10(1), p.137-147.
Michalopoulos, S. 2016. “E-health and the ‘fine line’ of big data.” Euractiv. Accessed March https://goo.gl/PrXN2X.
Khoja et al. 2012.
Canadian Medical Association. 2018. CMA Policy: CMA Code of Ethics (Update 2004). March. Accessed March 2018. https://goo.gl/RBkrnS
Canadian Medical Association.
2018. “Search Engine Market Share in Canada.” Accessed March 2018. http://gs.statcounter.com/search-engine-market-share/all/canada.; Dobby, Christine. 2013. “More than 90% of Canadians Can’t Get Enough of Google: Poll.” Financial Post. January 07. Accessed 2018. https://goo.gl/HtgcP2 34 Microsoft. 2018. “Test your document’s readability.” Office Support. Accessed March 2018. https://goo.gl/AcPxro.
Canadian Medical Association.
2010. “User-driven discontent.” MetaFilter. (Blog comment). Accessed 2018 March. https://www.metafilter.com/95152/Userdriven-discontent#3256046.
Leontiadis, I., C. Efstratiou, M. Picone, and C Mascolo. 2012. “Don’t kill my ads! Balancing privacy in an ad-supported mobile application market.” 12th Workshop on Mobile Computing Systems & Applications. San Diego, CA: HotMobile ’12.
2018. “How it Works.” Accessed March 2018. https://goevisit.com/how-it-works.
Distress Centres. 2016. “Distress Centres 2016 Annual Report.” Distress Centres. Accessed March https://goo.gl/JiWKud.
2016. “Funders.” https://need2.ca/funders/.
2018. ” Home.” https://www.livecare.ca/connect.
Derse, A. R., and T. E. Miller. 2008. “Net Effect: Professional and Ethical Challenges of Medicine Online”. Cambridge Quarterly of Healthcare Ethics, 453-464.
Statistics Canada. 2017. “Education in Canada: Key results from the 2016 Census.” Statistics Canada. from https://www150.statcan.gc.ca/n1/daily-quotidien/171129/dq171129a-eng.htm
MyCare MedTech Inc. 2018. “Privacy Policy.” Accessed March 2018. https://goevisit.com/privacy-policy.
Information Technology and Modern Public Service:
How to Avoid IT Project Failure and Promote Success
Scarlett Kelly
Table of Content
Introduction……………………………………………………………………………………………………………………. 2
Background……………………………………………………………………………………………………………………. 2
What are IT project failures and IT projects success?……………………………………………………………. 3
The factors that determine IT project failures……………………………………………………………………….. 5
People…………………………………………………………………………………………………………………. 6
Process……………………………………………………………………………………………………………….. 7
Product……………………………………………………………………………………………………………… 11
Case study……………………………………………………………………………………………………………………. 12
Recommendations for promoting IT projects success………………………………………………………….. 13
Conclusion…………………………………………………………………………………………………………………… 15
References……………………………………………………………………………………………………………………. 17
Introduction
Successful information technology (IT) projects have the potential to support and transform governmental functions to a higher level of efficiency and cost-effectiveness when delivering services to end-users.1 In this sense, the ideal state is that successful IT projects have the potential to improve public service functions and deliver services to citizens more efficiently and cost effectively.2 However, a global scan shows that IT projects have as high as 85% failure rates and only 15% success rates.3
The reality is that Canada seldom receives such benefits because of the repeated IT project failures and many unanswered questions behind these failures. How can we define IT project failures and successes? Who are the most important stakeholders in any IT project? Facing the negative consequences of IT project failures, especially the financial burden, is the purpose of this paper which performs an in-depth analysis of IT project failure/success factors with real-life examples, including the Phoenix pay system4 as a case study.
To answer the research question “what are the factors that contribute to the success or the failures of IT projects in governments,” this paper will examine the three key factors of IT projects — the people involved, IT processes (purpose of the project, planning, and implementation with a focus on external/internal management), and product to deliver to users. After presenting a holistic understanding of IT project failures, this paper will make actionable recommendations in the Canadian context for promoting IT project success.
Based on the research done to date, the key finding is that many of the IT projects are politically motivated and departmental staff expertise is often overlooked. Lack of leadership and sufficient in-house IT knowledge appears to have made governments make decisions by instinct, so the failure of linking IT products with the internal departmental function becomes inevitable.
Background
The application of IT in the government fundamentally changed the government in no less a way than the French revolution reshaped Europe or printing technology shaped the western civilization.5 6 Electronic government, or e-government provides a channel for citizens to directly communicate with the government in an online environment, which enhances citizen engagement, provides new information presentation, and consultation.7 However, IT projects do not always return benefits. The Auditor General of Canada (Auditor General) found that in the Department of National Defence (DND), IT project implementation took on average seven years after a long seven-year funding approval.8 Moreover, by 1994 about $1.2 billion out of $3.2 billion in the IT program budget was not supported by a plan that monitors expenditure and the implementation process, and $700 million could have been saved if 11 projects had been implemented based on priority.9
In addition to the technology failure, IT disruptions frequently happens because of:
- the failure of planning, managing and decision-making when implementing IT products;
- the lack of control and risk 10
Three main factors contribute to the IT failure or success in the government—people, process and product.11
- People include government departments, external stakeholders, and citizens/end-users.
- The IT project process begins with finding the right project and ends with implementing the project within a specific timeline. In other words, the IT process is a business process which includes defining the purpose of introducing IT products (the question why), listing all the desired features of the product, purchasing or manufacturing the product by establishing partnerships with the private sector, developing a detailed and complete implementation plan (financing, deadlines, evaluation, and accountability), managing the implementation both internally and externally, and delivering a functioning final product. Both senior management commitment and project management play vital roles in the IT process because of the complex relations between the public and private sectors as well as the considerations within the government and with end-users, which will be discussed in detail in the “process” section.
- Product includes the technology selected for users and its performance
The three components are inter-related; for example, when people fail to work together and develop a common goal, the IT process will not go smoothly and meet the goals all stakeholders agreed upon. The obstacles in the IT product implementation process can lead to malfunctioning projects which directly result in the final products not meeting the needs of the stakeholders. However, this relationship is not linear. For example, any problems in the process could change the relations among the people involved, which can change the final product and the performance evaluation framework. All these will be discussed in detail in the next few sections of this paper.
What are IT project failures and IT project successes?
IT project success is defined as most/all stakeholder groups having attained their major goals and there are no significant undesirable outcomes of IT process and products. 12 Such success is achieved by following project schedules, staying in budget, and delivering a final IT product that functions fully as expected. No part in the people, process, and product IT project lifecycle can fail.
The opposite of IT project success, IT project failure, can be defined as project outcomes are not what stakeholders initially expected. Such failure is caused by fragmented planning and mistakes in implementation, project management, and decision-making. These may include, ignoring stakeholders’ needs or the departmental operations that are less ideal for IT product implementation and management, where control and risk prevention are lacking.13 IT project failures can result in delayed schedules, high costs, system uselessness and/or reliability problems, 14 and worst of all, the loss of public confidence in government’s ability and accountability when handling taxpayer’s money. Fear of potential IT project failure can make governments hesitate when considering introducing IT products or deciding not to adopt IT products to eliminate risks. Therefore, IT failure could result in a vicious cycle: less innovation in IT projects due to fear, less effort put into IT projects because of the repeated and perceived failure, and less chance for success.
One of the many examples of IT project failure is the Agriculture and Agri-Food Canada’s attempt to build a fully integrated system, Agconnex, for farmers which resulted in a $14 million failure.15 Another example is the Automated Land and Mineral Record System (ALMRS) system in the U.S., which aimed to improve the Bureau of Land Management’s (BLM) ability to record, maintain, and retrieve information on land description and ownership. ALMRS’s major software component—Initial Operating Capability (IOC)—failed to meet BLM’s needs and was not deployable. 16 This is because BLM failed to strengthen its investment management system acquisition processes and an overall project plan and timeline for actions.17 After spending $411 million, including $67 million spending on the IOC software development, the project was terminated in 1998.18
The factors that determine IT project failures
Introducing IT products to organizations is not a linear technological change but involves complex human factors. 19 Three main factors—people, process, and product—contribute to IT project failure or success in governments. 20 Any interruptions in the people, process, and product implementation stages can result in ripple effects and eventually the project’s failure. For example, when there is stakeholder resistance, reaching a common goal and developing plans becomes more difficult. Such resistance also results in delays in project scheduling and difficulty in managing the IT implementation. There are no sequential relationships: any delay in the schedule can result in difficulty in management which then affects stakeholder and user confidence, as demonstrated in the graph below.
People
As the initial step that leads to IT project failures/successes, the people factor includes government departments, external/private sector stakeholders, and citizens/end-users. 21 The quality of departmental collaboration, stakeholder support/resistance and end-users’ comments on product functionality requirements can all become factors in the potential IT project failure/success.
First, the quality of departmental collaboration can initiate smooth IT planning, but the lack of an effective cross-departmental IT strategy and working governance can be a problem.22 For example, the Sustainable Access in Rural India (SARI) project in Tamil Nadu, India, was an e-government project that used a Wireless-in-Local Loop (WLL) technology to provide internet connections to 39 rural villages in the region.23 A lack of clearly defined goals appeared from the beginning—the program only transformed applications from paper-based to electronic submission without changing the traditional less-transparent back-office operations.24 Such a product did not meet the end-users’ expectations; only 12 villages used the service regularly.25 Furthermore, there was no cross functional service delivery framework due to the lack of collaboration with other levels of government and the failure continued in the long run. 26 There was also no sustained public leadership and commitment, either: the involved officials and staff constantly changed and there was no consistent support for the new technology which induced changes in the traditional roles, authorities and network.27
Second, the development of IT projects often involves multiple stakeholders who have different management styles and goals. 28 Their willingness to collaborate directly affects the project success or failure. For example, the Department of Homeland Security (DHS) in the U.S. is responsible for the security of cyber space. Its programs are aimed at recovery efforts for public and private internet systems, identifying laws and regulations regarding recovery in the event of a major internet disruption, evaluating plans for recovery, and assessing challenges.29 Clarification of roles and responsibilities is crucial because in the course of internet recovery, the private sector owns and operates the majority of the internet.30 Yet there was no consensus among public and private stakeholders about what DHS’ role was or when it should get involved.31 The private sector was reluctant to share information on internet performance with the government, but the government could only take limited actions due to legal issues.32 Such lack of stakeholder engagement directly resulted in the DHS programs failure.
Third, end-users are one of the most crucial components, since their approval of service quality and product functionality indicates the success of IT projects. Meeting end-user’ performance expectations, such as system usefulness and information quality, becomes key to earning their approval on the technology deliverable. Romania’s e-government success largely depended on how its services meet the citizens’ needs of usefulness, ease of use and quality and trust of e- government services.33 In this sense, IT products’ ability to influence citizens’ choices, offer personalized services, and build trust become three pillars to make citizens accept IT products.34
Process
The process stage follows the engagement of the people factors. The process is a broad and complex business concept, which includes clarifying the purpose of introducing IT products agreed upon by most/all stakeholders, identifying the desired features of the product, purchasing or manufacturing the product by establishing partnerships with the private sector, developing a detailed and complete plan on how to implement the products (finance, deadline, evaluation, and accountability), managing IT product implementation both internally and externally, and delivering a functioning final product. The IT process is fundamentally a change management process due to the introduction of new technology35 which establishes the purpose/motivation of IT projects, develops plans to implement IT products, and creates procedures to manage the IT implementation internally and externally. Because IT projects often involve stakeholders from both public and private sectors (technology vendors and consultants), any conflict between the different approaches to managing IT projects can result in project failure. Therefore, the first step is to identify the purposes of the IT project by defining the different interests and identifying common goals between the different stakeholders in the same or different sectors. Understanding different interests enables all the various sectors to identify desired features of the final IT products and develop a coordinated framework to work together. If the final IT project reflects the common goals and coordination and is delivered on schedule, within budget, and has all the required functionality in the final deliverable, the IT project can be considered a success. Any failure in the process can result in the project failures.
First, the business driver —why an IT product is purchased/designed and implemented—is a strong influencer on how the product is implemented.36 For example, if an IT product is introduced because there is leftover budget money at the end of the fiscal year, instead of meeting the identified needs of end-users, the IT project runs the risk of imposing a piece of unwanted technology on and receiving negative reactions from end-users. Globally, the e-government initiative failures often happen when the political stakeholder interest determines the IT design and process, not the users’ needs.37 Political and business influences that create conflicts of interest can play significant parts in IT project failures. For example, a case study in a small town in Germany found that the municipal government faced mayoral elections and the former mayor was running for re-election. The government wished to initiate administrative reform using the e- government implementation as one of the re-election campaign themes. 38 While the project appeared to be high on the political agenda, the actual implementation was fraught with challenges because of conflicts within the project team. The following summary outlines some of the issues the project faced:
- The differences in goal setting in the project team composed of different actors, including consultants, system engineers, researchers, and municipal public servants who had different expertise and interpretations of how municipal government functions.39
- Potential end-users were not involved until the IT product prototype was 40
- The accountability framework was never established, so it became unclear about who should pay for the software 41
- The mayor actively sold the e-government solution for the election campaign, so the doubts about the project failure were 42
The system was never truly functional and only existed for election purposes. Therefore, identifying the drivers behind the IT projects is crucial to understand why IT products are implemented. Defining the reason for adopting IT products is an important step towards the coordination between different sectors and stakeholders.
Second, the planning stage is crucial in terms of the management of the implementation process that usually involves both public and private sectors. Three areas—knowledge of IT products and the selection and implementation process, the project agenda and leadership during the planning and implementation process—need special attention to avoid the symptoms of IT project failure (delay, over budget, and a malfunctioning product as discussed earlier). The lack of knowledge can result in:
- a negative attitude by decision makers towards IT products;
- resistance to change by end users;
- unwillingness to accept new ideas, and
- fear of losing power or job 43
The lack of knowledge of products and vendors may also cause concern when selecting the IT product provider/designer from the private sector prior to contracting the implementation of the IT product. 44 Without sufficient knowledge of the potential IT product and the private sector operations, monitoring, reviewing, and communicating with the private sector IT provider/designer during the implementation phase becomes difficult. 45 Therefore, delays in schedule, higher costs, and ineffective service can happen due to insufficient knowledge of the IT products, private sector operations, and knowing how to manage both. One example is the intranet system implemented for the U.S. Navy that exceeded the cost of almost 4 million dollars in 2004 and completed two years later than the planned completion date.46 47 48
Proposed Solution
After accumulating in-house IT knowledge and identifying policy gaps, an agenda and leadership framework should be developed as the second step in planning. An agenda in the IT process is more than a technology implementation process. It is about setting a timeline that makes IT products acceptable to end-users, along with change or transformation of organizational structure and practice in governments, and expecting on-time, under-budgeted, and functional deliverables.49 Overambitious or unrealistic agendas may be developed if people involved in the IT processes are politically or business driven and do not have commonly agreed upon goal(s). Strong leadership must be in place when developing realistic agendas. Leadership plays a crucial role in IT project planning. A revised agenda may be required to meet unexpected changes, address managerial concerns when both public and private sectors are involved in the same project, and oversee the policy area.
Lack of leadership and insufficient in-house IT knowledge, as well as gaps in IT policy/management, may be one reason the government relies on only a few oligopoly IT suppliers when outsourcing the e-government design and implementation to the private sector. 50 The mismanagement and lack of overseeing policy areas can be reflected in the Canadian government funded Canada Health Infoway, a project which failed to establish a national electronic health record (EHR) after $1.6 billion was spent between 2001 and 2011.51 A case study of the 10-year history of Canada’s e-health plan (based on reviewing national reports and documents as well as conducting interviews with 29 key stakeholders responsible for policy and strategy establishment for health IT from national and provincial organizations) identified that the lack of an e-health policy, inadequate involvement of clinicians, the lack of a business case for using EHR, inadequate regional interoperability, and inflexibility in approach were major barriers to adopting a national EHR.52
Third, the process of implementing and managing IT projects should include managing the technology provider and the relevant departments as well as end users. This is perhaps the most demanding area in the people, process, and product IT project lifecycle because of the various human factors involved in different sectors with different interests, operations, and culture. The public-private (sector) partnerships (P3) arrangement has transferred some traditional government- manned projects to the private sector, which effectively use the comparative advantage of the private sector in terms of efficiency, flexibility, risk sharing, and information asymmetry reduction.53 Successful P3s is powerful in promoting IT project success because of the common goals and different expertise that both sectors bring. For example, in Romania after 2000, an e- procurement system accommodated both public servants and private sector suppliers in its design and management. It enabled the government to manage hundreds of millions of US dollars of transactions annually and reduced opportunities for corruption due to system transparency. 54 Therefore, increasing the e-government success can lay in bridging the gaps between IT products and the reality of government through effective management of P3 to ensure that the private sector IT design matches the public sector uses.55 However, there are many other factors, such as the lack of shared vision, respect, and trust, as well as the weak consensual decision-making capabilities that may result in issues around P3 and effective external management.56
Ideally, the application of technology should enable the government to better serve the public. Many IT products are created and designed by the private-sector. However, the private sector may lack the understanding of the unique processes, systems, structures, and culture in the public sector and cannot meet the governments’ timelines and specific organizational needs in IT design and implementation. 57 Such different views on the purposes of IT products make the internal management of IT products extremely difficult because the gaps in training and staffing and the existing public-sector culture may not meet the requirements of operating IT products. Different operations can reflect in the different perspectives in recognizing risk and risk management styles. As the public sector aims to minimize risks to be more accountable with the public’s money, a risk management plan sometimes does not exist or is not able to solve problems when crises happen. Yet, in general, the private sector is more risk-taking than the public sector and the implementation of new IT products may not be risk-free. Potential risks may be reflected by neglecting the necessary transition between the government’s traditional management processes and the requirements of new management when using technology. For example, the underlining problem in Liverpool, United Kingdom (UK) and in Sheffield, UK 2002 e-voting pilot project identified the gaps between a third-party commercial private sector technology provider and the traditional voting management process in the public sector without addressing potential risks before the election.58 The e-voting controversy in Florida during the 2000 presidential election is another example of government IT failure due in part to insufficient risk identification and a risk management framework.59
Product
The costliest elements of the IT project are the people and the processes. Without a clearly defined plan and change management strategy the project could likely fail.
However, the IT product is what citizens often perceive as the proof of IT project failure. There are some key points that measure the functionality of IT products. For example, IT product quality measures information relevancy, creditability, accessibility, and most importantly, service quality improvement.60 Other aspects include error-free data, consistency in technical performance, and timely and secure information delivery within government. 61 Moreover, fully functional IT products should reflect the common goal that stakeholders originally agreed upon without undesirable outcomes in both the people and process steps. Malfunctioning IT products do not only include the less functional products, but also the products that do not meet the needs of the end-users or the organizations.
A few theoretical models can be used to evaluate if the IT product is a success or a failure. For example, the functionality of the IT products can be summarized using DeLone and McLeans’62 information system (IS) six success components: information quality, system quality, service quality, IS use, user satisfaction, and perceived net benefit.63 End-users’ feedback should be the core of IT product performance evaluation, since citizens/end-users are one of the most important stakeholders of e-government activities and their satisfaction is a factor in measuring e- government service success.64 Furthermore, evaluating IT products is not only an examination of the technology itself, but also a learning process from the whole IT project in order to achieve long-term continuous improvement.
There are more elements that result in the failure to deliver functional IT products in the Canadian federal government. In terms of federal government projects there is the potential for conflict between the political agenda for the software selection and implementation and the departmental end-user and/or the public needs. As mentioned in previous sections, successful projects are those which define the requirements and select and implement a product with clearly defined goals, deliverables and timelines. Projects that fail may be those where software is selected to meet political agendas or because budget money is available at year-end, as has been identified, without any attention to effective implementation schedule and end user requirements.
Therefore, regarding the functionality of IT products mentioned in the previous two paragraphs, IT products in the federal government may present various symptoms of failure such as those software products that have been purchased to meet political agendas. They could end up sitting on shelves and not implemented. The Phoenix pay system is an example of a malfunctioning product that reflects political will, which is discussed in the next section.
Case study
The Phoenix pay system—a malfunctioning, unfixable, and money-eating system—is an example of a current and high-profile IT project failure in the Canadian federal government. The original proposal was to create a centralized payroll management system to save approximately $700 million from the salaries of compensation advisors in each department across the county. 65 However, thousands of employees have been incorrectly paid or not paid at all since Phoenix launched in 2016.66 Currently the attempts to fix Phoenix could cost over $1 billion, while stopping its use could also cost hundreds of millions. 67 As a typical IT project failure (overbudget, malfunctioning product, and loss of public confidence), Phoenix shows a series of failures in the people, process, and IT project management lifecycle. The recent Auditor General (2018) pointed to a few key issues that resulted in the Phoenix project failure. These included a lack of project management from Public Services and Procurement Canada, inadequate engagement with and participation of departments and agencies in designing and building Phoenix, and implementing the Phoenix system when it was not ready.68
By establishing a new payroll management operating model, Phoenix brought a significant change to the complex payroll system in the federal government in areas such as staffing and skillset requirements. 69 Ostensibly, political will, or desiring immediate financial returns may have prevented a collaboration between departments in the areas of planning, communicating, and identifying and addressing risks and concerns.70 Stakeholder involvement appeared to be flawed, especially with the technology provider IBM from the early bidding stage.71 Top-down decision- making processes and influence may have resulted in neglecting to address end-users’ feedback, those staff members that used Phoenix on a daily basis.72 Accordingly, the failure to address institutional changes, stakeholder collaboration, and end-user feedback may have led to the mismatch between Phoenix and the government functions, resulting in project failure.73
After failing the initial people step, Phoenix experienced a fragmented and ill-managed IT process. While the political will leaned towards quickly implementing the software during the change of political parties, 74 other stakeholders wished to have a functional payroll system. Different purposes/motivations and agendas resulted in multi-directional planning, and implementation timelines and deliverables. In-house IT knowledge appeared to be scarce. It was also said that project leadership, risk management oversight, and external and internal management virtually did not exist. The project went ahead even after payroll advisors voiced concerns about the system defects and risks.75 Phoenix’s failure could be inevitable when the system implementation and management was not based on goals agreed by all stakeholders. In other words, the failure of both the people and the process components resulted in a payroll system that did not meet stakeholder’s expectation, created more errors than the current solutions could correct, and led to tremendous financial loss.76
Recommendations for promoting IT project success
IT project success requires the collaboration between people, processes, and product. These factors are inter-related and changing due to people’s altering work environment and updates to technology. These factors make IT projects complex and vulnerable to failure. In this sense, IT projects are fragile: the success of IT projects requires every step to be agreed upon by the various people involved. Each step also has a sequential impact/influence on the next step. For example, the collaboration between government departments is a pre-requisite of establishing leadership and achieving effective external management in the P3. Effective internal and external project and change management in IT implementation procedures are key to ensure that the IT product deliverables are on time, within budget, and most importantly, functioning. In this way, any step must be fastidiously measured and managed, as demonstrated below.
To bridge the gaps between the ideal state (IT project success) and the reality (IT project failure), Goss Gilroy Inc. proposed 17 lessons to learn from Phoenix.77 78
The following recommendations will provide actionable supplements in a people, process, and product sequence to the theoretical lessons, which is not only applicable to Phoenix but future IT projects in the Canadian context. IT experts and information managers’ roles in stakeholder engagement, active participation in the IT procurement, implementation, and management process, and end-user feedback are emphasized.
The first step is to the creation of a leadership role, such as a Minister of Information, to be responsible for people management and central coordination in IT projects. Distributing IT tasks to different departments results in the lack of central power. Stakeholder engagement and common goal setting become difficult when no central power exists to coordinate and manage the complex relations among people and/or organizations. Creating a Minister of Information role is crucial79 in overseeing IT initiatives, such as identifying special needs of a wide range of stakeholders, building relations with the private sector, monitoring the planning and implementation timelines, and changing strategies based on changing priorities and circumstance. The Department of Information should be the central coordinator to effectively use other departments’ resources and establish clear accountability on IT projects. This department should include interdisciplinary experts in IT, information/data management, business/government relations, policy, economics, and psychology to link IT with other key government functions. Most importantly, the department should recognize IT experts and information managers as the most important stakeholders since IT experts and information managers’ expertise can equip the public sector with necessary IT knowledge, match their needs with IT product features, and predict technical risks. Changes in IT processes, such as change of management, communications, and in-house IT capacity may become possible after establishing strong central leadership.
The second step after establishing leadership is to initiate a change of project management responsibility in the IT process. Such change management reflects in the change in external management and internal management. In external management, successful P3s are powerful in promoting IT project success because of the different expertise and resources that both sectors bring. Strong leadership will be responsible for establishing common goals between the public and private sectors, despite the different values and methods of operation. Risk sharing in customizing IT products, instead of buy-off-the-shelf practice, must be negotiated. The successful implementation of the P3 model results in internal stakeholder support and positive organizational culture that meet the needs of introducing and operating new IT products, risk identification, and end-user considerations. In the 2013 Florida iProject, a bidding process was used to identify the top bidder with the most expertise and knowledge in software operating systems.80 Negotiations followed with the successful bidder to identify potential problems in collaboration, test design and product implementation, a method to adopt the agreed-on changes and cost proposal was developed.81 The final product was a functional, one-stop service portal in traffic congestion.82
The project became a success because of the application of the P3 model and the use of effective external management to return a product that met the public sector stakeholder’s needs.83
In internal management, it is crucial to achieve internal culture changes, to develop an understanding that IT projects are not just purchasing technical products but that they are a series in implementing business processes. Every project has potential risks, governments must proactively develop and adopt a risk detection and management framework rather than engaging in the traditional management style, i.e., that governments do not engage in risky behaviour. Any refusal to change the understanding, attitude, and approach towards IT projects may only result in the loss of control when unexpected situations happen. IT experts and information managers need to play an active role in both the external and internal management processes. Their knowledge of IT products can be useful when communicating with the private sector about the desired features of IT products and the establishment of a risk management framework. Internally, IT experts and information managers also have the knowledge of government operations, so the culture change that treats IT implementation and management as a business process could be achieved.
The U.S. Internal Revenue Service (IRS) e-file system in 1999,an electronic income tax return filing system, was a successful case in applying both external and internal management.84 Serving tens of millions of users in the U.S. each year, the IRS system is an example of long-standing successful partnership between the government and the private sector vendor specialized in tax preparation and software development.85 The IRS defined the requirements for the tax-return filing, and a private sector vendor developed software in order to enable tax filing electronically.86 Changes in the internal management of IRS were reflected in establishing strong IRS leadership and the willingness to take risks.87 Such a positive change of external and internal management helped to set a common goal, served the same interests, and created opportunities for all stakeholders. The smooth partnership makes the private sector keen to develop a partnership with IRS and understand the organizational policies and tax environment, while providing the IRS an opportunity to reengineer its tax filing process, thereby achieving a simpler, faster, and virtually error-free state as well as expanding its market.88 The IRS also received support from existing stakeholders, such as the Council for Electronic Revenue Communications Advancement and the National Association of Enrolled Agents, and attracted new expanded partners, such as third-party transmitters, credit card processors, and not-for-profit and professional groups.89
The third step is to change perceptions about IT products and raise the awareness about their implementation and ongoing support and maintenance. An IT product is not a onetime purchase. It requires expert in-house knowledge in project planning, product functionality, budget modification, policy development, software and user evaluation, and continuous product and process improvement. IT experts and information managers’ knowledge about IT products can be particularly useful for long-term IT product maintenance, risk management, and product improvement. When IT experts and information managers become active stakeholders in all stages of IT project planning, negotiation, and implementation, their consistent and insightful knowledge about every stage of the IT project could increase their influence in the decision-making for a particular IT project and future projects. With the involvement of IT experts and information managers, strong leadership should include both a top down and a bottom-up approach, as end- users should become the decision-makers of what products they will be able to use, not the political staff. Since IT experts and information managers are often end-users or work closely with end- users for technical assistance purposes, their input can be one of the most valuable components in the improvement of IT products and further IT projects. Therefore, departments should also share IT best practices, experience, and knowledge with each other to further create IT value.
Conclusion
IT project failure implies that the project outcomes are not what were initially expected and often come with undesirable results. IT project success implies that the project outcomes match most stakeholder groups’ original goals and that there are no significantly undesirable outcomes of IT process and products. Indicators of failure or success are driven by the project timeline, budget, and the functionality of final IT products. IT project failure is rarely due to the malfunction of technology itself but the human factors and underlying government policy at different stages of IT product implementation.90 The paper answered the research question “what are the factors that contribute to the success or the failure of IT projects in governments” through an analysis of various aspects of the people, process, and product in an IT project life cycle. Without leadership and sufficient in-house IT knowledge, governments tend to make decisions by instinct or private sector councils, so the failure of linking IT products with the internal departmental function becomes inevitable.91
In the Canadian context, the recommended three-step actions—establishing a leadership role to oversee people management and centralized coordination in IT projects, changing external and internal project management, and changing perspectives about IT products are crucial to fundamentally improve the current practice in IT product procurement and project management and reduce or even eliminate IT project failures. IT experts and information managers’ involvement in all stages of the project, from business case to implementation are crucial because IT specialists have the technology knowledge. They should be part of the decision-making process, involved in negotiations regarding technology procurement or design, and gathering end-user input for IT product improvement. Large-scale IT project failures, such as Phoenix, will not stop until there are changes to leadership and management in people, process, and product IT product selection and implementation. Only when Canada re-examines the relationships between people, IT implementation processes, and product selection and makes the necessary changes to meet the requirements of IT project success, will it realize the benefits of IT projects.
Bibliography
Abdullah, Nurul Aisyah Sim, Nor Laila Mohd Noor, and Emma Nuraihan Mior Ibrahim. “Contributing Factors to E-Government Service Disruptions.” Transforming Government: People, Process and Policy 10, no. 1 (2016): 120-138. http://ezproxy.library.dal.ca/login?url=https://search-proquest- com.ezproxy.library.dal.ca/docview/1774537026?accountid=10406.
Al-Mamari, Qasim, Brian Corbitt, and Victor Oyaro Gekara. “E-government Adoption in Oman: Motivating Factors from a Government Perspective.” Transforming Government: People, Process and Policy 7, no. 2 (2013): 199-224. Accessed April 19, 2017. doi: 10.1108/17506161311325369
Alenezi, Hussain, Ali Tarhini, and Sujeet Kumar Sharma. “Development of Quantitative Model to Investigate the Strategic Relationship between Information Quality and E-government Benefits.” Transforming Government: People, Process and Policy 9, no. 3 (2015): 324-
Accessed April 19, 2017. http://ezproxy.library.dal.ca/login?url=http://search.proquest.com.ezproxy.library.dal.ca/d ocview/1748862292?accountid=10406
Alshibly, and Chiong. “Customer Empowerment: Does It Influence Electronic Government Success? A Citizen-centric Perspective.” Electronic Commerce Research and Applications 14, no. 6 (2015): 393-404. doi: 10.1016/j.elerap.2015.05.003
Bagnall, James. “Bagnall: With AG’s report on Phoenix pay system looming, has government actually learned any lessons?” Ottawa Citizen, November 18, 2017. http://ottawacitizen.com/opinion/columnists/bagnall-with-ags-report-on-phoenix-pay- system-looming-has-government-actually-learned-any-lessons
Bhuiyan, Shahjahan H. “Modernizing Bangladesh Public Administration through E-governance:
Benefits and Challenges.” Government Information Quarterly 28(1) (2011): 54-65.
Accessed November 19, 2017. doi: 10.1016/j.giq.2010.04.006.
Blumenthal, A. “The long view.” Government Executive, 39 no. 8, (2007): 63 . http://ezproxy.library.dal.ca/login?url=http://search.proquest.com.ezproxy.library.dal.ca/d ocview/204321170?accountid=10406
Ciborra, Claudio. “Interpreting E-government and Development: Efficiency, Transparency or Governance at a Distance?” Information Technology & People 18, no. 3 (2005): 260-79. doi: 10.1108/09593840510615879
Colesca, Sofia Elena, and Dobrica Liliana. “E-government Adoption in Romania” Proceedings of World Academy of Science: Engineering & Technology, 44, 170-174. Accessed April 19, 2018. http://waset.org/publications/15361/e-government-adoption-in-romania
Das Aundhe, M. and Narasimhan, R. “Public Private Partnership (PPP) Outcomes in E- government – a Social Capital Explanation.” International Journal of Public Sector Management 29, no. 7 (2016): 638-58. doi: 10.1108/IJPSM-09-2015-0160
Delone, William H. and Ephraim R. McLean. “The DeLone and McLean Model of Information Systems Success: A Ten-Year Update.” Journal of Management Information Systems 19, no. 4 (2003): 9-30.
Dovifat, Angela, Martin Bruggemeier, and Klaus Lenk. “The “model of micropolitical arenas” – A framework to understand the innovation process of e-government-projects.” Information Polity: The International Journal of Government & Democracy in the Information Age 12(3) (2007): 127-138. Accessed April 19, 2017. http://web.b.ebscohost.com/ehost/pdfviewer/pdfviewer?vid=4&sid=8edccd57-d1eb- 41be-b0e6-157afe952834%40sessionmgr102
General Accounting Office (GAO). Land Management Systems: Status of BLM’s Actions to Improve Information Technology Management: Report to the Subcommittee on Interior and Related Agencies, Committee on Appropriations, House of Representatives. United States, Office, 2000.
Gillmore, Meagan. “More problems with Phoenix pay system revealed,” Rabble.ca, September 22, 2017. http://rabble.ca/news/2017/09/more-problems-phoenix-pay-system-revealed
Heeks, Richard. “E-Government as a Carrier of Context.” Journal of Public Policy 25, no. 1 (2005): 51-74. Accessed April 19, 2018. http://ezproxy.library.dal.ca/login?url=http://search.proquest.com.ezproxy.library.dal.ca/d ocview/58870342?accountid=10406
Heinrich, Erik. “The big chill: E-government poses many promises for the enlightened age. but will it save us from red tape or deliver us into evil?” Info Systems Executive, 6, no. 2 (2001): 10-13. Accessed April 19, 2018. http://www8.umoncton.ca/umcm-fass- administrationpublique/forum_2001/chill.pdf
Holden, Stephen H., and Patricia D. Fletcher. “The Virtual Value Chain and E-Government Partnership: Non-Monetary Agreements in the IRS E-File Program.” International Journal of Public Administration 28, no. 7-8 (2005): 643-664. doi: 10.1081/PAD-200064223
House of Commons Public Administration Select Committee. “Government and IT— ‘a recipe for rip-offs’: Time for a new approach,” (2011). Accessed November 19, 2017. http://www.publications.parliament.uk/pa/cm201012/cmselect/cmpubadm/715/715i.pdf
Imran, Ahmed, and Shirley Gregor. “Uncovering the Hidden Issues in E-Government Adoption in a Least Developed Country: The Case of Bangladesh.” Journal of Global Information Management, 18, no. 2 (2010): 30-56. Accessed April 19, 2018. doi: 10.4018/jgim.2010040102.
Ireton, Julie. “Phoenix payroll system doomed from the start: report,” CBC News, October 05, 2017. Accessed November 19, 2017. http://www.cbc.ca/news/canada/ottawa/phoenix- federal-government-report-lessons-1.4339476
Kelly, Scarlett. Digital Information Revolution Changes in Canada: E-Government Design, the Battle Against Illicit Drugs, and Health Care Reform. [Alberta: Lammi Publishing Inc., 2016]
Kumar, Rajendra, and Michael L. Best. “Impact and Sustainability of E-Government Services in Developing Countries: Lessons Learned from Tamil Nadu, India.” The Information Society 22, no. 1 (2006): 1-12. doi: 10.1080/01972240500388149
Lammam, Charles, Hugh MacIntyre, Jason Clemens, Milagros Palacios, and Niels Veldhuis. “Federal government failure in Canada : A review of the Auditor General’s reports, 1988- 2013.” Accessed April 19, 2017, [Vancouver, British Columbia: Fraser Institute].
Lawther, Wendell C. “The Growing Use of Competitive Negotiations to Increase Managerial Capability: The Acquisition of E-Government Services.” Public Performance & Management Review 30, no. 2 (2006): 203-20. doi: 10.2753/PMR1530-9576300204
Luna-Reyes, Luis F. and J. Ramon Gil-Garcia. “Using Institutional Theory and Dynamic Simulation to Understand Complex E-Government Phenomena.” Government Information Quarterly 28, no. 3 (2011): 329-45. Accessed April 19, 2017. doi: 10.1016/j.giq.2010.08.007
McGlinchey, D. Navy streamlines its intranet contract. (2004). Accessed April 19, 2017. www.govexec.com/dailyfed/1004/100604d1.htm
Moynihan, Donald P. “Building Secure Elections: E‐Voting, Security, and Systems Theory.” Public Administration Review 64, no. 5 (2004): 515-28. doi: 10.1111/j.1540- 6210.2004.00400.x
Office of Auditor General of Canada. “Report 1—Building and Implementing the Phoenix Pay System.” Last modified May 29, 2018. http://www.oag-bvg.gc.ca/internet/English/att e_43045.html
Osman, Anouze, Irani, Al-Ayoubi, Lee, Balcı, Medeni, and Weerakkody. “COBRA Framework to Evaluate E-government Services: A Citizen-centric Perspective.” Government Information Quarterly 31, no. 2 (2014): 243-56. doi: 10.1016/j.giq.2013.10.009
Randell, Brian. “A Computer Scientist’s Reactions to NPfIT.” Journal of Information Technology 22(3) (2007): 222-234. Accessed November 19, 2017. doi: 10.1057/palgrave.jit.2000106 Rozenblum, Ronen, Jang, Yeona, Zimlichman, Eyal, Salzberg, Claudia, Tamblyn, Melissa,
Buckeridge, David, Forster, Alan, Bates, David W, and Tamblyn, Robyn. “A Qualitative Study of Canada’s Experience with the Implementation of Electronic Health Information Technology.” CMAJ: Canadian Medical Association Journal = Journal De L’Association Medicale Canadienne 183, no. 5 (2011): E281-8. doi: 10.1503/cmaj.100856
Schuppan, Tino. “E-Government in Developing Countries: Experiences from Sub-Saharan Africa.” Government Information Quarterly 26, no. 1 (2009): 118-27. doi: 10.1016/j.giq.2008.01.006
Scotti, Monique. “With Phoenix pay system fix potentially costing $1B, union says time to pull the plug,” Global News, November 14, 2017. Accessed November 14, 2017. https://globalnews.ca/news/3859554/phoenix-pay-system-fix-cost-billion-union/
Seng, Wong Meng, Stephen Jackson, and George Philip. “Cultural Issues in Developing E- Government in Malaysia.” Behaviour & Information Technology 29(4) (2010): 423-32. Accessed November 19, 2017. doi: 10.1080/01449290903300931
Treasury Board of Canada Secretariat. “Lessons Learned from the Transformation of Pay Administration Initiative, October 2017.” Last modified October 10, 2017. https://www.canada.ca/en/treasury-board-secretariat/corporate/reports/lessons-learned- transformation-pay-administration-initiative.html#1
U.S. General Accounting Office. Information technology: Issues affecting cost impact of Navy Marine Corps intranet need to be resolved (GAO-03–33). (2002a). Accessed November 19, 2017. [Washington, DC: Government Printing Office]
Wang, Yi-Shun and Liao, Yi-Wen. “Assessing EGovernment Systems Success: A Validation of the DeLone and McLean Model of Information Systems Success.” Government Information Quarterly 25, no. 4 (2008): 717-33. doi: 10.1016/j.giq.2007.06.002
Wilshusen, G.C. “Internet Infrastructure: Challenges in Developing a Public/Private Recovery Plan.” 2006. [States: Government Accountability Office]
Xenakis, A and Macintosh, A. “Lessons learned from the e-voting pilots in the United Kingdom”. E-government: Information, technology, and transformation (Advances in management information systems; v. 17). (2010). Schnoll, Hans J Armonk, N.Y.: M.E. Sharpe.
Work Cited
1Shahjahan H. Bhuiyan. “Modernizing Bangladesh Public Administration through E-governance: Benefits and Challenges.” Government Information Quarterly 28(1) (2011): 54-65. Accessed April 19, 2018. doi: 10.1016/j.giq.2010.04.006.
2Shahjahan H. Bhuiyan. “Modernizing Bangladesh Public Administration through E-governance: Benefits and Challenges.” Government Information Quarterly 28(1) (2011): 54-65. Accessed November 19, 2017. doi: 10.1016/j.giq.2010.04.006.
3Richard Heeks. “E-Government as a Carrier of Context.” Journal of Public Policy 25, no. 1 (2005): 51-74. Accessed April 19, 2018. http://ezproxy.library.dal.ca/login?url=http://search.proquest.com.ezproxy.library.dal.ca/docview/58870342?acco untid=10406
4Julie Ireton. “Phoenix payroll system doomed from the start: report,” CBC News, October 05, 2017. Accessed November 19, 2017. http://www.cbc.ca/news/canada/ottawa/phoenix-federal-government-report-lessons-1.4339476
5Erik Heinrich. “The big chill: E-government poses many promises for the enlightened age. but will it save us from red tape or deliver us into evil?” Info Systems Executive, 6, no. 2 (2001): 10-13. Accessed April s19, 2018. http://www8.umoncton.ca/umcm-fass-administrationpublique/forum_2001/chill.pdf
6Scarlett Kelly. Digital Information Revolution Changes in Canada: E-Government Design, the Battle Against Illicit Drugs, and Health Care Reform. [Alberta: Lammi Publishing Inc., 2016]
7Tino Schuppan. “E-Government in Developing Countries: Experiences from Sub-Saharan Africa.” Government Information Quarterly 26, no. 1 (2009): 118-27. doi: 10.1016/j.giq.2008.01.006
8Charles Lammam, Hugh MacIntyre, Jason Clemens, Milagros Palacios, and Niels Veldhuis. “Federal government failure in Canada: A review of the Auditor General’s reports, 1988-2013.” Accessed April 19, 2017, [Vancouver, British Columbia: Fraser Institute].
9ibid
10Nurul Aisyah Sim Abdullah, Nor Laila Mohd Noor, and Emma Nuraihan Mior Ibrahim. “Contributing Factors to E- Government Service Disruptions.” Transforming Government: People, Process and Policy 10, no. 1 (2016): 120-138. http://ezproxy.library.dal.ca/login?url=https://search-proquest- com.ezproxy.library.dal.ca/docview/1774537026?accountid=10406.
11ibid
12Richard Heeks. “E-Government as a Carrier of Context.” Journal of Public Policy 25, no. 1 (2005): 51-74. Accessed April 19, 2018. http://ezproxy.library.dal.ca/login?url=http://search.proquest.com.ezproxy.library.dal.ca/docview/58870342?acco untid=10406
13Charles Lammam, Hugh MacIntyre, Jason Clemens, Milagros Palacios, and Niels Veldhuis. “Federal government failure in Canada: A review of the Auditor General’s reports, 1988-2013.” Accessed April 19, 2017, [Vancouver, British Columbia: Fraser Institute].
14Brian Randell. “A Computer Scientist’s Reactions to NPfIT.” Journal of Information Technology 22(3) (2007): 222- Accessed November 19, 2017. doi: 10.1057/palgrave.jit.2000106
15Charles Lammam, Hugh MacIntyre, Jason Clemens, Milagros Palacios, and Niels Veldhuis. “Federal government failure in Canada: A review of the Auditor General’s reports, 1988-2013.” Accessed April 19, 2017, [Vancouver, British Columbia: Fraser Institute].
16General Accounting Office (GAO). Land Management Systems: Status of BLM’s Actions to Improve Information Technology Management: Report to the Subcommittee on Interior and Related Agencies, Committee on Appropriations, House of Representatives. United States, Office, 2000.
17ibid
18ibid
19Wong Meng Seng, Stephen Jackson, and George Philip. “Cultural Issues in Developing E-Government in Malaysia.” Behaviour & Information Technology 29(4) (2010): 423-32. Accessed November 19, 2017. doi: 10.1080/01449290903300931
20Nurul Aisyah Sim Abdullah, Nor Laila Mohd Noor, and Emma Nuraihan Mior Ibrahim. “Contributing Factors to E- Government Service Disruptions.” Transforming Government: People, Process and Policy 10, no. 1 (2016): 120-138. http://ezproxy.library.dal.ca/login?url=https://search-proquest- com.ezproxy.library.dal.ca/docview/1774537026?accountid=10406.
21Wong Meng Seng, Stephen Jackson, and George Philip. “Cultural Issues in Developing E-Government in Malaysia.” Behaviour & Information Technology 29, no. 4 (2010): 423-32. Accessed November 19, 2017. doi: 10.1080/01449290903300931
22House of Commons Public Administration Select Committee. “Government and IT— ‘a recipe for rip-offs’: Time for a new approach,” (2011). Accessed November 19, 2017. http://www.publications.parliament.uk/pa/cm201012/cmselect/cmpubadm/715/715i.pdf
23Rajendra Kumar and Michael L. Best. “Impact and Sustainability of E-Government Services in Developing Countries: Lessons Learned from Tamil Nadu, India.” The Information Society 22, no. 1 (2006): 1-12. doi: 10.1080/01972240500388149
24ibid
25ibid
26ibid
27ibid
28Angela Dovifat, Martin Bruggemeier, and Klaus Lenk. “The “model of micropolitical arenas” – A framework to understand the innovation process of e-government-projects.” Information Polity: The International Journal of Government & Democracy in the Information Age 12(3) (2007): 127-138. Accessed April 19, 2017. http://web.b.ebscohost.com/ehost/pdfviewer/pdfviewer?vid=4&sid=8edccd57-d1eb-41be-b0e6- 157afe952834%40sessionmgr102
29G.C Wilshusen. “Internet Infrastructure: Challenges in Developing a Public/Private Recovery Plan.” 2006. [States: Government Accountability Office]
30ibid
31G.C Wilshusen. “Internet Infrastructure: Challenges in Developing a Public/Private Recovery Plan.” 2006. [States: Government Accountability Office]
32ibid
33Sofia Elena Colesca and Dobrica Liliana. “E-government Adoption in Romania” Proceedings of World Academy of Science: Engineering & Technology, 44, 170-174. Accessed April 19, 2018. http://waset.org/publications/15361/e-government-adoption-in-romania
34H Alshibly and R Chiong. “Customer Empowerment: Does It Influence Electronic Government Success? A Citizen-centric Perspective.” Electronic Commerce Research and Applications 14, no. 6 (2015): 393-404. doi: 10.1016/j.elerap.2015.05.003
35Ciborra, Claudio. “Interpreting E-government and Development: Efficiency, Transparency or Governance at a Distance?” Information Technology & People 18, no. 3 (2005): 260-79. doi: 10.1108/09593840510615879
36Qasim Al-Mamari, Brian Corbitt, and Victor Oyaro Gekara. “E-government Adoption in Oman: Motivating Factors from a Government Perspective.” Transforming Government: People, Process and Policy 7, no. 2 (2013): 199-224. Accessed April 19, 2017. doi: 10.1108/17506161311325369
37Richard Heeks. “E-Government as a Carrier of Context.” Journal of Public Policy 25, no. 1 (2005): 51-74. Accessed April 19, 2018. http://ezproxy.library.dal.ca/login?url=http://search.proquest.com.ezproxy.library.dal.ca/docview/58870342?acco untid=10406
38Angela Dovifat, Martin Bruggemeier, and Klaus Lenk. “The “model of micropolitical arenas” – A framework to understand the innovation process of e-government-projects.” Information Polity: The International Journal of Government & Democracy in the Information Age 12(3) (2007): 127-138. Accessed April 19, 2017. http://web.b.ebscohost.com/ehost/pdfviewer/pdfviewer?vid=4&sid=8edccd57-d1eb-41be-b0e6- 157afe952834%40sessionmgr102
39ibid
40ibid
41ibid
42ibid
43Ahmed Imran and Shirley Gregor. “Uncovering the Hidden Issues in E-Government Adoption in a Least Developed Country: The Case of Bangladesh.” Journal of Global Information Management, 18, no. 2 (2010): 30-56. Accessed April 19, 2018. doi: 10.4018/jgim.2010040102.
44Wendell C. Lawther. “The Growing Use of Competitive Negotiations to Increase Managerial Capability: The Acquisition of E-Government Services.” Public Performance & Management Review 30, no. 2 (2006): 203-20. doi: 10.2753/PMR1530-9576300204
45ibid
46ibid
47D. McGlinchey. Navy streamlines its intranet contract. (2004). Accessed April 19, 2017. www.govexec.com/dailyfed/1004/100604d1.htm
48U.S. General Accounting Office. Information technology: Issues affecting cost impact of Navy Marine Corps intranet need to be resolved (GAO-03–33). (2002a). Accessed November 19, 2017. [Washington, DC: Government Printing Office]
49Ahmed Imran and Shirley Gregor. “Uncovering the Hidden Issues in E-Government Adoption in a Least Developed Country: The Case of Bangladesh.” Journal of Global Information Management, 18, no. 2 (2010): 30-56. Accessed April 19, 2018. doi: 10.4018/jgim.2010040102.
50House of Commons Public Administration Select Committee. “Government and IT— ‘a recipe for rip-offs’: Time for a new approach,” (2011). Accessed November 19, 2017. http://www.publications.parliament.uk/pa/cm201012/cmselect/cmpubadm/715/715i.pdf
51Ronen Rozenblum, Jang, Yeona, Zimlichman, Eyal, Salzberg, Claudia, Tamblyn, Melissa, Buckeridge, David, Forster, Alan, Bates, David W, and Tamblyn, Robyn. “A Qualitative Study of Canada’s Experience with the Implementation of Electronic Health Information Technology.” CMAJ: Canadian Medical Association Journal = Journal De L’Association Medicale Canadienne 183, no. 5 (2011): E281-8. doi: 10.1503/cmaj.100856
52ibid
53M. Das Aundhe and Narasimhan, R. “Public Private Partnership (PPP) Outcomes in E-government – a Social Capital Explanation.” International Journal of Public Sector Management 29, no. 7 (2016): 638-58. doi: 10.1108/IJPSM-09-2015-0160
54Richard Heeks. “E-Government as a Carrier of Context.” Journal of Public Policy 25, no. 1 (2005): 51-74. Accessed April 19, 2018. http://ezproxy.library.dal.ca/login?url=http://search.proquest.com.ezproxy.library.dal.ca/docview/58870342?acco untid=10406
55ibid
56M. Das Aundhe and Narasimhan, R. “Public Private Partnership (PPP) Outcomes in E-government – a Social Capital Explanation.” International Journal of Public Sector Management 29, no. 7 (2016): 638-58. doi: 10.1108/IJPSM-09-2015-0160
57Richard Heeks. “E-Government as a Carrier of Context.” Journal of Public Policy 25, no. 1 (2005): 51-74. Accessed April 19, 2018. http://ezproxy.library.dal.ca/login?url=http://search.proquest.com.ezproxy.library.dal.ca/docview/58870342?acco untid=10406
58A. Xenakis and Macintosh, A. “Lessons learned from the e-voting pilots in the United Kingdom”. E-government: Information, technology, and transformation (Advances in management information systems; v. 17). (2010). Schnoll, Hans J Armonk, N.Y.: M.E. Sharpe.
59Moynihan, Donald P. “Building Secure Elections: E‐Voting, Security, and Systems Theory.” Public Administration Review 64, no. 5 (2004): 515-28. doi: 10.1111/j.1540-6210.2004.00400.x
60Hussain Alenezi, Ali Tarhini, and Sujeet Kumar Sharma. “Development of Quantitative Model to Investigate the Strategic Relationship between Information Quality and E-government Benefits.” Transforming Government: People, Process and Policy 9, no. 3 (2015): 324-51. Accessed April 19, 2017. http://ezproxy.library.dal.ca/login url=http://search.proquest.com.ezproxy.library.dal.ca/docview/1748862292?ac countid=10406
61ibid
62William H. Delone and Ephraim R. McLean. “The DeLone and McLean Model of Information Systems Success: A Ten-Year Update.” Journal of Management Information Systems 19, no. 4 (2003): 9-30.
63Wang, Yi-Shun and Liao, Yi-Wen. “Assessing EGovernment Systems Success: A Validation of the DeLone and McLean Model of Information Systems Success.” Government Information Quarterly 25, no. 4 (2008): 717-33. doi: 10.1016/j.giq.2007.06.002
64Osman, Anouze, Irani, Al-Ayoubi, Lee, Balcı, Medeni, and Weerakkody. “COBRA Framework to Evaluate E-government Services: A Citizen-centric Perspective.” Government Information Quarterly 31, no. 2 (2014): 243-56. doi: 10.1016/j.giq.2013.10.009
65Julie Ireton. “Phoenix payroll system doomed from the start: report,” CBC News, October 05, 2017. Accessed November 19, 2017. http://www.cbc.ca/news/canada/ottawa/phoenix-federal-government-report-lessons-1.4339476
66ibid
67Monique Scotti. “With Phoenix pay system fix potentially costing $1B, union says time to pull the plug,” Global News, November 14, 2017. Accessed November 14, 2017. https://globalnews.ca/news/3859554/phoenix-pay- system-fix-cost-billion-union/
68Office of Auditor General of Canada. “Report 1—Building and Implementing the Phoenix Pay System.” Last modified May 29, 2018. http://www.oag-bvg.gc.ca/internet/English/att e_43045.html
69Treasury Board of Canada Secretariat. “Lessons Learned from the Transformation of Pay Administration Initiative, October 2017.” Last modified October 10, 2017. https://www.canada.ca/en/treasury-board- secretariat/corporate/reports/lessons-learned-transformation-pay-administration-initiative.html#1
70Meagan Gillmore. “More problems with Phoenix pay system revealed,” Rabble.ca, September 22, 2017. http://rabble.ca/news/2017/09/more-problems-phoenix-pay-system-revealed
71ibid
72James Bagnall. “Bagnall: With AG’s report on Phoenix pay system looming, has government actually learned any lessons?” Ottawa Citizen, November 18, 2017. http://ottawacitizen.com/opinion/columnists/bagnall-with-ags- report-on-phoenix-pay-system-looming-has-government-actually-learned-any-lessons
73Luis F. Luna-Reyes, and J. Ramon Gil-Garcia. “Using Institutional Theory and Dynamic Simulation to Understand Complex E-Government Phenomena.” Government Information Quarterly 28, no. 3 (2011): 329-45. Accessed April 19, 2017. doi: 10.1016/j.giq.2010.08.007
74Monique Scotti. “With Phoenix pay system fix potentially costing $1B, union says time to pull the plug,” Global News, November 14, 2017. Accessed November 14, 2017. https://globalnews.ca/news/3859554/phoenix-pay- system-fix-cost-billion-union/
75James Bagnall. “Bagnall: With AG’s report on Phoenix pay system looming, has government actually learned any lessons?” Ottawa Citizen, November 18, 2017. http://ottawacitizen.com/opinion/columnists/bagnall-with-ags- report-on-phoenix-pay-system-looming-has-government-actually-learned-any-lessons
76Meagan Gillmore. “More problems with Phoenix pay system revealed,” Rabble.ca, September 22, 2017. http://rabble.ca/news/2017/09/more-problems-phoenix-pay-system-revealed
77Angela Dovifat, Martin Bruggemeier, and Klaus Lenk. “The “model of micropolitical arenas” – A framework to understand the innovation process of e-government-projects.” Information Polity: The International Journal of Government & Democracy in the Information Age 12(3) (2007): 127-138. Accessed April 19, 2017. http://web.b.ebscohost.com/ehost/pdfviewer/pdfviewer?vid=4&sid=8edccd57-d1eb-41be-b0e6- 157afe952834%40sessionmgr102
78Treasury Board of Canada Secretariat. “Lessons Learned from the Transformation of Pay Administration Initiative, October 2017.” Last modified October 10, 2017. https://www.canada.ca/en/treasury-board- secretariat/corporate/reports/lessons-learned-transformation-pay-administration-initiative.html#1
79Scarlett Kelly. Digital Information Revolution Changes in Canada: E-Government Design, the Battle Against Illicit Drugs, and Health Care Reform. [Alberta: Lammi Publishing Inc., 2016]
80Wendell C. Lawther. “The Growing Use of Competitive Negotiations to Increase Managerial Capability: The Acquisition of E-Government Services.” Public Performance & Management Review 30, no. 2 (2006): 203-20. doi: 10.2753/PMR1530-9576300204
81ibid
82ibid
83Wendell C. Lawther. “The Growing Use of Competitive Negotiations to Increase Managerial Capability: The Acquisition of E-Government Services.” Public Performance & Management Review 30, no. 2 (2006): 203-20. doi: 10.2753/PMR1530-9576300204
84Stephen H. Holden and Patricia D. Fletcher. “The Virtual Value Chain and E-Government Partnership: Non-Monetary Agreements in the IRS E-File Program.” International Journal of Public Administration 28, no. 7-8 (2005): 643-664. doi: 10.1081/PAD-200064223
85ibid
86ibid
87ibid
88ibid
89ibid
90House of Commons Public Administration Select Committee. “Government and IT— ‘a recipe for rip-offs’: Time for a new approach,” (2011). Accessed November 19, 2017. http://www.publications.parliament.uk/pa/cm201012/cmselect/cmpubadm/715/715i.pdf
91Blumenthal, A. “The long view.” Government Executive, 39 no. 8, (2007): 63. http://ezproxy.library.dal.ca/login?url=http://search.proquest.com.ezproxy.library.dal.ca/docview/204321170?acc ountid=10406
Defending Traditional Rights in the Digital Age:
Ktunaxa Nation Case Study
by Michelle Barroca, BA, MAS
Abstract
This paper provides a case study of the Ktunaxa Nation’s experience with using business and cultural records to legally defend traditional Ktunaxa rights in opposing permanent development in a culturally significant and ecologically sensitive area in the southeast corner of British Columbia.
In 2016, the Ktunaxa Nation v. British Columbia case became the first Indigenous Spirituality and Freedom of Religion case to be heard in the Supreme Court of Canada. The Ktunaxa argued that the proposed location of a year-round ski resort in the Jumbo Valley would cause irreparable harm to their culture and spiritual beliefs.
Despite supplying decades’ worth of documentary evidence, including affidavits containing closely-held Ktunaxa spiritual beliefs, the Crown determined that the proposed Jumbo Glacier Resort project does not infringe upon the Ktunaxa Nation’s right to religious practices. How is this possible when Ktunaxa spirituality, like that of other First Nations, is directly connected to the land?
Using the Ktunaxa Nation’s legal experience as the basis of this study, the author will highlight the challenges associated with documenting and using aboriginal traditional knowledge in the Canadian court system.
The content of this case study was presented by Michelle Barroca and Margaret Teneese at the ARMA Canada conference in Vancouver, BC on May 28, 2018, in addition to the ARMA Vancouver Island Chapter/Archives Association of BC conference in Victoria, BC on April 28, 2017.
Introduction to the Ktunaxa Nation
The Ktunaxa (pronounced “k-too-na-ha”), also known as Kootenay, Kootenai or Kutenai Indians, have inhabited the Kootenay and Columbia River Basins for more than 10,000 years. The Traditional Territory of the Ktunaxa Nation is approximately 70,000 sq. km within the Kootenay region of southeastern British Columbia, and historically included parts of Alberta, Montana, Idaho and Washington. Maps are provided on the following page for reference.



Ktunaxa citizenship is comprised of approximately 1500 Nation members from seven Bands situated throughout Ktunaxa Traditional Territory. Five Bands are located in British Columbia, Canada, and two are located in Idaho and Montana in the United States.
Contact occurred within the past 200 years as European explorers moved westward towards the Rocky Mountains and into Traditional Ktunaxa Territory. Permanent settlement of non-aboriginal inhabitants in the East Kootenay region followed the discovery of gold near Fort Steele in the late 1860s.
In 1886, the reserve system was implemented under the Indian Act, creating the following Ktunaxa communities in British Columbia:
- kyaknuqǂiʔit – Shuswap Indian Band (Invermere)
Note: Many Ktunaxa descendants are registered at the Shuswap Indian Band, which opted out of the Ktunaxa Nation Council in 2005.
- ʔakisq̓ nuk First Nation (formerly Columbia Lake Indian Band, Windermere)
- ʔakink̓ umǂasnuqǂiʔit – Tobacco Plains Indian Band (Grasmere)
- ʔaq̓ am – St. Mary’s Indian Band (Cranbrook)
- yaqan nuykiy – Lower Kootenay Indian Band (Creston) 1
The Ktunaxa language is unique among indigenous linguistic groups in North America. The written form of the language was only formally adopted in the 1970s, following the closure of the St. Eugene Mission Residential School in Cranbrook. Ktunaxa have place names for landmarks throughout the Traditional Territory and numerous heritage sites confirm this region as traditional Ktunaxa lands.
Organizational Context
In preparation of the closure of the Residential School and the Indian Affairs Office in Cranbrook, BC, the Kootenay Indian District Council originated in the 1960s to promote the political and social development of the Ktunaxa Nation.
Since 1982, the Ktunaxa Nation Council (KNC) has been incorporated as a registered non-profit society under the BC Societies Act and is operating as a government in anticipation of self-governance. KNC has been involved with treaty negotiations with Canada and BC since 1993 and is currently working under a revised approach towards self-government under the Rights Recognition and Reconciliation Framework. This new Core Treaty Model no longer includes “full and final” language.
KNC currently employs approximately 120 employees and contractors, and is comprised of a sector model that is representative of the poles of a teepee:
- Economic Investment Sector
- Education and Employment Sector
- Lands and Resources Sector
- Social Sector (includes Health services)
- Traditional Knowledge and Language Sector (includes Archives)
- Core Services, includes:
- Communications
- Facilities Management
- Finance
- Human Resources
- Information Technology
- Records and Information Management
Each Sector is accountable to a Sector Council, which consists of elected representatives from each of the four Ktunaxa Nation communities. The main decision- making body, the Ktunaxa Nation Executive Council, consists of the Chiefs of the four Ktunaxa Nation communities (represented by KNC), the five Sector Council Chairs and the Ktunaxa Nation Chair.
Managing KNC Records
As information management professionals, we are keenly aware of the values associated with the records in our care. Most commonly, records are kept for administrative, operational, fiscal, legal and informational value to an organization. The complexities of managing recorded information in a First Nations environment areheightened by such variables as funding cycles, limited staff capacity, ever-changing technology, as well as the need to integrate intangible cultural resources, such as oral traditions and spiritual beliefs, into official recordkeeping systems.
Once traditional knowledge is documented and maintained as records, the challenges are not focused so much on the technology itself, but rather on how to leverage technology in order to ensure that access permissions are managed appropriately.
Every First Nation will need to determine what types of cultural information may be made available to whom, and when. Categories of sensitive cultural information are being identified in KNC policy with input from Nation members and Elders.
The Ktunaxa Nation Council places great importance on effectively managing its information resources and has been working towards a corporate-wide Records and Information Management Program over the past decade. Early commitment to information management began in 1997 when the Ktunaxa Nation Archives was established to support treaty negotiations.
As the official repository for all KNC inactive records with enduring value, the Archives operates in close connection with the Records and Information Management Program. The Archives contains KNC business and Ktunaxa cultural records that date back to pre-Confederation in 1867. The Archives provides access services by appointment during regular business hours. Research requests are typically received from KNC staff and contractors, community members, as well as authors, students and lawyers. The Archives has a request process in place that is guided by an Access and Use Policy and related procedures.
Active recordkeeping activities within offices reflect a hybrid environment, with staff typically relying on electronic documents for convenience, while treating paper records as “official” records. Staff tend to rely on their email systems and shared network drives for storing and accessing records. The challenge with these practices is that records are not necessarily available to others in KNC who need to access the information.
To improve the systematic control of KNC records, an electronic document management system has been in use since 2007 to store and access important KNC records across the organization, including Council meeting records, resolutions, executed agreements, policies, Traditional Use Studies, and transcribed interviews with Ktunaxa members. Security permissions are applied to the folder structure to ensure appropriate protection of sensitive and confidential business and cultural information. A project is currently underway to replace the system with a comprehensive electronic document and records management system (EDRMS) that will have robust records management functionality while being focussed on providing a positive end-user experience.
Digitization efforts have been led by the Ktunaxa Nation Archives and the Records and Information Management Program, although all KNC employees are able to scan documents on demand using optical character recognition (OCR) software from desktop scanners and multi-purpose printers. The majority of users send scans via email or save them to shared drives, while key records are saved to the electronic document management system.
The business and cultural records of KNC, like other First Nations, are intimately linked and cannot be physically separated into strict “business” and “cultural” categories.
Since recorded information is stored in various physical and electronic places, including offices, email systems and networked file shares, intellectual control is the key to managing KNC’s records. Finding aids, such as box inventory lists, are vital to identifying and locating records stored across the organization. Access to the finding aids is generally restricted to records staff due to confidentiality and privacy.
In order to accurately and effectively manage the records of a First Nation, the Archivist and/or Records Manager must be well informed of the content and context of the records. At the Ktunaxa Nation Council, sensitive cultural information is closely guarded and not necessarily shared with all Ktunaxa members. For instance, certain songs, dances and ceremonies are believed to cause physical harm to a person when provided out of context or at the wrong time. It is imperative to listen to the First Nations community with respect to the types of information that must be protected, and when it may be disclosed.
Overview of the Disputed Project
Supported by foreign investors, the Pheidias Project Management Corporation of Vancouver, BC, submitted a proposal to the Province of British Columbia in 1991 to convert 6000 hectares of public land into a year-round, permanent, European style ski resort in the remote Jumbo Valley.2
A map of the project location with a design image of the proposed resort is provided below.3



The Jumbo Valley area is adjacent to the Purcell Wilderness Conservancy Park and is currently devoid of year-round road access. The project intends to replace the existing helicopter skiing access with a network of 23 ski lifts across four glaciers at an elevation of 3,400 metres, which are indeed moving. Limited construction has been completed to date, with concrete slabs for the day lodge placed in a known avalanche path.4
In this case, the location of the proposed Jumbo Glacier Resort project is the central issue of the dispute. The Jumbo Valley site was originally identified in the 1982 Federal-Provincial study entitled “The BC Rocky Mountain Tourism Region” as one of the two locations that would be suitable for destination ski resorts in the East Kootenays.5 Consultation with the Ktunaxa Nation was not part of the study.
The Ktunaxa Nation is not generally opposed to development within their Traditional Territory and actively collaborates with government and industry. In this particular case, however, the Ktunaxa have been steadfastly opposed to the proposed Jumbo Glacier Resort project since its inception for ecological, cultural and spiritual reasons.
Qat’muk (pronounced “got-mook”) is the Ktunaxa name of the lands in the central part of the Purcell Mountains that include the area of the proposed Jumbo Glacier Resort. The location is at the core of the territory of the Ktunaxa Nation and is the home of Grizzly Bear Spirit, which is a unique and indispensable source of collective as well as individual guidance, strength and protection. For the Ktunaxa, the importance of Qat’muk for Grizzly Bear Spirit is indivisibly linked with its importance for living grizzly bears, now and into the future. 6
Since the project was proposed in 1991, the Ktunaxa Nation chose to withhold detailed spiritual information regarding Qat’muk and to rely largely on scientific findings to support their position to oppose permanent development in the Jumbo Valley. Various studies were conducted regarding the potential impact to grizzly bear populations, biodiversity and water quality as a result of the Jumbo Glacier Resort project development.7 According to Kathryn Teneese, “The science was already saying the project was wrong and shouldn’t proceed. We didn’t think we needed to divulge our intimate spiritual beliefs, too.”8
Unfortunately, the Ktunaxa have been criticized for not sharing their spiritual information in detail from the outset.
As consultation with the Province continued through the 2000s, discussions tended to focus on finding “common ground” with the Ktunaxa Nation regarding the proposed ski development. Although the Ktunaxa Nation is completely opposed to permanent development in the Jumbo Valley, the Province and the Proponent tried to mitigate the proposed Jumbo Glacier Resort development by reducing the overall size of the proposed resort. Missing the point that the location, not size of the resort, is at issue, the Ktunaxa Nation decided that it was time to share their intimate spiritual beliefs to protect the home of Grizzly Bear Spirit.
Early in 2009, a Ktunaxa Chief came forward to share his recent experience with the Grizzly Bear Spirit with provincial decision makers. The Ktunaxa Nation formally requested a meeting with the Premier, who declined the invitation. In September of that year, a small number of Ktunaxa members and KNC staff, met with Cabinet Minister Krueger and his Deputy Minister in confidence. Chief Luke shared his story completely in the Ktunaxa language and an interpreter was present to provide an English translation. It seemed to the Ktunaxa that the Minister was sympathetic to Ktunaxa beliefs and felt optimistic that meaningful negotiations would continue.9
Shortly afterwards, a Provincial Cabinet shuffle occurred and Minister Thomson replaced Minister Krueger as the Minister of Tourism, Culture and the Arts. In attempts to continue strengthening the relationship between the Ktunaxa Nation and the Province, the Ktunaxa Nation invited the new Minister to visit Cranbrook and meet with the Ktunaxa Nation. In 2011, Chief Luke shared his same story nearly word-for-word in Ktunaxa with Minister Thompson in confidence, with assistance from the same Ktunaxa interpreter.10
Disappointingly, Minister Thomson approved the Master Development Agreement with the Proponent the following year and construction was permitted to begin in the Jumbo Valley. Absolutely no mention was made to Ktunaxa spirituality or to Section 2 Charter rights in the Minister’s decision to approve the Agreement. As a result, the Ktunaxa Nation initiated legal proceedings against the Ministry in the BC Supreme Court.
A brief chronology of key events from 1991 to present is provided for reference in the appendix at the end of the case study. The key activities and decisions serve to illustrate the different perspectives between the Ktunaxa Nation and the BC Provincial government regarding land development and meaningful consultation over the past three decades.
Legal Context
The Canadian legal system is based on case law. Some important precedents have been set for First Nations by the Delgamuukw and Tsilhoqot’in Supreme Court of Canada cases, to name only a couple. A number of excellent sources have explored these cases in detail, and only a high-level discussion will be provided here.
In Delgamuukw v. British Columbia, the Court gave greater weight to oral history of the Gitxsan and Wet’suwet’en people than to written evidence. Despite this determination, oral history was confined to the evidence phase only.11
The Tsilhoqot’in v. British Columbia case broke new legal ground when the Court awarded aboriginal title to Indigenous Protected Areas spanning 1750 sq. km in the British Columbia interior. This decision recognized broad aboriginal ownership to general areas and is not “site specific.” 12
On the surface, these decisions seem to provide strong legal precedents that would support the Ktunaxa Nation in their opposition to permanent development in Qat’muk. In reality, Canadian case law and common law have proven to be inadequate mechanisms for addressing aboriginal rights and spiritual beliefs.
The intrinsic dichotomy between predominantly Western and Indigenous ideology as it pertains to the Canadian legal system has been described as follows:
There are wide cultural gulfs between what Canadian law courts and aboriginal laws most trust. In Canadian courts, there is a heavy reliance upon sworn firsthand accounts, facts established by scientific methodology, probabilities demonstrated by statistical surveys, interpretations of the wording of textual business records, and the opinions of expert professionals. Canadian legal culture prefers that transactions be substantiated by signed and dated documents. It mistrusts hearsay. It is no surprise to Canadian courts when its witnesses, who promise God to tell the truth, lie. Most Canadians live in a predominantly literate and visually-oriented culture and their courts reflect this focus by their dependence on written proof and eyewitness testimony.13
Oral traditions are fundamental to the way First Nations document the past and interpret the present. They are integral to understanding Aboriginal Rights and Title. It is a collective responsibility amongst First Nations Chiefs, Elders and citizens to learn oral traditions, such as laws, stories, songs and dances, and to transmit that knowledge to next generations. Credibility and respect are given to oral traditions as accounts are told and retold, challenged and reconfirmed by First Nations community members throughout the centuries. Sadly, “when presenting traditional aboriginal evidence in Canadian courts, the system for creating the evidence is at odds with the system charged with evaluating it.”14
The general reliance on written documentary evidence over oral traditions in court is greatly concerning for First Nations. In addition to having their traditional knowledge and beliefs recorded in an affidavit and dismissed as hearsay, the many writings of early anthropologists, historians and even early government officials, often include significant errors and continue to perpetuate misinformation. Moreover, most aboriginal oral traditions must be translated in order to be admitted as evidence in court, where much of the meaning is lost in the process. Serious consideration must be given to oral traditions within the legal context in order for First Nations to participate equally in court.
Regardless of the potential legal implications, the Ktunaxa Nation is actively documenting oral traditions as a mechanism for retaining and transmitting traditional knowledge. Meetings with the Elders Advisory Committee, for example, are being digitally recorded to preserve the invaluable information provided by Elders. The recordings are stored on a dedicated server with restricted access by Traditional Knowledge and Language staff. Potential uses of the information include developing language curriculum and Ktunaxa cultural publications, as well as providing documentary evidence to support the Ktunaxa in defending aboriginal rights.
Supreme Court of Canada Case
The Ktunaxa Nation have put on record through the consultation process and with the BC Supreme Court, the BC Court of Appeal and the Supreme Court of Canada, the clear history of opposition to the proposed Jumbo Glacier Resort based principally on the probable effects of the project on foundational Ktunaxa spiritual and cultural values.15
After four years of litigation in the British Columbia court system, the Ktunaxa Nation petitioned for their case to be heard in the Supreme Court of Canada. On December 1, 2016, the Ktunaxa Nation made their mark on Canadian legal history by bringing the first Indigenous Spirituality and Freedom of Religion case in Canada.
Despite significant public support, the Ktunaxa Nation was unsuccessful at arguing that the Minister’s 2012 decision to allow the Glacier Resorts project to proceed violates their right to freedom of conscience and religion protected by s. 2(a) of the Canadian Charter of Rights and Freedoms. This claim was asserted independently from the
Ktunaxa’s s. 35 claim, in which aboriginal rights to practice its religion are recognized and affirmed in the 1982 Canadian Constitution Act (Section 35(1)).16
The Supreme Court’s position can be illustrated using the following consecutive excerpts from the November 2, 2017 “landslide decision”:
…This case is not concerned with either the freedom to hold a religious belief or to manifest that belief. The claim is rather that s. 2(a) of the Charter protects the presence of Grizzly Bear Spirit in Qat’muk. This is a novel claim and invites this Court to extend s. 2(a) beyond the scope recognized in our law.17
We would decline this invitation. The state’s duty under s. 2(a) is not to protect the object of beliefs, such as Grizzly Bear Spirit. Rather, the state’s duty is to protect everyone’s freedom to hold such beliefs and to manifest them in worship and practice or by teaching and dissemination. In short, the Charter protects the freedom to worship, but does not protect the spiritual focal point of worship…In this case, however, the appellants are not seeking protection for the freedom to believe in Grizzly Bear Spirit or to pursue practices related to it. Rather, they seek to protect Grizzly Bear Spirit itself and the subjective spiritual meaning they derive from it. That claim is beyond the scope of s. 2(a).18
It would seem that the Supreme Court Justices misunderstood the Ktunaxa Nation’s argument. The Ktunaxa were not seeking protection for the freedom to believe in Grizzly Bear Spirit or to pursue practices related to it. Rather, they sought to protect Grizzly Bear Spirit itself and the spiritual meaning derived from it. It is impossible for the Ktunaxa to separate Qat’muk from the Grizzly Bear Spirit. If this claim is beyond the scope of s.2(a) of the Charter, what hope does any First Nations have to protect their sacred areas from destruction in the name of development?
In the words of Kathryn Teneese, Ktunaxa Nation Chair, “With this decision, the Supreme Court of Canada is telling every indigenous person in Canada that your culture, history and spirituality, all deeply linked to the land, are not worthy of legal protection from the constant threat of destruction.”19
Legal counsel for the Ktunaxa Nation, Karenna Williams of Grant Huberman, goes on to say that:
The Ktunaxa people have been private or “secretive” with their spiritual beliefs. This is both because of what is called for within their own religious beliefs, and because it is was required in order for the Ktunaxa people and the Ktunaxa religion to exist within Canada. Sharing information with the Provincial government, beginning a judicial review, appearing before the Supreme Court of Canada with this most personal, secret, and sacred information showed a great deal of faith on the part of the Ktunaxa. The willingness to expose the most sacred part of what it means to be Ktunaxa was not taken lightly. The Ktunaxa did so with the hope that the Court would, earnestly, and in good faith, see them. Hear them. The majority’s decision shows clearly that the Ktunaxa people were alone in their efforts to meet the Court and other Canadians halfway. It shows a profound failure for the Court to see the Ktunaxa people at all, let alone as people whose values and beliefs deserve respect and protection under the Charter of Rights and Freedoms.20
On the plus side, two dissenting Judges noted an inextricable connection between land and spiritual beliefs. This small comfort to the Ktunaxa Nation may yet prove to be an important legal instrument for other First Nations in Canada, as new law tends to be built on dissenting decisions.
Lastly, it is interesting to note that a significant volume of Ktunaxa Nation records was provided in electronic form. The nine Supreme Court Justices, with assistance from each of their three Clerks, referenced the responsive records entirely in paper during the hearing. From a technological perspective, the answer to the “Are we there yet?” question as it pertains to the Canadian legal system is clearly “no.”
Conclusion
Through this case study, the Canadian court system has demonstrated that it is an inappropriate mechanism for resolving First Nations issues that are central to Aboriginal identity and beliefs. In the spirit of reconciliation, it is sincerely hoped that Justices will become more willing to acknowledge and define inherent Aboriginal rights within the scope of s. 2(a) of the Charter going forward into the future. Without the willingness to acknowledge different perspectives of truth, reconciliation cannot happen.
At the time of writing this article, the Supreme Court of Canada released a decision regarding the Proponent’s case against British Columbia. To add insult to injury to the Ktunaxa Nation, the Justices confirmed that the former Minister of Environment’s 2015 decision to not renew Jumbo Glacier Resort’s Environmental Assessment Certificate was “unfair.” The current Minister must now review the evidence associated with Minister Polak’s decision, which happened to be the only provincial decision that was sympathetic to Ktunaxa spiritual values and rights.
Kathryn Teneese expressed the Ktunaxa Nation’s disappointment in response to the Supreme Court decision as follows:
The irony of the situation is not lost on us…In the past, the courts went to great lengths to try to justify the Province’s failure to even consider the Ktunaxa right to freedom of religion under the Charter of Rights and Freedoms regarding this ski resort. For the developer, however, the court was more than willing to cancel the Province’s decision because something wasn’t apparently adequately addressed in the Province’s decision.21
Although the legal phase of the Ktunaxa journey to protect Qat’muk may be over, the Ktunaxa Nation will remain firmly opposed to any permanent development in the Jumbo Valley area. Like other Aboriginal people in Canada, the Ktunaxa have extensive oral traditions. Language and culture is deeply rooted in the land. The critical work that is being done at the Ktunaxa Nation Council will continue, including calling upon the Crown to act in the spirit of the Truth and Reconciliation Commission’s “94 Calls to Action”, finalizing the Qat’muk Stewardship Plan, and digitally capturing traditional knowledge as important information assets of enduring value to the Ktunaxa Nation.
Appendix: Chronology of Key Events
The following chronology summarizes the key events surrounding the proposed Jumbo Glacier Resort project in the Jumbo Valley. The source of the chronology from March 1991 to March 2012 is Ktunaxa Nation v. British Columbia (Forests, Lands and Natural Resource Operations), Application for Leave to Appeal to the Supreme Court of Canada, which was accepted by the SCC on October 1, 2015.
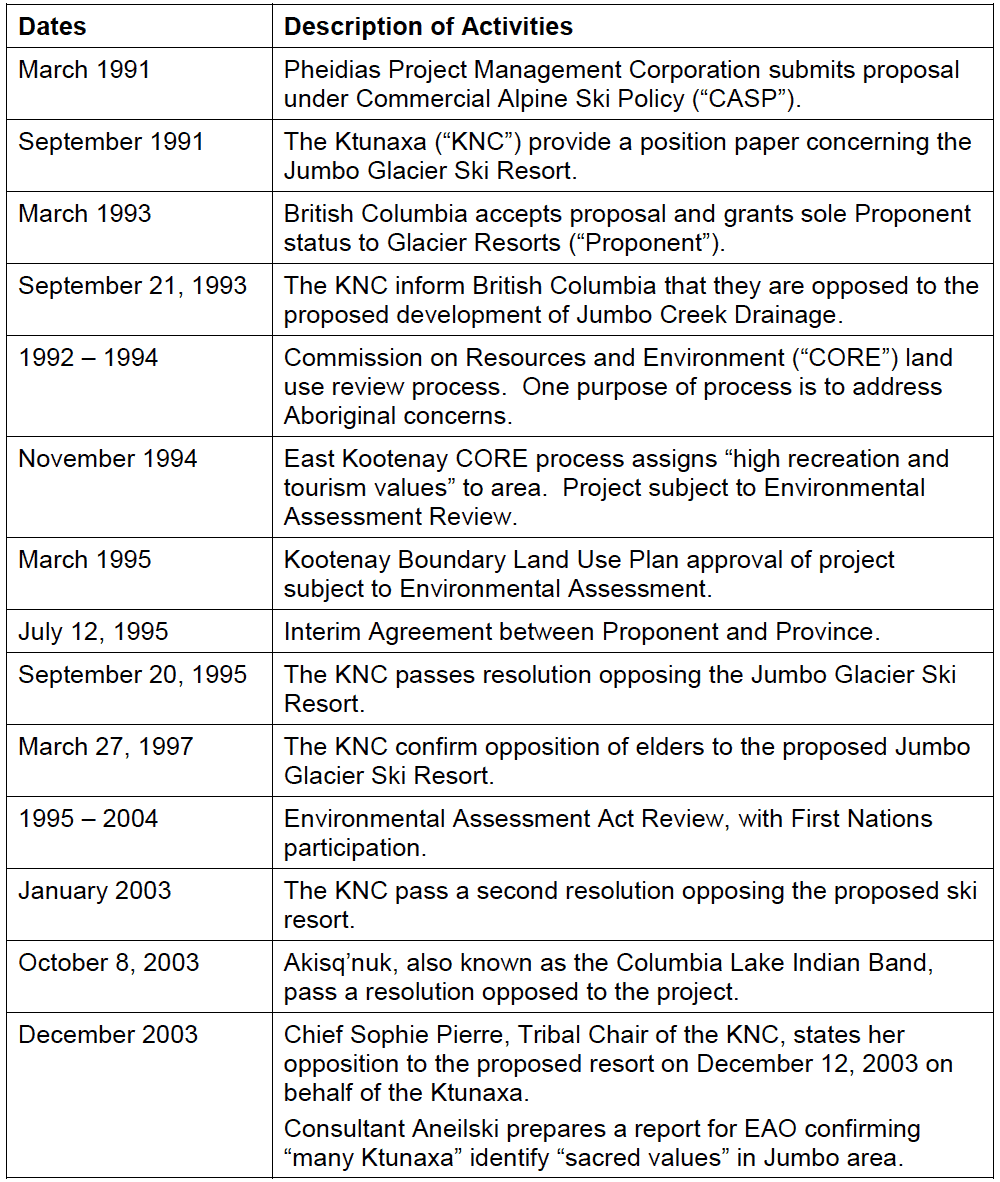



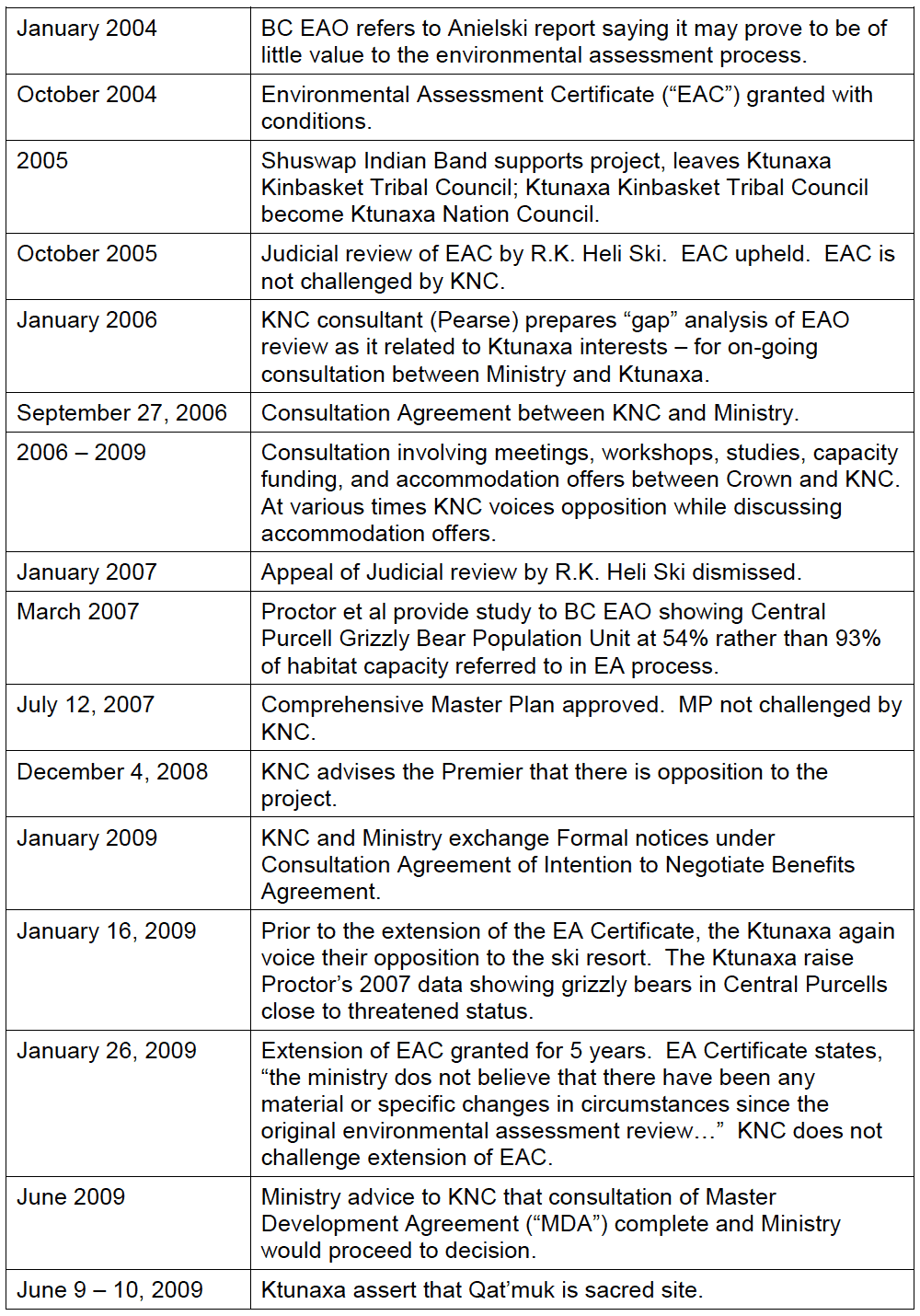



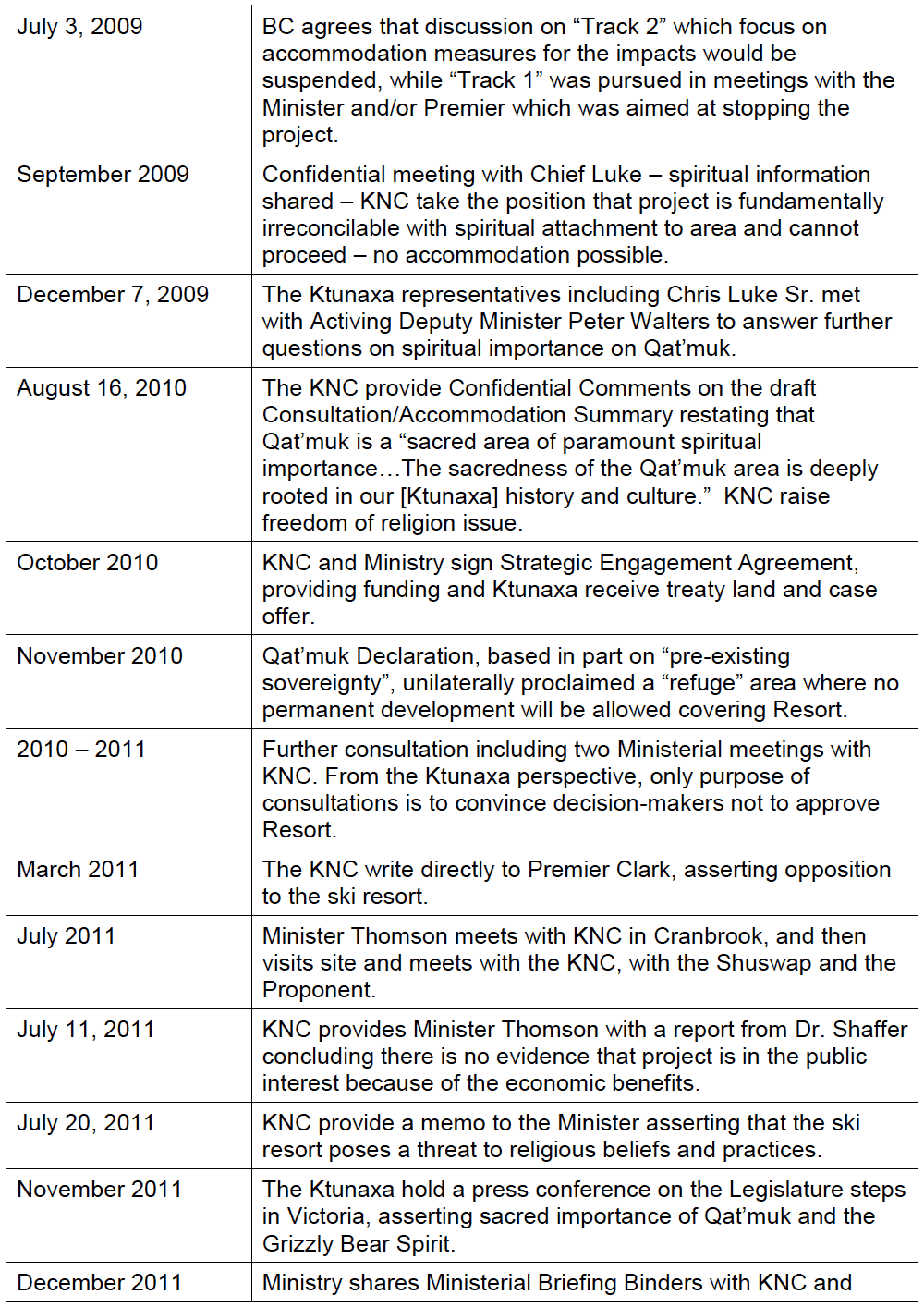



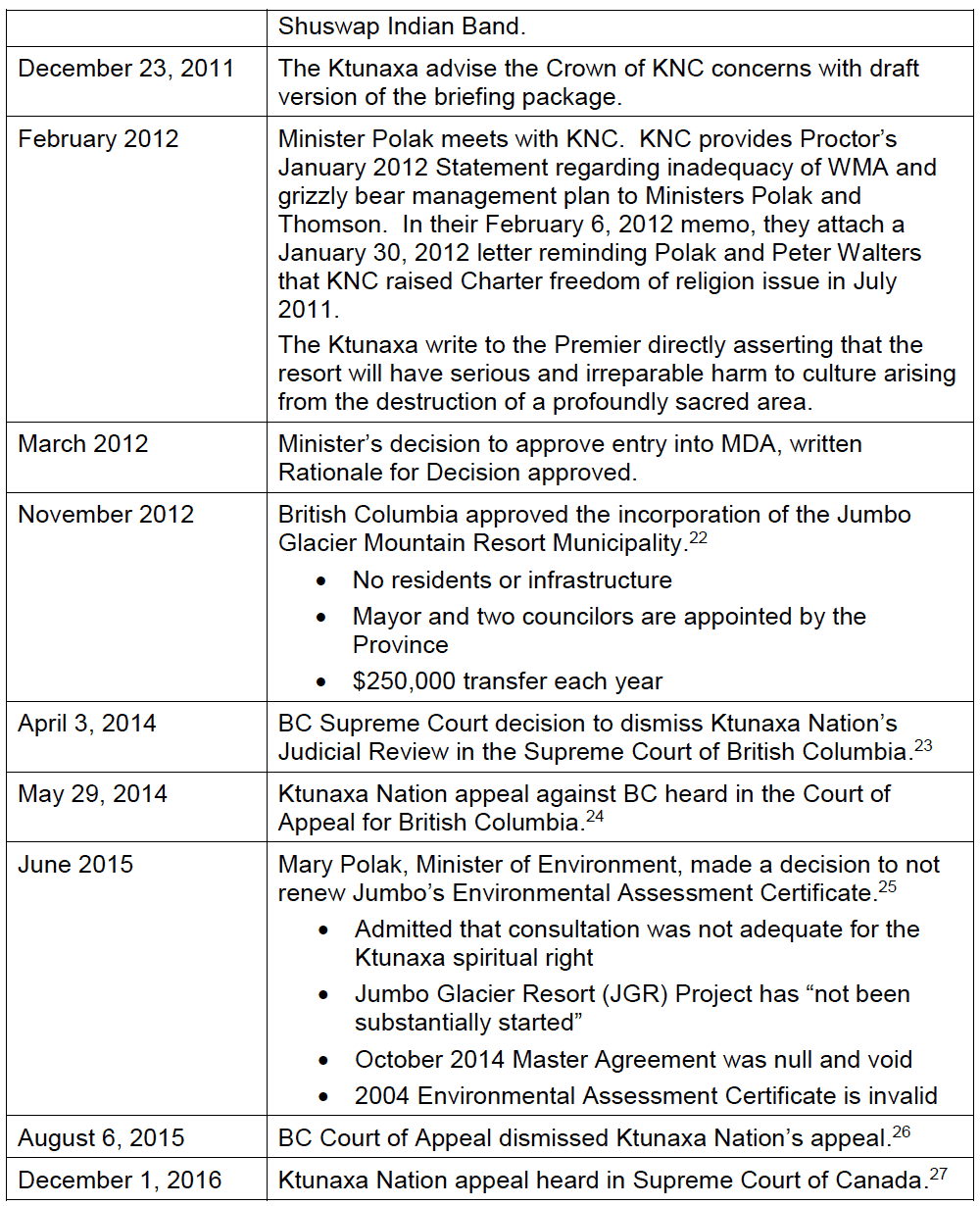







Works Cited
British Columbia. BC Gov News. Jumbo Becomes Mountain Resort Municipality. 20 November 2012. Web. 23 August 2018.
British Columbia. BC Gov News. Jumbo Glacier Resort Project Not Substantially Started. June 18, 2015. Web. 23 August 2018.
British Columbia. Minister of Environment. Reasons for Ministers Determination In the Matter of a Substantially Started Determination under Section 18(5) of the Act for the Jumbo Glacier Resort Project of Glacier Resorts Ltd. 18 June 2015.
Delgamuukw v. British Columbia. [1997] 3 S.C.R. 1010. Supreme Court of Canada. Web. 23 August 2018.
Glacier Resorts Ltd. v. British Columbia (Minister of Environment), 2018 BCSC 1389.
Supreme Court of British Columbia. Web. 23 August 2018.
Ktunaxa Nation Council. Media Release: Ktunaxa Nation Disappointed with BC Supreme Court Ruling. [Cranbrook, B.C.] 21 August 2018.—–. Qat’muk Declaration. [Cranbrook, B.C.] 2010.
Ktunaxa Nation v. British Columbia (Forests, Lands and Natural Resource Operations).
Application for Leave to Appeal to the Supreme Court of Canada. 2015.
Ktunaxa Nation v. British Columbia (Forests, Lands and Natural Resource Operations).
Court of Appeal for British Columbia. 2015 BCCA 352.
Ktunaxa Nation v. British Columbia (Forests, Lands and Natural Resource Operations).
Supreme Court of British Columbia. 2014 BCSC 568.
Ktunaxa Nation v. British Columbia (Forests, Lands and Natural Resource Operations), 2017 SCC 54. Supreme Court of Canada. 2017.
Pheidias Project Management Corporation, Jumbo Glacier Alpine Resort: Project Proposal Outline. [Vancouver, B.C.] 1995.
Pylypchuk, Mary Ann. The Value of Aboriginal Records as Legal Evidence in Canada: An Examination of Sources. Archivaria 32, Summer 1991.
Skimap.org. Jumbo Mountain Resort: Trail System for the Resort. 2000. Web. 23 August 2018.
Teneese, Kathryn. Correspondence. [Cranbrook, BC] [Provincial Government] 18 September 2017—–Personal Interview. 4 April 2017—–. Personal Interview. 19 June 2018.
Tsilhqot’in Nation v. British Columbia. 2014 SCC 44, [2014] 2 S.C.R. 256. Supreme Court of Canada. Web. 17 August 2018.
Williams, Karenna. Correspondence. [Vancouver, B.C.] [Kathryn Teneese] 2 November 2017.
1Driving time between Invermere and Creston is approximately 4 hours, with Cranbrook located roughly in the middle. Grasmere is approximately 1 hour from Cranbrook to the southeast.
2Pheidias Project Management Corporation, Jumbo Glacier Alpine Resort: Project Proposal Outline, 1995.
3Skimap.org, Jumbo Mountain Resort, 23 August 2018.
4The concrete foundation of the day lodge was the only construction completed prior to the provincial government’s Environmental Assessment Certificate deadline in 2014. See Minister of Environment, Reasons for Ministers Determination In the Matter of a Substantially Started Determination under Section 18(5) of the Act for the Jumbo Glacier Resort Project of Glacier Resorts Ltd 18 June 2015.
5Ibid., p. 5.
6Qat’muk Declaration, 15 November 2010.
7See Appendix.
8Kathryn Teneese, Personal Interview, 4 April 2017.
9Ibid.
10Ibid.
11See Delgamuukw v. British Columbia [1997] 3 S.C.R. 1010.
12See Tsilhqot’in Nation v. British Columbia, 2014 SCC 44, [2014] 2 S.C.R. 256.
13Mary Ann Pylypchuk, Value of Aboriginal Records, Archivaria 32 (Summer 1991), p.66.
14Ibid., p. 52.
15Kathryn Teneese, correspondence 18 September 2017.
16Ktunaxa Nation v. British Columbia (Minister of Forests, Lands and Natural Resource Operations), Supreme Court Judgement [58].
17Ibid, [70]
18Ibid, [71]
19Ktunaxa Nation Council, Media Release, 2 November 2017.
20Karenna Williams, correspondence to Kathryn Teneese, 2 November 2017.
21Ktunaxa Nation Council, Media Release, 21 August 2018.
22BC Gov News, Jumbo Becomes Mountain Resort Municipality, 20 November 2012.
23Ktunaxa Nation v. British Columbia (Forests, Lands and Natural Resource Operations), 2014 BCSC 568. 24 Ktunaxa Nation v. British Columbia (Forests, Lands and Natural Resource Operations), 2015 BCCA 352. 25 BC Gov News, Jumbo Glacier Resort Project Not Substantially Started, 18 June 2015.
26Ktunaxa Nation v. British Columbia (Forests, Lands and Natural Resource Operations), 2015 BCCA 352.
27Ktunaxa Nation v. British Columbia (Forests, Lands and Natural Resource Operations), 2017 SCC 54.
28Ibid.
29Glacier Resorts Ltd. v. British Columbia (Minister of Environment), 2018 BCSC 1389
Politique relative aux messages électroniques et son adoption Par Barb Bellamy, CRM et Anne Rathbone, CRM.
Introduction
Les politiques établissent sur papier les comportements et les objectifs attendus des employés d’une organisation. Une politique ou une directive n’est que le début de la démarche. Pour être efficace, une politique nécessite des standards, des règlements et des procédures la supportant, afin d’appliquer les exigences nécessaires. La politique relative à la gestion des messages électroniques est une des plus difficiles à mettre en œuvre et appliquer. Le défi réside en la perception que chaque individu auquel a été assigné un compte de messagerie électronique en possède le contenu. Afin de vraiment convaincre chaque personne, une politique claire et concise doit être créée et appuyée par l’équipe de gestion. Ce qui n’est pas surprenant. Ce qui peut être surprenant par contre, est comment appliquer une politique qui a de telles implications personnelles sur les individus.
La mise en œuvre d’une politique relative aux messages électroniques requiert une approche personnalisée; avec de l’information qui est perçue comme étant personnelle, une approche personnalisée est nécessaire. L’utilisation de slogans, d’images et de ludification n’est qu’un exemple de personnalisation de la formation et de la mise en œuvre d’une politique relative aux messages électroniques. Mais la mise en œuvre ne se termine pas avec la formation. Il faut aussi faire le suivi pour s’assurer de la compréhension et du respect de la politique par chaque employé. Cette étape est critique afin de pouvoir démontrer le respect de la politique relative aux messages électroniques, en cas de besoin. La surveillance et les mises à jour sont également des étapes cruciales dans le développement et la mise en œuvre d’une politique pour chaque organisation, mais elles ne seront pas décrites dans le présent article.
Exigences des politiques relatives aux messages électroniques
Par où commencer lors de la création d’une politique relative aux messages électroniques? La publication (doc) d’ARMA International intitulée « Mise en œuvre de la politique relative aux messages électroniques »1 est une excellente source d’informations, et l’annexe A offre 20 suggestions de dispositions de politique relatives aux messages électroniques. Mais ce ne sont pas toutes ces dispositions qui devraient être incluses dans une politique; celles qui seront choisies dépendront de l’organisation.
Exemples de dispositions suggérées :
- Des objectifs et une portée clairement définie, de même pour les rôles et responsabilités, dans le but d’approuver, de mettre en œuvre et de réviser le processus de la politique.
- Un énoncé établissant que les messages électroniques appartiennent à l’organisation, peuvent être considérés comme des documents légaux et sont donc sujets aux politiques et procédures réglementant les archives et l’information.
- Une liste de toute autre politique, procédure ou directive concernant les messages électroniques, ainsi que toute loi ou règle applicable à la gestion des archives de l’organisation.
- Le droit de l’organisation à effectuer une surveillance et à réglementer l’utilisation et la transmission de messages électroniques, ainsi qu’une clarification des droits à la vie privée que l’employé pourrait
- Une explication de la façon dont les messages électroniques seront utilisés en cas de différend.
Le développement de la politique requerra la participation de plusieurs parties, incluant les services juridiques, des ressources humaines, de la gestion de l’information, de la technologie de l’information et toutes les unités opérationnelles. Donc, il est recommandé d’affecter un comité ou une équipe à la politique relative aux messages électroniques. La haute direction doit approuver la politique et s’assurer que l’importance du respect de la politique est communiquée à tout le personnel.
Exigences d’archivage
Une politique relative aux messages électroniques doit inclure les exigences quant à la sauvegarde; si votre organisation a une politique de sauvegarde ou d’élimination, il faudra inclure une référence à cette directive, politique ou à ce standard. Les exigences d’archivage sont déterminées et maintenues par le service de gestion de l’information et des archives, et doivent respecter toute exigence légale ou professionnelle, ainsi que tout règlement du secteur ou du gouvernement. La politique doit s’appliquer à tout message électronique envoyé ou reçu par l’organisation et indiquer quels messages électroniques doivent être conservés, la durée de leur archivage et dans quels emplacements ils doivent être conservés.
Un des aspects les plus importants de l’archivage est l’automatisation — les messages électroniques devraient être retirés du système de façon régulière et sans intervention manuelle. Cette automatisation élimine le risque d’erreur humaine, ce qui diminue significativement la responsabilité de l’entreprise. L’automatisation doit inclure des mesures de contrôle installées afin de tenir compte de tout différend en attente, ou archivages de l’information avant l’élimination de quelque message électronique que ce soit. Une méthode d’archivage des messages électroniques peut vous aider à vous conformer à une politique d’archivage des messages électroniques automatisée.
Aux États-Unis, les exigences d’archivage des messages électroniques fait désormais partie intégrante des politiques relatives aux messages électroniques en 2006, lorsque les règles fédérales de procédures civiles (règles fédérales) ont été révisées afin d’inclure toute information électronique2, même si l’archivage des messages électroniques était déjà partie intégrante de plusieurs programmes de gestion de l’information. La règle 34 des règles fédérales établit que « tout document désigné ou toute information archivée électroniquement — y compris les textes, dessins, graphiques, tableaux, photographies, enregistrements sonores, images ou toute autre donnée ou compilation de données — enregistrée sur quelque média que ce soit, depuis lequel de l’information peut être obtenue soit directement ou, si nécessaire, suite à une traduction par la partie répondante en un format raisonnablement utilisable ». Les règles fédérales sont des règlements qui déterminent les procédures pour les poursuites civiles dans les tribunaux fédéraux des États-Unis. Elles ne font pas partie de la loi canadienne fédérale, provinciale ou territoriale, mais peuvent avoir le pouvoir de persuasion.
Le règlement général sur la protection des données (RGPD), qui a été approuvé en avril 2016 et est entré en vigueur en mai 2018, est un règlement de la loi de l’Union européenne (UE) sur la protection des données et de la vie privée pour tout individu dans l’UE et la région économique européenne. Le RGPD s’applique à toute organisation ayant une présence établie dans l’UE, qui offre des biens et services aux individus dans l’UE, ou qui effectue une surveillance du comportement des individus dans l’UE. Le RGPD a également exercé une pression sur les organisations canadiennes faisant affaire et échangeant de l’information avec l’UE; les messages électroniques jouent un rôle significatif lors de ces échanges.
Le RGPD stipule que « Les données personnelles peuvent seulement être conservation légales et traitées le temps nécessaire à la réalisation d’un but précis. Ceci nécessite une estimation prudente du délai adéquat de conservation des messages électroniques archivés, renforçant ainsi la nécessité d’une politique d’archivage des messages électroniques qui est concrète et complète »3.
Échantillon de Politique relative aux messages électroniques
Il est souvent utile de consulter les politiques relatives aux messages électroniques des autres organisations afin de voir s’il y a des éléments qui pourraient être inclus dans votre propre politique. Vous trouverez ici-bas un échantillon de dispositions d’une politique relative aux messages électroniques provenant d’un organisme public.
Politique
La messagerie électronique (messages électroniques) est l’une des façons les plus utilisées de communication entre les employés de [Organisme public], et entre le [Organisme public] et le public. Les messages électroniques, comme toute autre archive créée et reçue par le [Organisme public], sont des documents officiels.
La politique sur la gestion de la messagerie électronique fournit une direction générale au sujet de la possession, l’organisation, l’archivage et la protection des messages électroniques conservés dans les comptes de messagerie électronique de [Organisme public].
But
Le but de la politique sur la gestion des messages électroniques est d’assurer que les messages électroniques ayant une valeur durable pour le [Organisme public] demeurent disponibles afin de satisfaire toute exigence légale, commerciale ou en matière de responsabilisation, et d’assurer la suppression régulière de messages électroniques n’ayant qu’une valeur transitoire.
Général
Le [Organisme public] se réserve le droit, sans le consentement de l’utilisateur, de surveiller, examiner, copier, archiver, envoyer et révéler le contenu des messages électroniques, spécialement en rapport avec toute enquête, procédure légale, inconduite professionnelle ou demande sous la Loi sur l’accès à l’information et la protection de la vie privée.
Les employés doivent s’assurer que la réponse automatique d’avis d’absence est en fonction et qu’elle contienne le nom de la personne à contacter en cas d’absence prolongée.
Les règles usuelles de courtoisie doivent être respectées lors de l’utilisation du système de messagerie électronique du [Organisme public], selon les Directives et politique du réseau de technologie de l’information.
Les comptes de messagerie électronique d’employés ne travaillant plus auprès de [Organisme public] seront supprimés du système six (6) semaines après le dernier jour de travail dudit employé. Il est de la responsabilité du supérieur de l’employé qui quitte de s’assurer que les messages électroniques ayant une valeur durable demeurent disponibles et conservés dans les archives du système de gestion des archives et des documents électroniques.
Propriété
Tout compte de messagerie électronique est la propriété de [Organisme public] et est fourni à l’employé afin de faciliter la conduite des affaires de [Organisme public].
Les comptes de messagerie électronique peuvent être utilisés à des fins personnelles durant les périodes de temps non rémunérées, selon les Directives et politique du réseau de technologie de l’information.
Les employés n’ont aucun droit personnel ou exclusif sur les messages électroniques et les pièces jointes contenues dans les comptes de messagerie électronique de [Organisme public].
Conserver et archiver
Les messages électroniques de valeur durable pour le [Organisme public] seront :
• archivés selon le calendrier d’archivage de l’organisme;
• disponibles, suivant les restrictions de sécurité, et conservés aux archives de [Organisme public];
• ne seront pas conservés dans la boîte de réception ou sur un disque dur personnel de l’employé.
• une date d’échéance de deux (2) ans sera imposé à tout élément de compte de messagerie électronique. Les messages électroniques datant de plus de deux ans seront automatiquement supprimés.
Les messages électroniques envoyés à l’interne de [Organisme public] seront archivés par l’émetteur. Ceci inclut les messages envoyés et les réponses.
Les messages électroniques reçus de sources externes seront archivés par le destinataire. Si plus d’un employé est le destinataire, le premier employé sur la liste de destinataires conservera le message.
Protéger et sécuriser
L’accès au système de messagerie électronique de [Organisme public] est réservé aux employés et aux membres du conseil d’administration ayant reçu un compte de messagerie électronique.
Toute information confidentielle d’une tierce partie reçue par l’entremise du système de messagerie électronique du [Organisme public] devra être protégée de divulgation, d’utilisation ou de changement non autorisé ou accidentel.
Les signatures personnelles numérisées ne devront en aucun cas être utilisées dans les messages électroniques. Cette mesure protège contre leur utilisation de façon frauduleuse ou inappropriée.
Éliminer
Les messages électroniques transitoires seront gardés pour le temps nécessaire afin de remplir les exigences légales, commerciales ou en matière de responsabilisation.
La politique citée est un bon exemple de politique relative aux messages électroniques comme point de départ. Elle fournit une direction claire sur ce à quoi la politique se rapporte; les documents créés et reçus par le [Organisme public] sont des documents officiels. Le but est clair; les messages ayant une valeur durable restent disponibles afin de répondre aux exigences légales, commerciales ou en matière de responsabilisation, et d’assurer l’élimination régulière des messages électroniques. La politique omet de préciser l’information nécessaire aux employés afin de déterminer ce qui constitue un document officiel et ce qui constitue de l’information transitoire.
La section sur la propriété n’indique pas clairement « qui » ou « quoi » est le propriétaire du compte de messagerie informatique ou de son contenu. En cas de découverte, de qui est-ce la responsabilité de geler le(s) compte(s); l’employé, le supérieur ou tout autre fonctionnaire de l’organisation? Normalement, cette décision devrait être prise dans le cadre des activités générales de mise en suspens pour des raisons juridiques et être définie dans une politique de mise en suspens pour des raisons juridiques et ses documents de processus.
La section d’archivage et de conservation légale est très claire à propos des règles d’archivage et de suppression dans le cadre de la gestion des messages électroniques. « Une date d’échéance de deux (2) ans sera imposée sur tout élément de compte de messagerie électronique. Les messages électroniques datant de plus de deux ans seront automatiquement supprimés. » est un concept très intéressant, rarement mis en œuvre par les organisations. Sans propriétaire établi, qui est-ce qui applique cette politique?
Le gouvernement du Canada a un cadre de politique très utile qui regroupe tous les directives, politiques et standards en une vision unique4. Ceci permet aux employés d’avoir une compréhension globale du traitement de l’information en tant qu’atout. La gestion des messages électroniques n’est qu’un des standards utilisés lors de la gestion des archives et de l’information critique au sein du gouvernement du Canada5.
Formation et engagement des employés
La première étape de tout programme de formation est d’obtenir la compréhension et l’engagement des employés. Pour ce qui est de la gestion des messages électroniques, la formation est une étape critique à la mise en œuvre. Il est difficile de faire accepter aux employés la notion que les messages électroniques puissent être considérés comme étant des documents officiels et qui appartiennent à l’organisation, et non à l’individu qui les a créés ou reçus. Simplement leur fournir la politique et leur demander de la lire n’est pas suffisant. Une formation devrait permettre aux employés de comprendre la politique elle-même et de sa nécessité, ainsi que les connaissances pratiques pour l’utilisation de la technologie, des outils et d’autres ressources utiles afin de se conformer à la politique. Malgré que les périodes d’orientation ou de processus d’intégration soient des moments appropriés à la présentation de la politique aux employés, la formation continue peut aider à inculquer le besoin de conformité ainsi que rafraîchir la mémoire aux autres employés sur tous les aspects de la politique.
Inclure quelques activités amusantes dans la formation peut augmenter l’engagement des employés et pallier le fait que les employés progressent à des vitesses différentes.
Quelques idées pouvant être incluses dans la formation :
Garder ou éliminer :
Donner à chaque employé entre cinq et dix messages électroniques — un mélange de messages transitoires et archives. Les employés doivent les classer selon ce qu’ils veulent garder ou ce qu’ils veulent éliminer, dans un laps de temps donné. Ensuite, discuter des décisions de l’employé.
A, B ou C :
Donner à chaque employé trois cartes marquées A, B et C. Après avoir passé en revue la politique relative aux messages électroniques, poser des questions à choix multiples au sujet des dispositions incluses dans la politique. Remettre un prix à l’employé ayant eu le plus de réponses exactes. Par exemple :
À qui appartiennent les messages électroniques reçus dans le cadre de votre travail?
A. Vous — c’est votre nom sur le message électronique.
B. Votre organisation
C. Votre superviseur
Mots croisés ou mots cachés :
Créer un mot croisé en utilisant des termes de la politique. Le remettre aux employés pour qu’ils le terminent dans un laps de temps donné. Remettre un prix à l’employé ayant terminé le mot croisé en premier.
Jeopardy :
En utilisant des catégories en rapport avec la politique relative aux messages électroniques, les responsabilités des employés et la détermination de quels messages sont considérés des archives, les employés doivent fournir les questions aux réponses données. Par exemple :
Dans la catégorie « Archive ou transitoire », afficher la réponse « Un rendez-vous 2 semaines plus tôt » devrait entraîner la question « Qu’est-ce qu’un document transitoire? »
Thèmes :
Terminer la formation avec différents thèmes. Par exemple :
Avril est désigné comme étant le mois des archives et de l’Information chez ARMA. Lier l’évènement avec une activité de ménage de printemps des comptes de messagerie électronique des employés.
Sudoku:
Utiliser le mot « Complying » (se conformer) afin de créer un jeu de Sudoku6 — cette idée est empruntée au Centre des sciences marines et de la Côte Pacifique — faisant partie du sondage géologique américain.
Êtes-vous conforme à notre politique relative aux messages électroniques? Essayez de résoudre le jeu de Sudoku ici-bas. Chaque grand carré de 9 petits carrés doit contenir le mot
« COMPLYING ». Il en est de même avec chaque ligne et chaque colonne. Pouvez-vous compléter le puzzle afin que chaque grand carré ait toutes les lettres de « COMPLYING » sans répéter la même lettre, pour chaque grand carré, ligne ou colonne?
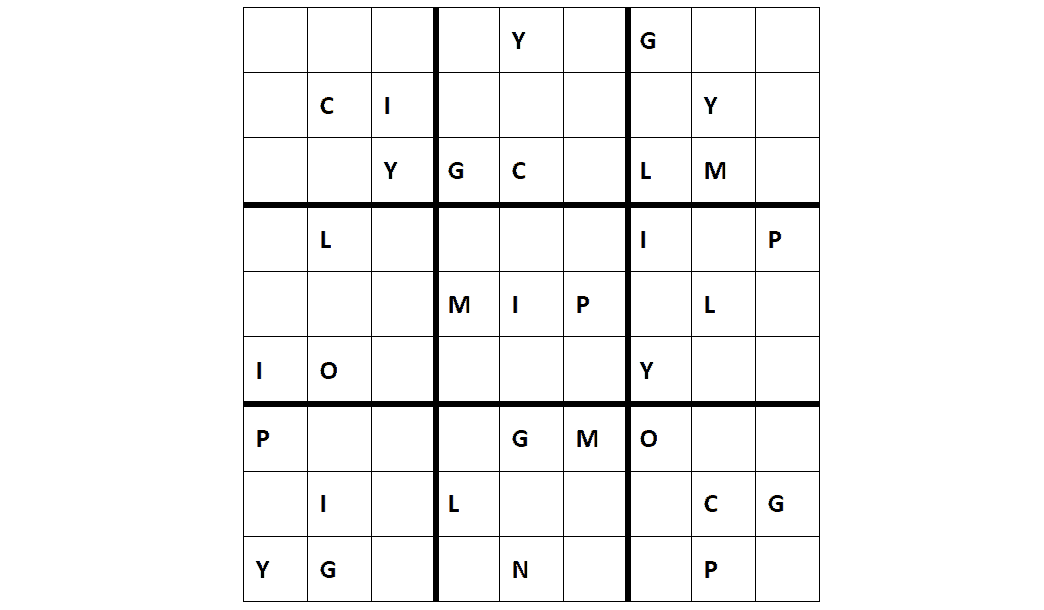



Création d’image de marque
BusinessDictionary.com définit la création d’image de marque (branding) comme étant « Le processus impliqué en créant un nom et une image unique pour un produit dans l’esprit du consommateur, principalement grâce à des campagnes publicitaires ayant un thème constant. La création d’image de marque a pour but d’établir une présence significative et différenciée sur le marché, qui attire et garde une clientèle loyale. »7
La création de votre marque peut être une autre méthode pour inciter la participation de vos employés et de susciter de l’enthousiasme envers la mise en œuvre de la politique. Demandez aux employés de soumettre des idées et remettez un prix à la personne avec la proposition gagnante.
Quelques exemples de création d’image de marque pour une politique sont :
- The biggest loser (Le plus grand perdant)
- Please be a tosser (S’il-vous-plaît soyez jeteur)
- Control your records before they control you (contrôlez vos archives avant qu’elles ne vous contrôlent)
- To keep or not to keep … that is the question (garder ou ne pas garder… telle est la question)
- Know when to hold’em, know when to throw’em (sachez quand les garder, sachez quand les jeter)
- If you purge it, they will come (si tu les éliminent, ils viendront)
- RM is the only profession that knows in advance what it is going to forget (La “RM” est la seule profession qui sait en avance ce qu’elle va oublier)
- Keep the Corporate memory — forget the clutter (garder la mémoire corporative — oubliez le désordre)
- Email is a communication tool, not a filing cabinet! (Les messages électroniques sont un outil de communication, et non pas un classeur à dossiers!)
Utilisez l’image de marque gagnante comme outil de marketing afin de promouvoir la politique. Par exemple, le thème « Know when to hold’em, know when to throw’em » pourrait avoir une image de bateaux de jeux sur le Mississippi ou du Far West. Un parieur ou un cowboy pourrait en être la mascotte. La chanson « The Gambler » de Kenny Rogers pourrait jouer lors de l’entrée des employés pour la formation. Les jeux suggérés dans cet article pourraient être renommés pour faire partie du thème.
Certaines organisations ont même créé des vidéos amusants utilisant leur marque afin de publiciser leur politique relative aux messages électroniques et d’expliquer aux employés leur responsabilité à ce sujet. Imaginez le plaisir à avoir en utilisant le thème « Know when to hold’em » lors de la création d’un vidéo.
Malgré que la création d’images de marque n’ait pas encore été utilisée pour mettre en œuvre une politique relative aux messages électroniques, le Sunshine Coast Regional District a utilisé cette technique pour la mise en œuvre de leur programme de gestion des documents électroniques et des archives, Dr Know. Ils ont utilisé un savant fou comme icône. La formation est faite dans le laboratoire de Dr Know, les employés ayant complété avec succès leur formation sont appelés des « Je-sais-tout », et ceux qui ont reçu une formation spécialisée sont appelés les « spécialistes ». La formation avait aussi un thème — la formation d’introduction était appelée « Apprendre à connaître Dr Know » et la formation avancée « Obtenir vos résultats de la part de Dr Know ». Les jours fériés ont également servi dans le cadre de la formation, par exemple la Saint-Valentin (Bee My Record), Pâques (les collections de Pâques de Dr Know), la rentrée scolaire (retour à l’école, retour à la base) et les vacances estivales (MOJITO – Managing Our Jobs using Information To Our Advantage). La création d’images de marque et le marketing peuvent être très efficaces — il suffit d’un peu d’imagination.
Sommaire
Les politiques sont des règles ou directives créées lors d’un processus d’affaires spécifique. Elles sont des instructions formelles applicables à l’ensemble de l’organisation qui doivent être respectées par chaque individu dans l’organisation. Le non-respect de ces politiques peut entraîner des mesures disciplinaires. Il est essentiel à la bonne mise en œuvre de toute nouvelle politique d’avoir l’approbation de la haute direction.
Les politiques sont le bon mécanisme afin de faire parvenir votre organisation à sa destination; s’assurer que l’information est traitée comme un atout, et archivée ou éliminée selon les règles que vous déterminez. Il y a une courbe d’apprentissage qui peut ne pas sembler naturelle à vos employés au départ, lors du déploiement d’une politique. La mise au point d’une politique claire et concise, qui explique qui, quoi, où, quand et pourquoi, est le point de départ. L’ajout de directives, de standards, de consignes et de procédures aidera à assurer la compréhension de la politique et son respect. Organiser des sessions de formation et créer une marque qui est amusante et stimulante sera attirant pour la plupart des employés et les incitera à respecter la politique. Le but ultime des politiques est d’avoir un bassin d’employés qui comprend et respecte les politiques de l’information déterminées par l’organisme, incluant les messages électroniques.
Il n’est pas suffisant pour les organisations de mettre en place la politique la mieux écrite. Elle doit également être capable d’attester de la formation qu’elles offrent, ainsi que démontrer, par les signatures et les performances des employés, qu’ils ont été formés et comprennent la politique et les conséquences de son non-respect. Ceci peut être accompli en signant une déclaration de complétion ou en réussissant un examen portant sur la gestion des messages électroniques. Cette attestation et certification est la preuve que les employés comprennent et respectent la politique relative aux messages électroniques; ces archives peuvent être utilisées lors de procès ou avec des régulateurs prouvant que l’organisation a fait son travail de façon assidue.
Les politiques doivent être révisées annuellement et, si nécessaire, actualisées ou réécrites. Si la politique est significativement modifiée, les employés doivent être avertis du changement et de la façon dont cela affectera leur rendement. Avec une formation appropriée et de la motivation, les employés utiliseront la politique relative aux messages électroniques et les documents qui y sont associés pour gérer leur compte de messagerie électronique comme prévu, créant ainsi une organisation plus forte et plus conforme.
Works Cited
1ARMA International, Implementing Electronic Messaging Policies TR31-2018 (Overland Park: ARMA International, 2018).
2https://www.cornell.edu/rules/frcp
3https://www.intradyn.com/email-retention-laws/
4https://www.tbs-sct.gc.ca/pol/doc-eng.aspx?id=12742
5https://www.tbs-sct.gc.ca/pol/doc-eng.aspx?id=27600
6US Geological Survey. Pacific Coastal and Marine Science Centre. walrus.wr.usgs.gov/infobank/programs/html/training/recordsmanagement/rmhumor.htlm
7http://www.businessdictionary.com/definition/branding.html
Email Policy and Adoption
by Barb Bellamy, CRM and Anne Rathbone, CRM.
Introduction
Policies establish in writing the expected behaviors and outcomes of an organization’s employees. A policy or directive is only the beginning of the journey. To be effective, a policy requires supporting standards, regulations and procedures to apply the necessary requirements. An email management policy is one of the toughest policies to implement and enforce. The challenge lies in the perception by each individual that has been assigned an email account that they own the contents. To truly get buy in from each individual, a clear and concise policy must be created and supported from the organization’s top management. This is not a surprise to anyone. What may be a surprise is how to implement a policy that has such intimate implications to the individual.
Email policy implementation requires a personalized approach; with perceived personal information, a personal approach is critical. Using catch phrases, branding and gamification are some examples of personalizing the training and implementation of an email policy. Your implementation does not end with the training. There is also the need to track that each employee understands and will follow the email policy. This step is imperative to prove compliance with the email policy should it ever be needed. Monitoring and refreshing are also critical steps in the policy development and implementation for each organization but will not be covered in this article.
Email policy requirements
Where to start when creating an email policy? ARMA International’s publication, “Implementing Electronic Messaging Policies”1 is an excellent resource and Appendix A provides 20 suggested provisions of an electronic messaging policy. Not all of the provisions would be included in an email policy. The provisions incorporated into a policy would depend on the organization.
Included in the suggested provisions are:
- A clearly defined scope and objectives, as well as the roles and responsibilities for approval, implementation and a review process of the
- A statement that emails belong to the organization, could be records and are therefore subject to the organization’s records and information policies and
- A list of any other organizational policies, procedures, or guidelines that address email as well as any applicable legislation or regulations that apply to management of the organization’s
- The organization’s right to monitor and regulate the use and transmission of email and clarifying what privacy rights the worker may
- A statement of how email will be managed during
Developing the policy will require input from a variety of stakeholders including legal, human resources, information management, information technology and all business units. Therefore, striking an email policy committee or team is recommended. Senior level management must approve the policy and ensure that the importance of complying with the policy is communicated to all staff.
Retention Requirements
An email policy must include retention requirements; if your organization has a Retention or Disposition policy include a reference to that directive, policy, or standard. Retention requirements are set and maintained by the Information / Records Management department and should comply with legal, business requirements, industry and government regulations. The policy must cover all emails sent or received by the organization and contain the guidelines for which emails should be kept, how long they are to be retained and where they are to be stored.
One of the most important aspects of the email retention is automation – emails should be removed from the system in a consistent manner without any manual intervention. This automation eliminates human error and decreases corporate liability significantly. The automation must have controls in place to account for any pending litigation or holds on the information prior to deleting any emails. An email archiving solution can help you to comply with an automating email retention policy.
In the United States, email retention requirements became part of email policy in 2006 when the Federal Rules of Civil Procedure (Federal Rules) were revised to include all electronic information2, although email retention was already part of many information management programs. Rule 34 of the Federal Rules states that “any designated documents or electronically stored information—including writings, drawings, graphs, charts, photographs, sound recordings, images, and other data or data compilations—stored in any medium from which information can be obtained either directly or, if necessary, after translation by the responding party into a reasonably usable form”. The Federal Rules are regulations that set out procedures for civil law suits within United States federal courts. The Federal Rules do not form part of Canadian, federal, provincial or territorial law but may have persuasive value.
The General Data Protection Regulation (GDPR) which was approved in April of 2016, and came into force in May 2018, is a regulation in the European Union (EU) law on data protection and privacy for all individuals within the EU and the European Economic Area. The GDPR applies to organizations with an established presence in the EU, which offer goods and services to individuals in the EU, or monitor the behavior of individuals in the EU. The GDPR has also put a burden on Canadian organizations that do business and exchange information with the EU; email plays a significant role in that exchange.
The GDPR stipulates that “Personal data can only be held and processed for as long as is necessary for a specific purpose. This necessitates careful consideration of how long archived emails need to be kept, further emphasizing the need for a concrete, thorough email retention policy.”3
Sample Email Policy
It is often useful to review other organizations’ email policies to see if there are elements that can be included in your policy. Below is a sample of a public body’s email policy.
Policy
Electronic mail (email) is one of the most extensively used forms of communication between [Public Body] employees and between the [Public Body] and the public. Email messages, like other records created and received by the [Public Body], are official records. The Policy on Electronic Mail Management provides direction on the ownership, organization, storage and protection of email messages stored within the [Public Body]’s email accounts.
Purpose
The purpose of the Policy on Electronic Mail Management is to ensure that email messages of enduring value to the [Public Body] remain accessible to meet legal, business and accountability requirements, and to ensure the regular disposal of email messages having only transitory value.
General
The [Public Body] reserves the right, without the consent of the user, to monitor, examine, copy, store, forward and disclose the contents of email messages, especially in relation to investigations, legal proceedings, professional misconduct and requests under the Freedom of Information and Protection of Privacy Act. Employees will ensure that their email “out of office” is turned on advising whom to contact during prolonged periods of absence. Common rules of etiquette will be followed when using the [Public Body] email system, per the Information Technology Network Policy and Guidelines. Email accounts of employees that are no longer employed at the [Public Body] will be removed from the system six (6) weeks after the employee’s last day of employment. It is the responsibility of the departing employee’s manager to ensure that email of enduring value remains accessible and stored in the Electronic Document and Records Management System (EDRMS) repository.
Ownership
All email accounts are the property of the [Public Body] and are provided to employees to facilitate the conduct of [Public Body] business. Email accounts may be used for personal use on personal time, per the Information Technology Network Policy and Guidelines. Employees do not have any personal or proprietary rights over email messages and attachments contained within [Public Body] email accounts. Upon request from the manager, custodial rights to email messages within an account of a former employee will be transferred to a current employee, usually the immediate supervisor.
Store and Retain
Email messages of enduring value to the [Public Body] will:
• Be retained following the [Public Body]’s retention schedule
• Remain accessible, based on security constraints, and will be stored in the EDRMS
• Will not be stored in an employee’s inbox or on a personal drive
• A date limit of two (2) years will be imposed on all email accounts. Emails older than two years will automatically be deleted.
Email messages sent within the [Public Body] will be saved by the sender. This includes the outgoing message and the responses. Email messages received from external sources will be saved by the recipient. If more than one employee is a recipient, the first employee on the recipient list will save the email message.
Protect and Secure
Access to the [Public Body]’s email system is limited to employees and Board members who have been assigned an email account. Sensitive third-party information received via the [Public Body]’s email system will be protected from unauthorized or accidental disclosure, use or alteration. Scanned personal signatures will not be included within email messages under any circumstances. This is to prevent their use in a fraudulent or inappropriate manner.
Dispose
Email messages that are transitory will be retained only as long as needed to meet legal, business and accountability requirements.
The policy above is a good example of an email policy as a starting point. It provides clear direction on what the policy pertains to; records created and received by the public body are official records. The purpose is clear; messages of enduring value remain accessible to meet legal, business and accountability requirements, and to ensure the regular disposal of email messages. The policy does lack the information required for employees to determine what is an official record and what is transitory information.
The ownership section does not clearly spell out “whom” or “what” is the owner of the email account and its contents. In the case of discovery, who is responsible for placing a hold on the email account (s), is it the responsibility of the employee, manager or someone other officer of the organization? Normally this decision would be made as part of the overall Legal Hold activities and be defined in a Legal Hold policy and process document.
The store and retain section is very clear regarding retention and disposition rules surrounding the management of emails. “A date limit of two (2) years will be imposed on all email accounts. Emails older than two years will automatically be deleted” is a very interesting concept that is not implemented by organizations often. Without a clear owner, who enforces this policy?
The Government of Canada has a very useful policy framework that ties all related directives, policies and standards into a single view4. This allows employees to get a holistic understanding of Information being treated as an asset. Email management is just one of the standards use to manage records and critical information at the Government of Canada.5
Training and Employee Buy-in
The first step in all training programs is to get the understanding and support of the employees. With email management, training is critical to the implementation. Having employees accept the concept that email can be a record and belongs to the organization, not to the individual who created or received it, is difficult. Simply providing them with the policy and asking them to read it is not adequate. Training should provide employees with an understanding of the policy itself, why it is necessary and how to use technology, tools and other resources in order to be compliant with the policy. While orientation or during the onboarding process are good times to introduce employees to the policy, ongoing training can help ingrain the need for compliance as well as providing a refresher to employees on all aspects of the policy.
Including some fun activities in the training can increase employee buy-in and may help to address the fact that employees have different learning needs.
Some ideas to include in the training are:
Keep or Toss:
Give employees five to ten emails – a mixture of transitory emails and records. The employees are to sort them into keep or toss piles, within a given time limit. Then discuss the employee decisions.
A, B or C:
Give each employee three cards marked A, B, and C. After reviewing the email policy, ask multiple choice questions about the provisions included in the policy. Have a prize for the employee with the most correct answers. For example:
Who owns emails received as part of your work duties?
A. You – it’s your name on the email.
B. Your organization
C. Your supervisor
Crossword Puzzle or Word Search:
Using terms from the email policy, create a puzzle. Give the puzzle to the employees and have them solve it, within a given time frame. Have a prize for the employee who solves the puzzle first.
Jeopardy:
Using categories relating to the email policy, employee responsibilities and determining which emails are records, players provide questions to the answers displayed. For example:
Under the Category, “Record or Transitory”, displaying an answer of “A meeting appointment 2 weeks out of date” would elicit the correct response of, “What is a transitory document?”
Themes:
Tie in the training with various themes. For example;
April is designated as ARMA’s Records and Information Month. Tie that in with spring cleaning of employee email accounts.
Sudoku:
Use the word “Complying” to create a Sudoku puzzle6 – this idea is borrowed from Pacific Coastal and Marine Science Centre – part of the US Geological Survey.
Are you “COMPLYING” with our Email Policy? Try completing the Sudoku puzzle below. Each large square of 9 smaller squares will contain all the letters in the word “COMPLYING”. All rows and columns will do the same. Can you complete the puzzle so each large square has all the letters in “COMPLYING” without repeating the same letter within a large square, row or column?



Branding
BusinessDictionary.com defines branding as “The process involved in creating a unique name and image for a product in the consumers’ mind, mainly through advertising campaigns with a consistent theme. Branding aims to establish a significant and differentiated presence in the market that attracts and retains loyal customer.”7
Creating your brand can be another method to engage your employees and create enthusiasm for the policy implementation. Ask employees to submit ideas and award a prize to the winning submission.
Some examples of branding email policies are:
- The biggest loser
- Please be a tosser
- Control your records before they control you
- To keep or not to keep…that is the question
- Know when to hold’em, know when to throw’em
- If you purge it, they will come
- RM is the only profession that knows in advance what it is going to forget
- Keep the Corporate memory – forget the clutter
- Email is a communication tool, not a filing cabinet!
Use the winning brand as a marketing tool to promote the policy. For example, the theme listed above “Know when to hold’em, know when to throw’em” could have an old riverboat gambler or old west slant to it. A riverboat gambler or cowboy could be used as a mascot. Kenny Rogers’ song “The Gambler” could be played when employees are arriving for training. The games suggested in this article could be renamed to incorporate the theme.
Some organizations have even created entertaining videos using their brand to publicize the email policy and to teach employees their responsibilities regarding the email policy. Imagine the fun that could be had using the “Know when to hold’em” theme when creating a video.
While branding has not yet been used for implementing an email policy, the Sunshine Coast Regional District did use this technique for their implementation of an electronic document and records management software, Dr. Know. They used a mad scientist as the icon. Training was done in Dr. Know’s laboratory, those who completed training were called “Know-it-all’s”, and those with in-depth training who could act as a resource within their departments were called “Specialists”. Training was also themed – the introductory training was called “Getting to Know Dr. Know” and advanced training was “Getting Your Results from Dr. Know”. Holidays have also been used for training, including Valentine’s Day (Bee My Record), Easter (Dr. Know’s Easter Collections), back to school (Back to School, Back to Basics), and summertime (MOJITO – Managing Our Jobs using Information To Our advantage).
Using branding and marketing tools can be very effective – all it takes is a little imagination.
Summary
Policies are rules or guidelines for a specific business process. They are formal organization- wide instructions that must be followed by everyone within the organization. Violation of policies may result in disciplinary action. It is critical to the implementation of new policies to have approval from top management.
Policies are the mechanisms to get your organization to its destination; ensuring that information is treated as an asset and retained or disposed of in accordance with your published rules. There is a learning curve that may not feel natural to employees at first while deploying an email policy. Creating a policy that is clear and concise, explains who, what, where, when and why is the starting point. Adding directives, standards, guidelines and procedures will help to ensure understanding of and compliance with the policy. Conducting training sessions and creating a brand that is fun and engaging will appeal to most employees and generate compliance to the policy. The ultimate goal of policies is to have a workforce which understands and follows the information policies set out by the organization including email.
It is not enough for organizations to put even the most well written policies in place. They must also be able to attest to the policy training they provided, as well as certify by employees’ signatures and performance that they have been trained and understand the policy and the consequences of violating it. This can be completed by signing a declaration of completion or passing a test on email management. The attestation and certification provides proof that employees understand and are to follow the email policy; these records can be used during legal actions or with regulators that the organization has done its due diligence.
Policies must be reviewed annually and, if necessary, refreshed or rewritten. If the policy is altered significantly, employees must be informed of the change and how it affects their performance. With proper training and incentives, employees will use the email policy and its supporting documents to manage their email accounts as expected, making for a stronger, more compliant organization.
Works Cited
1ARMA International, Implementing Electronic Messaging Policies TR31-2018 (Overland Park: ARMA International, 2018).
2https://www.cornell.edu/rules/frcp
3https://www.intradyn.com/email-retention-laws/
4https://www.tbs-sct.gc.ca/pol/doc-eng.aspx?id=12742
5https://www.tbs-sct.gc.ca/pol/doc-eng.aspx?id=27600
6US Geological Survey. Pacific Coastal and Marine Science Centre. walrus.wr.usgs.gov/infobank/programs/html/training/recordsmanagement/rmhumor.htlm
7http://www.businessdictionary.com/definition/branding.html
Thank you to John Bolton!
by Alexandra (Sandie) Bradley, CRM, FAI
John Bolton was a founding member of ARMA Canada’s Sagesse: Journal of Canadian Records and Information Management, Editorial Board, and a contributing author to the publication.
In early 2018, he retired from the Board, and his fellow members of the Board wish to thank him for his contributions and provide the following profile of his career and contributions to the records and information management community.
Biography
John was born in Oakland, California in 1950, and came to Canada with his family in 1954. He grew up in the Niagara Peninsula region of Ontario. He attended the University of Waterloo for his first degree in urban and regional geography, then attended Wilfred Laurier University to obtain an MA in geography.
Following graduation, he worked for the regional government of Niagara, creating maps for emergency management, and become the environmental lead in emergency response. In the fall of 1978, he moved west to Calgary, where he joined a division of Texas Instruments (TI), and worked in geotechnical seismic exploration. After a couple of years, he became a company troubleshooter, providing support and relief to company crews, travelling all over the world, working in both land and maritime environments.
After six years, he left TI, and was in the process of applying to the PhD program at the University of Alberta. However, conversations with a librarian let him to discover that he had been working with two sides of the triangle of information management: “the creation and gathering of information”, and “researching and using of information”. The librarian had suggested the missing piece was “the management of information”. To follow the management pathway, he could either go into the Information Technology (IT) field (just developing in the late ‘80s) or go to Library School. Knowing nothing about librarianship, he conducted his research the old fashioned way, using books and references, to discover that this profession could be a match for his interests. His future wife (Debbie) lived in Vancouver, so he applied and was accepted at the University of British Columbia, where he completed an MLIS in 1987. Among the courses he completed was a records management class, taught by Sandie Bradley. That introduced to John the “Life Cycle” concept, which supported his interest in the management of information and ultimately turned his career path toward records and information management.
RIM Career
When he graduated from UBC, he worked for Klohn Leonoff Engineering from 1987 to 1993 (and married Debbie!). During that time, he was manager of records and library services, and ultimately became the office manager before he left the firm. He obtained his CRM in 1995.
His RIM career continued when he joined the BC Government in 1994, as a records officer in the Ministry of Skills, Training and Labour. The British Columbia Freedom of Information and Protection of Privacy Act had been introduced in October, 1993, and he was immediately processing FOI requests. When asked by his manager to identify his career goals, John stated that he wanted his manager’s job. Two months later, his manager was gone, and John got his wish, becoming the FOI and Records Coordinator. With one assistant, he managed the flood of requests arising from the new legislation, plus the management of all of the ministry’s records.
A joint project between BC and the Government of Canada to manage the devolution of federal programs to the province led him to a sub-committee to develop an information sharing agreement. In 2001, he was head-hunted to join another Ministry, Human Resources, where he continued to review privacy issues, but also was doing more training and policy development. By 2004 he was spending so much time on new systems development, including the alignment of information privacy and security requirements to new computer technology that he was asked to join the IT department. The following year he joined a data warehousing project. As part of his training he completed a master’s level program in project management at the University of Victoria. From 2006 until his retirement in 2014, his title was Data Warehouse Architect, conducting business intelligence projects for the various ministry programs and working with the management of his ministry’s “big data”.
ARMA Involvement
John’s involvement with ARMA International started with he joined the Vancouver Chapter in 1988. He was immediately tagged the Membership Chair, and in in 1990-91, he was the treasurer of the first ARMA Canada conference held in Vancouver. He was also the CLARA representative. While an active member of the chapter, he also contributed a regular column “As I See It” to the chapter newsletter, offering his perspective on new trends or issues. He won the Chapter Member of the Year Award in 2000.
In 2003, he became a charter member of the Vancouver Island Chapter, when it was established as an independent chapter. His busy work life kept him on the sidelines of chapter activities for a number of years, although he was a speaker to students at UBC, and he presented a paper at the Mountain Pacific Region’s “Whining about Records” conference in Kelowna in 2010. In 2011-12, he was the co-chair for the ARMA Canada Conference hosted by the Vancouver and Vancouver Island chapters in Nanaimo.
Along the way, he got “goosed” in recognition for his service to the profession.
At the International level, he joined the Email Standards Task Force in 1997. From then until 2004 he served as a member of the Standards Development Committee, during the last year as Co-chair. During his time on the committee he was part of the review of both ISO 154891 and the US DoD 5015.02 standards2. Over his ARMA career John presented at numerous conferences and was a published author for ARMA.
Sagesse
Through his deep and abiding interest in professional research and scholarship, he was a founding member of the Editorial Board of Sagesse. He contributed not only to the structure and functions of the Board, but also helped to shape the early operations of the peer review process, and contributed his views on the quality and quantity of content. As a speaker and writer, he also presented his research on the decline of scholarly publishing by RIM professionals, and provided a joint workshop with fellow Board member Christine Ardern (Entitled “Getting Your Message Across in Writing”) offering encouragement for members to write for Sagesse. This presentation was provided at the ARMA Canada conference in Toronto, May 29-13, 2017.
Asked to describe his perspective on the RIM profession now that he is retired, he stated “Nothing is new, but issues always follow the swinging door of whatever is new”….He continues to see no new research or shifting of paradigms. In 2014 he addressed UBC students in a class where he put forth the idea that the records life cycle is a 500 year old paradigm now dead in view of the constant change within information technology. Hopefully there are researchers at work who can put forward the newer paradigm we need.
In recognition for his work in establishing Sagesse, John was awarded the ARMA Canada Region Distinguished Member Award in 2016.
The Sagesse Editorial Board, so grateful to John for sharing his perspectives and passion about information, and they also need to share additional thoughts:
Sandra Dunkin notes:
John has been an enthusiastic supporter of professionals new to RIM. Always available to give astute advice and guidance to those who need it. He has mentored CRM candidates with his unique perspective gleaned from both RIM practise and PMP training – invaluable tuition for anyone hoping to succeed on Part 6 of the CRM exam. He also offers endless encouragement to colleagues to progress not only in their career, but in the expansion of their professional development on broader topics that enhance RIM practise. John is one of those colleagues we all hope to encounter during our careers, his kindness and support have been of incalculable value to those who have had the great fortune to know him.
Stuart Rennie shares:
I first met John Bolton years ago at an ARMA Vancouver Chapter event where he was speaking. My first impression of John was that he was very intelligent, engaging and funny. Years later, we worked together as founding editorial board members at Sagesse, Journal of Canadian Records and Information Management. On the Sagesse board, John’s sage counsel was instrumental in getting us off the ground and publishing. We had many thought-provoking discussions about the RIM profession and publishing. For example, John taught me about concept of the “Hamburger” style of writing. Proper writing needs a top bun– a clear distinct opening; then filler–facts and evidence; finally, a bottom bun–a conclusion that wraps it all up. Tasty AND fun!
Uta Fox adds:
Being a member of Sagesse’s Editorial committee with John was a delight and education. While working through articles the Editorial committee were considering as publish-worthy he habitually referred to himself as the “curmudgeon” of the group. John’s exceptional “eye” immediately spotted misplaced commas that changed meaning, or inconsistent sentence structures or an argument that did not address the focus of the article. With his mastery of grammar, punctuation and sentence structure, he was also an expert on developing logical arguments whether it was addressing RIM theory or its practical aspects; he demonstrated the same zest for expression.
I urge readers to re-read John’s article in Sagesse’s first issue in 2016 entitled “A Content Analysis of Information Impact: Professionalism or Not – a Critical Twenty-Five Year Review” available on the ARMA Canada website: www.armacanada.org. You’ll see how he weaves the concept of RIM as a profession (is it or isn’t it?), with content analysis, the value of a theoretical foundation for RIM, improving Canadian authorship and addressing RIM from the Canadian perspective. His article is brilliant, the insights viable and valuable and so much food for thought provided (and not just the hamburger type!). Thank you, John for your participation and assistance in promoting the Sagesse publication. You set the bar high and we accept the challenge.
John Bolton’s contributions to the RIM profession have shaped Sagesse in focus and content. Thank you and well done!
Works Cited
1ISO/TR15489-1. Information and Documentation – Records Management – Part 1: General. First Edition, ISO, 2001. ISO/TR15489-2. Information and Documentation – Records Management – Part 2: Guidelines. ISO, 2001.
2United States Department of Defense. Electronic Records Management Software Applications: Design Criteria Standard. April 25, 2007. http://jitc.fhu.disa.mil/cgi/rma/standards.aspx.
Are We There Yet?
Introduction to the SharePoint & Collabware Implementation at the First Nations Summit
Sandra Dunkin, MLIS, CRM, IGP
Records & Information Management Coordinator First Nations Summit
Sam Hoff
ECM Consultant Gravity Union
Introduction1
The topic of SharePoint and its use for records management has been of perennial interest in the records and information management (RIM) community since Microsoft first decided to enter the market with SharePoint in 2001. Through the various iterations of the SharePoint platform, Microsoft has endeavoured to provide records management capabilities both out of the box, through customizations, and more recently through third party add on applications to manage the compliance and automation of records classification and disposition. Numerous case studies and educational sessions have been offered by Microsoft and related third party add-on vendors as well as subject matter experts, like Bruce Miller. Each year information organizations such as ARMA International, ARMA Canada, the various ARMA Chapters as well as many other North American and international information management professional organizations, continue to offer SharePoint sessions as part of their education outreach. SharePoint remains a hot topic in the RIM industry with increasing market share as third party developers continue to evolve their applications to manage sophisticated RIM tasks. Many organizations are keen to provide multipurpose solutions for their business needs rather than investing in specialised software solutions for siloed RIM activities, making SharePoint an attractive alternative to expensive, specialised and often modular RIM software applications.
This case-study will give an overview of the SharePoint implementation project at the First Nations Summit (FNS), underlining lessons learned, missteps, failures and eventual successes. From the inception of the project, the FNS has endeavoured to create a multi-purpose solution to address the evolving needs of staff, executive and contractors in the daily routine of their work as well as addressing RIM requirements for their large volume of records. The challenges of change management, user training and adoption, various upgrades and the changing environment as users engage more actively with SharePoint will also be covered.
A few words about the First Nations Summit
The First Nations Summit is comprised of a majority of First Nations and Tribal Councils in British Columbia and provides a forum for First Nations in BC to address issues related to Title and Rights and treaty negotiations as well as other issues of common concern.
In October 1990, leaders of BC First Nations met with the Prime Minister of Canada and then with the Premier and Cabinet of British Columbia urging the appointment of a tripartite task force to develop a process for modern treaty negotiations in BC. The federal and provincial governments agreed and on December 3rd, 1990, the BC Claims Task Force was established by agreement of the Government of Canada, the Government of British Columbia, and representative leadership of First Nations.
Leaders from First Nations across British Columbia appointed three members to the BC Claims Task Force at a meeting called the First Nations Summit. Two members were appointed by the Government of Canada, and two by the Province of British Columbia. Following more than five and half months of deliberations, the 1991 Report of the BC Claims Task Force recommended that First Nations, Canada and British Columbia establish a new relationship based on mutual trust, respect and understanding – through political negotiations.
FNS Role
The FNS is an action and solutions oriented First Nations-driven organization. The Summit’s original mandate is to advance discussions with the governments of Canada and BC to support First Nations in conducting their own direct treaty negotiations with Canada and BC. The foundation for our mandate arises from:
- the tripartite 1991 BC Claims Task Force Report jointly developed by the First Nations, Canada and BC,
- the 1992 agreement to create the BC Treaty Commission as the independent body to “facilitate” treaty negotiations, and
- subsequent federal and provincial legislation and the First Nations Summit Chiefs resolutions implementing the 1992 agreement and establishing the BC Treaty Commission as a distinct legal entity.
Approximately 150 First Nations in BC participate in FNS assemblies to bring forward, discuss and provide political direction on issues of common concern.
In carrying out their mandate, the FNS does not participate as a negotiating party at any First Nations specific negotiations. Over time and through the collective decisions by First Nations Chiefs and leaders, as directed by resolutions, they have been instructed to take a leadership and advocacy role on the full range of issues of concern to First Nations, including negotiations and implementation issues of treaties, agreements and other constructive arrangements and day-to-day social and economic issues which affect First Nations.
A critical element of the Summit’s work includes identification of concrete steps to overcome negotiation barriers. In First Nations‐Crown treaty negotiations in BC, they are facing a number of process and substantive issues that pose significant challenges and must be overcome in order to reach treaties, agreements and other constructive arrangements.
Although the they remain committed to the made‐in‐BC approach to negotiations and to assisting First Nations in achieving full and comprehensive treaties as a primary objective, they fully respect and support decisions of any First Nation to enter into alternative agreements and other constructive arrangements to advance the interests and priorities of their respective nations.
FNS People
The executive of the First Nations Summit consists of a three (3) member political executive (FNS Task Group) and a two (2) member administrative executive (FNS Co-Chairs). Each member of the executive serves a three-year term upon election. The FNS currently has a permanent staff of ten who implement the mandate, as determined by resolutions passed by chiefs in assembly at First Nations Summit Meetings, which are held three times each year. They also partner with numerous other First Nation organizations, such as the BC Assembly of First Nations and the Union of BC Indian Chiefs to collectively work on issues of concern to BC First Nations.
FNS Information Management
As treaty negotiations are an ongoing activity, the bulk of the FNS’s records also remain active during the process, from the inception of the First Nations Summit in 1991 to the present. At the current rate of accumulation, the FNS will soon exceed their storage capacity. They have a large volume of paper records and are facing significant space limitations not to mention concerns regarding the structural integrity of the building and the increasing weight of their collections (they are on the 12th floor of an aging office tower).
The FNS also has a broad variety of collections – numerous types and formats of records, including typical paper records, meeting binders, verbatim transcripts, bound publications, as well as video tape and other formats. All of this content is historically and continuously important, informing current activities. However, until recently, this important collection of material was entirely unavailable offsite.
History of the Project
On December 5, 2007, the ARMA Vancouver Chapter hosted an educational event at the City of Surrey, BC, demonstrating the City’s pilot SharePoint implementation. This demonstration showcased the features and capabilities of the SharePoint Records Centre as well as the collaboration features inherent in the platform. At the same time, the FNS began to realize the accumulation of their records was accelerating beyond the capacity of existing storage units (various file, binder, video and library cabinets). They were looking for alternative solutions for the maintenance of their collections that would address the growth of physical records collections. The FNS recognized they would need to rely on digital records collections to address this growth.
After much research, consideration and investigation, the FNS subsequently purchased and began implementation of SharePoint 2007 in August 2009. They later upgraded to the new release of SharePoint 2010 the following year.
Initially the FNS attempted to install and operate SharePoint without any external support, however, they promptly realized that due to the complex nature of the software they would need additional, specialized assistance to succeed with their implementation. Therefore, the FNS hired a consulting firm to set-up SharePoint 2010 with native Records Centre capabilities and some customisations to meet their unique needs. Unfortunately, the consulting firm they hired did not have adequate knowledge of the SharePoint Records Centre or RIM compliance requirements. Ultimately, this project failed as the configuration and capabilities of SharePoint out-of-the-box did not provide satisfactory RIM compliance, structures and protocols out-of-the-box.
At the 2013 ARMA Canada Conference in Saskatoon, the FNS Records Manager participated in the two- day SharePoint pre-conference delivered by Bruce Miller. During this session, Mr. Miller strongly recommended a small number of third party add-ons for RIM in SharePoint to meet RIM compliance requirements. Following his session, the Records Manager sought out and watched demos of many third party RIM add-ons while at the conference and then met with representatives of these vendors following the conference.
The FNS eventually chose to purchase Collabware CLM. This decision was based on several factors, most importantly the in-place records management feature as the best solution for staff and existing workflows. They relaunched the project with the new SharePoint 2013 platform and Collabware in August 2013.
The FNS have taken a unique approach to SharePoint by ensuring Records Management compliance through Collabware was fully configured before any content was uploaded, and the SharePoint interface was functional and relatively intuitive for users. They also decided to invest significant time and effort to populate the SharePoint site before going live. They have, therefore, spent much of the last few years doing extensive conversion of legacy records in various formats and uploading this content into SharePoint to enhance the user experience when launched to staff. It was also determined that in order to facilitate the change management process they would need to provide sufficient materials to demonstrate the utility and functionality of SharePoint. Furthermore, they used this process to gain additional experience and proficiency with the uploading of records in SharePoint to be better able to assist when users have questions or concerns. This process has, therefore, allowed the development team to work through any ‘glitches’, or anomalies as they have encountered them, saving users the frustration of experiencing them unaided. As of the date of this article, the FNS has over 12,250 documents and several thousand hours of labour invested in the implementation.
A quick note about the network infrastructure
Back in 2009 the FNS initiated the SharePoint 2007 implementation using dedicated hardware – three physical servers to host SharePoint server, SQL server, and a sandbox for testing. All servers were hosted on site with internal static IPs.
By 2010, they had already begun the process of virtualizing the other server applications to facilitate maintenance, failover, and recovery processes – when upgrading to SharePoint 2010 all of the associated SharePoint server applications were subsequently virtualized.
As of June 2018, The FNS launched a new project to upgrade to SharePoint 20162, Collabware CLM v3.2, SQL Server 2017 and Office Online Server. This solution was built in a test environment parallel to the existing SharePoint 2013 implementation. Once the functionality of the new SharePoint 2016 platform had been confirmed SharePoint 2013 was shut down and the related Domain Naming System (DNS) records were updated to go live with the 2016 platform. The SharePoint 2016 implementation is now running within a virtualized environment with a total of four SharePoint-related servers.
It should be noted that the FNS continue to maintain all of their servers on premise due to proprietary, confidentiality, privacy and security concerns and lack of sufficient reliable and trustworthy cloud services within Canada and within British Columbia specifically. There remains a lack of transparency with respect to the exact location of user data on cloud server farms and insufficient Canadian owned and operated cloud services available. Most cloud options in Canada are owned by extraterritorial corporations, making the data potentially subject to foreign government search and seizure, specifically the provisions of the U.S. Patriot Act. At this time the cloud remains far too ambiguous with respect to ownership, jurisdiction and protection of data for the Summit to feel confident in placing their intellectual property in the cloud.3
FNS Goals
The FNS had several goals they hoped to achieve in adopting SharePoint in addition to Records Management:
- Resolution of the shared drive chaos;
- Elimination of redundant versions and copies of documents;
- Reduction of email clutter;
- Improved
Shared drive issues
Like many organizations, the FNS shared drives had grown out of control over the years. There are complex subjective folder structures which represent individual interpretations of the material and which are entirely indecipherable to coworkers and often to the staff member themselves over time. While attempts had been made to impose order on the shared drive, all attempts proved futile as staff resisted change and continued to work within their existing folder structures.
SharePoint Search has alleviated a great many challenges with respect to the shared drive – most significantly the indexing of the shared drive as an external repository and revealing the location of relevant records/documents in the complex folder structures.
Redundant copies
The proliferation of multiple redundant copies and numerous versions of individual documents has also proved to be a significant impediment to efficient workflow. These various versions and copies exist across numerous folders for various staff members, often appearing in more than one folder within a single staff member’s folder series. Rarely are the drafts, disparate versions or “old” copies deleted from staff folders, further complicating the identification of the authoritative document or record. These versions and copies are difficult to browse and almost impossible to search with common desktop search tools.
SharePoint allows staff to maintain a version history for each document. At any time, a document can be compared with and reverted to a previous version. This means that all staff can be working on and editing a single document without needing to save and merge multiple versions. Also, SharePoint enables multiple users to be actively editing a single document at once, again removing the need for more than one copy of the document.
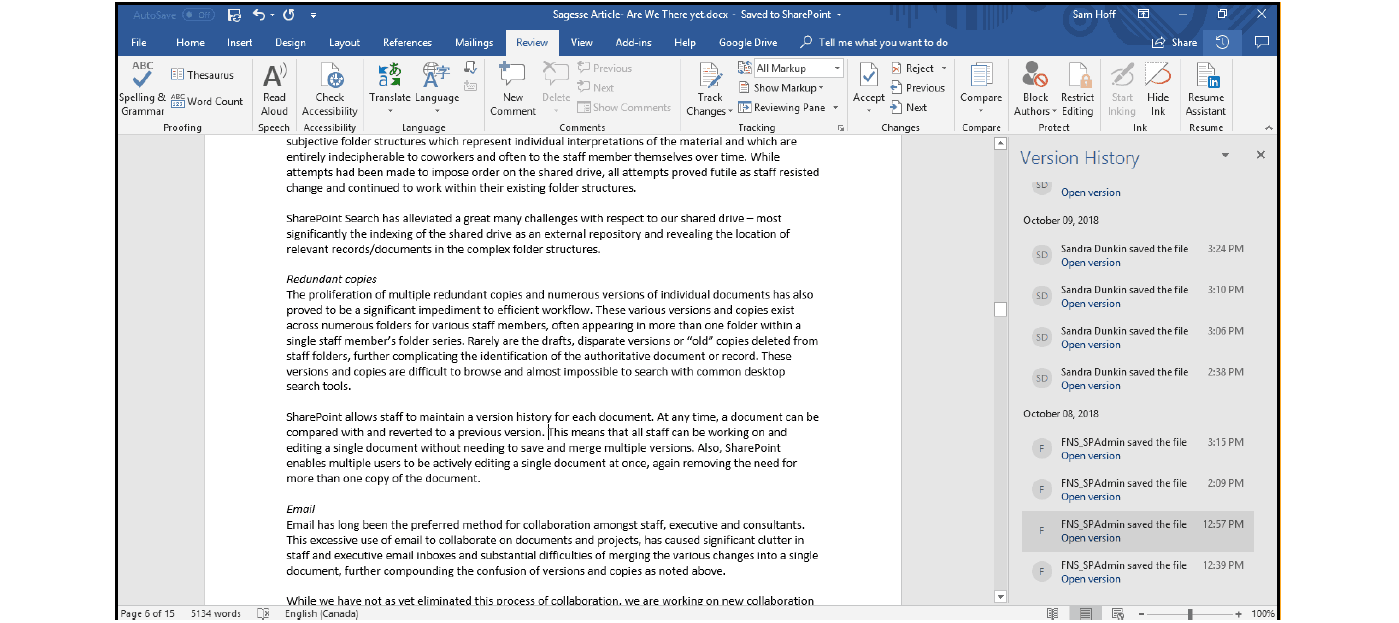



Email has long been the preferred method for collaboration amongst staff, executive and consultants. This excessive use of email to collaborate on documents and projects has caused significant clutter in staff and executive email inboxes and substantial difficulties of merging the various changes into a single document, further compounding the confusion of versions and copies as noted above.
While they have not as yet eliminated this process of collaboration, the FNS is working on new collaboration sites within SharePoint to address specific projects and staff objectives. They are hoping that staff will gradually migrate away from email to these ‘team sites’ to eliminate email clutter and excessive growth of email inboxes and secondary email folders.
Collaboration
Collaboration was another consideration – as described above, collaboration has been achieved through long email strings, resulting in disparate versions of a single document needing to be amalgamated. The FNS wanted to consolidate and streamline the versioning process to make collaboration more efficient. As a corollary to collaboration, they also sought to provide better access to additional content for stakeholders without geographic restrictions, more specifically, access to the historic treaty collections. The FNS are also hoping that increased engagement with SharePoint team sites will reduce the volume of disparate versions, with such evolving titles as “document-draft1”, “document-draft2”, “document- final”, and so on.
The FNS decided that their implementation would be engineered to have governance structures and protocols applied to the content up-front to limit, if not prevent, the proliferation of “free-range” content as with the shared drive. Rather than allowing end users to create content areas however they like, the core Records Management team is responsible for adding new content areas with user consultation, allowing them to maintain control and consistency.
The FNS also have the issue of older, stale-dated, content as software has been discontinued and the acceleration of software versioning has made older content no longer accessible – for instance they have a large volume of legacy WordPerfect documents but no longer use WordPerfect. They are currently engaged in a document conversion process to maintain these records and make them accessible within SharePoint. The bulk of these documents are being converted to .pdf format, uploaded into SharePoint and then deleted from the shared drive in a process to eventually eliminate the shared drive altogether.
Classification in the digital environment
The FNS began with their alphanumeric paper records classification of over 5000 categories, which is managed in a simple DBTextworks database for their paper records filing. This classification is very granular to assist efficient records retrieval. Obviously, they had to rethink how their classification scheme would transition into the digital environment.
FNS has a large set of metadata terms, enforcing standardized descriptions and organization as well as a ‘tags’ or ‘subject” folksonomy that users can contribute to, to further describe the records. By leveraging the power of metadata, they were able to reduce the total categories to an initial 96 ‘big buckets’ within which to organize their records. They have subsequently expanded these categories somewhat to allow for variations of retention and information capture.
Some of the key differences between a paper records-based file plan and an electronic records file plan are the use of record categories as metadata, physical limits on how many records can fit into an individual location, and security.
Metadata can be used to classify content, regardless of location
Compared to a paper filing system, where documents of a particular classification are typically filed together in the same physical location, in an electronic content management system, the location of content within the system does not need to be tied to its record category. Metadata on the documents can be used to correctly classify content no matter where it “lives”.
Classification does not need to be used as metadata
Since we are alleviated from tying the location of a document to its classification, there is also no need to break out into subcategories to allow for meaningful grouping of documents into manageable chunks. Many documents can reside in one single record category and use metadata to split them out however wanted. For example, rather than having a set of “by year” record categories, which are essentially using the record category to add metadata to the document, they can have a single category and use metadata in the system to separate the documents by year.
Many documents can reside in a single location
They are also much freer in terms of limits on volume. In the physical world, it may be painful to have thousands of records in a single category as it would become increasingly difficult to find any specific content within that classification. However, since the location and metadata are separated from the classification and retention in the electronic world, this is not a problem. There can be 200,000 records in a single classification that are spread out into multiple libraries in the system. Users are still able to find what they are looking for using metadata and search, much how most in the modern world use iTunes or Spotify to easily locate a single song in a database of millions.
Classification has been mostly decoupled from security, except for semi active content
While the above points free us in our use of Record Categories to simplify our file plan, security is a constraint that remains in the electronic records management world. In addition to SharePoint’s built-in security model, which allows us to define who can view and/or edit documents, we need to allow for a new case for semi-active records. If documents reach a point in their lifecycle when they are no longer relevant to users, they are sent to a repository so that they are retained as needed but are not cluttering up the document libraries that people are using to locate relevant documents. How physical content is classified in certain categories may be retained together in locked cabinets or rooms, we enforce security by classification for semi-active content. The result is that all content in a given classification will have the new security applied to it once it is moved to a repository, regardless of what the security of the individual items was during their active stage.
Retention in the digital environment
The FNS also leveraged Collabware’s automation capabilities for their retention policies. Through the development of workflows, using the visual workflow editor, they have created a workflow set that more precisely reflects the lifecycle of their records and they have applied these workflows throughout the collection using Content Rules applied to custom content types. Content Rules are a feature in Collabware CLM that allows the system to identify, classify, and declare records automatically through the use of rules. These rules are able to identify the correct records by the use of unique combinations of Content Types applied to libraries and metadata entered by users or provided by the documents.
An example of a content rule may be: “All Documents that are of Content Type Meeting Document, that are PDFs and have Final selected by a user as their status.” In this example, the combination of the type of content as well as the metadata provided by a user, can be used to automatically classify this document as a Record in the correct Record Classification without any direct action by the end user.
They may not even be aware it has occurred, as they were simply following their business process for adding documents to the system.
Once classified, content will follow the flow of the lifecycle management workflow associated to each Record Category. Many actions and flows are possible. Some examples are that a document can be locked down, have different security applied, be sent to a repository, go through a review process, and have a final disposition action.
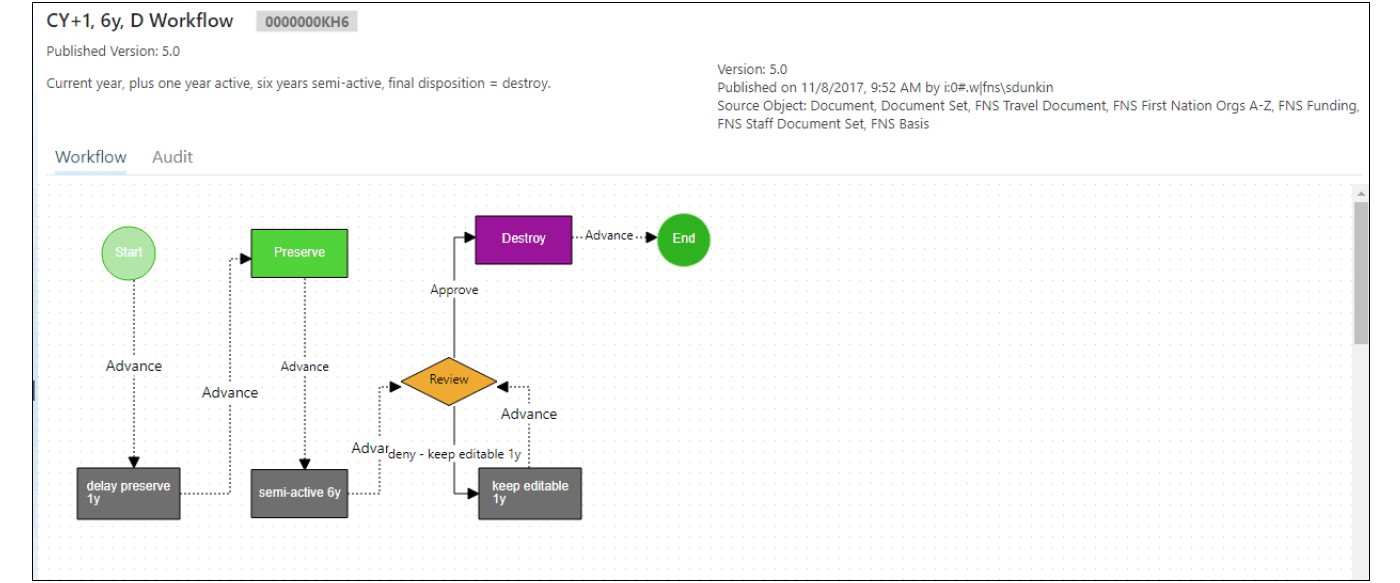



Navigation within the Site
The structure and layout of the homepage was largely developed based on user consultation – it was decided that it would be best to follow the highest-level classification structure, moving from broad categories as the launching point to the more granular organization of the records. Each category is shown on the home page with an icon so that it can be easily identified and selected by users. The most commonly accessed areas grouped under the heading “Business of the Summit”, are also listed in a menu at the top of the screen which reveal sub areas in a list when the cursor is pointed at them.



Within each category are subcategories and libraries of documents. The different categories are listed across the top of the page, while libraries are listed along the left-hand side.



Once in a specific document library, metadata is used to assist users to search, sort, filter, and group documents by their metadata in order to more easily find the documents they are searching for.



Figure 5: An example of a document library with metadata shown in several columns5
SharePoint Challenges
During the project implementation the FNS encountered a number of challenges with SharePoint:
- Vocabulary and concept Issues;
- Lack of Microsoft product support documentation and resources;
- Naming conventions
Vocabulary and Concepts
Misunderstandings were frequent and often unavoidable in discussions between the Records Manager and the first team of consultants due to the overlapping vocabulary of SharePoint and established Records Management terminology. Concepts such as “policy” and “archives”, both of which have specific meanings in both SharePoint and established RIM vocabulary became pain points for moving forward with the project. The importance of working with a consulting firm that has a well-developed understanding of records management as well as SharePoint’s Records Centre cannot be overstated, as this knowledge will save countless hours of frustration arising from misunderstanding of terms.
Likewise, the SharePoint “content type”, an entity in SharePoint which is employed to apply metadata columns, workflows, settings and other forms of data capture to a piece of content, was a particularly difficult concept to understand initially. The content type’s function and relationships within the SharePoint environment were not immediately transparent and not clearly explained for comprehension. As the project has continued, the concept of a ‘content type’ has gradually became clearer as the layers of function were revealed, more types of content were uploaded, and more content types were created to describe each of these new types of content.
Support Documentation and Resources
Additionally, and frustratingly, Microsoft does not produce software user manuals to assist with the learning process and few tools or online resources are available for the ‘lay-user’. There are a variety of third party manuals available on the market, however, many of these target expert admin users, are expensive and at the rapid rate of change, quickly obsolete. More and more these third party manuals reference the cloud-based Office 365 SharePoint Online offering rather than the on-premise server implementation that the FNS has. The FNS eventually overcame the lack of supporting documentation through repetition of activities and tasks, as well as significant input from the new team of consultants. The FNS have subsequently created both a User Guide specific to their SharePoint site, and a Governance Manual to assist users and administrators to understand and/or maintain and adapt the implementation to keep up with changing user needs.
Naming Conventions
As for naming conventions, SharePoint utilizes two distinct fields for the description of documents, name and title. The name field directly contributes to the 256-character limit for the SharePoint URL as the name forms part of the URL locator for retrieval of the record. This is significant, as they learned the hard way when their content became unavailable once the URL exceeded the 256-character limit imposed by Microsoft. The implications of the name field were initially unknown to them as they began uploading content with long and descriptive names as employed by staff on the shared drive. After several panic attacks and a rather emotional melt-down when their efforts were discovered to have been obliterated by these descriptive names, they finally had to accept that they had ventured forth using the wrong field, leading to substantial intervention from the consultants and many hours of data revision.
The FNS have subsequently adopted a file Naming Best Practice based on one published by Stanford University Libraries, incorporating international date formatting for clarity. They have utilized the title field for more the descriptive name to indicate what the substance of the record is to the user.




SharePoint victories
The FNS finally launched SharePoint to their end users in early 20186 and they are currently engaged with ongoing group training sessions and individual support activities with staff, executive and consultants. Through a series of lunch and learns they have acquainted users with the structural elements of the implementation in order to familiarize staff with the platform. The FNS are now holding smaller group sessions to focus training on different interactions with the content, such as site navigation, working within libraries utilizing column filtering and sorting, local search, and paging forward to view results.
Search
SharePoint search has been the single biggest victory for staff buy-in. SharePoint search allows much more effective searching of content than was previously available through the existing desktop search tools, saving much time and frustration among staff.
SharePoint search also improves the experience for content that has not yet been migrated to SharePoint or content that will not be migrated, as they have configured SharePoint search to index the shared drives to allow users to search content across all of our digital collections more efficiently.
SharePoint search improves upon common windows search by searching not only the document title and metadata, but also the content of the documents themselves in the fashion of keyword searching. There is one caveat however, the shared drive search results can only be viewed and accessed by users within our office network.



Offsite Access
FNS wants their users to be able to interact with all their resources no matter where they may be – the executive are rarely in the office, and staff are often involved in offsite meetings with their constituents or with partner organizations.
Therefore, they created a targeted remote access workstation for external access. Offsite users open a remote session with the designated workstation on the office network to utilize the SharePoint search when they are not physically in the office. Content on the shared drive can then be identified and uploaded to SharePoint during the remote session to make it available to all users through a generic browser session.
FNS legal counsel have been particularly active using these remote sessions to search and acquire relevant records on the fly without having to engage our staff. They are also in the process of learning how to upload content they have created on behalf of the FNS.
Research Tools
The FNS have also recently utilized Collabware’s Information Query tool and the custom ‘FNS Topic’ folksonomy to feature research results in a single list where these records exist in disparate locations throughout the SharePoint libraries. This query tool has been enormously useful in aiding the FNS in their ability to respond to queries from legal counsel and to support research efforts.



Figure 8: An example of an Information Query being used to have a single list content related to a specific topic, regardless of where the documents are actually stored
Where the FNS is going from here
The FNS is currently in the process of developing the collaborative functionality of SharePoint. New staff and legal counsel have requested the development of team sites to facilitate collaboration on various activities, including sites for working groups, committees and research activities. They expect SharePoint to continue to evolve to address new concerns, needs and capabilities as Microsoft also continues to evolve their software. The FNS is aware of the new SharePoint 2019 development and will consider making the upgrade when it is eventually released – though not before the bugs and hiccups have been resolved.
Work Cited
1This paper was originally delivered by the authors as a presentation for the ARMA Canada Conference in May 2018, in Vancouver, BC.
2All of the purchases of SharePoint Server and associated User CALs (client access licenses) have been facilitated through TechSoupCanada.ca which offers special, deeply discounted pricing for non-profit and charitable organizations.
3The Office of the Privacy Commissioner of Canada has some useful links for Cloud computing and privacy, however, the most recent of these articles dates to June 2012 which is much too old to be considered current, considering the rapid rate of change in technology. The issues of ownership and jurisdiction of data stored in the cloud are not addressed.
4It should be noted that we have implemented a one-year delay for declaration of a document as a record to allow for additional modification of the document and correction of errors.
5The FNS has implemented a column, “True Document Date” to indicate the actual date of the document as recorded on the document itself as distinct from the machine date applied when the document is uploaded. This is particularly important to assist in identifying historical documents which have been uploaded often years after their creation or receipt.
6It should be noted here that the document conversion process has been substantially time-consuming, leading to the significant time lapse between implementation and launch.
Quand est-ce qu’on arrive?
Introduction à l’implémentation de SharePoint & Collabware au First Nations Summit
Sandra Dunkin, MLIS, CRM, IGP
Coordonnatrice Gestion des Archives & Information
First Nations Summit
Sam Hoff Consultant ECM Gravity Union
Introduction1
L’objectif de SharePoint et son utilisation dans le cadre de la gestion des archives est d’intérêt pérenne dans la communauté de la gestion des archives et de l’information (GAI), et ce, dès que Microsoft a décidé de faire son entrée sur ce marché avec SharePoint en 2001. Au fil des diverses versions de la plateforme SharePoint, Microsoft a veillé à assurer des capacités de gestion des archives non seulement en version originale ou grâce à des configurations particulières, mais plus récemment grâce à des applications complémentaires de tierces parties, afin de régir la conformité et l’automatisation de la classification et l’élimination des archives. De nombreuses études de cas et sessions d’information ont été offertes par Microsoft, par des fournisseurs complémentaires associés ainsi que par des experts en la matière, tel que Bruce Miller. Chaque année, des organisations spécialisant dans la gestion de l’information comme ARMA International, ARMA Canada, les diverses branches d’ARMA ainsi que plusieurs organisations internationales professionnelles de gestion de l’information, continuent d’offrir des sessions SharePoint dans le cadre de leurs programmes de formation. SharePoint demeure un sujet chaud dans l’industrie du GAI, occupant une part croissante du marché alors même que des développeurs tiers ne cessent d’améliorer leurs applications pour les rendre aptes à gérer des tâches de GAI complexes. Plusieurs organisations sont désireuses d’obtenir des solutions multifonctionnelles pour leurs besoins d’affaires, plutôt que d’investir dans des logiciels spécialisés pour des activités de GAI compartimentées, rendant SharePoint une alternative intéressante aux applications logicielles onéreuses, spécialisées et souvent modulaires.
L’étude de cas décrite ci-après donnera une vue d’ensemble du projet d’implémentation de SharePoint au First Nations Summit (FNS), soulignant les leçons apprises, erreurs, échecs et éventuels succès. Depuis le commencement du projet, le FNS s’est efforcé de créer une solution polyvalente afin de répondre aux besoins évolutifs des membres du personnel, de la direction et des consultants, lors du travail quotidien, ainsi que de combler les exigences de GAI pour une grande quantité d’archives. Les défis de gestion du changement, de formation et de ralliement des utilisateurs, de mises à jour variées et de l’environnement changeant créé par des utilisateurs engagés plus activement dans SharePoint seront aussi abordés.
Quelques mots au sujet du First Nations Summit
Le First Nations Summit, composé majoritairement de Premières Nations et Conseils de bande de la Colombie-Britannique, offre un forum aux Premières Nations de la C.-B. pour aborder les enjeux en lien avec les Titres et Droits, ainsi que la négociation de traités et autres points d’intérêt commun.
En Octobre 1990, les chefs des Premières Nations de la C.-B. ont rencontré le Premier Ministre du Canada, puis le Premier Ministre et le Cabinet de la Colombie Britannique pour exhorter l’importance de la nomination d’un comité tripartite mandaté de développer un processus moderne de négociation de traités en C.-B. Les gouvernements fédéral et provincial en sont venus à un accord et le 3 décembre 1990, le Groupe de Travail sur les Revendications fut établi suite à l’accord entre le gouvernement du Canada, le Gouvernement de la Colombie-Britannique et des chefs représentants des Premières Nations.
Les chefs de Premières Nations de partout en Colombie-Britannique ont assigné trois membres au Groupe de travail sur les revendications, au cours d’une réunion intitulée le First Nations Summit. Deux membres ont été désignés par le gouvernement du Canada, et deux par le gouvernement de la Colombie Britannique. Au terme de plus de cinq mois et demi de délibérations, le Rapport du Groupe de travail sur les revendications de 1991 a recommandé que les Premières Nations, le Canada et la Colombie-Britannique établissent une nouvelle relation basée sur la confiance mutuelle, le respect et la compréhension — par la voie de négociations politiques.
Rôle du FNS
Le FNS est une organisation menée par les Premières Nations et axée sur les actions et les solutions. Le mandat initial du FNS était d’assurer le progrès des discussions avec les gouvernements du Canada et de la C.-B. afin de soutenir les Premières Nations qui conduisent leurs propres négociations directement avec ceux-ci. La raison d’être du mandat émane de:
- Le Rapport tripartite de 1991 du Groupe de travail sur les revendications, élaboré conjointement par les Premières Nations, le Canada et la -B.,
- L’accord de 1992 de créer la Commission des traités de la C.-B. en tant que corps indépendant afin de « faciliter » la négociation des traités, et
- Les législations fédérale et provinciale subséquentes et les résolutions des chefs des Premières Nations d’implémenter l’accord de 1992 et d’établir la Commission des traités de la C.-B. en tant qu’entité légale
Approximativement 150 Premières Nations de la C.-B. participent aux assemblées du FNS pour faire avancer, discuter et donner une direction politique aux enjeux d’intérêt commun.
Dans le cadre de l’accomplissement de son mandat, le FNS ne participe pas en tant que partie négociante dans quelque négociation spécifique des Premières Nations que ce soit. Au fil du temps, et à travers les décisions collectives des chefs et leaders de Premières Nations, tel qu’indiqué par les résolutions, ils ont été avisés de n’assumer qu’un rôle de direction et de plaidoyer pour la vaste gamme d’enjeux d’intérêt pour les Premières Nations, incluant négociations et problèmes d’implémentation de traités, d’accords et autres arrangements constructifs et questions sociales et économiques de tous les jours affectant les Premières Nations.
Un élément critique du travail du FNS est l’identification de mesures concrètes pour surmonter les obstacles aux négociations. Lors des négociations entre les Premières Nations et la Couronne en C.-B., ils feront face à certains problèmes de processus et de fond qui représentent des défis significatifs et qui doivent être surmontés afin d’en venir à des traités, accords, ententes et autres arrangements constructifs.
Malgré qu’il maintienne son engagement à l’approche « fait-en-C.-B. » au sujet des négociations et de l’assistance offerte aux Premières Nations pour réaliser des traités pleins et entiers comme objectif premier, le FNS respecte et appuie les décisions de toute Première Nation à s’engager dans tout autre accord ou autre arrangement constructif, dans le but de promouvoir les intérêts et priorités de leurs nations respectives.
L’équipe du FNS
Le comité exécutif du First Nations Summit consiste en un groupe exécutif politique de trois (3) membres (FNS Groupe de travail)et d’un groupe exécutif administratif de deux (2) membsr(eFNS
coprésidents). Chaque membre du comité exécutif est investi d’un mandat de trois ans à son élection. Le FNS a présentement une équipe permanente de 10 personnes qui mettent en œuvre le mandat tel que déterminé par les résolutions adoptées par les chefs en assemblée lors des réunions du First Nations Summit, lesquelles sont tenues trois fois par année. Il est également en partenariat avec de nombreuses autres organisations des Premières Nations, telles que l’Assemblée des Premières Nations de la C.-B. et l’Union des Chefs Indiens de la C.-B., afin de travailler collectivement sur des enjeux d’intérêt aux Premières Nations de la C.-B.
Gestion de l’information au FNS
Puisque la négociation de traités est un travail constant, l’ensemble des dossiers du FNS demeure actif tout au long du processus, depuis la création du First Nations Summit en 1991 jusqu’à ce jour. Au rythme actuel d’accumulation, le FNS va bientôt surpasser sa capacité de stockage. Ils ont un volume important de dossiers en version papier et font face à de sévères contraintes d’espace sans parler des préoccupations en ce qui concerne l’intégrité structurale de l’édifice et le poids grandissant de leurs collections (ils sont au 12e étage d’une tour à bureaux vieillissante).
Le FNS a également une vaste gamme de collections — dossiers de types et formats variés, incluant des dossiers typiques en papier, classeurs de réunions, transcriptions textuelles, publications reliées, ainsi que des enregistrements vidéo et en autres formats. Tout ce contenu est important historiquement et toujours d’actualité, façonnant les activités courantes. Malgré cela, jusqu’à tout récemment, cette importante collection de documents n’était accessible que sur place.
Historique du projet
Le 5 décembre 2007, la section d’ARMA de Vancouver a organisé un évènement de formation à Surrey, en C.-B., faisant une démonstration de l’implémentation pilote de SharePoint pour le compte de la ville. Cette démonstration mettait de l’avant les caractéristiques et capacités du Centre de documentation SharePoint ainsi que les fonctions de collaboration inhérentes à la plateforme. Au même moment, le FNS a commencé à réaliser que l’accumulation de dossiers s’accélérait au-delà de la capacité de leurs unités de stockage existantes (dossiers, classeurs, vidéos et classeurs de collection). Ils étaient à la recherche d’une solution alternative pour la gestion de leur collection qui tiendrait compte de l’expansion de leur collection de dossiers physiques. Le FNS a reconnu avoir besoin de collections de documents électroniques pour garder le contrôle sur cette expansion.
Après beaucoup de recherches, de considération et d’enquête, le FNS a subséquemment acquis SharePoint 2007 et débuté son implémentation en août 2009. Ils ont ensuite fait une mise à niveau à la parution de SharePoint 2010, l’année suivante.
Initialement, le FNS a tenté d’installer et d’exploiter SharePoint sans support externe, cependant ils ont rapidement réalisé qu’en raison de la nature complexe du logiciel, ils auraient besoin de soutien spécialisé additionnel pour réussir leur implémentation. Par conséquent, le FNS a engagé une firme de consultants afin de configurer SharePoint 2010 pour développer les capacités locales du centre de documentation et configurer quelques adaptations pour satisfaire des exigences particulières. Malheureusement, la firme engagée ne possédait pas les connaissances nécessaires sur le Centre de documentation SharePoint ou les exigences de conformité au GAI. Ultimement, ce projet a échoué puisque la configuration et les fonctions originales de SharePoint n’offraient pas une conformité au GDI satisfaisante ni des structures ou des protocoles originaux.
Lors de la conférence d’ARMA Canada à Saskatoon, en 2013, le Gestionnaire des Archives du FNS a participé à la préconférence SharePoint présentée par Bruce Miller, qui a duré deux jours. Lors de cette session, M. Miller a fortement recommandé quelques compléments tiers pour GAI dans SharePoint conçus dans un but de conformité des exigences GAI. Suite à cette session, le Gestionnaire des Archives a assisté à des démonstrations de plusieurs fournisseurs de compléments tierces pour GAI pendant la conférence puis a rencontré les représentants de ces fournisseurs après la conférence.
Le FNS a éventuellement décidé d’acquérir Collabware CLM. Cette décision fut prise sur la base de plusieurs facteurs, le plus important étant la fonction de gestion des documents qui était déjà en place, étant la meilleure solution pour le personnel et le déroulement du travail. Ils ont relancé le projet avec la nouvelle plateforme SharePoint 2010 et Collabware, en août 2013.
Le FNS a opté pour une approche unique à SharePoint en s’assurant que la conformité à la gestion des documents par l’entremise de Collabware soit pleinement configurée avant que quelque contenu que ce soit y soit téléchargé, et que l’interface SharePoint soit fonctionnelle et relativement intuitive pour les utilisateurs. Ils ont également décidé d’investir significativement temps et effort pour alimenter le site SharePoint avant la date de son lancement. Ils ont donc passé une grande partie des quelques dernières années à effectuer la conversion exhaustive des documents patrimoniaux de formats variés et le téléversement de ce contenu dans SharePoint afin d’améliorer l’expérience utilisateur au moment du lancement aux utilisateurs. Il a aussi été déterminé qu’en vue de faciliter le processus de gestion du changement, ils devraient fournir suffisamment de matériel pour démontrer l’utilité et le bon fonctionnement de SharePoint. De plus, ils ont utilisé ce processus pour acquérir plus d’expérience et d’efficacité lors du téléversement de documents dans SharePoint, afin d’être mieux outillés à aider les utilisateurs qui pourraient avoir des questions ou des problèmes. Ce processus a donc permis à l’équipe de développement de régler les pépins ou anomalies au fur et à mesure qu’ils survenaient, évitant ainsi aux utilisateurs la frustration de les affronter sans assistance. À ce jour, le FNS a plus de 12 250 documents et plusieurs milliers d’heures de travail d’investis dans l’implémentation.
Petite note à propos de l’infrastructure du réseau
En 2009, le FNS a débuté l’implémentation de SharePoint 2007 avec du matériel informatique dédié
- trois serveurs physiques pour héberger le serveur SharePoint, le serveur SQL, et un environnement de test pour effectuer des tests. Tous les serveurs étaient situés sur place, avec des adresses IP statiques
Puis en 2010, ils avaient déjà entamé le processus de virtualisation des autres applications de serveur afin de faciliter l’entretien, le basculement et les processus de récupération — alors suite à la mise à niveau à
SharePoint 2010, toutes les applications des serveurs SharePoint associés ont été subséquemment virtualisées.
Depuis juin 2018, le FNS a lancé un nouveau projet pour la mise à niveau à SharePoint 20162, Collabware CLM v3.2, SQL Server 2017 et Office Online Server. Cette solution a été développée dans un environnement test, parallèle à l’implémentation de SharePoint 2013 existante. Une fois que le bon fonctionnement de la nouvelle plateforme SharePoint 2016 a été confirmé, SharePoint 2013 a été fermé et les documents de Système de Noms de Domaines (SND) associés ont été mis à jour pour redémarrer avec la plateforme 2016. L’implémentation de SharePoint 2016 fonctionne maintenant dans le cadre d’un environnement virtuel avec un total de quatre serveurs SharePoint associés.
Il convient de noter que le FNS maintient en fonction tous ses serveurs sur place, en raison de préoccupations d’exclusivité, de confidentialité et de sécurité, et le manque de services de nuage qui sont fiables et dignes de confiance au Canada et en Colombie-Britannique spécifiquement. Un manque de transparence subsiste en ce qui concerne l’emplacement exact des données utilisateur dans les parcs de serveurs web et il n’y a pas suffisamment de services de nuage détenus et exploités au Canada. La majorité des options de nuage au Canada sont détenus par des corporations à l’extérieur du territoire, rendant les données potentiellement sujettes à la perquisition et la confiscation de la part de gouvernements étrangers, notamment les dispositions du Patriot Act américain. En ce moment, le nuage demeure beaucoup trop ambigu quant à la propriété, la juridiction et la protection des données pour que le FNS y place sa propriété intellectuelle avec confiance. 3
Objectifs du FNS
Le FNS a plusieurs objectifs qu’il espère atteindre grâce à l’adoption de SharePoint en complément de la Gestion des Dossiers :
- Résolution du chaos des disques partagés;
- Élimination des versions et copies redondantes de documents;
- Réduction de l’encombrement des boites de réception de courriels;
- Collaboration améliorée.
Enjeux des disques partagés
Comme plusieurs autres organisations, le FNS avait perdu le contrôle de ses disques partagés au fil des années. Certaines structures de dossiers sont subjectives et complexes et correspondent à des interprétations individuelles du contenu et totalement indéchiffrables pour des collègues et souvent aux employés eux-mêmes au fil du temps. Alors que des tentatives ont été faites pour imposer un certain ordre dans le disque partagé, toute démarche fut en vain puisque les employés résistaient au changement et continuaient à travailler à l’intérieur de leurs structures de dossier existantes. La fonction de recherche de SharePoint a atténué plusieurs des défis en ce qui concerne le disque partagé — plus précisément l’indexation du disque partagé en tant que dépôt externe et la révélation de l’emplacement de documents pertinents dans les structures complexes des dossiers.
Copies redondantes
La prolifération de multiples copies redondantes et de nombreuses versions de documents individuels s’est aussi révélée être un obstacle significatif au déroulement efficace des opérations. Ces versions et copies variées existent au travers de multiples dossiers et pour plusieurs employés, souvent figurant dans plus d’un dossier de l’ensemble des dossiers d’un même employé. Les ébauches, versions disparates ou anciennes versions sont rarement supprimées des dossiers des employés, compliquant encore davantage l’identification du dossier ou document officiel. Ces versions et copies sont difficiles à naviguer et presque impossibles à perquisitionner avec des outils de recherche courants.
SharePoint permet aux employés de préserver un historique des versions pour chaque document. À tout moment, un document peut être comparé avec ou rétabli à une version précédente. Ce qui signifie que l’ensemble des employés peuvent travailler sur, et modifier, un même document sans avoir besoin d’enregistrer et de regrouper plusieurs versions. De plus, SharePoint permet à plusieurs utilisateurs de modifier simultanément un même document, ce qui élimine la nécessité d’avoir plus d’une copie du document.




Courriels
Les courriels sont depuis longtemps la méthode préférée de collaboration entre employés, directeurs et consultants. Cette utilisation excessive des courriels pour travailler ensemble sur des documents et des projets cause un désordre significatif dans les boites de réception des employés et des membres de la direction, et des difficultés substantielles lors de la fusion des changements variés dans un seul document, consolidant encore plus la confusion des diverses versions et copies, comme mentionné précédemment.
Même si ce processus de collaboration n’a pas encore été éliminé, le FNS élabore de nouveaux sites de collaboration à l’intérieur même de SharePoint afin de pouvoir travailler sur des objectifs spécifiques à certains projets ou pour les employés. L’objectif est que le personnel migre graduellement des courriels à ces sites de collaboration afin d’éliminer l’encombrement des courriels et l’augmentation excessive de la taille des boites de réception et des dossiers secondaires de courriels.
Collaboration
La collaboration était une autre chose à considérer — tel que décrit plus haut, les collaborations sont accomplies avec de longues chaines de courriels, ce qui entraîne des versions disparates d’un même document nécessitant une fusion. Le FNS désirait consolider et uniformiser le processus de production de diverses versions pour rendre la collaboration plus efficace. Comme corollaire à la collaboration, ils ont également cherché à offrir un meilleur accès à du contenu additionnel pour les partenaires sans restrictions géographiques, plus spécifiquement, un accès aux collections de traités historiques. Le FNS espère aussi que l’augmentation de l’utilisation des sites de collaboration de SharePoint réduira la quantité de versions disparates, avec des noms changeants tels que « document-ébauche1 », « document-ébauche2 », « document-final », etc.
Le FNS a opté pour une implémentation conçue avec des structures de gouvernance et des protocoles appliqués au contenu initial afin de limiter, sinon prévenir, la prolifération de contenu indépendant comme dans le cas du disque partagé. Au lieu de permettre à l’utilisateur final de créer des espaces de contenu comme il le souhaite, le noyau de l’équipe de Gestion des Dossiers est responsable de l’ajout d’espaces pour le nouveau contenu qui peut être consulté par les utilisateurs, leur permettant de garder le contrôle et la constance.
Le FNS doit également faire face au problème de contenu plus vieux, périmé, pour lequel les logiciels ont été discontinués ainsi que l’apparition rapide de nouvelles versions de logiciels qui rend inaccessible le contenu plus vieux — par exemple, ils ont une grande quantité de documents de référence WordPerfect, mais n’utilisent plus WordPerfect. Ils sont présentement impliqués dans un processus de conversion de ces documents afin de préserver ces archives et les rendre accessibles dans le cadre de SharePoint. L’essentiel de ces documents sont convertis en format PDF, téléversés dans SharePoint puis supprimés du disque partagé afin d’éventuellement éliminer le disque partagé complètement.
La classification dans l’environnement numérique
Le FNS a commencé avec la classification avec leurs documents papier alphanumériques, dans plus de 5000 catégories, répertoriées pour l’archivage dans une simple base de données DBTextworks. Cette classification est très granulaire pour permettre une récupération efficace des documents. Évidemment, ils ont eu à repenser au passage de leur système de classification vers un environnement numérique.
Le FNS a un large vocabulaire de termes de métadonnées, imposant des descriptions et des organisations standardisées ainsi qu’une folksonomie d’étiquettes’ ou de sujets auxquels les utilisateurs peuvent contribuer, pour décrire plus amplement les dossiers. En exploitant le pouvoir des métadonnées, ils ont pu réduire le nombre total de catégories à 96 répertoires dans lesquels les dossiers sont organisés. Ils ont subséquemment augmenté quelque peu ces catégories afin de permettre des variations de sauvegarde et d’enregistrement de données.
Certaines des différences majeures entre les plans de classement de dossiers en format papier et ceux des dossiers électroniques sont l’utilisation de catégories en tant que métadonnées, les limites physiques de la quantité de documents pouvant être stockées dans un site unique, et la sécurité.
Les métadonnées peuvent servir à classer du contenu, peu importe l’emplacement
Comparativement à un système de classification papier, où les documents d’une classification particulière sont typiquement rangés ensemble à un même endroit physique, dans le cas d’un système de gestion du contenu électronique, la localisation du contenu à l’intérieur du système n’a pas besoin d’être liée à sa catégorie de dossier. Les métadonnées du document peuvent être utilisées pour le classifier correctement selon son contenu, peu importe où il « réside ».
La classification n’a pas besoin d’être utilisée comme métadonnée
Puisque nous n’avons pas à lier l’emplacement du document à sa classification, il n’y a non plus aucune nécessité de les séparer en sous-catégories dans le but de classer les documents en groupes ayant un sens et d’une taille appropriée. Plusieurs documents peuvent demeurer dans une seule et même catégorie de documents, et utiliser les métadonnées pour les trier de n’importe quelle autre façon. Par exemple, au lieu d’avoir une catégorie « par année », ce qui revient essentiellement à utiliser la catégorie de dossier pour ajouter des métadonnées au document, ils peuvent avoir une seule catégorie et utiliser les métadonnées dans le système pour séparer les documents par année.
Plusieurs documents peuvent résider dans un même emplacement
Ils sont également beaucoup plus libres en termes des limites de volume. Dans le monde physique, il pourrait devenir très difficile d’avoir des milliers de documents dans une même catégorie puisqu’il deviendrait de plus en plus ardu de trouver du contenu spécifique à l’intérieur de cette même catégorie. Par contre, puisque dans le monde électronique l’emplacement et les métadonnées sont séparés de la classification et de l’archivage, ce n’est plus un problème. Il peut y avoir 200 000 documents dans une même classification répartie en multiples collections dans le système. Les utilisateurs peuvent toujours trouver ce qu’ils cherchent à l’aide des métadonnées et de la fonction de recherche, tout comme la plupart des gens maintenant utilisent iTunes ou Spotify pour repérer facilement une chanson dans un répertoire de plusieurs millions.
La classification a été découplée de la sécurité dans l’ensemble, excepté pour le contenu semi-actif
Bien que les points mentionnés ci-haut nous affranchissent d’avoir à utiliser des catégories de dossiers pour simplifier notre plan de classement, la sécurité reste une contrainte dans le monde de la gestion de documents électroniques. En plus du modèle de sécurité intégré à SharePoint, qui nous permet de définir qui peut accéder et (ou) modifier des documents, il faut prévoir des mesures dans le cas des documents semi-actifs. Si un document n’est plus pertinent pour les utilisateurs, il est envoyé aux archives afin d’être conservé si nécessaire, mais n’encombre plus les collections de documents dont les utilisateurs se servent pour repérer des documents actuels. Le contenu physique est classé dans certaines catégories et peut être conservé dans un classeur ou une pièce verrouillée, et nous appliquons des mesures de sécurité pour la classification de contenu semi-actif. En fin de compte, la nouvelle mesure de sécurité sera appliquée à tout le contenu d’une classification donnée, une fois qu’elle est déplacée aux archives, peu importe les mesures de sécurité appliquées aux items particuliers pendant leur phase active.
Préservation dans l’environnement numérique
Le FNS a également mis à profit les capacités d’automatisation de Collabware dans le cadre de leur politique d’archivage. Par l’entremise du développement des processus de travail, en utilisant l’éditeur visuel, ils ont créé un ensemble de flux de travail qui reflète plus précisément le cycle de vie de leurs documents, et ils ont appliqué ces processus à l’ensemble de la collection en utilisant les Règles pour le Contenu appliquées au type de contenu sur mesure. Les Règles pour le Contenu sont une fonction de Collabware CLM qui permet au système d’identifier, de classer et de déclarer des documents automatiquement par l’entremise de certaines règles. Ces règles sont conçues pour identifier les documents appropriés grâceà l’utilisation de combinaisons uniques de Types de Contenu appliquées à des collections et des métadonnées enregistrées par les utilisateurs ou fournies par les documents.
Un exemple d’une règle de contenu pourrait être : « Tout document qui est du type Document de Réunion, qui est en format PDF et a un statut final décrété par un utilisateur ». Dans cet exemple, l’association du type de contenu et des métadonnées fournies par l’utilisateur peut être utilisée afin de classifier automatiquement ce document en tant qu’archive, dans la classe de document appropriée, sans intervention directe par l’utilisateur. Le mécanisme pourrait même passer inaperçu, puisque l’utilisateur poursuivait simplement le processus d’ajout de documents dans le système.
Une fois classé, le contenu suivra le cours du processus de travail associé à chaque Catégorie de Document. Plusieurs actions et processus sont possibles. Par exemple, un document peut être verrouillé, avoir un protocole de sécurité différent, être envoyé aux archives, subir un processus de révision ou même d’élimination finale.




Navigation au sein du Site
Le développement de la structure et de la disposition de la page d’accueil a été largement influencé par l’utilisation des employés — il a été déterminé que la meilleure façon de procéder était de suivre la structure de classification la plus élevée, partant de catégories larges comme point de départ jusqu’à l’organisation plus granulaire des documents. Chaque catégorie est affichée sur la page d’accueil avec sa propre icône afin d’être facilement identifiée et sélectionnée par les utilisateurs. Les sections les plus souvent consultées regroupées dans la rubrique « Summit Activities » sont également énumérées dans un menu au haut de l’écran, avec des sous-catégories énumérées lorsque le curseur y est pointé.




Il y a des sous-catégories et des collections de documents dans chaque catégorie. Les différentes catégories sont énumérées au haut de la page, alors que les collections sont disponibles tout le long du côté gauche de la page.




Image 4 : un exemple de sous-catégorie
Dans une collection donnée, les métadonnées sont utilisées afin d’aider les utilisateurs à chercher, filtrer et regrouper des documents selon leurs métadonnées, dans le but de les retrouver plus facilement.




Image 5 : Un exemple d’une bibliothèque de documents contenant des métadonnées figurant dans diverses catégories,5
Défis de SharePoint
Tout au long de l’implémentation, le FNS a fait face à un certain nombre de défis avec SharePoint :
- Vocabulaire et problèmes de concept;
- Manque de documentation et de ressources de soutien de produit de Microsoft;
- Conventions d’appellation.
Vocabulaire et concepts
Les malentendus étaient fréquents et souvent inévitables lors de discussions entre le Gestionnaire des registres et la première équipe de consultants en raison du vocabulaire redondant entre SharePoint et la terminologie établie en Gestion des Documents. Des concepts tels que « politique » et « archives », ayant tous deux une signification spécifique en SharePoint et dans le vocabulaire établi de la GDR sont devenus des points sensibles dans l’avancement du projet. On ne peut trop insister sur la nécessité de travailler conjointement avec une firme consultante ayant une solide compréhension de la gestion de dossiers ainsi que du Centre des archives de SharePoint, puisque leur maîtrise du sujet évitera d’innombrables heures de frustrations découlant de la mauvaise compréhension des termes.
De la même façon, le « type de contenu » de SharePoint (une entité dans SharePoint qui sert à appliquer des colonnes de métadonnées, processus de travail, paramètres et autres types de saisies de données à du contenu), était initialement un concept particulièrement difficile à saisir. La fonction type de contenu et ses liens à l’intérieur même de l’environnement SharePoint n’étaient pas immédiatement clairs et n’étaient pas distinctement expliqués. Au fur et à mesure que le projet a évolué, le concept de « type de contenu » est graduellement devenu plus clair, et alors que les multiples niveaux de fonction étaient exposés, plus de types de contenu étaient créés et téléversés, pour décrire ces nouveaux types de contenu.
Documentation et ressources de soutien
De plus, et de façon exaspérante, Microsoft ne produit pas de manuels de soutien à l’utilisateur pour faciliter le processus d’apprentissage et peu d’outils ou de ressources en ligne sont disponibles à l’utilisateur » profane ». Il y a plusieurs manuels de parties tierces sur le marché, mais la plupart de ceux- ci ciblent une clientèle d’utilisateurs experts en administration, sont onéreux et, au rythme rapide de l’évolution du contenu, deviennent vite désuets. De plus en plus, ces manuels de parties tierces font référence à l’option d’Office 365 SharePoint Online sur le nuage plutôt que l’implémentation serveur sur place qu’offre le FNS. Il a éventuellement surmonté l’obstacle du manque de documentation de soutien par la répétition d’activités et de tâches, ainsi que grâce à des contributions significatives de la nouvelle équipe de consultants. Le FNS a subséquemment créé à la fois un Guide pour l’Utilisateur spécifique à leur site SharePoint et un Manuel de gouvernance pour aider les utilisateurs et administrateurs à comprendre et\ou maintenir et adapter l’implémentation et ainsi garder la cadence face aux besoins changeants des utilisateurs.
Conventions d’appellation
Pour ce qui est des conventions d’appellation, SharePoint utilise deux champs distincts pour la description des documents, le nom et le titre. Le champ d’appellation contribue directement aux 256 caractères permis pour le lien SharePoint URL, puisque le nom fait partie intégrante du localisateur d’URL pour la récupération d’un document. C’est un détail important; ce qu’ils ont appris à leurs dépens quand leur contenu n’était soudainement plus disponible parce que l’URL avait dépassé la limite de 256 caractères imposée par Microsoft. L’importance du champ d’appellation leur était initialement inconnue alors qu’ils entamaient le téléversement de contenu ayant des noms longs et descriptifs comme ceux utilisés par les employés sur le disque partagé. Après plusieurs attaques de panique et un effondrement plutôt émotif lorsqu’ils ont découvert que leurs efforts avaient été oblitérés par leurs appellations, ils ont finalement dû se résigner à admettre qu’ils s’étaient aventurés en utilisant le mauvais champ, nécessitant une intervention majeure des consultants et beaucoup d’heures de révision de données.
Le FNS a subséquemment adopté une Meilleure Pratique d’Appellation des documents inspirée d’une semblable publiée par la Stanford University Libraries, et qui incorpore le formatage en date internationale dans un but de clarté. Ils ont utilisé le champ d’appellation pour un nom plus descriptif, afin d’indiquer à l’utilisateur la substance du document.




Victoires de SharePoint
Le FNS a finalement mis SharePoint à disposition des utilisateurs finaux en début 20186 et ils sont présentement impliqués dans des sessions de formation de groupe et des activités de soutien individuelles avec des membres du personnel, de la direction et les consultants. Par l’entremise d’une série de déjeuners-conférences, ils ont familiarisé les utilisateurs avec les éléments structuraux de l’implémentation pour apprendre à connaitre la plateforme. Le FNS tient également des groupes de formation plus restreints, axés sur de différentes interactions avec le contenu, telles que la navigation du site, le travail dans le cadre d’une collection en utilisant la filtration avec les colonnes, la recherche locale, et avancer d’une page afin de visionner des résultats.
Recherche
La fonction de recherche de SharePoint a été sans contredit la plus grande victoire en termes de ralliement du personnel. Elle permet une recherche de contenu beaucoup plus efficace que les outils de recherche disponibles précédemment sur le bureau, réalisant une économie de temps et beaucoup moins de frustration pour le personnel.
La fonction de recherche de SharePoint améliore également le travail dans le cas de contenu n’ayant pas encore été migré à SharePoint ou qui ne sera pas migré, puisque qu’elle a été configurée pour indexer les disques partagés, afin de permettre aux utilisateurs de rechercher du contenu à travers toutes les collections numériques de façon plus efficace. La recherche SharePoint améliore la recherche courante en recherchant non seulement le titre et les métadonnées du document, mais aussi le contenu lui-même du document, comme une recherche par mot-clé. Par contre, il y a une restriction : les résultats de la recherche d’un disque partagé ne peuvent être consultés que par des utilisateurs au sein du réseau de bureau.




Accès hors site
Le FNS désire que les utilisateurs puissent interagir avec toutes leurs ressources peu importe où ils sont — les membres de la direction sont rarement à leurs bureaux, et les membres du personnel sont souvent en réunion hors site avec leurs mandants ou des organisations partenaires.
C’est pourquoi ils ont créé une station de travail externe ciblée pour l’accès extérieur. Les utilisateurs hors site y accèdent en ouvrant une session à distance avec la station de travail désignée par le réseau de bureau pour utiliser la fonction de recherche de SharePoint lors de leur absence du bureau. Le contenu du disque partagé peut alors être identifié et téléversé à SharePoint pendant la session à distance afin de le rendre disponible à tous les utilisateurs lors d’une session de navigation générique.
Les conseillers juridiques du FNS ont été particulièrement actifs en termes de sessions à distance pour rechercher et obtenir des documents appropriés de façon impromptue, sans avoir à impliquer le personnel. Ils apprennent présentement à téléverser du contenu créé pour le compte du FNS.
Outils de recherche
Le FNS a aussi récemment utilisé l’outil de recherche Information Query de Collabware et la folksonomie « FNS Topic » courante afin de présenter les résultats de recherche en une liste unique alors que ces documents sont en divers endroits au travers des collections SharePoint. Cet outil de recherche a été extrêmement utile pour l’aide apportée au FNS visant à améliorer leur habileté à répondre aux demandes des conseillers juridiques et à participer aux recherches.




L’avenir du FNS
Le FNS procède en ce moment au développement de la fonctionnalité collaborative de SharePoint. De nouveaux membres du personnel et des conseillers juridiques ont demandé la création de sites de collaboration dans le but de faciliter le travail au cours de diverses activités, incluant des sites pour groupes de travail, et comités et activités de recherche. Ils espèrent que SharePoint continuera d’évoluer pour aborder les nouveaux problèmes, besoins et capacités au fur et à mesure que les logiciels de Microsoft évoluent également. Le FNS est conscient du développement du nouveau SharePoint 2019 et considérera faire la mise à niveau lors de sa sortie éventuelle — toutefois pas avant que les pépins et contretemps aient été réglés.
Works Cited
1Cet article était originalement présenté par les auteurs lors d’une conférence d’ARMA Canada, en mai 2018, à Vancouver, C.- B.
2Tous les achats de SharePoint Server et licences d’utilisation CALs (client access licences) ont été réalisés grâce à TechSoupCanada.ca qui offre des prix spécialement réduits pour les organisations sans but lucratif et de charité.
3Le Commissariat à la protection de la vie privée du Canada suggère des liens utiles pour le Cloud computing et la vie privée, par contre, l’article le plus récent y figurant date de juin 2012 et est beaucoup trop vieux pour être considéré d’actualité, vu le rythme rapide de changement en technologie. Les questions de propriété et de juridiction des données stockées dans le cloud n’y sont pas mentionnées.
4Il est important de noter que nous avons implémenté un délai d’un an pour la déclaration d’un document en tant qu’archive afin de permettre des modifications additionnelles ou corrections d’erreurs sur un document.
5Le FNS a mis en place une colonne, « True Document Date » pour indiquer la date réelle du document, telle qu’elle est enregistrée sur le document lui-même, par opposition à la date appliquée automatiquement lors du téléchargement du document. Ceci est particulièrement important pour aider à identifier les documents historiques qui ont été téléchargés souvent des années après leur création ou leur réception.
6Il est important de noter que le processus de conversion de documents a été substantiellement long, amenant à un délai significatif entre l’implémentation et le lancement.
A Record of Service: The First Canadian Conference on Records Management “A Giant Success”1
By Sue Rock, CRM
In 1977 ARMA International conducted a vote among all Canadian members to determine if a separate Canadian Region should be formed. The result was an overwhelming response favouring the formation called Region VIII, now known as ARMA Canada.
In the winter of 1980, Region VIII hosted its first conference. It was a startling, yet not unpredictable success. After all, Canadian records managers had served prominently within ARMA International leadership throughout the ‘70s. Many had presented papers at ARMA International conferences, and had received prestigious International awards. They knew how to market records management and how to serve an eager audience. Their goal was to showcase what Canadians can accomplish despite geographical and cultural differences.
The Conference theme was “Sea to Sea Information”. It was held from February 4 – 6, 1980 in Banff, Alberta.
The final registration of the First Canadian Conference on Records Management totalled 252 participants with representation both in speakers and general attendance from every province and territory except Prince Edward Island.
Over a three-day period, the conference offered a staggering 42 educational sessions, ranging in duration from 1.5 hours to full day sessions. Not one speaker received expense money from conference funds and some speakers came at their own expense. Organizations who defrayed the expenses of their employees to attend were recognized as an indication of the importance of records management as the discipline entered the 1980s.
First Conference 1980 Educational Content and Outcomes
The Conference received “super-positive feedback”1 from the participants on the quality of speakers. As a result, a Canadian Speakers Roster was developed by Judi Harvey, Vancouver Chapter, to be provided to all chapters in Region VIII as well as the ARMA Speakers Bureau.
The sessions which received the highest ratings are equally sustainable from our 21st century perspective. Though we may find references to microfilm as ‘quaint’, remember, the Standards Council of Canada had recently approved the new National Standard CAN-CGSB-72.11-M79 Microfilm as Documentary Evidence which remained a solid reference tool right into the 21st century.
Sessions highly rated included: Fundamentals of Records Management; Microfilm vs Paper; Systems Approach to Records Management; Records Centres; Micrographics Equipment Review; Directive Management; Effective Writing; Computer Output Microfilm; Resistance to Change; Word Process; Cost Benefit Analysis; Form Management; Implementation of Records Management Programs; Interface between Libraries and Records Management and Special Interest Group on Petroleum.2
The keynote speaker at the first day’s luncheon was Dr. W. I. Smith, Dominion Archivist, Public Archives of Canada. His topic was: Records Management in Canada: Challenge and Opportunity. Day two featured Ms. Anneliese Arenburg, President, Arenburg Consultants Ltd. speaking on Records Management Future: A consultant’s point of view.
Much like our current “Poster Board” conference sessions, the First Conference offered a “Call for Papers”, with a 10-minute on-site soundbite per author. These 10-minute sessions permitted any participant to share an informative management project or system that had been successfully implemented in their organization. The paper would then be published in the conference proceedings.
First Conference Chapter Leadership Outcomes
In the background of Conferences, ARMA leadership teams get together to exchange ideas and develop a cohesive strategic direction. Noteworthy is that all Chapter Presidents representing the seven Chapters: Calgary, Edmonton, Montreal, Ottawa, Toronto, Vancouver, and Winnipeg, were in attendance, which led to a very constructive Chapter Presidents’ Meeting.
At this First Conference, Gerry Roussy of Fredericton, New Brunswick coordinated a meeting of individual Chapter Education Directors. The end result was that the Canadian Position Paper on Records Management Education would be authored by Gerry, based on feedback received from each Chapter. Records management educational circulars and course outlines from each Chapter’s geographic location were shared at the meeting.
A legacy from the First Conference was that the Chapter Presidents recommended a Canadian Region Conference be held every two years and should be rotated East, Central, and West. [Ironically, the theme of the First Conference was “Sea to Sea Information” – note, Maritime Chapters did not exist at the time.] As an immediate result, Winnipeg, Toronto and Montreal indicated interest in hosting the 1982 Region VIII Conference. In 1982, the second Canadian Conference was held in Montreal, with presentations and proceedings in both official languages.
First Conference Awards and Recognition
One of the highlights of the Conference was the presentation of the William J. Gray Award3 for research and development in the field of Information Management which was presented to the two main forces in the Canadian Records Retention Project, Ted Hnatiuk and Jim Coulson of Toronto. Certificates of appreciation were awarded to Peg Barlow and Stephen Pollishuke who contributed a great deal to the project.
The Canadian Records Retention Project was also known by its acronym SCORR – the Special Committee on Records Retention, chaired by Ted Hnatiuk with Carl Weise and Jim Coulson, and all members of the ARMA Toronto Chapter.4 With participation from all Canadian ARMA Chapters, SCORR was successful in petitioning the Federal government to produce a definitive list of Federal regulatory retention requirements. The first “red book” of Federal records retention regulatory requirements in Canada was published in 1980. It addressed 27 Federal departments with 74 Federal Statutes, 111 Federal Regulations with 67 different retention periods placed on business records. Approximately 50% of the regulations did not contain stated retention periods.
The Infomatics Award for furtherance of interfacing with other disciplines within the field of Information Management was presented to Patricia Schick, Edmonton Chapter (cited in many ARMA Journals under her subsequent name Patricia Acton, and future president of the Institute of Certified Records Managers (ICRM). This award was first sponsored in 1978 by the ARMA Edmonton Chapter, intended to be presented annually to a “deserving person making outstanding contributions in the information processing field”.5 The award description includes “computing and systems” as one of the three primary areas of information and records management at the time.
ARMA Canadian Pioneers comprising founding Chapter Presidents, Former Regional Vice Presidents, ARMA International Officers and Charter Members who had remained active in ARMA for a number of years were honoured at the Conference. The following pioneers were presented with Certificates of Appreciation at a special Pioneer Luncheon:
Calgary: James C. Carrow; F. Whiteley Graham; Donald E. Worden
Edmonton: Robert P. Morin CRM; Sandra Ercse; Howard Brinton
Montreal: Denis Deslongchamps CRM and former Regional VP; William Gray CRM; John Andreassen CRM; Margaret Sadler former ARMA International Secretary; George Lawson; Clifford Wynn
Ottawa: Ralph Westington; Milton Thwaites; Ted Ferrier; John Smith future ARMA International President
Toronto: D.V. Andres CRM; A. Arenburg CRM; D.T. Barber CRM and former Regional VP; J.W. Champers; P. Collins; P.M. Fraser; G. Gammie; W.J. Hardy; J.T. Harrison; G.J. Joyce; W.F. Ludlam CRM; H.A. Moulds; G.B. Mowat CRM; A.W. Murdoch; V. Niggl CRM; G.M. Pratt; J.E. Thorne; K.A. Wadwell; R.L. Webb; R.A.H. Westmore; G. Fletcher former Regional VP
Vancouver: Judi Harvey; Pam Neish; Olive J. Pennock; Anthony P. Farr; Harry C. Chapin; Jacqueline Rowland; Harold A. Findlater; Edith Laurenda Daniells
Winnipeg: Terry Smythe; Ken Smith; J. A. Spokes, future ARMA International President
First Conference Networking Opportunities
The Conference was hosted in Banff, Alberta mid-winter, February 4 – 6, 1980. The logistics of shuttling participants to and from the location must’ve been staggering. However, the logistics would have provided an opportunity for immediate networking!
Here’s a snapshot of the Guest Spouse Program, at an additional cost of $55.00 for the three-day tour and activities. How about that “romantic bus ride to Elkana Ranch”?




Conferences are often fondly remembered for their social networking opportunities. For seasoned ARMA Canada conference participants, many will fondly recall outings often disrupted by the unexpected, such as a moose halting a convoy to a picnic location at the 1999 event in Saskatoon!
The First Canadian Conference 1980 offered the usual Sunday evening welcoming cocktail party, followed by a Monday wine and cheese party, with the Tuesday Night at Elkana Ranch as the grande soirée for a fine dinner, requisite speeches and awards, followed by an evening to schmooze.
As a review of the First Canadian Conference 1980 draws to a close…
The delivery of educational opportunities remains a cornerstone of ARMA activity. Conferences fulfill ARMA educational objectives by presenting au current information-related topics to an eager learning audience. Networking at Conferences is an unmeasurable deliverable for ARMA, but one can confidently conclude that sharing and exchanging experience and information related to the field of records and information management occurs from the moment one registers for a conference.
Most of us head off to the annual ARMA Canada Conference happy to be a participant and receive thoughtfully orchestrated education. When one considers the responsibilities that a Conference team assumes, it becomes apparent that Conference success is achieved through a devotion of the committee members’ personal time, effort prior and during the conference.
Annual ARMA Canada conferences are a tribute to the pioneers who organized the First Canadian Conference on Records Management in 1980. Imagine how they celebrated the obvious success of their investment! They created the path for us to continue to develop and advance standards of professional competence in the field of records and information management.
Interviewer: In spite of all the difficulties in records management, why do you remain in the field?
King Lear: I am tied to the stake, and I must stand the course.6
Works Cited
1Canadian Notes by Don H. Bell, ARMA Quarterly April 1980 p52
2Ibid
3William J. Gray, CRM ARMA Montreal Chapter; author – “Correspondence Course in Systems and Procedures” ARMA Quarterly October 1980 p 20
4Jim Coulson, CRM, FAI, author – “Some Personal Reflections on the History of RIM in Canada”, Sagesse Spring 2016 Vol. 1 Issue 1
5ARMA Quarterly April 1979 p 48
6William Benedon Interviews William Shakespeare on Records Management, ARMA Quarterly January 1980 p 30
