Winter 2018 Edition
Winter 2018 Sagesse Publication
- Introduction to Sagesse
- A Record of Service, Bob Morin, CRM. By Sue Rock
- Un recit de service – Bob Morin, CRM. By Sue Rock
- CAN/CBSG 72.34-2017 (French). By Sharon Byrch, Uta Fox & Stuart Rennie
- CAN/CGSB 72.34-2017 (English). By Sharon Byrch, Uta Fox & Stuart Rennie
- Metadata in Recent Canadian Case Law. By Joy Rowe
- Privacy-Driven RIM in Ontario’s Universities. By Carolyn Heald
Biographies
Sharon Byrch is an experienced local government records and privacy manager, working for the Capital Regional District in Victoria, BC. Her mission is helping government digitize and overcome information chaos by optimizing valuable information assets as a ‘single source of managed truth’ through applied IM/ERM strategy, learning and effective partnerships.
Uta Fox, CRM, FAI is the Manager of Records and Evidence Section, Calgary Police Service. She holds a Master’s Degree from the University of Calgary, is a Certified Records Manager and in 2017, made a Fellow of ARMA International – #55. Uta represented ARMA Canada on the Canadian General Standards Board Committee that updated CAN/CGSB 72.34-2017 Electronic records and documentary evidence.
Carolyn Heald is Director, University Records Management and Chief Privacy Officer at Queen’s University in Kingston, Ontario. She started her career as an archivist at the Archives of Ontario before moving into policy and records management. Later, she took on both privacy and records management at York University in Toronto. She holds an MA in History and a Master’s of Library Science, and is a Certified Information Privacy Professional (CIPP/C) from the International Association of Privacy Professionals.
Stuart Rennie, JD, MLIS, BA (Hons.) has a Vancouver, Canada-based boutique law practice where he specializes in records management, privacy and freedom of information, law reform, public policy and information governance law. He is a member of ARMA International’s Content Editorial Board. Stuart is also an adjunct professor at the School of Library, Archival and Information Studies at the University of British Columbia in Vancouver.
Sue Rock, CRM, is owner of The Rockfiles Inc. and an operating partner of Trepanier Rock®, with a focus on ensuring records management principles are embedded into all information management solutions. She is an active supporter of ARMA. Sue influences friends and colleagues with her enthusiasm for historical content captured in ARMA’s IM journals.
Joy Rowe is the Director of Records Management Compliance for a private sector company in metro Vancouver, and she previously worked as the Records Management Archivist at Simon Fraser University. She is a graduate of the School of Library, Archival, and Information Studies at University of British Columbia. She has published articles and presented on topics such as openly-licensed training tools for records creators, accessibility and universal design, and human rights and records. She was one of six selected from an international pool to be part of the 2017-2018 New Professionals Programme of the International Council on Archives.
Sagesse: Journal of Canadian Records and Information Management an ARMA Canada Publication Winter, 2018 Volume III, Issue I
Introduction
ARMA Canada is pleased to announce the launch of its third issue of Sagesse: Journal of Canadian Records and Information Management, an ARMA Canada publication.
This latest edition features a biography of an ARMA Canada pioneer, a thorough review of metadata, a discussion of the Canadian General Standards Board updated CAN/CGSB 72.34-2017 Electronic records as documentary evidence and a look at privacy challenges at Ontario’s universities in regards to records management.
One of the goals of Sagesse’s editorial team is to honour and bring forward former Canadian members involved with ARMA Canada / ARMA International who have made significant contributions to ARMA and the records and information management (RIM) and information governance (IG) industries. Sue Rock, CRM, accepted this challenge and provided a biography of Bob Morin, CRM. Bob was a founding member of ARMA Canada Region, a founding member of three of ARMA Canada’s chapters and a champion of ARMA International. To learn more about his tremendous achievements, see “A Record of
Service: Bob Morin, CRM,” in this issue. This article has been translated into French.
“Metadata in Canadian case law,” by Joy Rowe is a thorough exploration of metadata and its value focusing on admissibility as well as records identification, retrieval and assisting in the authenticity and integrity of records systems. As well, the article examines case law including those related to the business records exception to the hearsay rule, the best evidence rule and evidence weight, use of standards in authentication and computer-generated versus human-generated electronic records.
And in keeping with the admissibility of electronic records, Sharon Byrch, Uta Fox, CRM, FAI and Stuart
Rennie collaborated to write “The New CAN/CGSB 72.34-2017 Electronic records as documentary
evidence.” They discuss the major changes made from the 2005 version to that of 2017 in regards to legal issues, records management and information technology. The authors wish to thank the Canadian General Standards Board for reviewing this article. Please note: this standard is now available in both French and English and can be obtained at no cost on their website (see the article for the links). This article has also been translated into French.
Carolyn Herald examines “Privacy-Driven RIM in Ontario’s Universities” and the role of privacy as a means of implementing records management in Ontario’s universities. Ontario’s Freedom of Information and Protection of Privacy Act (FIPPA) was amended in 2014 and since then more and more universities have established records management programs because of the recordkeeping amendments. This article is relevant to RIM/IG practitioners in all other industries.
We would like to take this opportunity of thanking you, the RIM and IG professionals that access and use the information in these issues in your workplaces and for education and / or training purposes.
Sagesse’s articles have been downloaded from hundreds of times to over 18,000 downloads. That means this information is relevant, useful, practical and appreciated; ARMA Canada is most pleased to be able to provide this content for you.
Please note the disclaimer at the end of this Introduction which notes that the opinions expressed by the authors are not the opinions of ARMA Canada or the editorial committee. Whether you agree or not with this content, or have other thoughts about it, we urge you to share them with us. If you have recommendations about the publication we would appreciate receiving them. Forward opinions and comments to: armacanadacancondirector@gmail.com.
If you are interested in providing an article for Sagesse, or wish to obtain more information on writing for Sagesse, visit the ARMA Canada’s website – www.armacanada.org – see Sagesse.
Enjoy!
ARMA Canada’s Sagesse’s Editorial Review Committee:
Christine Ardern, CRM, FAI; John Bolton; Alexandra (Sandie) Bradley, CRM, FAI; Stuart Rennie and Uta Fox, CRM, FAI, Director of Canadian Content.
Disclaimer
The contents of material published on the ARMA Canada website are for general information purposes only and are not intended to provide legal advice or opinion of any kind. The contents of this publication should not be relied upon. The contents of this publication should not be seen as a substitute for obtaining competent legal counsel or advice or other professional advice. If legal advice or counsel or other professional advice is required, the services of a competent professional person should be sought.
While ARMA Canada has made reasonable efforts to ensure that the contents of this publication are accurate, ARMA Canada does not warrant or guarantee the accuracy, currency or completeness of the contents of this publication. Opinions of authors of material published on the ARMA Canada website are not an endorsement by ARMA Canada or ARMA International and do not necessarily reflect the opinion or policy of ARMA Canada or ARMA International.
ARMA Canada expressly disclaims all representations, warranties, conditions and endorsements. In no event shall ARMA Canada, it directors, agents, consultants or employees be liable for any loss, damages or costs whatsoever, including (without limiting the generality of the foregoing) any direct, indirect, punitive, special, exemplary or consequential damages arising from, or in connection to, any use of any of the contents of this publication.
Material published on the ARMA Canada website may contain links to other websites. These links to other websites are not under the control of ARMA Canada and are merely provided solely for the convenience of users. ARMA Canada assumes no responsibility or guarantee for the accuracy or legality of material published on these other websites. ARMA Canada does not endorse these other websites or the material published there.
A Record of Service: Bob Morin, CRM
By Sue Rock, CRM
Introduction
A Record of Service: Bob Morin, CRM coincides with the 150th anniversary of Canada as a country. Bob is one of many Canadian records management pioneers who persevered in establishing records management as a profession.
This tribute focuses on Bob’s achievements within the context of professional organizations such as ARMA and ICRM because Bob believed in the need for common organization.
Bob Morin, CRM died on February 17, 2012 in Saskatoon, Saskatchewan. Bob was a records management pioneer in the truest sense. Remembered fondly for his personality and humour, Bob carved his career through vision, determination, strength and perseverance. He found inspiration from his ARMA International colleagues both in Canada and the US. He sought to measure his records management competency by receiving his CRM designation. He demonstrated continuous dedication to industry associations such as ARMA and ICRM wherein he formed life-long professional partnerships and a multitude of personal friendships.
ARMA – How contributions are measured and documented for enduring historical perspective
ARMA employs a system of categories comprising leadership, awards, education, publication and presentations to recognize individual efforts to advance the profession of records management. ARMA membership provides opportunities for individual professional growth, and measures success through these hallmarks. Achievements are documented within ARMA’s historic and present journals.
Bob’s contributions to the profession of records management are documented within ARMA International’s archival collection of journals. The journals, currently known as Information
Management, were previously entitled ARMA Records Management Quarterly commencing 1967, and as the title states, they were published four times per year.
Through his membership as documented within professional organizations, such as ARMA and the ICRM, we begin to derive an understanding of Bob’s personal values, his job involvement, his active participation in decision making, and his motivation – the sphere of influence he created.
ARMA – Leadership and the importance of vision
In 1978 the ARMA Canada Region, designated at the time as “Chapter VIII” was inaugurated. This milestone was achieved through a devotion of time and effort by founding Canadian Chapter Presidents including Bob Morin, Former Regional Vice Presidents, International Officers and Charter Members who remained active in ARMA for a number of years. We celebrate our current Canada Region status in ARMA International as an outcome of their vision and leadership.
At the same time, Bob represented Canada as voting member Regional Vice President 1978-80 on the Board of Directors, ARMA International. ARMA documents that as Region VIII nominee National Office 1978-1979 “Mr. Morin’s education ranges from archival management to computer sciences.”
Bob focused on the role of technology for managing records. The collective term at the time for individual technologies such as microcomputers, FAX machines, and micrographic equipment, was office automation.
The challenge of rapidly emerging technology solutions to records management problems during this era is strikingly similar to those faced in the 21st century. Identification of the role of technology within Bob’s career is paramount to the direction he championed.
By 1980, Bob had already established two ARMA Chapters within Canada: “He was the founder and first president of the Ottawa chapter…and repeated the same organizational effort recently when he moved to Edmonton.”2 On May 2, 1983 the Saskatchewan Chapter was chartered, with Bob as its President, flanked by a stellar ARMA Chapter team.3

ARMA – Awards and recognition
On the basis of his championing the role of technology within records management, Bob received the first Infomatics Award in 1978 for his efforts in implementing a records management program for the Government of Alberta. This achievement award was sponsored by the ARMA Edmonton Chapter, intended to be presented annually to a “deserving person making outstanding contributions in the information processing field.”4 The award description includes “computing and systems” as one of the three primary areas of information and records management at the time.
The first Canadian Conference on Records Management recruited 252 participants to Banff, Alberta February 4-6, 1980. The conference honoured the “ARMA Canadian Pioneers”. Of course Bob was among them! The group comprised “…founding Chapter Presidents, Former Regional Vice Presidents, International Officers and Charter Members who … remained active in ARMA for a number of years … These pioneers were presented with Certificates of Appreciation at a Pioneer Luncheon at the Banff conference, February 6th, 1980.” The pioneers are named, and they represent seven Canadian Chapters at the time: Montreal, Ottawa, Toronto, Winnipeg, Calgary, Edmonton, and Vancouver. 5
An excerpt from one of Bob’s colleagues, Jim Coulson, CRM, FAI breathes life into Bob-the-person with regard to the first Canadian Conference: “Bob Morin, of Saskatoon, was a passionate RIM pioneer who brought records management professionals together from across the country to put on the first Canadian Records and Information conference. Two years later, the conference was held in Montreal, with presentations and proceedings in both official languages. The ARMA Canada conference has since become a highly respected annual event.”6
ARMA – Publication and presentation – hallmarks of contribution
Bob shared his on-the-job experience with the ARMA community through both publication and presentation. These communication channels are highly regarded within the ARMA community.
An article Bob wrote for the The Records Management Quarterly in 1980 entitled “Management Information Systems – a Total Approach” speaks to computer literacy as a continuing theme in his career. The article is not only informs us of the technology components of records management at the time, but also states the importance of integrating the technologies and disciplines: “The approach stresses the need for analysis of clerical systems in the design stages. Cost effectiveness is illustrated by efficient use of all information technologies such as micrographics, word processing, forms design, data processing and library resources.”7
ARMA published an earlier article by Bob in 1976 “Relocating a Records Management Operation”.8 In this article, Bob’s thesis is that the records manager will become involved in office moves due to “his interest in all aspects of paperwork”. These moves vary from a simple re-arrangement to a complete relocation. It provides a step-by-step plan covering both the preparation and the physical movebrequirements of particular value to the records manager. This topic continues to weigh into a records manager’s domain in the 21st century!
In 1983, Bob shared his knowledge in a presentation at the 28th Annual Conference, where the conference theme was “The Emerging Information Economy”. His topic was “What the Records Manager Should Know about Data Processing Systems Documentation”. The synopsis states “…the proper handling of magnetic tapes…How to schedule data processing records such as magnetic tapes, databases, and diskettes will be discussed.”9
ARMA – Promotion of education for records managers
Another cornerstone of ARMA professional activity is the delivery of educational programs. Bob was a leader in this area, too.
While Director of Records Management for the Alberta Government Services from 1975-82, “…he directed an eleven-course Training Program that covered File Management, Records Systems,
Micrographics, Office Automation, Forms Management, and Data Processing…He taught Records Management at the University of Alberta, Faculty of Library Science, where he was instrumental in establishing a Credit Course in Records Management.”10
It has been said by his students and colleagues that Bob was fierce in generosity to help fledglings. He always raised the collective morale of those around him.
As a memorial, the ARMA Saskatchewan Chapter continues to present the Bob Morin Award to a young professional to financially assist with training in the Records Management field.
From ARMA’s checklist for professional status including awards, education, publication, presentation, and sphere of influence, Bob hit the highlights. For any of us who have served in any volunteer capacity one might ponder: “Where did he get the energy?” He didn’t stop with ARMA!
IRMF – International Records Management Federation
In 1978, Bob was named as one of ARMA International’s two delegates to a professional organization called the International Records Management Federation (IRMF).11
Initially, the Federation was designed to serve a world-wide interest that Records Management was experiencing. The The Records Management Quarterly published a column called Outlook for the Federation to share its goals, membership bragging rights, and achievements. “Records Management is no longer an all-American sport although many of we ‘internationals’ still gaze in awe at ARMA – 4800 plus strong and still growing, and what a Management team!”12
By 1982, Bob had graduated to the Federation President’s leadership role.13 A position paper examining the future of the Federation was presented the same year to ARMA International. As a result, a new constitution was reviewed and approved by the Executive Board of the IRMF. It was renamed to International Records Management Council.14 Another “first” for Bob.
ICRM – Institute of Certified Records Managers
Bob went on to assume leadership in and to share his sphere of personal influence with the ICRM — the Institute of Certified Records Managers. He served as an officer of the Board of Regents for the term January 1986 through December 1988.
In conclusion …
Bob is one of many colourful Canadian records management pioneers. Their adaptability, their determination and their drive to achieve have created a remarkable example of excellence in the Canadian records management business scene.
It’s a particular challenge to those of us who remain, or who are new to the profession, to pause, to reflect on their journey. We are in our own records management career hiatus – forging our way, while learning time management skills to prioritize and succeed.
Time for reflection? Consider it a professional vacation. A few minutes to lean backwards into a previous century will reap the reward of inspiration and awe for those who faced very similar circumstances: the influence of society, politics, world events, and, always, the advance of technology.
Bibliography
1”Association News and Events”, ARMA Records Management Quarterly, 12, Number 3 (1978), 51-52
2”Association News and Events”, ARMA Records Management Quarterly, 12, Number 3 (1978), 51-52
3”Association News and Events”, ARMA Records Management Quarterly, 17, Number 3 (1983), 56 4David H. Bell, “Canadian Notes”, ARMA Records Management Quarterly, 13, Number 2 (1979), 48 5Don H. Bell, “Canadian Notes”, ARMA Records Management Quarterly, 14, Number 2 (1980), 52 6Jim Coulson, “Some Personal Reflections on the History of RIM in Canada”, 2017
7Robert P. Morin, “Management Information Systems – A Total Approach”, ARMA Records Management Quarterly, 14, Number 2 (1980) 5-6, 16
8”Records Management Quarterly Cumulative Index of Articles (Annotated) January 1967 – October
1977”, ARMA Records Management Quarterly, 11, Number 4 (1977), 63
9”28th Annual Conference ARMA The Emerging Information Economy”, ARMA Records Management Quarterly, 17, Number 3 (1983) 61
10”ICRM Information”, ARMA Records Management Quarterly, 19, Number 4 (1985), 62
11”Outlook – International Records Management Federation”, ARMA Records Management Quarterly, 12, Number 2 (1978), 55
12Outlook – International Records Management Federation”, ARMA Records Management Quarterly, 12, Number 2 (1978), 55
13ARMA Records Management Quarterly April 1982 page 69
14IRMF Reorganizes: Announces New Publications”, ARMA Records Management Quarterly, 16, Number 2 (1982)
1An emphasis on computer sciences became a key ingredient to Bob’s career in records management.
2ARMA Records Management Quarterly July 1978 pages 51-52
3ARMA Records Management Quarterly July 1983 page 56
4ARMA Records Management Quarterly April 1979 page 48
5ARMA Records Management Quarterly April 1980 page 52
6Some Personal Reflections on the History of RIM in Canada, Jim Coulson, CRM, FAI
7ARMA Records Management Quarterly April 1980 page 5
8ARMA Records Management Quarterly October 1977 page 63
9ARMA Records Management Quarterly July 1983 page 61
10ARMA Records Management Quarterly October 1985 page 62
11ARMA Records Management Quarterly April 1978 page 55
12ARMA Records Management Quarterly April 1978 page 55
Un récit de service: Bob Morin, CRM
par Sue Rock, CRM
Introduction
Un récit de service: Bob Morin, CRM, coïncide avec le 150e anniversaire du Canada en tant que pays. Bob est l’un des nombreux pionniers de la gestion des documents au Canada qui ont persévéré pour l’établissement de la gestion des documents en tant que profession.
Cet hommage se concentre sur les réalisations de Bob dans le contexte d’organisations professionnelles, telles que l’ARMA et l’ICRM, car Bob croyait en la nécessité d’une organisation commune.
Bob Morin, CRM, est décédé le 17 février 2012 à Saskatoon, en Saskatchewan. Bob était un pionnier de la gestion des documents dans le vrai sens du terme. Commémoré affectueusement pour sa personnalité et son humour, Bob a façonné sa carrière avec vision, détermination, force et persévérance. Il trouvait son inspiration parmi ses collègues d’ARMA International, au Canada et aux États-Unis. Il a cherché à mesurer sa compétence en gestion des documents en recevant son titre CRM. Il a fait preuve d’un dévouement constant envers les associations de l’industrie telles que l’ARMA et l’ICRM, où il a formé des partenariats professionnels à vie et une multitude d’amitiés personnelles.
ARMA – Comment les contributions sont mesurées et documentées pour créer une perspective historique durable
ARMA emploie un système de catégories comprenant le leadership, les prix, l’éducation, la publication et les présentations afin de reconnaître les efforts individuels pour faire progresser la profession de gestion des documents. L’adhésion à l’ARMA offre des opportunités de croissance professionnelle aux individus et mesure leur succès grâce à ces caractéristiques. Les réalisations sont documentées dans les revues passées et présentes de l’ARMA.
Les contributions de Bob à la profession de gestion des documents sont documentées dans la collection de revues d’archives d’ARMA International. Les revues, actuellement connues sous le nom de Information Management (Gestion de l’information), étaient auparavant intitulées ARMA Records Management Quarterly (Gestion de documents trimestrielle d’ARMA) à partir de 1967, et comme l’indique le titre, étaient publiées quatre fois par an.
Grâce à son appartenance à des organisations professionnelles telles que l’ARMA et l’ICRM, nous commençons à comprendre les valeurs personnelles de Bob, son implication professionnelle, sa participation active à la prise de décision et sa motivation – la sphère d’influence qu’il a créée.
ARMA – Leadership et importance de la vision
En 1978, la Région canadienne de l’ARMA, désignée à l’époque sous le nom de « Chapitre VIII », a été inaugurée. Ce jalon a été atteint grâce au dévouement en temps et en détermination dont ont fait preuve les présidents de sections canadiennes, tels que Bob Morin, les anciens vice-présidents régionaux, les dirigeants internationaux et les membres fondateurs, qui sont demeurés actifs au sein de l’ARMA pendant plusieurs années. Nous célébrons le statut actuel de notre région dans l’ARMA International grâce à leur vision et leur leadership.
Au même moment, Bob représentait le Canada comme membre votant au poste de vice-président régional 1978-80 au conseil d’administration d’ARMA International. L’ARMA documente que, en qualité de candidat à la Région VIII, Bureau national 1978-1979 « La formation de M. Morin s’étend de la gestion des archives à l’informatique. » 1 L’accent mis sur les sciences informatiques est devenu un élément clé du succès de la carrière de Bob dans la gestion des documents.
Bob s’est concentré sur le rôle de la technologie dans la gestion des documents. Le terme général de l’époque pour les technologies individuelles, telles que les micro-ordinateurs, les télécopieurs et l’équipement micrographique, était la bureautique.
Le défi que représentaient les solutions technologiques émergentes face aux problèmes de gestion des documents de l’époque est étonnamment semblable à celui du XXIe siècle. L’identification du rôle de la technologie dans la carrière de Bob est primordiale dans la direction qu’il défend.
Dès 1980, Bob avait déjà établi deux sections d’ARMA au Canada: « Il a été le fondateur et le premier président de la section d’Ottawa…et a récemment répété les mêmes efforts organisationnels lorsqu’il a déménagé à Edmonton. 2 » Le 2 mai 1983, la section de la Saskatchewan a été agréée, avec Bob en tant que président, encadré par une excellente équipe de la section d’ARMA. 3




ARMA – Prix et reconnaissance
En promulguant le rôle de la technologie dans la gestion des documents, Bob a remporté le premier Prix de l’informatique en 1978 pour ses efforts dans la mise en œuvre du programme de gestion des documents du gouvernement de l’Alberta. Ce prix d’excellence a été parrainé par la section ARMA d’Edmonton, et devait être présenté annuellement à la « personne méritante apportant des contributions exceptionnelles dans le domaine du traitement de l’information ». La description du prix inclut « informatique et systèmes » comme l’un des trois principaux domaines de gestion d’information et de documents de l’époque. 4
La première conférence canadienne sur la Gestion des documents a accueilli 252 participants à Banff, en Alberta, du 4 au 6 février 1980. La conférence a honoré les « Pionniers canadiens ARMA ». Bien sûr, Bob était parmi eux! Le groupe était constitué de « …présidents fondateurs de section, anciens vice-
présidents régionaux, officiels internationaux et membres fondateurs qui…sont restés actifs dans l’Arma pendant plusieurs années… Des certificats d’appréciation leur ont été décernés au Déjeuner des Pionniers, à la conférence de Banff, le 6 février 1980. » Les pionniers sont nommés et ils représentent sept sections canadiennes de l’époque : Montréal, Ottawa, Toronto, Winnipeg, Calgary, Edmonton et Vancouver. 5
Une citation d’un des collègues de Bob, Jim Coulson, CRM, FAI, insuffle de la vie au personnage, au moment de la première Conférence canadienne: « Bob Morin, de Saskatoon, a été l’un des pionniers passionnés de CRI, qui réunit des professionnels de gestion de documents provenant des quatre coins du pays, et a organisé la première Conférence sur les documents et l’information au Canada. Deux ans plus tard, la conférence a eu lieu à Montréal, avec des présentations et des procédures dans les deux langues officielles. La conférence d’ARMA Canada est depuis lors devenue un événement annuel hautement respecté. » 6
ARMA – Publication et présentation – emblèmes de la contribution
Bob a partagé son expérience pratique avec la communauté ARMA grâce aux publications et aux présentations. Ces canaux de communication sont hautement respectés au sein de cette communauté.
Un article que Bob a écrit pour le Records Management Quarterly en 1980, intitulé « Gestion de systèmes d’information – une approche globale », montre comment l’alphabétisation informatique est un thème continu de sa carrière. L’article ne fait pas que nous informer sur les composantes technologiques de la gestion des archives de l’époque, mais souligne également l’importance de l’intégration des technologies et des disciplines: « L’approche met l’accent sur le besoin d’analyse des systèmes cléricaux dans leurs phases de conception. La rentabilité est illustrée par l’utilisation efficace de toutes les technologies de l’information telles que la micrographie, le traitement de texte, la conception de formulaires, le traitement de données et les ressources documentaires. » 7
ARMA a publié un article antérieur de Bob, datant de 1976 et intitulé « Relocating a Records Management Operation. » 8 Dans cet article, la thèse de Bob est que le gestionnaire de documents s’impliquera dans les déménagements de bureaux en raison de « son intérêt pour tous les aspects de la paperasserie ». Ces mouvements vont d’un simple réaménagement à une délocalisation complète. Il fournit un plan, étape par étape, couvrant à la fois les exigences de préparation et de déplacement physique, d’une valeur particulière pour le gestionnaire de documents. Ce sujet continue d’être d’actualité pour les gestionnaires de documents du 21e siècle!
En 1983, Bob a partagé ses connaissances lors d’une présentation à la 28e conférence annuelle, où le thème de la conférence était « L’économie émergente de l’information ». Son sujet était « Ce que le gestionnaire de documents doit savoir sur la documentation des systèmes de traitement de données ». Le synopsis indique que la présentation inclut « …la manipulation correcte des bandes magnétiques…La façon de planifier les enregistrements de traitement de données, tels que les bandes magnétiques, les bases de données et les disquettes, sera discutée. » 9
ARMA – Promotion de la formation pour les gestionnaires de documents
Une autre pierre angulaire de l’activité professionnelle de l’ARMA est la prestation de programmes de formation. Bob était aussi un leader dans ce domaine.
De 1975 à 1982, alors qu’il était directeur de la gestion des documents pour le Gouvernement de
l’Alberta, « il a dirigé un programme de formation de onze cours portant sur la gestion de documents, les systèmes de documents, la micrographie, la bureautique, la gestion de formulaires et le traitement de données… Il a enseigné la Gestion de documents à la faculté de bibliothéconomie de l’Université de l’Alberta, où il a joué un rôle déterminant dans l’établissement d’un cours crédité sur la gestion des documents. »10
Ses étudiants et ses collègues ont dit de Bob qu’il était acharné dans sa générosité pour aider les jeunes. Il a toujours soulevé le moral collectif de ceux qui l’entouraient.
En hommage, la section de l’ARMA de la Saskatchewan continue de remettre le prix Bob Morin à un jeune professionnel, pour l’aider financièrement dans le domaine de la gestion des documents.
De la liste de contrôle ARMA pour le statut professionnel, y compris les prix, l’éducation, la publication, la présentation et la sphère d’influence, Bob a souligné les grandes lignes. Pour ceux d’entre nous qui ont servi à titre de bénévoles, on peut se demander: « Où prenait-il son énergie? » Et il ne s’est pas arrêté avec ARMA!
IRMF – International Records Management Federation
En 1978, Bob a été choisi pour être l’un des deux délégués d’ARMA International à une organisation professionnelle appelée International Records Management Federation (Fédération internationale de gestion des documents) (IRMF). 11
Au départ, la Fédération a été établie pour servir un intérêt mondial pour la gestion des documents. Le Records Management Quarterly a publié une rubrique intitulée Outlook for the Federation afin de partager ses objectifs, ses motifs de fierté et ses réalisations. « La Gestion de documents n’est plus un sport entièrement américain, bien que plusieurs parmi nous “internationaux” admirent toujours ARMA – fort de plus de 4 800 membres et toujours en augmentation, et quelle équipe de gestion! » 12
En 1982, Bob avait un rôle de leadership pour le président de la Fédération.13 Un document de réflexion sur l’avenir de la Fédération a été présenté la même année à ARMA International. En conséquence, une nouvelle constitution a été examinée et approuvée par le Conseil exécutif du IRMF, qui a été renommé International Records Management Council (IRMC -Conseil International d’Administration des Archives).14 Une autre “première” pour Bob.
ICRM – Institute of Certified Records Managers
Bob a continué à assumer le leadership et à utiliser sa sphère d’influence personnelle avec l’ICRM – Institute of Certified Records Managers (Institut des gestionnaires de documents certifiés). Il a été membre du Conseil d’administration de janvier 1986 à décembre 1988.
En conclusion …
Bob est l’un des nombreux pionniers de la gestion des documents au Canada. Leur capacité d’adaptation, leur détermination et leur volonté de réussir créent un remarquable exemple d’excellence dans le domaine de la gestion des documents au Canada.
C’est un défi particulier pour ceux d’entre nous qui restent, ou qui sont nouveaux dans la profession, de faire une pause, de réfléchir sur leur parcours. Nous suivons notre propre parcours de carrière en gestion des documents – forgeant notre chemin, tout en acquérant des compétences de gestion de temps pour établir des priorités et réussir.
C’est le temps de réfléchir? Considérez cela comme des vacances professionnelles. Quelques minutes passées à retourner dans le siècle précédent vous donneront comme récompense l’inspiration et de l’admiration pour ceux qui ont fait face à des circonstances très semblables: l’influence de la société, la politique, les événements mondiaux et, toujours, le progrès de la technologie.
Bibliographie
1”Association News and Events”, ARMA Records Management Quarterly, 12, Numéro 3 (1978), 51-52
2”Association News and Events”, ARMA Records Management Quarterly, 12, Numéro 3 (1978), 51-52
3”Association News and Events”, ARMA Records Management Quarterly, 17, Numéro 3 (1983), 56 4David H. Bell, “Canadian Notes”, ARMA Records Management Quarterly, 13, Numéro 2 (1979), 48 5Don H. Bell, “Canadian Notes”, ARMA Records Management Quarterly, 14, Numéro 2 (1980), 52 6Jim Coulson, “Some Personal Reflections on the History of RIM in Canada”, 2017
7Robert P. Morin, “Management Information Systems – A Total Approach”, ARMA Records Management Quarterly, 14, Numéro 2 (1980) 5-6, 16
8”Records Management Quarterly Cumulative Index of Articles (Annotated) janvier 1967 – octobre 1977”, ARMA Records Management Quarterly, 11, Numéro 4 (1977), 63
9”28th Annual Conference ARMA The Emerging Information Economy”, ARMA Records Management Quarterly, 17, Numéro 3 (1983) 61
10”ICRM Information”, ARMA Records Management Quarterly, 19, Numéro 4 (1985), 62
11”Outlook – International Records Management Federation”, ARMA Records Management Quarterly, 12, Numéro 2 (1978), 55
12Outlook – International Records Management Federation”, ARMA Records Management Quarterly, 12, Numéro 2 (1978), 55
13”IRMF Reorganizes: Announces New Publications”, ARMA Records Management Quarterly, 16, Numéro 2 (1982)
14IRMF Reorganizes: Announces New Publications”, ARMA Records Management Quarterly, 16, Numéro 2 (1982)
1ARMA Records Management Quarterly, juillet 1978 pages 51-52
2ARMA Records Management Quarterly, juillet 1978 pages 51-52
3ARMA Records Management Quarterly, juillet 1983 page 56
4ARMA Records Management Quarterly, avril 1979 page 48
5ARMA Records Management Quarterly, avril 1980 page 52
6Some Personal Reflections on the History of RIM in Canada, Jim Coulson, CRM, FAI
7ARMA Records Management Quarterly, avril 1980 page 5
8ARMA Records Management Quarterly October 1977 page 63
9ARMA Records Management Quarterly, juillet 1983 page 61
10ARMA Records Management Quarterly, octobre 1985 page 62
11ARMA Records Management Quarterly, avril 1978 page 55
12ARMA Records Management Quarterly, avril 1978 page 55
13ARMA Records Management Quarterly, avril 1982 page 69
14ARMA Records Management Quarterly, avril 1982 page 69
CAN/CGSB 72.34-2017 ENREGISTREMENTS ÉLECTRONIQUES UTILISÉS À TITRE DE PREUVES DOCUMENTAIRES
Par Sharon Byrch, Uta Fox, CRM, FAI et Stuart Rennie JD, MLIS, BA (Hons.)
Introduction
En mars 2017, l’Office des normes générales du Canada (ONGC) a publié la nouvelle norme sur les Enregistrements électroniques utilisés à titre de preuves documentaires, CAN/CGSB-72.34- 2017. Cette nouvelle norme annule et remplace la version de 2005, CGSB 72.34-2005. Deux des auteurs de cet article, Uta Fox et Stuart Rennie, étaient membres du comité de l’ONGC qui a élaboré la CAN/CGSB-72.34-2017. Ayant co-présenté les deux versions de la norme CAN/CGSB-
- dans les conférences nationales d’ARMA Canada et dans les sections d’ARMA Canada à travers le pays, ils sont fréquemment contactés afin de fournir plus d’informations sur cette norme. Cet article répond à ces demandes d’informations de la communauté de gestion des documents (GD) sur la mise à jour de 2017, et sur comment l’appliquer.
Afin d’élargir la portée de cet article, ils ont abordé Sharon Byrch, professionnelle de la GD, qui a accepté de collaborer à sa rédaction. Il traite des différences majeures amenées par la norme CAN/CGSB-72.34-2017 comparativement à la version de 2005, du point de vue juridique, de gestion des documents (GD) et des technologies de l’information (TI). Bien que l’accent soit mis principalement sur les changements importants au contenu, il contient certaines recommandations pour la mise en œuvre de la norme dans vos programmes de gestion des documents et de gouvernance de l’information (GI).
Dans cet article, les opinions exprimées par les auteurs sont personnelles et ne sont affiliées à aucun organisme. Les informations fournies sont basées sur leurs expériences et sur les connaissances qu’ils ont acquises, et sont uniquement partagées à titre informationnel, et non dans le but de fournir des conseils juridiques, techniques ou professionnels.
L’objectif de la norme CAN/CGSB-72.34-2017 est de suggérer des principes et des procédures que les organismes peuvent appliquer afin d’améliorer l’admissibilité de leurs enregistrements électroniques à titre de preuve dans les procédures judiciaires. La norme CAN/CGSB-72.34-2017 est une norme volontaire, disponible à l’achat en français et en anglais, et peut être obtenue en format papier ou en version électronique. La norme CAN/CGSB-72.34-2017 ne remplace pas les conseils juridiques et techniques d’experts.
L’ONGC est un organisme du gouvernement fédéral canadien qui aide à l’élaboration de normes dans de nombreuses industries. Actuellement, il y a plus de 300 normes à l’ONGC. Ces normes sont élaborées par un comité de bénévoles, experts dans leurs domaines respectifs. L’ONGC est accrédité par le Conseil canadien des Normes (CCN), une société d’état fédérale, à titre d’organisme d’élaboration de normes. Son mandat est de promouvoir des normalisations efficientes et efficaces au Canada. La norme CAN/CGSB-72.34-2017 est une norme nationale du Canada, comme en témoigne l’inclusion du préfixe «CAN» dans son numéro de référence, ce qui indique qu’elle est reconnue comme norme canadienne officielle dans un domaine particulier. 1
Lors de la lecture de la norme, les utilisateurs doivent être attentifs au langage utilisé par l’ONGC pour que les organismes puissent se conformer à la norme. Prenez le mot « doit » par exemple, souvent utilisé dans CAN/CGSB-72.34-2017. “Doit” implique des exigences obligatoires. Par exemple, “Un organisme doit établir le programme de GD”.2 Ceci est une déclaration d’obligation. Autrement dit, les organismes qui utilisent cette norme doivent avoir en place un programme de GD autorisé. Le mot « devrait » indique une recommandation tandis que « peut » correspond à une option, ou ce qui est permis dans les limites de la présente norme.
En plus de démontrer l’intégrité, l’authenticité et la fiabilité des enregistrements électroniques afin de répondre aux exigences en matière de preuve, les organismes doivent s’assurer que les enregistrements électroniques qu’ils créent, reçoivent et conservent dans les systèmes de tenue d’enregistrements électroniques sont conformes aux exigences du CAN/CGSB-72.34- 2017, afin d’assurer leur admissibilité dans les instances judiciaires. Comme indiqué:
Cette norme fournit un cadre et des lignes directrices pour la mise en œuvre et l’exploitation des systèmes de dossiers pour les enregistrements électroniques, que les renseignements qu’ils contiennent soient ou non éventuellement requis à titre de preuve. Ainsi, le respect de cette norme doit être considéré comme une démonstration de gestion responsable des affaires.
L’application de la norme aux procédures d’un organisme n’éliminera pas la possibilité de litiges, mais il est fort probable que cela rendra la production d’enregistrements électroniques plus faciles et leur acceptation dans une procédure juridique plus certaine.3
L’un des changements apportés grâce à la mise à jour CAN/CGSB-72.34-2017 est que l’ONGC a retiré une norme complémentaire : CAN/CGSB-72.11-93 Microfilms et images électroniques à titre de preuve documentaire. Ce retrait est entré en vigueur le 24 janvier 2017.4 Le raisonnement qui a mené au retrait de la norme CAN/CGSB-72.11-93 est dû à son utilisation limitée et à l’appui général au sujet de sa révision. De plus, la section 3 de la partie III et la section 3 de la partie IV, traitant des images électroniques dans la norme CAN/CGSB 72.11-93, sont incorporées dans la norme CAN/CGSB-72.34-2017. Les organismes peuvent toujours utiliser et référencer CAN/CGSB-72.11-93, mais cela n’est pas recommandé, puisqu’elle n’a plus de poids et n’est plus appuyée par l’ONGC. Par conséquent, les organismes devraient utiliser la version la plus récente de la norme, la CAN/CGSB-72.34-2017.
Exigences juridiques relatives aux enregistrements électroniques à titre de preuves documentaires
La section 5 de la norme CAN/CGSB-72.34-2017 détermine les exigences juridiques applicables aux enregistrements électroniques à titre de preuve documentaire.
Comme la version 2005, la nouvelle norme 2017 se concentre sur ces exigences juridiques en matière de recevabilité juridique:
[L ‘] utilisation d’un enregistrement électronique à titre de preuve exige la démonstration de l’authenticité de l’enregistrement, qui peut être faite en démontrant l’intégrité du système de dossiers électroniques dans lequel l’enregistrement est fait ou reçu ou stocké, et en démontrant que l’enregistrement a été fait “dans le cours normal des affaires” ou est par ailleurs exempté de la règle juridique interdisant le ouï-dire. 5
Il en résulte que les versions 2017 et 2005 sont essentiellement les mêmes, afin que les organismes utilisant la norme de 2005 puissent modifier leurs politiques, procédures et flux de travail pour se conformer à la nouvelle norme CAN/CGSB-72.34-2017 sans avoir à recommencer. Ce qui est pratique.
La norme CAN/CGSB-72.34-2017 fait constamment référence à la Loi sur la preuve au Canada et ne mentionne pas les lois provinciales ou territoriales. Les organismes qui ne sont pas assujettis à la juridiction fédérale canadienne devront examiner la loi provinciale ou territoriale qui s’applique à eux, au sujet de leurs enregistrements électroniques.
De plus, les organismes peuvent utiliser d’autres sources d’informations juridiques pour comprendre comment les cours et tribunaux du Canada interprètent ces exigences juridiques. Une source d’information utile à ce sujet est le site Web de l’Institut canadien d’information juridique: https://www.canlii.org/. CanLII, un organisme non gouvernemental à but non lucratif, offre en ligne un accès gratuit à des jugements de tribunaux, décisions judiciaires, lois et règlements provenant de toutes les provinces et de tous les territoires du Canada, avec une interface de recherche facile à utiliser. L’information juridique est disponible en anglais et en français. CanLII est l’une des meilleures sources d’information pour les avocats, ainsi que le grand public, pour consulter la loi canadienne.
La section5 de la norme CAN/CGSB-72.34-2017 souligne à juste titre que les organismes doivent prouver que leurs enregistrements électroniques sont juridiquement admissibles. Deux outils clés pour la preuve que les organismes peuvent utiliser sont: (1) Manuel de GD (2) Guide de gestion du système informatique. Ces outils devraient contenir les politiques et procédures autorisées de l’organisme servant à fournir les preuves documentaires que celui-ci satisfait les exigences en matière d’admissibilité juridique de ses enregistrements électroniques.
La norme CAN/CGSB-72.34-2017 comporte de nouveaux éléments pour refléter les changements technologiques depuis 2005:
- Découverte électronique (preuve électronique);
- Révision assistée par la technologie (RAT) utilisant un logiciel spécifique de recherche;
- Mise en suspens pour des raisons juridiques; et
- Signatures électroniques et
Découverte électronique (preuve électronique) et préparation aux litiges
Dans la section 5.3, pour la première fois, CAN/CGSB-72.34-2017 fait référence à la découverte électronique au cours de litiges civils. La découverte électronique est une procédure préalable au procès, où les parties en litige sont tenues d’échanger les enregistrements électroniques pertinents, sous la supervision des tribunaux. Puisque les organismes créent et enregistrent maintenant des enregistrements électroniques en plus grand nombre, leur défi est de pouvoir rechercher, consulter et produire les enregistrements électroniques pertinents requis par les tribunaux canadiens, afin qu’ils puissent être admissibles à titre de preuve dans les procédures judiciaires.
En 2008, pour aider les organismes à la production d’enregistrements électroniques admissibles au Canada, les Principes de Sedona Canada portant sur la découverte électronique (Principes de Sedona Canada) ont été élaborés. Sedona Canada est une organisation bénévole non gouvernementale regroupant avocats, juges et technologues à travers le Canada. Les Principes de Sedona Canada sont en grande partie une norme volontaire, comme l’ONGC, sauf en Ontario. Depuis 2010, les principes de Sedona Canada sont obligatoirement utilisés dans les tribunaux de l’Ontario, en vertu des Règles de procédure civile de la province. À l’extérieur de l’Ontario, les principes de Sedona Canada sont acceptés dans les cours et les tribunaux du pays pour aider les parties à produire et à consulter les enregistrements électroniques pertinents, en temps opportun et de manière efficace et économique. À l’heure actuelle, il existe une jurisprudence canadienne en cours de développement en matière de Principes de Sedona Canada.
En 2015, à l’instar des changements apportés par l’ONGC en 2017 à la norme CAN/CGSB-72.34- 2005, Sedona Canada, pour tenir compte des changements dans les domaines technologiques et juridiques, a publié une deuxième édition mise à jour des Principes de Sedona Canada.6
En ce qui concerne la divulgation dans les procédures pénales, le CAN/CGSB-72.34-2017 est référé, pour la première fois, dans R. c. Oler, 2014 ABPC 130 (CanLII).7 L’affaire Oler est un cas majeur pour plusieurs raisons. Premièrement, Oler est la première instance à considérer et à appliquer la norme CAN/CGSB-72.34 de 2005. Deuxièmement, Oler est aussi le premier cas au Canada à soutenir que le processus de numérisation d’un organisme est admissible à titre de preuve électronique, parce qu’il est conforme à la Loi sur la preuve au Canada, et à l’Alberta Evidence Act pour son utilisation des standards industriels. Troisièmement, le tribunal dans
l’affaire Oler est le premier au Canada à accepter la preuve d’expert en gestion des dossiers. L’expert dans l’affaire Oler était Uta Fox, co-auteure de cet article. Uta Fox est la première gestionnaire de GD reconnue au Canada pour avoir été acceptée à titre de témoin expert juridique qualifiée. À ce titre, elle a aidé le tribunal à déterminer l’admissibilité juridique d’enregistrements électroniques.
Il existe peu de jurisprudences au Canada sur la relation entre la GD et la loi. Il en faut plus, afin de faire progresser la profession de gestion des documents électroniques et de l’information, ainsi que l’admissibilité des documents, en particulier les enregistrements électroniques, dans les tribunaux canadiens. Cette situation devient d’autant plus critique au fur et à mesure que les organismes deviennent de plus en plus « numériques » et ne créent et gèrent que des enregistrements électroniques, et non des documents papier. Compte tenu de la prédilection des tribunaux canadiens à faire référence à des Normes nationales du Canada approuvées, telle que CAN/CGSB-72.34-20, l’affaire Oler est un pas dans la bonne direction pour la gestion des documents électroniques et de l’information.
Il est de plus en plus nécessaire que les professionnels de la GD soient acceptés devant les tribunaux en tant qu’experts, comme Uta Fox l’a été, pour les aider à déterminer l’admissibilité de la preuve électronique. Les tribunaux canadiens ne qualifient pas les personnes d’experts à la légère. Ils exigent des preuves démontrant qu’une personne possède les qualifications, la formation, les connaissances spécialisées et l’expertise nécessaires pour être qualifiées d’expert. De plus, la personne doit être indépendante et impartiale pour assister le tribunal en tant qu’expert.8 Les organismes qui, à l’instar du Service de police de Calgary dans l’affaire Oler, utilisent des systèmes de gestion des enregistrements électroniques et des documents et des dossiers (SGEDD), exploitent et gèrent des systèmes complexes de GD et de TI, avec des répercussions juridiques dépassant l’expérience du public ou de l’utilisateur occasionnel. Alors que de plus en plus d’organismes passent au SGEDD, il doit y avoir plus d’experts de GD attitrés par les tribunaux pour conseiller sur ces systèmes complexes, afin de déterminer l’admissibilité de leurs enregistrements électroniques dans les affaires civiles et criminelles. Oler est la première affaire au Canada qui autorise l’admissibilité des enregistrements électroniques numérisés à l’aide d’un SGDDE, à la place d’originaux sur papier. Nous devons développer la jurisprudence en matière de GD pour suivre le rythme de l’utilisation des SGDDE en affaires.
D’un point de vue juridique, ce sont des ajouts favorables à la norme. Les organismes peuvent se référer aux Principes de Sedona Canada et à l’affaire Oler, en plus de la norme CGSB 72.34- 2017, comme sources d’information sur les meilleures pratiques crédibles afin d’améliorer encore davantage la conformité juridique de l’organisme, et réduire ses risques juridiques.
Revue assistée par la technologie (RAT) et autres outils et techniques automatisés
La norme de 2005 est muette sur la revue assistée par la technologie. Elle est abordée pour la première fois dans la section 5.3.1 de CAN/CGSB-72.34-2017. La revue assistée utilise la technologie pour automatiser le processus d’identification des enregistrements électroniques pertinents. Comme la preuve électronique, CAN/CGSB-72.34-2017 fait référence aux Principes de Sedona Canada, et avec raison. Les organismes utilisent de plus en plus la revue assistée par la technologie, et la jurisprudence canadienne y fait référence, ce qui en fait un autre ajout favorable.
Mise en suspens pour des raisons juridiques
La section 5.4 de CAN/ONGC-72,34-2017 fait référence à une « mise en suspens pour des raisons juridiques », qui était absente de la norme de 2005. De plus en plus appliquée à tous les dossiers, une mise en suspens pour des raisons juridiques est un processus où un organisme conserve toute forme de document potentiellement pertinent lorsque le litige est raisonnablement prévu, ou en cours. Le risque encouru par un organisme pour ne pas avoir préservé les preuves électroniques sous une mise en suspens pour des raisons juridiques est que des preuves pertinentes soient détruites par inadvertance, et donc indisponibles aux tribunaux pour déterminer la responsabilité ou la décharge. Quand un organisme détruit par inadvertance des preuves importantes, cela augmente son risque d’avoir à subir des sanctions juridiques par les tribunaux, qui sont mécontents lorsqu’il y a destruction de la preuve, car cela pourrait servir à subvertir la primauté du droit.
La norme CAN/CGSB-72.34-2017 fait référence aux Principes de Sedona Canada concernant les mises en suspens pour des raisons juridiques. Ensemble, la CAN/CGSB-72.34-2017 et les Principes de Sedona Canada permettent aux organismes de bien comprendre ce qu’il faut conserver, comment l’appliquer et comment éviter le risque de détruire ou de spolier par inadvertance des preuves électroniques pertinentes. Les deux normes soulignent le besoin de conseils juridiques d’experts dès que possible lorsqu’une mise en suspens pour des raisons juridiques s’avère nécessaire.
Signatures
Pour ce qui est des signatures, la norme de 2005 ne comporte pas de section spécifique pour les signatures électroniques et papier, elle ne fait que les mentionner au passage.
Quant à la norme CAN/CGSB-72.34-2017, elle consacre la section 5.5 aux signatures électroniques et manuscrites. Une signature manuscrite est généralement faite en encre, avec un sceau de papier ou même avec de la cire traditionnelle. La distinction entre les signatures électroniques et manuscrites est utile. De nombreux organismes utilisent aujourd’hui simultanément les deux types de signatures; il y a souvent confusion et incertitude au sein même des organismes quant à l’admissibilité juridique de ces deux signatures. La norme CAN/CGSB-72.34-2017 fournit les exigences de base pour leur utilisation, et spécifie quand demander l’avis d’un expert pour assurer leur admissibilité juridique.
Copies papier authentifiées pour les procédures judiciaires (« copies certifiées »)
Pour les « copies certifiées », la norme de 2005 de la section 5.6 exigeait que les copies papier soient authentifiées comme une « copie certifiée » de l’original, avec une signature pour améliorer sa recevabilité et son importance devant les tribunaux. Cette authentification devait être documentée avec des procédures.
Dans la version 2017, la section 5.6 est énoncée essentiellement comme la norme de 2005. La principale différence est que la norme de 2005 ne mentionne pas les « dossiers électroniques », ils sont implicites; la norme CAN/CGSB-72.34-2017, quant à elle, utilise l’expression « enregistrements électroniques » pour préciser que les copies d’enregistrements électroniques doivent être authentifiées par signature comme étant des « copies certifiées » des enregistrements électroniques.
La norme CAN/CGSB-72.34-2017 ajoute également qu’un affidavit peut être utilisé comme enregistrement d’authentification; la norme de 2005 ne mentionne pas l’affidavit. La nouvelle référence à l’utilisation d’un affidavit est utile, puisque c’est un outil usuel de preuve dans le processus de litige.
Programme de Gestion des documents (GD)
Les deux versions de la norme CAN/CGSB-72.34 contiennent des dispositions sur l’établissement d’un programme de GD. La version 2005, intitulée « Création d’un système de GD » a été modifiée en 2017 pour devenir « Programme de gestion des documents d’archives ».
Avant de discuter des changements à la GD dans la norme CAN/CGSB-72.34-2017, passons en revue ce qui est reporté de la norme de 2005, puisque ce sont des éléments essentiels pour votre programme de GD. Les sections 6.1 à 6.4.1 de la norme CAN/CGSB-72.34-2017 traitent des éléments fondamentaux qu’un organisme doit posséder en ce qui concerne: les concepts de GD, principes, méthodes et pratiques adoptés par l’organisme doivent démontrer qu’un programme de GD approprié est en place et fait partie intégrante du processus habituel et normal des activités de l’organisme en question.9
Par conséquent, les organismes doivent avoir :
- Un programme de GD autorisé;
- Une politique de GD autorisée;
- Un manuel de GD autorisé; et
- Un archiviste.10
À la section 6.1, il est mentionné que le programme de gestion des documents lui-même « doit prendre en charge un système de dossiers composé de procédures et de contrôles des dossiers appropriés qui complémentent les procédures opérationnelles de l’entreprise. »11 Un organisme doit:
- Établir le programme de GD;
- Élaborer une politique de GD, avec des définitions et des attributions de responsabilités;
- Concevoir des procédures de GD avec sa documentation connexe;
- Sélectionner et mettre en œuvre des technologies soutenant le système de GD;
- Établir des mesures de protection des documents, y compris des pistes de vérification et de sauvegarde; et
- Établir un processus d’assurance qualité des documents.12
Remarquez, ces déclarations sont des déclarations “doit”; ce qui signifie que l’organisme doit soutenir les systèmes de GD en utilisant des procédures d’enregistrement et des contrôles appropriés en harmonie avec les opérations commerciales.
Les organismes doivent établir un programme de GD, avoir une politique GD, utiliser des définitions, attribuer des responsabilités, élaborer des procédures, sélectionner des technologies, mettre en œuvre des processus de protection des documents et adopter un programme d’assurance qualité. Ce sont des facteurs non négociables qui doivent être en place avant même que l’organisme puisse commencer à se conformer à cette norme.
Responsabilité – Archiviste
Les deux versions, soit celle de 2005 et de 2017 du CAN/ONGC72.34, imposent aux organismes de nommer un archiviste, qui sera responsable de la mise en œuvre du programme de GD, et qui assurera son intégration aux activités régulières de l’organisme. De plus, l’archiviste est responsable de certifier que l’organisme met en œuvre la politique, le programme, et le manuel de GD. Le rôle et les responsabilités de l’archiviste doivent être définis dans une politique, un règlement ou une directive, car son rôle est essentiel à l’établissement et au maintien du programme de GD, et à la supervision de la conformité de l’organisme aux lois, normes et politiques ayant un impact sur le programme.
La norme CAN/CGSB-72.34-2017 fournit des directives à l’archiviste en reconnaissant que la politique de l’organisme lui confère la responsabilité de maintenir et de modifier «…le manuel de GD, avec le soutien du personnel de TI, afin qu’il reflète l’état exact des documents d’archives et puisse constituer une preuve de la conformité du système avec la loi et cette norme.»13 Les responsabilités des employés ayant des fonctions de GD doivent également être définies à des fins de vérification de conformité. Cette directive s’applique à tous les employés d’un organisme qui ont des fonctions de GD, pas seulement les employés du département de GD. Afin de se conformer à la norme CGSB 72.34-2017, assurez-vous que votre organisme remplisse les exigences et les devoirs de la GD pour tous vos employés.
Politique de GD
Les deux versions de l’ONGC soulignent que la haute direction doit autoriser une politique de GD qui stipule que la gestion des enregistrements électroniques fait partie intégrante du cours normal des activités de l’organisme. De plus, la politique doit identifier et élaborer sur:
- Les dossiers applicables, systèmes de dossiers et exclusions (portée);
- Les normes pertinentes de GD et de la technologie de l’information, utilisées dans les programmes de GD;
- La responsabilité de l’archiviste pour le système de dossiers;
- La conformité du système de dossiers avec le manuel de GD, la loi, les normes nationales, internationales et industrielles;
- La responsabilité de l’archiviste quant au maintien et la mise à jour du manuel de GD;
- Les exigences relatives à la création, à la gestion, à l’utilisation et à la disposition des documents;
- Le travail conjoint du département informatique avec l’archiviste pour intégrer la GD dans le processus habituel des affaires; et
- Les processus de l’assurance qualité sont attribués à l’archiviste.14
Manuel de GD
Le manuel de GD est l’outil qui sert à regrouper toutes les procédures liées aux documents, afin d’assurer l’exhaustivité et la cohérence de la pratique15, et qui sont incluses dans les deux versions de la norme CAN/CGSB-72.34. Les composants requis d’un manuel de GD, par exemple les procédures pour faire, recevoir, sauvegarder et supprimer des documents, sont également cohérents entre les versions. CAN/CGSB-72.34-2017 souligne que le manuel de GD:
devra être tenu à jour et refléter avec précision la nature exacte, les fonctions, procédures et processus du système électronique de l’organisme, c’est-à-dire la façon dont ce système participe et soutient le processus habituel des affaires;16
La norme CAN/CGSB-72.34-2017 indique que le manuel doit spécifier le fonctionnement et l’utilisation des systèmes électroniques et inclure des références à d’autres documents pertinents, par exemple le Guide de gestion du système des TI, les procédures opérationnelles ou la documentation du système des TI.17 Voilà un autre exemple de la norme contraignant les TI et la GD à collaborer pour se conformer aux exigences.
Alors que la GD communique ses exigences différemment des TI, il est clair que ces deux domaines ont des intérêts communs et le même but final: une meilleure gouvernance de l’information à propos de la gestion des dossiers électroniques. Il est tout à fait stratégique pour la GD et les TI de collaborer, car supporter un domaine fait avancer les buts et les objectifs de l’autre et, finalement, les deux en bénéficient. Les TI et la GD sont essentiellement des expressions différentes d’un même objectif. Vos parties prenantes se superposent en partie, vous partagez les mêmes risques et conséquences, ressources et priorités.
Le futur de la GD dépend de son implémentation et intégration réussie, à l’intérieur même d’un organisme. Les rouages internes entre la GD et les TI sont décisifs pour cette réussite, et elle ne dépend que de l’implication des deux parties dans cette méthodologie stratégique. Le plus tôt cette coopération de travail, ce développement de ressources, cette communication et assistance pour faire avancer le travail est établie, le mieux cela sera.
Garder le manuel à jour, en utilisant un processus d’examen formel à des moments prédéterminés, garantis que le manuel de GD continue de refléter les activités de GD pour les enregistrements électroniques, en temps réel.18
Votre politique, votre programme, votre manuel et votre archiviste combinés forment les assises et les aspects fondamentaux de vos opérations de GD. Les organismes ne sont pas conformes à la norme CAN/CGSB-72.34-2017 s’ils ne disposent pas d’une politique, d’un programme, d’un manuel ou d’un archiviste et qu’ils sont appelés à produire leurs dossiers électroniques à des fins judiciaires. Comme l’indique la norme CAN/CGSB-72.34-2017, le respect de cette norme « devrait être considéré comme une démonstration de la gestion responsable des affaires ».19
Numérisation
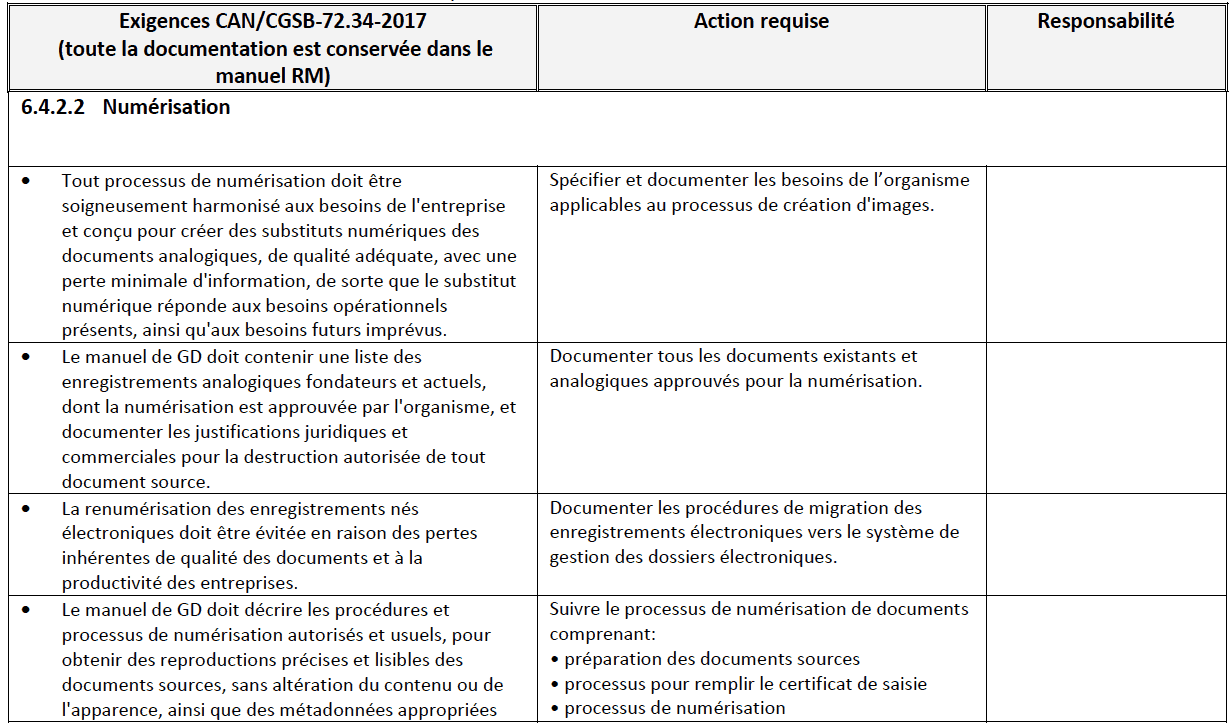
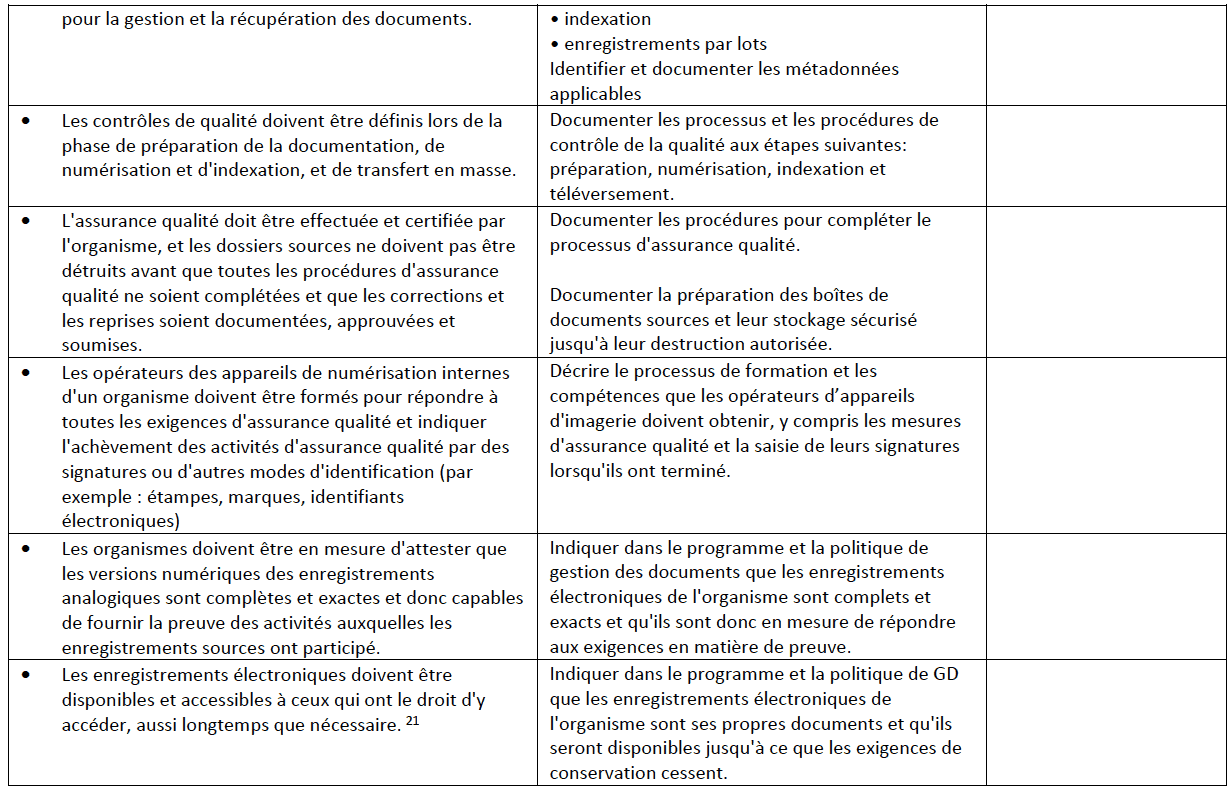
Tel qu’indiqué à la page 3, la norme CAN/CGSB-72.34-2017 incorpore les éléments fondamentaux de Microfilms et images électroniques comme preuve documentaire (CAN/CGSB- 72.34-11-93) requis pour la numérisation. Les organismes qui mettent en œuvre un programme d’imagerie dans leurs programmes de GD peuvent utiliser la liste de contrôle suivante qui énumère les exigences de CAN/CGSB-72.34-201720, décrites dans le Tableau I ci-dessous. Les organismes ayant un programme d’imagerie existant peuvent aussi utiliser cette liste de contrôle comme outil de vérification pour démontrer leur conformité à la norme CAN/CGSB- 72.34-2017.
Cette liste de contrôle fournit les exigences « doit », directement prises de la norme (voir la colonne « Exigences CAN/CGSB-72.34-2017 » ci-dessous). Elle mentionne également les exigences qui doivent être adressées et appliquées, avec la colonne “Action requise”. Enfin, la colonne “Responsabilité” détaillera les postes responsables de la réalisation des actions. Cette liste de contrôle ne contient que des suggestions, et il est fortement recommandé de développer un système de suivi quelconque afin de documenter l’état de l’implémentation et son progrès.
Tableau I
Liste de contrôle pour la numérisation – 6.4.4.4 Numérisations






Exigences de conservation des dossiers
Un certain nombre de modifications ont été apportées à la section sur la conservation des documents dans la norme CAN/CGSB-72.34-2017. La version de 2005 traitait des exigences en matière de consommation, de biens et de services lors de l’attribution de périodes de conservation, tandis que la version de 2017 adopte une approche commerciale générale. La norme CAN/CGSB-72.34-2017 stipule que pour attribuer des périodes de conservation appropriées, les personnes autorisées responsables des fonctions organisationnelles prises en charge par les documents (par exemple, représentation juridique, finances, RH) doivent être incluses dans les décisions d’évaluation et de conservation. Idéalement, les organismes devraient établir un comité de gestion des documents, composé d’experts en la matière, du juridique, de la finance, des ressources humaines et autres responsables, de ces décisions. Les décisions prises par le comité d’autorisation attribuant les périodes de conservation pour les séries de documents doivent être documentées dans le cadre du calendrier de conservation des documents, et liées au système de classification.
La norme fournit plusieurs facteurs critiques d’évaluation qui peuvent ultimement définir les exigences de rétention, notamment:
- Comment l’organisme utilise les documents, à l’interne et à l’externe;
- Le besoin d’accès des utilisateurs en cas de sinistre;
- La valeur financière, juridique, sociale, politique et historique des documents;
- Analyse coûts/avantages de la rétention;
- Impact sur l’organisme si les documents sont détruits; et
- La valeur probante des dossiers si nécessaires pour un litige, un audit ou une enquête.22
Les autres changements apportés à la norme de 2017 portent sur le système de dossiers de l’organisme et sur sa capacité à tenir compte des conservations à date d’échéance fixe, par date d’événement et permanente. L’archiviste doit examiner toutes les dispositions relatives aux dossiers avant qu’une décision de destruction ne soit prise afin de s’assurer que les documents dont l’élimination est prévue ne sont pas assujettis à une mise en suspens pour des raisons juridiques, ou un contrôle organisationnel ou gouvernemental.23 Si tel est le cas, les documents doivent être suspendus du processus de destruction, tel que décrit à la section 5.4 Mise en suspens pour des raisons juridiques de la norme CAN/CGSB-72.34-2017.
Disposition des documents
Il y a des changements importants à la section sur la disposition dans la norme CAN/CGSB- 72.34-2017. La version de 2005 reconnaissait la disposition qui comprenait la destruction des documents et le transfert à une autre entité, mais il n’y avait pas de discussion sur le transfert des documents à un autre organisme ou sur la conservation des dossiers.
La norme CAN/CGSB-72.34-2017 rectifie cette situation en fournissant des détails substantiels sur le processus de disposition, la destruction des enregistrements électroniques, le transfert des documents à une autre entité et les pratiques de préservation des dossiers conservés de façon permanente ou à long terme.
Destruction d’enregistrements électroniques
Tel que mentionné, les deux versions de la norme reconnaissent que les documents doivent d’abord répondre aux exigences de conservation et être autorisées à être éliminées/détruites avant de commencer toute action de disposition. La norme CAN/CGSB-72.34-2017 précise que le manuel GD doit permettre au système d’enregistrement de détruire, de modifier ou de corriger les documents, à l’aide d’un processus modifiable. Quant aux documents qui ont été détruits, les procédures du système doivent assurer que le document, ainsi que son localisateur, sont détruits. Il stipule également que la destruction des documents doit être complétée de manière à ne pas compromettre la confidentialité et la protection des renseignements personnels.24
Transfert d’enregistrements électroniques à une autre entité
Dans la section 6.4.6.4 de la norme CAN/CGSB-72.34-2017, il est stipulé que le manuel GD d’un organisme doit documenter tous les documents transférés et acceptés par les archives (ou une autre entité), et que l’organisme qui transfère les documents et celui qui les reçoit doivent maintenir cette documentation. L’organisme destinataire peut exiger des informations supplémentaires telles que: l’identité du matériel et des logiciels qui ont généré les enregistrements, la documentation du programme décrivant le format, les codes de fichier, la disposition des fichiers et autres détails techniques du système de documents dans lequel les documents résidaient.25
Conservation des documents
La section 6.4.6.5 de la norme CAN/CGSB-72.34-2017 reconnaît que les organismes doivent s’assurer que leurs manuels de GD insistent sur le fait que la conservation des documents débute avec la création et la conservation des documents en formats de fichiers conservables, qui enregistrent les métadonnées d’identité et de tenue de documents requis. Tout au long du cycle de vie des documents, les organismes doivent démontrer que les enregistrements électroniques ont été créés, reçus et conservés dans le cours normal de leurs affaires et continuent de répondre aux exigences d’admissibilité en assurant leur authenticité.
Les organismes tenus de conserver des documents de manière permanente doivent s’assurer que leurs systèmes de tenue de documents sont capables de tenir en permanence des registres
– surtout à considérer lors de la sélection des systèmes de dossiers, tout comme la protection des documents contre l’obsolescence de logiciels.26
Conversion des documents et migration
La section 6.4.6.5.2 de la norme CAN/CGSB-72.34-2017 décrit la conversion des documents comme étant le changement d’informations enregistrées d’un format à un autre, tandis que la migration est le déplacement d’informations enregistrées d’un système des TI à un autre (les deux sont des méthodes d’éviter l’obsolescence des programmes, et les deux comportent des risques). La norme dénote qu’il y a deux types d’obsolescence :
- L’obsolescence des formats de fichiers – lorsque le programme ne peut ouvrir ou visionner le contenu du document. L’obsolescence des formats de fichiers peut être évitée par la conversion des documents ou le déplacement d’un document d’un format à un autre;
- L’obsolescence des systèmes – lorsqu’un système ou une application n’est plus supporté et les documents ne peuvent pas être récupérés. L’obsolescence des systèmes peut être remédiée par la migration des documents électroniques à un nouveau système.27
Les organismes doivent avoir une politique de conversion et de migration. De plus, cette politique doit être documentée dans votre manuel de GD et inclure les procédures adoptées pour assurer la protection et la préservation de la structure, du contenu, de l’identité et des métadonnées de conservation des documents. Cette protection et cette préservation doivent s’étendre à tous les dossiers électroniques, y compris les courriels, leurs pièces jointes, les liens, les preuves de livraison, les listes de distribution et les liens avec d’autres documents de l’organisme.
Toutefois, avant que toute activité de conversion ou de migration ne commence, la norme stipule que l’organisme doit identifier les éléments suivants:
- les fonctionnalités requises de l’ancien format;
- les fonctionnalités qui doivent être maintenues dans le nouveau format et le nouveau système; et,
- documenter toutes les décisions.
Surtout, la migration et la conversion doivent toutes deux être intégrées dans un processus d’affaires documenté, faisant partie du fonctionnement habituel du système électronique.28
Formats de conservation
La section 6.4.6.5.2 de la norme CAN/CGSB-72.34-2017 suggère aux organismes d’identifier les formats privilégiés pour la conservation des documents par type de documents. C’est-à-dire, quel type de document sera conservé et dans quel format. Les décisions concernant les formats de conservation doivent être fondées sur l’amplitude du changement qui peut être effectué avant que le document ne devienne trop dégradé pour servir de copie fiable au cours d’une procédure judiciaire. De plus, les décisions concernant le format de conservation doivent être documentées dans le manuel de GD. L’annexe C, sur la conservation, fournit des informations précieuses sur les formats de conservation.29
Assurance qualité
Les versions de 2005 et de 2017 exigent toutes deux que les organismes intègrent des mesures et des processus d’assurance qualité dans leurs programmes de GD.
L’assurance qualité signifie que le niveau de service approprié est défini et que le personnel connaît et comprend ce niveau de service. De plus, il faut que le personnel ait reçu la formation nécessaire pour offrir le niveau de service défini.
La mise en œuvre des processus d’assurance qualité est à la charge de l’archiviste et doit inclure l’évaluation du rendement, la surveillance de la conformité, les autoévaluations, les audits externes, le traitement des incidents et la documentation et certification du respect de toutes les obligations de GD. Les problèmes importants doivent être signalés à la haute direction, afin d’effectuer des modifications au programme de GD, si nécessaire.30
Éléments informatiques
Compte tenu de la tendance actuelle à la numérisation, les organismes adoptent des technologies plus rapidement que leur permet leur capacité à incorporer des protocoles appropriés dans leurs systèmes, planification technologique et gestion. Cela conduit à un chaos d’information et à des risques de non-conformité accrus, surtout lorsque les documents s’accumulent et se distribuent dans les différents systèmes, espaces, services, dispositifs et formats, et sous la garde des employés. Forbes et d’autres spécialistes du secteur estiment actuellement que l’information électronique double chaque année.31 Entre temps, sur le volume total de documents (papier et électronique), de nombreux utilisateurs des systèmes de GD estiment qu’approximativement 5-10% nécessiteront une conservation permanente. Ils conviennent, d’après l’expérience de Sharon Byrch, qu’approximativement 60% à 80% de l’information électronique d’un organisme consiste en des documents indésirables documents transitoires avec une valeur à court terme seulement, non durable tels que duplicatas, copies à titre informatif, versions obsolètes et travaux incomplets ou abandonnés; ou des documents qui sont expirés et ne sont plus nécessaires. Ces documents pourraient être légalement détruits, et de façon routinière, s’ils étaient facilement identifiables parmi les documents de l’entreprise qui sont encore nécessaires.
Les professionnels de l’informatique savent que le fouillis d’informations est coûteux. Les besoins en stockage de données et les coûts associés ne cessent d’augmenter à mesure que les entreprises continuent d’étendre leur empreinte numérique. De plus, trier l’information pertinente dans le fouillis est coûteux, en temps et en argent, pour les TI et la GD, et a un impact sur les employés; l’encombrement fait qu’il est difficile pour les employés d’identifier les documents transitoires parmi les documents officiels des entreprises lorsqu’ils recherchent des informations fiables et qui font autorité pour faire leur travail. C’est une situation désavantageuse pour toutes les parties concernées, et un facteur de motivation pour le changement et la mise en œuvre de la norme CAN/CGSB-72.34-2017, afin d’avoir une meilleure gestion des dossiers électroniques, une conformité accrue à la loi et une réduction des risques.
Au même moment où les entreprises se tournent vers le numérique pour gérer leur entreprise, les documents sur papier (analogiques) deviennent de plus en plus des documents d’archives. Par exemple, Sharon Byrch a constaté que, dans un organisme pour laquelle elle travaillait, il y avait un ratio d’environ 1:1000 de documents papier à numériques, ce qui signifie que pour chaque document papier créé, l’organisme a créé 1000 enregistrements électroniques. Ce ratio est une progression naturelle, en raison du déclin de la création de documents papier, et est courant dans plusieurs organismes.
En toute honnêteté, si les organismes ne s’assurent pas que leurs documents sont saisis et rendus facilement accessibles pour usage électronique, ou géré adéquatement en tant que documents (y compris à des fins juridiques, de confidentialité et de sécurité), et conséquemment ne satisfont pas aux critères d’admissibilité pour des procédures judiciairesces organismes gaspillent des ressources inestimables, leur temps et leur argent. Étant donné le taux actuel d’augmentation et de diffusion de l’information que connaissent les organismes de toutes les industries, il est réaliste de penser que les organismes ne puissent plus rattraper leur retard. Pour surmonter cette situation, les organismes doivent repenser leur approche sur la gestion des enregistrements électroniques.
Guide de gestion du système informatique
Un changement important pour les TI est que la norme CAN/CGSB-72.34-2017 a mis à jour toutes les références au « guide de gestion du système », l’étape clé et la responsabilité des TI, à « Guide de gestion du système de TI ». La première instance apparaît dans la section 6.5.1 Guide de gestion du système informatique. La section 6.5.1 présente la directive générale des TI à propos de la norme CAN/CGSB-72.34-2017:
Tous les détails significatifs de l’architecture logique et physique du système informatique conservant les documents seront entièrement documentés dans le guide de gestion du système informatique, y compris les responsabilités et les relations entre la gestion du système informatique, le programme de GD et la conduite des affaires. Le guide de gestion du système informatique doit être structuré de telle sorte que l’intégrité du système puisse être démontrée à tout moment.32
Se conformer à cette directive des TI est essentiel pour faire valoir avec succès l’argument juridique en faveur de la recevabilité des documents à titre de preuve documentaire dans les procédures judiciaires. C’est la raison d’être de cette norme, du point de vue des TI, et est directement liée à la Loi sur la preuve au Canada à l’alinéa 31.2 (1) a) de sorte que:
Par principe, la meilleure preuve à l’égard d’un enregistrement électronique est satisfaite
- sur preuve de l’intégrité du système d’enregistrements électroniques par ou dans lequel l’enregistrement électronique a été enregistré ou stocké.33
La clé de voûte pour les TI est que la documentation de gestion du système informatique est la façon de démontrer l’intégrité du système informatique pour la gestion des enregistrements électroniques et ensuite, les faire répondre aux exigences d’admissibilité comme preuve.
L’aspect critique est que l’intégrité des enregistrements électroniques dépend entièrement de l’intégrité du ou des systèmes qui les gèrent; ceci est mieux décrit et documenté par le personnel informatique, qui est expert en systèmes et principalement responsable de sa gestion technique. C’est de cette façon fondamentale que le service informatique prend en charge les exigences juridiques en matière de gestion des documents pour la gestion des dossiers numériques afin d’assurer leur admissibilité future dans les procédures judiciaires.
Il est important de noter qu’il est obligatoire que le service des TI maintienne son manuel des systèmes informatiques à jour comme preuve de conformité, comme la GD l’exige avec son manuel de GD. Bien que pratiquement parlant, ces documents sont constamment en cours de révision. Il est recommandé aux organismes de s’assurer qu’elles conservent les versions antérieures, comme preuve de leur conformité passée.
Bien que l’exigence d’avoir un guide de gestion du système n’ait pas changé depuis la norme de 2005, la norme CAN/CGSB-72.34-2017 offre une meilleure répartition entre l’informatique et la gestion des documents. Ceci est particulièrement vrai depuis que les sujets du guide de gestion du système informatique sont distincts des rubriques du manuel de procédures GD, qui se trouvent dans la section 6.4 Manuel. Cela les rend moins déroutants pour l’utilisateur. Les professionnels de la TI et de la GD trouveront intéressant d’examiner la répartition des responsabilités entre ces sections.
Piste de vérification
Dans la section 6.5.5 de la norme CAN/ONGC-72,34-2017, alors que les exigences techniques pour les pistes de vérification sont décrites comme une responsabilité des TI, elles sont prioritaires pour la GD et les départements juridiques. Par conséquent, la GD et le juridique sont des parties prenantes clés pour les TI; ils sont soucieux des exigences en matière de preuve qui sont saisies et démontrées par les pistes de vérification. Il est judicieux que les TI incluent ces deux parties prenantes dans le processus de gestion TI.
Voici quelques conseils pour les TI sur leur collaboration avec la GD à propos des pistes d’audit: la GD est particulièrement bien placé pour valider que la piste de vérification d’un système saisit et enregistre les aspects nécessaires à la preuve, puisqu’elle travaille en étroite collaboration avec les entreprises propriétaires des documents, pour établir quels documents exigent la saisie et la gestion comme preuve liée à leurs activités commerciales. En conséquence, les employés des TI devraient être familiers avec les technologies concernées. De plus, la GD détermine le cycle de vie des documents et leurs exigences en matière de gestion par le biais d’un processus d’évaluation détaillé, et saura quel est le(s) but(s), le ou les utilisation(s) et les exigences juridiques des documents, leurs utilisateurs, le(s) format(s) requis, le délai de conservation des documents et comment en disposer une fois qu’ils ne sont plus requis pour les affaires.
La connaissance approfondie du service de GD sur la collecte des documents de l’organisme, de leurs utilisateurs et de leur gestion, y compris les technologies impliquées, en fait un atout considérable pour les TI. Ceci est particulièrement important lorsque le département de TI envisage, teste et met en œuvre des modifications du système, de nouvelles versions, des mises à niveau ou de nouvelles technologies susceptibles d’avoir un impact sur les pistes de vérification de façon inhabituelle, imprévue ou indétectable par eux. En tant que meilleure pratique, les TI devrait impliquer la GD dès le début du processus et leur laisser le temps d’identifier et de tester les risques et problèmes éventuels qui pourraient nécessiter des mesures d’atténuation et de la documentation pour référence future.
Nouvelles technologies
Dans la section 7 de la norme CAN/CGSB-72.34-2017, sont présentées pour la première fois des sections concernant :
- 2 Infonuagique;
- 3 Médias sociaux; et
- 4 Appareils mobiles, y compris, apportez votre équipement personnel de communication (AVEC) et utilisez votre propre nuage (UVPN).
Dans la norme CAN/CGSB-72.34-2017, chacune de ces technologies a aussi sa propre annexe avant la bibliographie. Cependant, et surtout, avant d’aborder ces sujets technologiques, la section 7.1 détermine de façon globale la nécessité de procéder à une évaluation des risques avant d’adopter une nouvelle technologie.
Évaluation des risques
À la section 7.1 de la norme CAN/CGSB-72.34-2017, comme on pouvait s’y attendre, il est recommandé d’adopter une approche multidisciplinaire pour l’évaluation des risques. Pour ce faire, il faut créer une équipe d’intervenants clés représentant les archives, le juridique, la sécurité, la confidentialité, les TI et la gestion des risques. Il est important que les organismes déterminent si leurs fournisseurs de services pourraient ou *devraient* faire partie de ces parties prenantes.
Selon les exigences juridiques, les politiques de confidentialité et de sécurité et le processus de gestion des risques, les organismes peuvent être amenés à impliquer les prestataires de services dans la conduite des évaluations des risques. Cela est particulièrement le cas pour les organismes publics, ou organismes qui fournissent des services à des organismes publics, qui peuvent être tenus, de par la loi sur l’accès à l’information applicable au statut de leur juridiction, de traiter les prestataires de services, et leurs agents et/ou sous-traitants, comme des organismes publics. Dans de tels cas, les organismes publics sont responsables au final des activités de leurs fournisseurs de services. Cela comprend: l’accès à l’information, la divulgation, la gestion du stockage et l’emplacement de sa juridiction, la sécurité, la sauvegarde/ reprise après sinistre et la gestion des violations de la vie privée. Habituellement, dans des cas comme celui-ci, un processus formel d’évaluation des facteurs relatifs à la vie privée (ÉFVP) est prévu par la loi sur l’accès à l’information. De plus, il existe des outils pour documenter l’évaluation des risques. Ce processus peut être capitalisé aux fins de CAN/CGSB-72.34-2017.
L’utilisation d’une approche multidisciplinaire pour effectuer des évaluations des risques est nécessaire pour: 1) examiner pleinement les avantages et les risques de la mise en œuvre de nouvelles technologies et 2) élaborer une analyse de rentabilité solide pour leur mise en œuvre ou leur abandon. Le résultat final de la conduite d’un processus d’évaluation des risques est la création d’un outil d’information précieux et d’un atout servant à plusieurs fins:
- informer le service des communications afin d’aviser les cadres supérieurs/décideurs des risques, des menaces et des avantages;
- orienter l’élaboration de nouvelles politiques et procédures d’atténuation et de gestion des risques, au besoin;
- établir un processus réutilisable et faire l’analyse comparative de la nouvelle technologie pour développement futur et propositions; et
- servir de document de traçabilité, nécessaire afin de démontrer les considérations, les décisions, les activités et activités subséquentes liées au processus d’évaluation des risques et à la mise en œuvre ou à l’abandon de la technologie.
Il est recommandé aux organismes d’élaborer un modèle qu’ils peuvent réutiliser pour d’autres projets d’évaluation des risques. De cette manière, les organismes peuvent développer une approche et une documentation uniformes. De plus, ils peuvent évaluer et mettre à jour leurs modèles au besoin, pour assurer la conformité. Conjointement, les organismes devraient conserver les versions précédentes pour référence chronologique.
Bien que ce ne soit pas directement mentionné dans la norme CAN/ONGC-72,34-2017, les organismes peuvent utiliser deux normes de l’Organisation internationale de normalisation (ISO) pour renforcer davantage leurs systèmes informatiques. La première est la norme ISO/TR 18128: 2014, Information et documentation – Évaluation du risque pour les processus et les systèmes d’enregistrement. L’ISO/TR 18128: 2014 peut être utilisé par les organismes pour évaluer les risques aux dossiers et systèmes, afin qu’ils puissent répondre aux besoins opérationnels identifiés. La deuxième norme est ISO 15489-1: 2016, Information et documentation – Gestion des documents – Partie 1: Concepts et principes. L’ISO 15489-1: 2016 définit les concepts et principes que les organismes peuvent utiliser en ce qui concerne la création, la saisie et la gestion des documents, y compris les enregistrements électroniques.
Voici un dernier conseil sur les fournisseurs de services, peu importe si votre organisme est légiféré pour impliquer les fournisseurs de services dans vos processus d’évaluation des risques. En réalité, si les fournisseurs de services sont impliqués dans la saisie, le stockage, la maintenance ou le partage des documents d’un organisme, ils ont un rôle à jouer dans l’évaluation des risques, et devraient être inclus dans une meilleure pratique. Les organismes devront comprendre, évaluer et documenter leur système d’architecture et leurs protocoles de gestion. Ces protocoles incluent: la gestion de la sécurité, la gestion du stockage des données, la résolution de problèmes et la gestion technique. L’organisme doit ensuite utiliser ces protocoles pour: (1) détecter les risques ou les menaces qui nécessitent des mesures d’atténuation et de communication (2) établir des références pour le développement futur et (3) créer la documentation de traçabilité requise pour le processus d’évaluation des risques.
Un autre aspect important de l’évaluation des risques, bien qu’il ne soit pas explicitement mentionné dans la norme CAN/CGSB-72.34-2017, est qu’il est recommandé que les organismes effectuent leurs évaluations des risques au début du processus d’examen de la nouvelle technologie. De plus, vous devez vous assurer d’impliquer vos principales parties prenantes, surtout les TI, la gestion des documents, la sécurité, la confidentialité et le juridique. Selon votre situation, vous devrez peut-être impliquer des parties prenantes externes. Par exemple, en Colombie-Britannique, au Nouveau-Brunswick et en Nouvelle-Écosse, les organismes publics sont tenus de soumettre leurs évaluations des facteurs relatifs à la vie privée au gouvernement et/ou à leur commissaire respectif à l’information et à la protection de la vie privée.34 L’examen externe peut avoir des impacts importants sur les délais, la portée et l’exécution des projets, de sorte que les organismes devraient intégrer l’évaluation des risques dans les exigences et les échéanciers de chaque projet technologique dès les premières phases. Les phases s’appliquent aux nouvelles technologies ou aux changements à une technologie existante. Ils peuvent inclure: mises à niveau, modules complémentaires et nouveaux modules ou intégration avec d’autres systèmes. N’oubliez pas que les changements apportés à une technologie existante peuvent être tout aussi risqués que la mise en œuvre de nouvelles technologies, selon la portée du changement en cause.
Infonuage
La section 7.2 de la norme CAN/CGSB-72.34-2017 décrit généralement l’infonuage. L’annexe D donne des informations plus détaillées sur l’infonuage. La norme CAN/CGSB-72.34-2017 recommande que l’informatique en infonuage, si elle est utilisée par un organisme, soit documentée dans le guide de gestion du système de TI et le manuel de GD.
Médias sociaux
La section 7.3 de la norme CAN/CGSB-72.34-2017 décrit généralement les médias sociaux, notamment: identification, auteur/propriété, contexte, fiabilité, exactitude et authenticité, et chaîne de responsabilité. Pour résoudre ces problèmes, les organismes sont invités à adopter («doit») une politique sur les médias sociaux qui prévoit la gestion du cycle de vie des affichages. L’affichage est considéré comme un document. L’annexe E donne plus d’informations sur les médias sociaux. À l’instar de l’infonuagique, si un organisme utilise les médias sociaux, cela devrait être documenté dans le guide de gestion du système informatique et le manuel de GD.
Appareils mobiles
La section 7.4 de la norme CAN/CGSB-72.34-2017 décrit généralement les appareils mobiles, comme AVEC et UVPN. L’annexe F traite des appareils POUT (Propriété de l’organisme, utilisation pour le travail) ou POUP (Propriété de l’organisme, utilisation personnelle). Les professionnels de TI trouveront la section 7.4 et l’annexe F particulièrement utiles, puisqu’elles donnent un bon aperçu des questions et implications juridiques, et du besoin de politiques, d’évaluation des risques, de procédures, de sécurité stricte, etc. Les solutions de gestion des appareils mobiles (Mobile Device Management (MDM)) ou de gestion de la mobilité en entreprises (Enterprise Mobility Management (EMM)) sont également abordées.
Annexes
Les 6 annexes de la norme CAN/CGSB-72.34-2017 sont des ajouts. Ils contiennent des instructions “devrait” uniquement. Ces 6 annexes sont:
- Annexe A: Sources pour cette
- Annexe B: Métadonnées.
- Annexe C: Formats de préservation.
- Annexe D:
- Annexe E: Médias
- Annexe F: Appareils
L’évaluation des risques du BYOD à l’annexe F est extrêmement utile et sa lecture est recommandée à toutes les parties prenantes. L’annexe F offre une excellente vue d’ensemble des principaux domaines d’évaluation des risques, pour toutes les parties prenantes: sécurité, redondance, vérifiabilité, propriété des données, chaîne de responsabilité, gestion de l’information, conservation et mise en suspens pour des raisons juridiques, disposition des actifs informationnels, intégrité des données, licenciement des employés et perte de revenus. Penser à la gestion des risques de cette façon sera utile dans d’autres situations auxquelles un organisme est confronté.
Bibliographie
La bibliographie de CAN/CGSB-72.34-2017 énumère 18 sources. Parmi les 18 sources énumérées, 5 sont des normes informatiques. Parmi ceux-ci, 2 sont également trouvés dans la version 2005:
- CAN/CSA-ISO/CEI 11179-3-04, Technologies de l’information – Registres de métadonnées (RMD) – Partie 3: Métamodèle de registre et attributs de base; et
- CAN/CSA-ISO/IEC 14662-01, Technologies de l’information – Modèle de référence EDI- ouvert.
En 2010, la norme CAN/CSA-ISO/IEC 14662-01 a été révisée et remplacée par la norme CAN/CSA-ISO/IEC 14662-10 (R2015). CAN/CSA-ISO/IEC 14662-10 (R2015) est toujours d’actualité.
En 2013, la norme CAN/CSA-ISO/IEC 11179-3-04 a été révisée et remplacée par l’ISO/CEI 11179- 3: 2013. La norme ISO/CEI 11179-3: 2013 est toujours d’actualité.
Les trois nouvelles normes de TI présentées dans CAN/CGSB-72.34-2017 sur la sécurité sont les suivantes:
- ISO/IEC 27001 Technologies de l’information – Techniques de sécurité – Systèmes de gestion de l’information – Exigences;
- ISO/IEC 27002 Technologies de l’information – Techniques de sécurité – Code de bonnes pratiques pour la gestion de la sécurité de l’information; et
- ISO/IEC 27005 Technologies de l’information – Techniques de sécurité – Gestion des risques liés à la sécurité de l’information.
Entre temps, les sources GD sont passées de 3 à 12 en 2017; 5 normes ISO pour la GD ont été introduites, pour un total de 7 normes ISO pour la GD. ARMA International avait 4 rapports techniques et lignes directrices.
La Loi uniforme sur la preuve électronique, qui avait également sa propre annexe dans la version 2005 de l’ONGC, a été abandonnée par la norme CAN/ONGC-72,34-2017. Dans la norme CAN/CGSB-72.34-2017, une nouvelle source, les Principes de Sedona Canada traitant de la découverte numérique (deuxième édition), a été ajoutée. Les changements dans les sources utilisées de 2005 à CAN/ONGC-72,34-2017 démontrent clairement le changement général de vocabulaire et de langage de TI à la GD qui a eu lieu dans les affaires en général.
Les organismes pourraient souhaiter investir dans l’acquisition de ces cinq normes informatiques, ainsi que les 12 normes de source de GD, rapports techniques et directives énoncées dans la bibliographie de la norme CAN/ONGC-72,34-2017, pour les ajouter à l’ensemble de leurs connaissances d’entreprise pour la gestion des enregistrements électroniques. Au moment d’écrire ces lignes, le CEA, la LPRPDE et Sedona Canada sont disponibles gratuitement en ligne; ceux qui sont intéressés par la cybersécurité, la loi sur la vie privée et sur la protection des données, pourraient trouver ces ressources juridiques précieuses.
Conclusion : Obtenez CAN/CGSB-72.34-2017 et implémentez-le !
Tous les organismes devraient envisager d’investir dans la mise en œuvre de la norme CAN/CGSB-72.34-2017, afin de démontrer clairement leur engagement à préserver la fiabilité de leurs documents et à préserver les preuves juridiquement admissibles par la gestion responsable de leur entreprise. Les TI et la GD sont les responsables techniques de la mise en œuvre de la norme CAN/CGSB-72.34-2017. En conséquence, les TI et la GD doivent développer une approche robuste et intégrée. L’amélioration de la gestion des connaissances organisationnelles, de la prise de décision et de la prestation de services d’information sont parmi les principaux avantages, nécessaires au personnel dans leur travail quotidien. Ce sont des atouts importants pour les organismes afin d’atteindre leurs objectifs à long terme: réduction des risques liés à l’information et meilleure conformité.
L’application de la norme CAN/CGSB-72.34-2017 peut apporter un réel avantage pratique aux organismes. La norme CAN/CGSB-72.34-2017 peut aider à:
- augmenter la conformité juridique;
- assurer l’admissibilité juridique des enregistrements électroniques;
- réduire le chaos et l’encombrement de l’information numérique;
- augmenter la saisie et la gestion de «source unique de données» et la rendre disponible électroniquement pour l’utilisation; et
- protéger les informations contre l’accès non autorisé, la divulgation, les modifications, l’utilisation et la suppression/destruction.
Notre dernier point majeur, la mise en œuvre de normes, de systèmes et de procédures appropriées pour la gestion des enregistrements électroniques améliore la gouvernance de l’information. Il aide les organismes à créer un bassin stable d’informations faisant autorité, juridiquement conformes, fiables et sûrs et prêtes à être optimisées et exploitées par des systèmes et des technologies. Le résultat final est une situation gagnante pour tout le monde. Vous pouvez réduire le risque lié à l’information et améliorer la conformité, tandis que le personnel et la direction peuvent obtenir de meilleurs résultats avec moins d’effort pour le travail de gestion d’information qu’ils sont tenus de faire. Ceci, amis juridiques, GD et IT, est le ticket gagnant, et ce que nous aspirons à faire.
1“Standards Council of Canada,” What is a National Standard of Canada (NSC)?, https://www.scc.ca/en/faq-what- is-a-national-standard-of-canada, accessed on August 24, 2017.
2Section 6.1 General, page 14.
3Section 0.1 About this standard, page iv.
4Voir https://www.tpsgc-pwgsc.gc.ca/ongc-cgsb/programme-program/normes-standards/notification/sect1b- eng.html.
5Section 5.2 Requirements for admissibility of electronic records as documentary evidence, page 9.
6Voir https://thesedonaconference.org/publication/The%20Sedona%20Canada%20Principles.
7Voir http://canlii.ca/t/g7n43.
8The leading test for Canadian courts to qualify experts is White Burgess Langille Inman v. Abbott and Haliburton Co., 2015 SCC 23 (CanLII), http://canlii.ca/t/ghd4f
9Section 6.1 Général, page 14.
10Ibid.
11Ibid.
12Ibid.
13Section 6.3.2 Content of the policy, pages 15-16.
14Ibid.
15Section 6.4.1 General, page 16.
17Ibid.16 Ibid.
18Ibid.
19Section 0.1 About this standard, page iv.
20Section 6.4.2.2 Numérisation, page 17.
22Section 6.4.5 Records retention requirements, page 18.
23Ibid.
25Section 6.4.6.4 Transfer of electronic records to another entity, page 19.
26Section 6.4.6.5 Records preservation, page 19.
28Ibid.
29Ibid.
30Section 6.4.7 Quality assurance, page 20.
31http://www.forbes.com/sites/gilpress/2013/05/28/a-very-short-history-of-data-science/#7f0fa8cb69fd
32Page 20.
33R.S.C. 1985, c. C-5, http://canlii.ca/t/52zlc
34See sections 69 and 69.1 of the Freedom Of Information And Protection Of Privacy Act, R.S.B.C. 1996, c. 165 (http://canlii.ca/t/52sth), section 77 of the Right to Information and Protection of Privacy Act, S.N.B. 2009, c. R-(http://canlii.ca/t/52wbq) and section 72 of the Access to Information and Protection of Privacy Act, 2015, S.N.L. 2015, c. A-1.2 (http://canlii.ca/t/52wbq).
CAN/CGSB 72.34-2017 ELECTRONIC RECORDS AS DOCUMENTARY EVIDENCE
By Sharon Byrch, Uta Fox, CRM, FAI and Stuart Rennie JD, MLIS, BA (Hons.)
Introduction
In March 2017, the Canadian General Standards Board (CGSB) released the new Electronic Records as Documentary Evidence standard, CAN/CGSB-72.34-2017. The new CAN/CGSB-72.34- 2017 supersedes and replaces the 2005 version, CGSB 72.34-2005. Two authors of this article, Uta Fox and Stuart Rennie were members of CGSB committee that developed CAN/CGSB-72.34- 2017. Having co-presented on both versions of CAN/CGSB-72.34 at ARMA Canada’s national conferences and ARMA Canada chapters around the country, they are continually being contacted to provide more information on this standard. This article responds to those requests from the RM community to learn about the 2017 update and how to apply it.
Widening the scope of the article, they approached Sharon Byrch, RM professional, who agreed to collaborate in writing this article. This article discusses the major changes made to the CAN/CGSB-72.34-2017 standard compared to the 2005 version from the perspectives of the RIM, IT and legal. While the primary focus is on significant changes to content, there are recommendations for implementing the standard into your RM and information governance (IG) programs.
In this article, the views of the authors are their own personal views and are not affiliated with any other organization. As well, the information provided in this article is for information purposes only and not for the purposes of providing legal, technical or other professional advice.
The purpose of the CAN/CGSB-72.34-2017 standard is to set out principles and procedures for organizations to use for managing their electronic records to enhance their admissibility as evidence in legal proceedings. The CAN/CGSB-72.34-2017 is a voluntary standard, available for purchase in paper and electronic formats and in both English and French. The CAN/CGSB-72.34- 2017 is not a substitute for expert legal and technical advice.
The CGSB is a Canadian federal government organization that assists with the development of standards in many industries. Currently, there are over 300 CGSB standards. CGSB standards are developed by a committee of volunteers. These volunteers are experts in their fields. The CGSB is accredited by the Standards Council of Canada (SCC) as a Standards Development Organization. The SCC is a federal Crown corporation. It has its mandate to promote efficient and effective standardization in Canada. Additionally, the CAN/CGSB-72.34-2017 is a National Standard of Canada, as evidenced by the inclusion of “CAN” as part of the standard’s reference number indicating it is recognized as the official Canadian standard in a particular subject.1
When reading the standard, users should be cognizant of CGSB’s language used for organizations to achieve compliance. Take the word “shall”, often used in CAN/CGSB-72.34- 2017. “Shall” denotes mandatory requirements. For example, “An organization shall establish the RM program”2. This is a must statement. That is, organizations using this standard must have an authorized RM program in place. The word “should” refers to recommendations while “may” articulates an option or what is permissible within the limits of this standard.
In addition to demonstrating the integrity, authenticity and reliability of electronic records to meet evidential requirements, organizations need to ensure the electronic records they create, receive and maintain in electronic recordkeeping systems are in compliance with the CAN/CGSB-72.34-2017 to ensure their admissibility in court proceedings. As noted:
This standard provides a framework and guidelines for the implementation and operation of records systems for electronic records, whether or not any information held therein will ever be required as evidence. Thus compliance with it should be regarded as a demonstration of responsible business management. Applying the standard to an organization’s business will not eliminate the possibility of litigation, but the probability is that it will make the production of electronic records easier and their acceptance in a legal procedure more certain.3
One change that occurred with the CAN/CGSB-72.34-2017 update is that the CGSB has withdrawn a companion standard: CAN/CGSB-72.11-93 Microfilm and Electronic Images as Documentary Evidence. This withdrawal is effective January 24, 2017.4 The logic underlying the withdrawal of CAN/CGSB-72.11-93 is due to its limited use and support for its revision. As well, section 3 of Part III and section 3 of Part IV about electronic images in CAN/CGSB 72.11-93 are incorporated into CAN/CGSB-72.34-2017. Organizations can still use and reference CAN/CGSB- 72.11-93, but it not recommended since CAN/CGSB-72.11-93 no longer carries the weight or is supported by the CGSB. As a result, organizations should use the most current version of the standard, the CAN/CGSB-72.34-2017.
Legal Requirements For Electronic Records As Documentary Evidence
Section 5 of the CAN/CGSB-72.34-2017 sets out the legal requirements for electronic records as documentary evidence.
Like the 2005 version, the new 2017 standard focuses on these legal requirements for legal admissibility:
[U]se of an electronic record as evidence requires proof of the authenticity of the record, which can be inferred from the integrity of the electronic records system in which the record is made or received or stored, and proof that the record was “made in the usual and ordinary course of business” or is otherwise exempt from the legal rule barring hearsay.5
The result is that the 2017 and 2005 versions are substantially similar so organizations using the 2005 standard can amend their policies, procedures and workflow to comply with the new CAN/CGSB-72.34-2017 without having to start over. This is helpful.
The CAN/CGSB-72.34-2017 refers consistently to the Canada Evidence Act (CEA) and does not mention provincial or territorial statutes. Organizations that do not come under Canadian federal jurisdiction will need to review the applicable provincial or territorial law that applies to them for their electronic records.
In addition, organizations can make use of other available legal sources to understand how courts and tribunals across Canada are interpreting these legal requirements. A useful legal information source is the website of the Canadian Legal Information Institute: https://www.canlii.org/. CANLII, a non-governmental, non-profit organization, which provides free Internet access to: court judgments, tribunal decisions, statutes and regulations from all jurisdictions across Canada. CANLII employs an easy to use search interface. Its legal information is available in both English and French. CANLII is one of the best sources for lawyers and the general public to consult Canadian law.
Section 5 of the CAN/CGSB-72.34-2017 rightly emphasizes that organizations must prove that their electronic records are legally admissible. Two key evidentiary tools for organizations to use is the: (1) RM manual and (2) IT system management guide. These tools should contain the organization’s authorized policies and procedures to provide documentary evidence that the organization has meet the legal requirements for legal admissibility of its electronic records.
CAN/CGSB-72.34-2017 has new, welcome additions to reflect changes in technology from 2005:
- Electronic discovery (e-discovery);
- Technology Assisted Review (TAR) using specific search software;
- Legal hold; and
- Electronic and wet ink
Electronic Discovery (E-Discovery) And Litigation Preparedness
In section 5.3, for the first time, CAN/CGSB-72.34-2017 refers to e-discovery in civil litigation. E- discovery is a pre-trial procedure where parties to the litigation are required to exchange relevant electronic records as supervised by the courts. As organizations are now creating and managing electronic records in greater numbers, the challenge for them is being able to search, access and then produce relevant electronic records required by Canadian courts so that these electronic records can be admissible as evidence in the legal proceedings.
In 2008, to assist organizations in producing admissible electronic records in Canada, The Sedona Canada Principles Addressing Electronic Discovery (Sedona Canada Principles) were developed. Sedona Canada is a non-governmental volunteer organization of lawyers, judges and technologists across Canada. The Sedona Canada Principles are largely a voluntary standard like the CGSB, except for Ontario. Since 2010, the Sedona Canada Principles are mandatory for use in Ontario courts under the Ontario Rules of Civil Procedure. Outside of Ontario, the Sedona Canada Principles are acceptable for use in courts and tribunals across the country to assist parties to produce and access relevant electronic records in a timely and efficient, cost- effective manner. Currently, there is a developing Canadian e-discovery case law around the Sedona Canada Principles.
In 2015, like the changes CGSB made in 2017 to CAN/CGSB-72.34-2005, Sedona Canada, to account for changes in technology and the law, issued an updated Second Edition of the Sedona Canada Principles.6
As well, for the first time, for disclosure in criminal law proceedings, the CAN/CGSB-72.34-2017 refers to R. v. Oler, 2014 ABPC 130 (CanLII).7 The Oler case is a leading case for several reasons. First, Oler is the first case to consider and apply the 2005 CAN/CGSB-72.34 standard. Second, Oler is the first case in Canada to provide that an organization’s scanning process is admissible as electronic evidence because its scanning process complies with both the Canada Evidence Act and the Alberta Evidence Act for its use of industry standards. Third, Oler is the first court in Canada to accept records management expert evidence. The expert in Oler was Uta Fox, co- author of this article. Uta Fox is the first records manager known in Canada to be accepted as a court qualified expert witness. In that role, she assisted the court in determining the legal admissibility of electronic records.
There is little case law in Canada on the relationship between RM and the law. More case law is needed to advance both the RIM profession and the admissibility of records, especially electronic records in Canadian courts. This situation becomes more critical as organizations become increasingly ‘digital’ and only create and manage electronic records, not paper records. Given the preference for Canadian courts to cite with approved National Standards of Canada like CAN/CGSB-72.34-20, the Oler case is a step in the right direction for RIM.
As well, there is an increasing need for RM professionals to be accepted in court as experts, like Uta Fox was, to assist the court in determining the admissibility of electronic evidence.
Canadian courts do not qualify persons as experts lightly. Courts need proof that the person has proper qualifications, education, specialized knowledge and expertise to be an expert.
Furthermore, the person must be independent and impartial to assist the court as an expert.8 Organizations, like the Calgary Police Service in Oler, that use electronic document and records management systems (EDRMS) are operating and managing complex RM and IT systems, with legal implications beyond the experience of the public or the casual user. As more organizations move to EDRMS, there needs to be more RIM experts admitted by courts to advise on how these complex systems work to proof admissibility of electronic records in both civil and criminal cases. Oler is the first case law in Canada that permits the admissibility of scanned electronic records in place of paper originals using an EDRMS. We need to develop the RM case law to match pace with the use of EDRMS in business.
From a legal perspective, these are welcomed additions to the standard. Organizations can refer to the Sedona Principles and the Oler case in addition to CGSB 72.34-2017 as sources for credible best practice to further enhance the organization’s legal compliance and reduce the organization’s legal risks.
Technology Assisted Review (TAR) And Other Automated Tools And Techniques
The 2005 standard is silent on Technology Assisted Review (TAR). It is first introduced in section 5.3.1, for CAN/CGSB-72.34-2017. TAR uses technology to automate the process of identifying relevant electronic records. Like e-discovery, CAN/CGSB-72.34-2017 rightly refers to the Sedona Canada Principles. Organizations are increasingly using TAR and it is being referred to in Canadian case law, so this is another welcome addition.
Legal Hold
Section 5.4, CAN/CGSB-72.34-2017 refers to a “legal hold” which was absent from the 2005 standard. Increasingly applied to all records, a legal hold is a process where an organization preserves all forms of potentially relevant records when litigation is reasonably anticipated or underway. The risk to an organization for not preserving electronic evidence with a legal hold is that relevant evidence is inadvertently destroyed and thus unavailable to the courts to determine liability or not. When an organization inadvertently destroys important evidence, this increases the organization’s risk to legal sanctions by the courts who are unhappy with the destruction of evidence as a tool to subvert the rule of law.
CAN/CGSB-72.34-2017 refers to the Sedona Canada Principles on legal holds. Taken together, CAN/CGSB-72.34-2017 and the Sedona Canada Principles provide organizations with a good understanding of what a legal hold is, how to apply it and how to avoid the risk of inadvertently destroying or spoliating relevant electronic evidence. Both standards highlight the need for expert legal advice as soon as possible when a legal hold is needed.
Signatures
For signatures, the 2005 standard does not have a specific section for electronic and person signatures. The 2005 standard makes only passing reference to them.
The CAN/CGSB-72.34-2017 dedicates section 5.5 to electronic and wet signatures. A wet signature is usually ink, a paper seal or even the traditional wax. The distinction between electronic and wet signatures is useful. Many organizations today use both wet and electronic signatures; there is often confusion and uncertainty in organizations about the legal admissibility of these two signatures. CAN/CGSB-72.34-2017 provides the basic requirements for use of these signatures and when to seek expert advice to ensure legal admissibility.
Authenticated Paper Copies For Legal Proceedings (“True Copies”)
For “True copies”, the 2005 standard in section 5.6 required paper copies to be authenticated as a “true copy” of the original with a signature to enhance its admissibility and weight in court. That authentication needed to be documented with procedures.
In the 2017 version, section 5.6 is substantially similarly in wording to the 2005 standard.
The main difference is that the 2005 standard does not mention “electronic records”, it is implied; CAN/CGSB-72.34-2017 uses the phrase “electronic records” to make it clear that paper copies of electronic records need to be authenticated by signature as “true copies” of the electronic records.
CAN/CGSB-72.34-2017 also adds that an affidavit can be used as the authentication record; the 2005 standard does not mention the affidavit. The new reference to using an affidavit is helpful since the affidavit is a common tool of evidence in the litigation process.
Records Management (RM) program
Both versions of CAN/CGSB-72.34 have provisions on establishing a RM program. The 2005 version, titled “Establishing a Records management system (RMS) program” changed in 2017 to the “Records Management (RM) program.”
Before discussing RM changes in CAN/CGSB-72.34-2017, let’s review what’s carried forward from 2005 since it is vital to your RM program. Sections 6.1 to 6.4.1 of the CAN/CGSB-72.34- 2017 address the fundamental components an organization must have in terms of the: records management concepts, principles, methods and practices adopted by the organization shall demonstrate that an appropriate RM program is in place and is an integral part of the organization’s usual and ordinary course of business.9
Your organization must have an authorized:
- RM program;
- RM policy;
- RM manual; and
- records officer (RO)10
In section 6.1, the RM program itself “shall support a records system consisting of appropriate records procedures and controls that complement business operating procedures.”11 An organization shall:
- establish the RM program;
- develop a RM policy, with definitions and assignment of responsibilities;
- design RM procedures and related documentation;
- select and implement technologies supporting the records system;
- establish records protection measures, including audit trails and backup; and
- establish a records quality assurance12
Notice, these statements are “shall” statements; meaning, the organization must support records systems using suitable records procedures and controls that harmonize business operations.
Organizations must establish a RM program, have a policy, use definitions, assign responsibilities, develop procedures, select technologies, implement records protection processes and adopt a quality assurance program. These are non-negotiable factors that must be in place before an organization can even begin to comply with this standard.
Responsibility – Records Officer (RO)
Both the 2005 and the 2017 versions require organizations to establish a RO to be responsible for implementing the RM program, ensuring it is part of the organization’s usual and ordinary course of business. Additionally, the RO must assure that the organization implements the RM policy, program and RM manual. The RO’s role and responsibilities must be defined in policy, bylaw or directive as this role is central to establishing and maintaining the RM program and providing oversight to ensure organizational compliance with standards, policy and legislation impacting the RM program.
CAN/CGSB-72.34-2017 provides more direction to the RO by acknowledging that the organization’s policy must make the RO responsible for maintaining and amending the RM manual, for the RM program and the records system functions; these responsibilities must be fully supported by IT personnel. Not only must the RO’s responsibilities be documented in the RM program but also, all personnel with RM duties must also be defined for compliance monitoring.13 That directive extends to all employees of an organization that have any RM duties, not just the staff of the RM department. For compliance with CGSB 72.34-2017, make sure your organization addresses the RM requirements and duties of all its employees.
RM Policy
Both CGSB versions emphasize that senior management must authorize a RM policy that stipulates the management of electronic records is an integral component of the organization’s usual and ordinary course of business. Further, the policy needs to identify and address:
- applicable records, records systems and exclusions (scope);
- relevant RM and IT standards used in RM programs;
- the RO’s responsibility for the records system;
- compliance of the record system with RM manual, the law, national, international and industry standards;
- that the RO is responsible for maintaining and updating the RM manual;
- requirements for records creation, management, use and disposition;
- that IT works with RO to integrate RM into organization’s usual and ordinary course of business; and
- the processes of quality assurance processes is assigned to the14
RM Manual
The RM manual is the instrument that consolidates all records related procedures to ensure completeness and consistency of practice15 which both versions of CAN/CGSB-72.34 address. The required components of a RM manual, for example, procedures for making, receiving, capturing and disposing records are also consistent between the versions. CAN/CGSB-72.34- 2017 emphasizes that the RM manual:
shall be kept up-to-date and accurately reflect the exact nature, functions, procedures and processes of the organization’s records system, i.e., the way in which this system participates in and supports the usual and ordinary course of business;16
CAN/CGSB-72.34-2017 notes that the manual must specify the operation and use of records systems and include reference to other applicable documentation, for example, the IT System Management Guide, business procedures or IT system documentation.17 This is another example of the standard compelling IT and RM to collaborate in complying with requirements.
While RM communicates its requirements differently from IT, clearly these two fields have shared interests and the same end goal: better information governance over electronic records management. It’s completely strategic for RM and IT to support each other because helping one field advances the goals and objectives of the other and ultimately, both. IT and RM are essentially different expressions of the same objective. Your stakeholders overlap, you share the same risks and consequences, resources and priorities.
The future of electronic records management depends on its successful implementation and integration within organizations. The inner workings between IT and RM can make or break this work and it’s up to you both to build capacity to onboard this strategic management methodology. The sooner you figure out how to work together and develop resources, communications and support to advance your work, the better off you are.
Keeping the manual current using a formal review process at pre-determined times ensures the RM manual continues to reflect the business of RM for electronic records in real time.18
Your RM policy, program, manual and RO combined formulate the foundation and fundamental aspects of your RM operations. Organizations cannot be compliant with CAN/CGSB-72.34-2017 if they do not have a RM policy, program, manual or a RO in place if called upon to produce their electronic records for court purposes. As CAN/CGSB-72.34-2017 states compliance with this standard “should be regarded as a demonstration of responsible business management.”19
Digitization
CAN/CGSB-72.34-2017 incorporates the fundamental elements of the Microfilm and electronic images as documentary evidence (CAN/CGSB-72.34-11-93). If you are implementing an imaging program into your RM program, you can use the following checklist itemizing CAN/CGSB-72.34- 2017’s requirements20, described in Table I below. If your organization has an existing imaging program, use the checklist to audit your program using CAN/CGSB-72.34-2017’s digitization requirements to your imaging program.
This checklist provides the “shall” requirements directly captured from standard, see the “CAN/CGSB-72.34-2017 Requirement” column below. It also identifies the requirements that must be addressed and actioned, using the “Action Required” column. Lastly, the “Responsibility” column is populated with those positions responsible for completing the actions. This checklist is a recommendation only but we encourage you to develop a tracking system of some type to document the status of your implementation and its progress.
Table I
Digitization Checklist – 6.4.4.4 Digitization
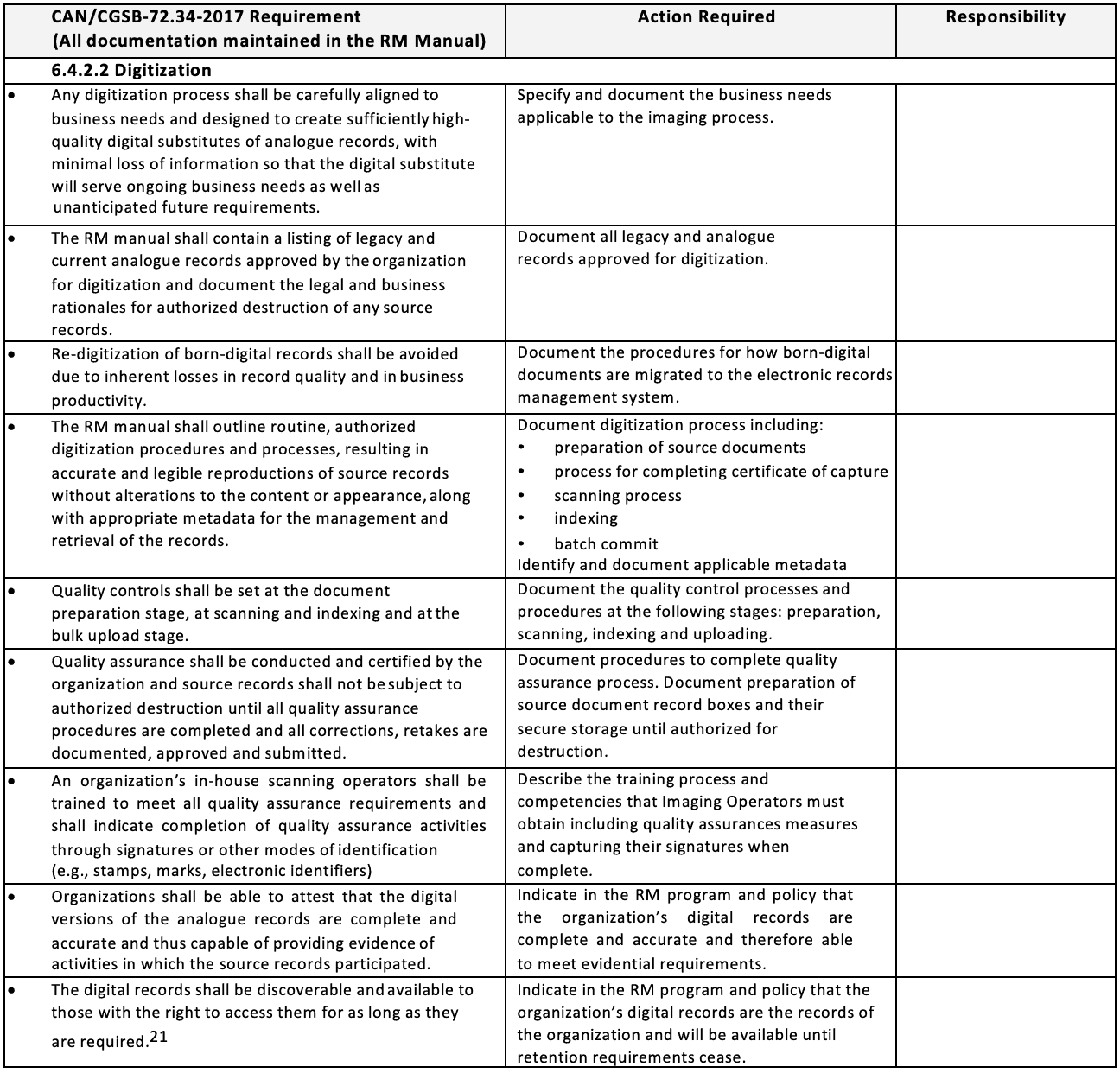



Records Retention Requirements
A number of modifications were made to the records retention section by CAN/CGSB-72.34- 2017. The 2005 version addressed consumer, goods and services requirements in assigning retention periods while the 2017 version adopts a general business approach. CAN/CGSB-72.34- 2017 stipulates that to assign proper retention periods, authorized individuals responsible for the organizational functions that the records support (e.g., legal representation, finance, HR) must be included in records appraisal and retention decisions. Ideally, organizations should establish a RM committee, composed of subject matter experts from legal, finance, HR and the like to be responsible for these decisions. Decisions made by the authorizing committee assigning retention periods for record series must be documented as part of the Records Retention Schedule and linked to the classification system.
The standard provides several critical appraisal factors that can ultimately define retention requirements including:
- How the organization uses the records, internally and externally;
- Users’ need for access if a disaster occurs;
- Financial, legal, social, political, historical value of the records;
- Costs/benefits analysis of retention;
- Impact on the organization if records are destroyed; and
- Evidentiary value of records if required for litigation, audit or22
Other changes in the 2017 standard focus on the organization’s records system and its ability to accommodate fixed-date, event date and permanent retention. The RO must review all records dispositions before any dispositioning takes place to ensure that records scheduled for disposal are not subject to a legal hold, organizational or government review.23 If they are, the records must be suspended from destruction as outlined in section 5.4 Legal hold of the CAN/CGSB- 72.34-2017.
Records Disposition
There are some significant changes to the disposition section in CAN/CGSB-72.34-2017. The 2005 version recognized disposition that included records destruction and transfer to another entity but there was no discussion on transferring records to another body or on records preservation.
CAN/CGSB-72.34-2017 rectifies that by providing substantial details on the disposition process, the destruction of electronic records, transferring records to another entity and preservation practices for those records that are permanently retained or have long-term retention requirements.
Destruction of Electronic Records
As mentioned, both versions of the standard acknowledge that records must first meet retention requirements and be authorized for disposition/destruction prior to commencing any dispositioning actions. CAN/CGSB-72.34-2017 specifies that the RM manual must allow the records system to destroy, amend or correct records using an editable process. For those records that have been destroyed, the system procedures must ensure both the record and its locator are destroyed. It also stipulates that the records destruction process must be completed in such a manner that the confidentiality and protection of personal information is not compromised.24
Transfer of Electronic Records to Another Entity
In section 6.4.6.4 of the CAN/CGSB-72.34-2017, an organization’s RM manual must document all records transferred to and accepted by the archives (or another entity) and both the organization transferring the records and the organization receiving the records must maintain this documentation. The receiving organization may require additional information such as: the identity of the hardware and software that generated the records, the program documentation describing the format, file codes, file layout and other technical details about the records system in which the records resided.25
Records Preservation
Section 6.4.6.5 of the CAN/CGSB-72.34-2017 recognizes that organizations must ensure their RM manuals stress that records preservation begins with records created and maintained in preserve-able file formats capturing required identity and recordkeeping metadata. Throughout the records lifecycle organizations must demonstrate that electronic records were created, received and stored in their usual and ordinary course of business and continue to meet admissibility requirements by ensuring their authenticity.
Organizations required to maintain records permanently must make certain that their recordkeeping systems are capable of permanently maintaining recordsdefinitely a consideration when selecting records systems as is the safeguarding of records against software obsolescence.26
Records Conversion And Migration
Section 6.4.6.5.1 of the CAN/CGSB-72.34-2017 defines records conversion as changing recorded information from one format to another, while migration is moving recorded information from one IT system to another (both are methods of avoiding software obsolescence and both involve risks). The standard notes that there are two types of digital record obsolescence:
- file format obsolescence – when the software cannot open or view the records contents. File format obsolescence is addressed by file conversion or moving a record from one file format to another;
- systems obsolescence – when a system or application is no longer supported and records cannot be retrieved. System obsolescence is addressed by migrating digital files to a new27
Organizations must have a conversion and migration policy. Additionally, this policy must be documented in your RM manual and include the procedures developed that ensure the records’ structure, content, identity and recordkeeping metadata are protected and preserved. This protection and preservation must extend to all electronic records, including emails, their attachments, links, proof of delivery, distribution lists and relationship to other records of the organization.
However, before any conversion or migration activity commences the standard stipulates that the organization must identify the following:
- the required functionalities of the old format;
- the functionalities that have to be maintained in the new format and system; and,
- document all
Most importantly, both migration and conversion must be integrated in a documented business process that is part of the regular operation of the records system.28<s/up>
Preservation Formats
Section 6.4.6.5.2 of the CAN/CGSB-72.34-2017 directs organizations to identify the preferred formats for records preservation by type of record. That is, what type of record will be preserved and in what format. Preservation format decisions must be based on the amount of change that can be introduced before the record becomes too degraded to serve as a reliable copy of the record in a legal proceeding. Further, preservation format decisions should be documented in the RM manual. Annex C, on preservation, provides valuable information on preservation formats.29
Quality Assurance
Both the 2005 and 2017 versions require organizations to incorporate quality assurance measures and processes into their RM programs.
Quality assurance means the appropriate level of service is defined and that staff are aware and understand that level of service. As well, it requires that staff have received the necessary training to provide the defined level of service.
Implementing the quality assurance processes is the responsibility of the RO and must include performance, compliance monitoring, self-assessments, external audits, incident handling, documenting and certifying that all RM duties are fulfilled. Significant issues must be reported to senior management for RM program modifications, if required.30
IT Elements
Given the current push in many organizations to become digital, organizations are adopting technologies more quickly than their capacity to incorporate appropriate protocols into systems, technologies planning and management. This leads to growing information chaos and increased compliance risks. Particularly, as records accumulate and spread across systems, spaces, services, devices, formats and in the custody of workers. Forbes and other industry research experts, currently estimate that electronic information doubles annually.31 Meanwhile, of the total volume of records (hardcopy and electronic), many RM practitioners believe that roughly 5-10% will require permanent retention. RM practitioners in Sharon Byrch’s experience consistently agree that anywhere between 60%-80% of an organization’s electronic information is unwanted cluttertransitory records with short-term or no enduring value—including duplicates, convenience copies, outdated versions and incomplete or abandoned work; or records which have expired and are no longer necessary. These records could be routinely and legally destroyed if they were easily identifiable from the records which are still required for business.
IT professionals know information clutter is costly. Data storage requirements and associated costs keep rising as organizations continue expanding their digital footprint. Moreover, sorting through information clutter is time-consuming and costly for IT and RM and impacts workers; clutter makes it difficult for workers to identify transitory records from official business records when looking for authoritative, trustworthy information to do their jobs. It’s a lose-lose situation and a motivating factor for change and implementing CAN/CGSB-72.34-2017 for better electronic records management, increased legal compliance and reduced risk.
At the same time as organizations are going ‘digital’ to run their businesses, paper hardcopy (analogue) records are becoming legacy documentation. For example, Sharon Byrch has experienced in one organization she worked for, that the organization had a ratio of roughly 1:1000 hardcopy to electronic records, meaning that for everyone 1 hardcopy record created, the organization created 1000 electronic records. This ratio is a natural progression by virtue of the decline in the creation of hardcopy records and is common in many organizations.
Quite honestly, if organizations are not ensuring that their records are captured and made easily available for use electronically, or managed appropriately as records (including for legal, privacy and security purposes) and consequently, do not meet admissibility requirements for legal proceedingsthose organizations are wasting their precious resources, time and money.
Given the current rate of information growth and spread experienced by organizations in all industries, realistically organizations can’t expect to catch up either. To overcome this situation, organizations need to re-think their approach to electronic records management.
IT System Management Guide
An important change for IT is that the CAN/CGSB-72.34-2017 updated all references from “system management guide”, the key deliverable and responsibility of IT, to “IT system management guide”. The first instance appears in section 6.5.1 IT system management guide. Section 6.5.1 outlines IT’s overall directive for CAN/CGSB-72.34-2017:
All significant details of the logical and physical architecture of the IT system keeping the records shall be fully documented in the IT system management guide, including the responsibilities and the relationships between IT system management, the RM program, and the conduct of the organization’s business. The IT system management guide shall be structured so that the integrity of the system can be demonstrated for any point in time.32
Meeting this IT directive is essential to successfully make the legal case for records admissibility as documentary evidence in court proceedings. It is the point of this standard from an IT perspective and is directly linked to the Canada Evidence Act in section 31.2(1)(a) so that:
The best evidence rule in respect of an electronic document is satisfied on proof of the integrity of the electronic documents system by or in which the electronic document was recorded or stored.33
The key takeaway here for IT is that IT system management documentation is how to demonstrate IT system integrity for managing electronic records and then having them meet admissibility requirements as evidence. The critical aspect is that the integrity of electronic records is completely dependent on the integrity of the system(s) managing them; this is best described and documented by IT staff who are systems experts and primarily responsible for their technical management. This is the core way IT supports the legal RM requirements for managing electronic records to ensure their future admissibility in court proceedings.
It is important to note that it is mandated that IT will keep its IT systems manual current as evidence of compliance, same as RM is mandated to with its RM manual. Though practically speaking, these documents are under continuous revision. It is a best practice for organizations to make sure they retain previous versions as evidence of their compliance.
While the requirement to have a system management guide has not changed since the 2005 standard, CAN/CGSB-72.34-2017 provides better clarity between IT and RM. This is particularly true now that the IT system management guide topics are better separated from the RM procedure manual topics found under section 6.4 Manual. This makes it less confusing to the user. IT and RM professionals will find it interesting to look at the division of responsibilities between these sections.
Audit Trail
In section 6.5.5 of CAN/CGSB-72.34-2017, while the technical requirements for audit trails are laid out as an IT responsibility, audit trails are a key priority for RM and legal departments.
Consequently, RM and legal are key stakeholders for IT; they are concerned with the evidentiary requirements being captured and proven by audit trails. It is wise for IT to include these two stakeholders in IT’s management process.
Here is some advice for IT about working with RM on audit trails: RM is particularly well-suited to audit how well a system’s audit trail is capturing and recording the required aspects for evidence. Since RM works closely with the business owners of the records to establish what records require capture and management as evidence of their associated business activities. As a result, IT should be familiar with the technologies involved. Moreover, RM determines the lifecycle of records and their management requirements through a process of detailed appraisal, and will know what the purpose(s), use(s) and legal requirements of the records are, their users, required format(s), how long to keep records and what to do with them once they are no longer required for business.
RM’s intimate knowledge of the organization’s records collections, their users and their management, including technologies involved, makes them a huge asset to IT. This is particularly important when IT is contemplating, testing and implementing system feature changes, new releases, upgrades or new technologies which could impact audit trails in ways unfamiliar, unanticipated or undetectable by IT. As a best practice, IT should involve RM early in the process and give RIM time to evaluate and test for possible risks and issues that may need mitigation and documenting for future reference.
New Technologies
In section 7 of CAN/CGSB-72.34-2017, for the first time are sections regarding
- 2 Cloud computing;
- 3 Social media; and
- 4 Mobile devices, including, bring your own device (BYOD) and bring your own cloud (BYOC).
In CAN/CGSB-72.34-2017, each of these technologies also has its own annex before the bibliography. However, more importantly, before discussing these technology topics, section
- broadly identifies the need to conduct a risk assessment prior to adopting new
Risk Assessment
In section 7.1 of CAN/CGSB-72.34-2017, as one might expect, it is recommended that a multi- disciplinary approach be taken for conducting risk assessments. This is done by developing a team of key stakeholders representing records, legal, security, privacy, IT and risk management. It is important for organizations to determine, if their service providers could or *should* be among these stakeholders.
Depending on your organization’s legal requirements, privacy and security policies and risk management process, organizations may be required to involve service providers in conducting risk assessments. This is particularly so for public bodies or organizations which provide services to public bodies, who may be required under the applicable freedom of information statute for their jurisdiction, to treat service providers and their agents and/or subcontractors as if they are public bodies. In cases like this, public bodies are ultimately accountable for the activities of their service providers. This includes: information access, disclosure, storage management and jurisdictional location, security, backups/disaster recovery and privacy breach management.
Typically, in cases like this, a formal Privacy Impact Assessment (PIA) process is legislated under freedom of information legislation. As well, there are tools are in place for documenting the risk assessment. This process can be capitalized on for CAN/CGSB-72.34-2017’s purposes.
Using a multi-disciplinary approach for conducting risk assessments is necessary to: 1) fully examine the benefits versus risks of implementing new technologies and 2) develop a solid business case for their implementation or abandonment. The end-result of conducting a risk assessment process is the creation of a valuable information asset and tool that serves multi- purposes:
- informs communications to advise senior management/decision-makers of risks, threats and benefits;
- informs the development of new policies and procedures for risk mitigation and management where required;
- establishes a re-usable process and benchmarks the new technology for future development and proposals; and
- serves as necessary chain of custody documentation to evidence the considerations, decisions, activities and subsequent activities related to the risk assessment process and the technology’s implementation or
It is a recommended best practice for organizations to develop a template that they can re- purpose for other risk assessment projects. In this way, organizations can develop a consistent approach and documentation. As well, they can evaluate and update their templates as needed to ensure compliance. At the same time, organizations should but retain previous versions for historical reference.
While not directly mentioned in CAN/CGSB-72.34-2017, organizations can use two International Organization for Standardization (ISO) standards to further strengthen their IT systems. The first ISO standard is ISO/TR 18128:2014, Information and documentation — Risk assessment for records processes and systems. ISO/TR 18128:2014 can be used by organizations to assess risks to records processes and systems in order for organizations to ensure they can meet identified business needs. The second ISO standard is the ISO 15489-1:2016, Information and documentation — Records management — Part 1: Concepts and principles. ISO 15489-1:2016 defines the concepts and principles that organizations can use regarding the creation, capture and management of records are developed, including electronic records.
Here is some final advice about service providers, regardless whether or not your organization is legislated to involve service providers in your risk assessment processes. The practical truth is, if service providers are involved in capturing, storing, maintaining or sharing an organization’s records, they have a role in the risk assessment and should be included as a best practice. Organizations will need to understand, evaluate and document their system architecture and management protocols. These protocols include: security management, data storage management, troubleshooting and technical management. Then the organization needs to use these protocols in order to: (1) detect any risks or threats that need mitigation and communicating, (2) establish benchmarks for future development and (3) create the required chain of custody documentation for the risk assessment process.
Another important aspect about risk assessments, while not explicitly stated in CAN/CGSB- 72.34-2017, it is recommended organizations tackle their risk assessments early in the process of considering new technology. As well, you should make sure you involve your key stakeholders, particularly IT, RM, security, privacy and legal. Depending on your situation, you may need to involve external stakeholders. For example, in British Columbia, New Brunswick and Nova Scotia, public bodies are required to provide their privacy impact assessments to the government and/or their respective Information and Privacy Commissioner for review.34 External review can result in serious impacts to project timelines, scope and delivery so organizations should build the risk assessment into each technology project’s requirements and timelines during early phases. The phases are for new technology or changes to existing technology. They can include: upgrades, add-ons and new modules or integration with other systems. Remember that changes to existing technology can be equally risky as implementing new technologies, depending on the scope of change involved.
Cloud Computing
Section 7.2 of CAN/CGSB-72.34-2017 generally describes cloud computing. Annex D gives more detailed information on cloud computing. CAN/CGSB-72.34-2017 advises that cloud computing, if used by an organization, should be documented in the IT system management guide and RM manual.
Social Media
Section 7.3 of CAN/CGSB-72.34-2017 generally describes social media, including: identification, author/ownership, context, reliability, accuracy and authenticity and chain of custody. To address these issues, organizations are advised to adopt (“shall”) a social media policy that provides for the lifecycle management of postings. Posting are considered records. Annex E gives more information about social media. Like cloud computing, if an organization uses social media, that use should be documented in the IT system management guide and RM manual.
Mobile Devices
Section 7.4 of CAN/CGSB-72.34-2017 generally describes mobile devices, like BYOD and BYOC. Annex F discusses COBO (Corporate Owned Business Only) devices or COPE (Corporate Owned Personally Enabled) devices. IT professionals will find section 7.4 and Annex F particularly useful since they give a great overview of the legal issues and implications and the need for policies, risk assessments, procedures, tight security and so forth. Mobile Device Management (MDM) or Enterprise Mobility Management (EMM) solutions are also touched on.
Annexes
The 6 Annexes of CAN/CGSB-72.34-2017 are additions. They contain “should” statements only. These 6 Annexes are:
- Annex A: Sources for this
- Annex B:
- Annex C: Preservation
- Annex D: Cloud
- Annex E: Social
- Annex F: Mobile
The risk assessment for BYOD in Annex F is extremely valuable and recommended reading for all stakeholders. Annex F provides a great overview of key risk assessment areas across stakeholders, including: security, redundancy, auditability, data-ownership, chain of custody, managing information, retention and legal hold, disposition of information asset, data integrity, employee termination and revenue loss. Thinking about risk management like this will be applicable in other situations as well that an organization faces.
Bibliography
The Bibliography of CAN/CGSB-72.34-2017 lists 18 sources. Of the 18 sources listed, 5 are IT standards. Of those, 2 are also found in the 2005 version:
- CAN/CSA-ISO/IEC 11179-3-04, Information Technology — Metadata Registries (MDR) — Part 3: Registry Metamodel and Basic Attributes; and
- CAN/CSA-ISO/IEC 14662-01, Information Technology — Open-EDI Reference
In 2010, the CAN/CSA-ISO/IEC 14662-01 was revised and replaced by CAN/CSA-ISO/IEC 14662- 10 (R2015). CAN/CSA-ISO/IEC 14662-10 (R2015) is still current.
In 2013, the CAN/CSA-ISO/IEC 11179-3-04 was revised and replaced by ISO/IEC 11179-3:2013. ISO/IEC 11179-3:2013 is still current.
The 3 new IT standards introduced in CAN/CGSB-72.34-2017 on security are:
- ISO/IEC 27001 Information technology – Security techniques – Information management systems – Requirements;
- ISO/IEC 27002 Information technology – Security techniques – Code of practice for security controls; and
- ISO/IEC 27005 Information technology – Security techniques – Information security risk management.
Meanwhile, RM sources increased from 3 to 12 in 2017; 5 ISO standards for RM were introduced, for a total of 7 ISO standards for RM. ARMA International had 4 technical reports and guidelines.
The Uniform Electronic Evidence Act (UEEA), which also had its own annex in the 2005 CGSB version, was dropped by CAN/CGSB-72.34-2017. In CAN/CGSB-72.34-2017, a new source, the Sedona Canada Principles Addressing Electronic Discovery (Second Edition) was added. The changes in sources used from the 2005 to CAN/CGSB-72.34-2017, clearly support the general shift in vocabulary and language from IT to RM that has occurred in business in general.
Organizations may wish to invest in acquiring these 5 IT standards, along with the 12 RM source standards, technical reports and guidelines mentioned in CAN/CGSB-72.34-2017’s bibliography to add to their overall corporate body of knowledge for managing electronic records. At the time of this writing, the CEA, PIPEDA and Sedona Canada are freely available online; those interested in cybersecurity, privacy and data protection law may find these legal sources valuable.
Conclusion: Get CAN/CGSB-72.34-2017 and Implement It!
All organizations should consider investing in implementing CAN/CGSB-72.34-2017 as a clear demonstration of their commitment to preserving the trustworthiness of their records and as ensuring legally admissible evidence from their responsible business management. IT and RM are the technical leads for implementing CAN/CGSB-72.34-2017. As a result, IT and RM need to develop a solid, integrated approach. Improved corporate knowledge management, decision- making and delivery of information services are some of the major benefits that are important to staff in their everyday work. These are important wins for organizations for achieving your long-range targets: reduced information risks and better compliance.
Applying CAN/CGSB-72.34-2017 can provide real practical benefit for organizations. CAN/CGSB- 72.34-2017 can help to:
- increase legal compliance;
- ensure legal admissibility of electronic records;
- reduce electronic information chaos and clutter;
- increase capturing and managing a ‘single source of truth’ and making it available electronically for use; and
- protect information from unauthorized access, disclosure, modifications, use and deletion/destruction.
Our final major point, implementing appropriate standards, systems and procedures for electronic records management improves information governance. It helps organizations create a stable pool of authoritative information that is legally compliant, trustworthy and secureand ready to be optimized and leveraged by systems and technologies. The end-result is a win-win situation for everyone. You can reduce information risk and improve compliance while staff and management can achieve better results with less effort for the information work they are required to do. That, legal, RM and IT friends, is the golden ticket and what we aspire to do.
END
Works Cited
1“Standards Council of Canada,” What is a National Standard of Canada (NSC)?, https://www.scc.ca/en/faq-what- is-a-national-standard-of-canada, accessed on August 24, 2017.
2Section 6.1 General, page 14.
3Section 0.1 About this standard, page iv.
4See https://www.tpsgc-pwgsc.gc.ca/ongc-cgsb/programme-program/normes-standards/notification/sect1b- eng.html.
5Section 5.2 Requirements for admissibility of electronic records as documentary evidence, page 9.
6See https://thesedonaconference.org/publication/The%20Sedona%20Canada%20Principles.
7See http://canlii.ca/t/g7n43.
8The leading test for Canadian courts to qualify experts is White Burgess Langille Inman v. Abbott and Haliburton Co., 2015 SCC 23 (CanLII), http://canlii.ca/t/ghd4f
9Section 6.1 General, page 14.
10Ibid.
11Ibid.
12Ibid.
14Ibid.13 Section 6.3.2 Content of the policy, pages 15-16.
15Section 6.4.1 General, page 16.
16Ibid.
17Ibid.
18Ibid.
19Section 0.1 About this standard, page iv.
20Section 6.4.2.2 Digitization, page 17.
22Section 6.4.5 Records retention requirements, page 18.
24Section 6.4.6.3 Destruction of electronic records, page 19.
25Section 6.4.6.4 Transfer of electronic records to another entity, page 19.
26Section 6.4.6.5 Records preservation, page 19.
27Section 6.4.6.5.1 Records conversion and migration, page 20.
28Ibid.
29Ibid.
30Section 6.4.7 Quality assurance, page 20.
31http://www.forbes.com/sites/gilpress/2013/05/28/a-very-short-history-of-data-science/#7f0fa8cb69fd
32Page 20.
33R.S.C. 1985, c. C-5, http://canlii.ca/t/52zlc
34See sections 69 and 69.1 of the Freedom Of Information And Protection Of Privacy Act, R.S.B.C. 1996, c. 165 (http://canlii.ca/t/52sth), section 77 of the Right to Information and Protection of Privacy Act, S.N.B. 2009, c. R-10.6 (http://canlii.ca/t/52wbq) and section 72 of the Access to Information and Protection of Privacy Act, 2015, S.N.L. 2015, c. A-1.2 (http://canlii.ca/t/52wbq).
Metadata in Recent Canadian Case Law
By Joy Rowe
1.0 Introduction
Metadata underlies every part of modern records management, from the digital records captured in an electronic document and records management system (EDRMS), stored in shared drives to the automatic logs being constantly generated by the computer system. The filename entered before saving a new document, the date and time that reflects the last instance the document was opened, the formulas and scripts linking together different portions of a document such as notes, bibliography and text and the countless “prior edits” automatically registered as this article was being prepared are all part of the hundreds of pieces of metadata that are associated with a typical digital record. Metadata reflects both the traces of human interactions with electronic systems as well as the trails of countless automated computer activities that require no human intervention. As a ubiquitous part of the digital realm, metadata is a key element of the records and information we manage.1
Archivists, concerned with the permanent retention of select digital records, have explored the roles of metadata in the multiple tasks of preservation2. Records managers, involved in the creation and numerous business uses of digital records, have focused on the role of metadata for retrieval functions3. Both professions within the information management field have also considered metadata as part of the legal uses of records. This includes the importance of good metadata for timely, accurate identification of records to facilitate the retrieval of records during the legal discovery and document production processes. It also includes exploring the legal understandings of authentication and integrity of the digital recordkeeping system4.
Many discussions of metadata in the legal context tend to center around the discovery process. This article looks at metadata in the Canadian legal context with a focus on admissibility5. Its purpose is to guide records and information professionals in the multiple metadata tasks undertaken in the course of their work where the legal uses of records and information need to be considered. These may include, but are not limited to:
- establishing meaningful and useful metadata profile in electronic document or record systems;
- communicating important legal distinctions of digital information creation methods to IT or other colleagues, and;
- using basic metadata type classification to correctly characterize electronic information as potential legal evidence for admissibility
Drawing largely from recent case law rulings, this article examines how metadata is treated as electronic evidence in the Canadian legal system. Case law in the area of metadata and electronic evidence in general has expanded greatly in the last ten years. Concentrating on rulings related to admissibility, the leading cases on electronic records6 are presented, including those related to the business records exception to the hearsay rule, best evidence rule and weighting of evidence, use of standards in authentication, and computer- generated versus human-generated electronic records.
2.0 Structure of the article
A historical review of archival and records management literature, beginning with the legal aspects of traditional records and ending with recent work on metadata, is discussed. Then, an overview of the Canadian legal system is given, including how statutory law and case law work together. Next, the main types of evidence – comprising real, documentary, and demonstrative evidence – are presented. Metadata – which include system, substantive, and embedded metadata – are then explored and are shown to be part of real evidence as well as documentary evidence. Finally, the leading Canadian case rulings related to metadata are examined.
3.0 Perspectives on records and the law over time
Archival and records management literature has explored the legal aspects of records from multiple perspectives, including how to maintain records as trustworthy potential legal evidence, the uses of metadata for electronic document discovery, and various typologies to describe and explain metadata. The following section is a review of literature to assist records and information management (RIM) professionals in understanding the foundational knowledge of archival science as well as recent evolutions in the archival and RIM fields.
3.1 Authenticity of documents
Archivists and records managers are keenly aware of the need to manage records as potential evidence. As explained in Sheppard’s 1984 article, “Records and Archives in Court,” archivists need to understand the criteria for admitting records in court as evidence7, including those of authentication, best evidence, and hearsay rules of admissibility. These key aspects of documentary evidence are deeply embedded in archival science; indeed, central archival concepts of authenticity, integrity, and reliability are built on and derived from Western common and civil law systems.
Roman law held records to be trustworthy because they were kept in inviolable places by trusted custodians such as an archives. The spread of Roman law and the credibility it attributed to records led to widespread forgery. To control for improper and untrustworthy records, specific rules were created that are at the root of basic evidence in common law systems: the best evidence rule and the authentication rule8.
Forgery became a common problem, to the point that specific rules had to be introduced to prevent it, such as a requirement of great formality in the creation and structuring of the original record, and a requirement of authentication by experts whenever a record was offered as proof of a fact at issue9. This adaptation of the law to the circumstances of the times is at the root of the two basic rules of evidence in common law: 1) best evidence rule, which gives a preference for an original document when a document is submitted as evidence and 2) the authentication rule, which requires that to adduce a document there must be evidence provided that the document is what it purports to be10.
The methods of authenticating records have changed over time. Archival documents were authenticated by their chain of custody under Roman law. Sir Hilary Jenkinson believed that records were “authenticated by the fact of their official preservation11.” To him, records’ history of legitimate custody was a sufficient guarantee that a record was trustworthy. Another key archival scholar challenged this faith in the chain of custody and stated that records must be tested for indications of their authenticity through studying their provenance and elements of their form (diplomatics)12. Authenticity may be defined as “the quality of a record that is what it purports to be and that is free from tampering or corruption13.” In current Canadian statutory law, authenticating electronic documents is a burden placed on the party adducing the document, who must provide “evidence capable of supporting a finding that the electronic document is that which it is purported to be14” or, stated another way, “capable of supporting a finding of authenticity.”
Archival science and diplomatics provide a model of “record” and a way to define the authenticity of a record. A record is defined as a document made or received in the course of practical activity and set aside for future action or reference15. To establish its authenticity, the record’s integrity and identity must be demonstrated. InterPARES 3 project defines integrity as “the quality of being complete and unaltered in all essential respects” while identity is “the whole of the characteristics of a document or a record that uniquely identify it and distinguish it from any other document or record. With integrity, [identity is] a component of authenticity16.”17
For records created in a digital environment, authenticity is inferred from evidence on how the records have been created and maintained18. In common law legal systems, documentary evidence must be authenticated to be admissible at trial. Authenticity, established through processes of authentication, is codified in our legal systems through statute and common law. Authentication of documentary evidence is accomplished through witness testimony, expert analysis, non-expert opinion, or, in the case of public documents or other special types, circumstances of record creation and preservation19.
3.2 Metadata and electronic documents
In records management (RM) literature , metadata plays many roles over the record life cycle. The Information Governance Maturity Model, which incorporates the Principles® from ARMA International, explicitly cites the role of metadata in an effective information governance system, including the higher levels of principles such as integrity and compliance. Metadata assists in ensuring that information generated has reasonable and suitable guarantees of authenticity and integrity (Integrity Principle) and that an information governance program complies with laws and organizational policies (Compliance Principle)20. The Principles® are a well-known guide for records professionals seeking to assess and improve how records and information are created, managed, and used in organizations21.
Ensuring timely, efficient and accurate retrieval of records, including for legal discovery, is another frequently discussed concern that metadata addresses. Early treatments of metadata for legal purposes tended to draw analogies to analog records. Metadata was initially described in RIM literature using bibliographic schemas, such as the three-way distinction between descriptive, structural, and administrative metadata used widely in the library and archives sphere. This typology of metadata put the focus on availability and retrieval. Descriptive metadata describes a resource for purposes such as discovery and identification. Structural metadata indicates how compound objects are put together.
Administrative metadata provides information to help manage a resource25. This library- informed conception of metadata simply extended the typical tasks of bibliographic retrieval to include legal discovery.
A mid-2000s RIM report also used paper documents as an analogy to describe metadata when considering records as legal evidence. Writing on electronic records as evidence, Mason distinguished between two types of metadata. He used analog document examples to explain the metadata associated with electronic documents using a binary distinction between explicit and implicit metadata. He described explicit metadata as metadata that comes from perusing the paper itself, “such as the title of the document, the date, the name of the person that wrote it, who received it and where the document is located.” Implicit metadata was described as automatically originating from the application software, or being supplied by the records creation. Examples of implicit metadata include “types of type used, such as bold, underline or italic; perhaps the document is located in a coloured file to denote a particular type of document, or labels on file folders26.”
A little over ten years ago, it was common to think of metadata through the lens of a paper document world and to apply existing knowledge on bibliographic and library cataloging systems to explain metadata. While analogies to paper or analog documents are useful for describing the relatively new concept of electronic metadata, it arguably also limits the discussion on metadata drastically. It is certainly useful to know where to look for metadata to assist with a certain task, such as discovery, or to understand that some metadata may be hidden or implicit. However, larger questions such as who creates metadata and how to consider it in legal proceedings are left unanswered. Indeed, courts and the legal community were finding Electronically Stored Information (ESI) and metadata to be less straightforward than previous paper records.
Sedona Canada, coming after the US Sedona Conference Principles of 2007, explicitly acknowledged that ESI was a different animal from analog records. The working group opened its best practices document on electronic discovery in 2008 by explicitly stating: “ESI behaves completely differently from paper documents.”… [It] “can be mishandled in ways that are unknown in the world of paper27.” They also noted that ESI may be created, copied, and distributed without active human involvement28. Unlike paper documents that record or reflect human statements or intentions, electronic information is not necessarily generated as the result of human activity.
As a consequence, the courts and judges seemed unsure on whether computer-generated information such as metadata had anything in common with documents or documentary evidence. R. v. Hall (1998) was an early case in Canada that recognized that computer information was generated with no direct human intervention was admissible as real, rather than documentary evidence. In the mid-2000s, courts on both sides of the border were considering how to treat “hidden” or “embedded” information (i.e. metadata). Courts applied federal and provincial/state rules of court30 and determined with Williams v.
Sprint/United Mgmt Co. (2007)31 in the US and Hummingbird v. Mustafa (2007) in Canada32 that metadata is part of electronic documents and should be produced as part of discovery. In considering discovery questions, the Hummingbird v. Mustafa case ruling determined that metadata should be produced but it also noted that not all metadata will be useful for understanding a document.
The Sedona Principles of the US also concentrated on discovery and production, and they outlined best practices on handling electronic documents. Regarding metadata, the US Sedona Principles stated that metadata can be embedded in the document or stored external to the document on the computer’s file system33. The primary distinction made in US Sedona Principles was between two types of metadata: application and system.
Application metadata is “embedded in the file it describes and moves with the file when it is moved or copied.” System metadata, on the other hand, is stored externally. “System metadata is used by the computer’s file system to track file locations and store information about each file’s name, size, creation, modification, and usage34 35.” This description of metadata moved away from a paper-oriented understanding of documents and shifted focus to the different metadata-generating layers of the computer system.
A different articulation of metadata was elaborated in an ARMA International Education Foundation (AIEF)-commissioned report on “Metadata in Court: What RIM, Legal, and IT Need to Know)36 Isaza described three types of metadata: substantive, system, and embedded. This typology was taken from the American case Aguilar v. Immigration Customs Enforcement Division (2008):
- Substantive metadata is application-based that were not necessarily intended for adversaries to see. Examples of substantive metadata include document author edits, reviewer comments,
- System-based metadata includes information automatically captured by the computer system. Examples of system-based metadata include author name, date and time of creation, and timestamps of
- Embedded metadata consists of text, numbers, and content that is directly input but not necessarily visible on output. Examples of embedded metadata include spreadsheet formulas or hyperlinks to other documents, charts37
While Isaza’s report was on discovery and spoliation and not on issues of admissibility, the metadata distinctions that he included are useful beyond their purposes for discovery.
System metadata (e.g. file names and extensions, sizes, creation dates) is most relevant for authentication purposes. This data could be crucial to authenticating the record for any purpose where authenticity of the record is paramount, like archival or historical uses38 39.
Compared to the role of metadata in assisting with timely discovery, there is much more limited discussion in RIM literature on metadata and its role in legal cases, including the role of metadata in establishing the authenticity of records for admissibility purposes. This may be due to the fact that very few records professionals are called upon as expert witnesses to authenticate digital records before a trier of fact in a court case. In a transnational survey of records professionals, only about 5% of 293 respondents had ever been required to authenticate digital records before a court during the course of their career. In follow-up interviews, some respondents commented that they were more likely to be involved in the production phase, while IT professionals were likely to be called to act as experts of the system40.
In Canadian court cases, this experience also holds true. Records professionals are infrequently called upon to authenticate digital records or the systems in which they reside. A recent exception includes R. v. Oler. This case is discussed further in 5.3: Use of standards in authentication.
Contributions to RIM literature from records professionals with direct experience in authenticating digital records or testifying to the integrity of their records system would be meaningful and useful to the records management community. In the meantime, recent court rulings on electronic evidence give important insight into how metadata is being addressed and considered in today’s Canadian courts.
4.0 Legal foundations
Having explored the contributions of archival and records scholars on the topic of the legal uses of records and metadata, it is also important to understand the legal context of how Canadian legal decisions are made. The following section is intended to outline the basic elements of the Canadian legal framework for RIM professionals who may not be experts in case law. The main sources of law are explained, including the distinctions between federal and provincial Evidence Acts. The different types of evidence as well as admissibility rules are described. RIM professionals have a particular contribution to make in understanding and correctly characterizing how the ESI was created. Understanding the wider context of law can greatly assist RIM professionals in ensuring that the appropriate rules of evidence are applied when and if they are called upon to assist in a legal trial.
4.1 Statutory and case law
As is the case in most common law jurisdictions, evidence law in Canada comes primarily from common law, which does not vary among jurisdictions. Each court applies essentially the same evidence law, but each jurisdiction also has evidence acts (statutory law) that may modify or supplement common evidence law41 Two main sources of law are 1) enacted statutes and 2) cases adjudicated by judges in courts of law. Legislative bodies, including the Parliament of Canada, the ten provincial legislatures, and the three territories, are granted the legislative authority to enact statutes42 These sovereign legislative bodies may delegate authority to a subordinate body to create rules, as Ontario’s Courts of Justice Act delegates rule-making authority to the Civil Rules Committee43. Rules of courts are therefore a type of subordinate legislation and are a part of statutory law.
In addition to statutory law, case law is the second major source of law. Case law comes from the written decisions of courts on particular matters. Judges’ decisions, and the stated reasons for those decisions, serve as precedence for future courts deciding on similar situations. Courts are bound to follow precedent cases, and the body of case law develops to give guidance to judges as they decide on contemporary matters44.
Statutes and regulations, such as court Rules of Civil Procedure, operate together to form a code of procedural law; while they work in tandem, the majority of procedural law in Canadian Superior Courts is set out by the Rules rather than by any statute45. The Civil Rules Committee has delegated legislative authority to make rules in relation to the practice and procedure of the Court of Appeals and Superior Court in all civil proceedings for the relevant jurisdiction (federal, provincial)46.
The rules of court may not conflict with what is stated in an Act, such as the Evidence or Interpretation Act. However, they may supplement what is provided in the Act by further articulating practice and procedure47. Rules of court give guidelines to judges and lawyers on how things shall be done during a trial and codify expectations and common understandings.
Federal matters and criminal cases are tried under the Canada Evidence Act, and each province and territory has its own evidence act for civil and provincial matters48. Issues specific to electronic evidence have been largely coordinated among the jurisdictions through the Uniform Electronic Evidence Act49. Through the adoption of Uniform Electronic Evidence Act provisions, the focus was shifted away from satisfying authentication and best evidence of a particular record. Instead, the focus moved to inferring trustworthiness from the integrity of the electronic system. The adducing party is required to show that the system was operating as expected when the record was created. If this is done, the evidentiary requirements are satisfied50.
4.2 Types of evidence
Evidence is submitted in the form of either oral testimony by witnesses or as real evidence51. As established by statutory law and case law, evidence may be of three main types: real evidence, documentary evidence, and demonstrative evidence. The first type, real evidence, speaks for itself. The trier of fact (judge, jury, or other adjudicator) can use their own reasoning to understand real evidence and can draw conclusions based on what is presented. In a murder trial, a gun registered to the accused may be real evidence52.
The second type, documentary evidence, is evidence that is offered for the truth of the statement it contains53. It is not the fact that the evidence is in a document form which makes it documentary evidence. The crucial characteristic of documentary evidence is that it is “a recording … of an out-of-court statement of fact made by a person who is not called as a witness, that is tendered for the truth of the statement it contains54.”
The third type, demonstrative evidence, is evidence that is not strictly material to the case but which can help the trier of fact interpret the material facts55 Digital animations or other computer-generated images are examples of demonstrative evidence but they tend to require expert testimony to accompany them. Tests for expert opinion rules will usually apply, including cost-benefit analysis of whether the demonstrative evidence helps the jury or trier of fact to understand the evidence without creating a prejudicial effect and distorting the fact finding process56. Demonstrative evidence can in turn be testimonial (e.g. expert witness), documentary (e.g. medical illustration and photographs of an injury), or real (e.g. videotaped re-enactments of events to contextualize witness testimony)57.
A leading case on electronic records acknowledged that metadata may complicate these boundaries of evidence. In Saturley v. CIBC World Markets, Justice Wood stated, “It is possible that a given item of electronic information may have aspects of both real and documentary evidence58.” An email, for instance, has automatically generated metadata that records when the message was sent and from which computer. These “statements” are not made by a person who could be called as a witness and cannot be properly called documentary evidence. The email also has statements made by human declarants in its contents such as the message text itself. As such, an email has components that may be either real or documentary evidence.
4.3 Admissibility rules
The basic principles of evidence at trial include admissibility, weight, and standards of proof. These apply regardless of type of evidence. Admissibility and weight are formally kept separate. Admissibility is the judge or court’s determination that the evidence can be presented during the trial. The judge (or trier of law) determines if the evidence is relevant to a material fact in the case59. The item must have some tendency to make the existence of a fact in the case more or less probable. Admitted evidence becomes part of the body of evidence that goes before the trier of fact (either a judge or jury) who must, at the end of the trial, determine the “weight” of evidence. This includes determinations of which parts are accepted and which are rejected based on the standard of proof; for civil cases, the party admitting the evidence must prove that the evidence is true based on the balance of probabilities, while for criminal cases, the measure used is beyond reasonable doubt60.
In order to be admitted as evidence in court, potential evidence must pass various tests of admissibility. Some admissibility criteria and appropriate rules of evidence apply to all types of evidence. For example, rules of materiality and relevance apply without regard to evidence type61. Evidence must assist the trier of fact in drawing the necessary inferences (weight), and it must be relevant to the issues or events in question (relevance).
Another admissibility rule, the best evidence rule, says that if there are two records with the same content, then the one that is the “original” will be accepted. Electronic documents can fulfill the best evidence rule if the adducing party provides evidence that speaks to the “integrity of the electronic documents system by and in which the electronic document was records or stored62.” Proof of integrity can be established through proof that the storage medium (e.g. hard drive, operating system) was operating properly, proof that the document was recorded or stored by the other (“adverse”) party63, or proof that the document was recorded or stored in the ordinary course of business64. Integrity can be proven by an affidavit or expert evidence65. Integrity of the system can also be proven by providing evidence that current standards, procedures, and practices were adhered to66. Finally, a print out of an electronic document that was “manifestly or consistently acted upon” as a record, can be deemed as best evidence67.
Other rules of admissibility differ according to the type of evidence considered68. The hearsay rule and its exceptions, for instance, only apply to statements that are made by humans. The hearsay rule prevents statements by a person who cannot be examined as a witness from becoming evidence in court.
Authentication of analog documents often involves having the author confirm that they created it or having a witness confirm that they saw the creation of the document.
Authentication of electronic evidence focuses on the metadata associated with the documents or on the metadata traces left behind when the document was created. The process of creating, saving and editing an electronic document leaves evidence fragments in the form of metadata that can be used to authenticate electronic evidence69.
4.4 ESI as real and documentary evidence
ESI may be admitted as real, rather than documentary, evidence. Underwood and Penner note that while the distinction between ESI as real or documentary evidence has been recognized in English and American courts, Canadian treatment of ESI as real evidence has been less uniform. They note that Canadian counsel and courts to date (i.e. 2010) have failed to properly characterize ESI as real or documentary at the outset of proceedings, leading to a failure in applying the appropriate rules of evidence to determine admissibility70. Properly characterized ESI entails an understanding of both how it was created and the purpose for which it is tendered. While legal counsel may ably address the latter question, it is in the realm of records and information management professionals to understand the former and to correctly characterize how the ESI was created so that the appropriate rules of evidence can be applied.
Evidence may be real evidence either for the purpose it is submitted or for the manner in which it was created. If either of the following conditions apply, the evidence should be submitted as real evidence:
- the ESI is not tendered for the purpose of the truth of its content, but rather for the fact that it existed or was found in the possession of a person;
- the information embodied in the ESI does not depend upon the interposition of a human observer or recorder between the external event and the ESI that captures the information about the event. This ESI results from an automated process, or is computer-generated71
ESI, metadata associated with electronic documents, or analog documents can all be admitted as real evidence when their purpose is to serve as proof of the fact of their own existence rather than for the purpose of providing the truth of the statements they contain72. An email and its associated metadata may be entered as real evidence if they are tendered as proof that the sender sent the communication at a certain time, or to link the statements contained in the email to the author73. However, if the email is submitted because of the contents of the message, it would be adduced as documentary evidence74. The purpose the evidence is intended to serve is more important than the form the evidence takes.
Canadian courts tended to treat ESI that is automatically generated in same fashion as documentary evidence and admit them under the exception to the hearsay rule, rather than admit them as real evidence75. However, since the publication of Underwood and Penner, several Canadian courts’ rulings, including the influential Saturley v. World CIBC Markets, have cited their work and have made finer distinctions between ESI as real or documentary evidence76. Saturley cited this useful passage from Underwood and Penner’s Electronic Evidence in Canada to explain the distinction:
A record that is created by a computer system whose function it is to capture information about cellular telephone calls would be introduced as real evidence, and the record could be relied upon for the truth of its contents without resort to any exception to the hearsay rule. Because the information that is captured (the date, time and duration of the call, for example) is recorded automatically without being filtered through a human observer, the condition for real ESI evidence is satisfied. It is also important to note that the information recorded is itself not an out-of-court statement by a human declarant, but rather it consists of objective information that is captured and recorded by an automated process.
On the other hand, if a record is created by a human sitting at a computer keyboard and entering data, the ESI embodied in the record could not be tendered as real evidence if it is offered for the truth of its contents, and its proponent would have to bring the record within the ambit of an exception to the rule against hearsay. The record would be documentary evidence, and subject to the same limitations as would apply to a conventional document. The information contained in the record has been filtered through a human observer, and the ESI reflects the human declarant’s out-of-court statements concerning what he or she observed, heard or did. It is not real evidence77.
When ESI is not properly characterized as either real or documentary, the unstated assumption is that ESI is documentary and, consequently, hearsay78. However, if ESI is automatically generated or may otherwise be characterized as real evidence, the evidentiary rules relating to documentary evidence need not be applied79 80.
Metadata is one of the most important sources of real evidence81. Some, but not all, metadata is automatically generated and, if properly characterized, need not be admitted as documentary evidence and need not meet the admissibility criteria for hearsay exceptions.
ESI as real evidence must have evidence to establish the authenticity and threshold reliability established to be admissible82. Threshold reliability exists on a spectrum, from “utterly unreliable to highly reliable.” The proponent offering the evidence must satisfy the judge that the information is, on the balance of probabilities, sufficiently reliable. It need not be error-free. Like documentary evidence, such matters of potential of error go to weight, not admissibility83.
The type of metadata can assist in correctly characterizing the evidence under consideration. A useful typology of metadata from the US Aguilar case was elaborated to assist in making evidence type distinctions. The metadata types of system, substantive, and embedded are created with varying levels of human input84.
System metadata is an automatic capture of data from the system that created the electronic document and is a type of real evidence that includes the date and time the file was created, as well as details on when the file was modified or viewed. System metadata does not record any out-of-court statements made by human declarants and is therefore not documentary evidence. This type of metadata changes readily and may be intentionally or unintentionally altered. To pass admissibility tests of reliability and authenticity of real evidence, system metadata often must be subjected to expert forensic analysis85.
Substantive metadata is also called application metadata, because it is generated by the application software. It captures information about the creation and editing history of the electronic document. This type of metadata shows prior edits or modifications to the file and includes formatting display rules like font type and line spacing. Depending on the type of information it captures and how it will be put to use, substantive metadata may be either documentary or real evidence86. When the metadata is captured automatically and used to show that a comment or text edit has been included, the metadata is usually considered real evidence. When the metadata is being admitted to prove the truth of the content of a comment or text edit, the substantive metadata would be considered documentary evidence instead87.
Embedded metadata is information that is part of the electronic document because the user placed it there. Examples include spreadsheet formulas, hyperlinks to other documents, a video clip included in a PowerPoint presentation, or even hidden cells or linking relationships in a database. Embedded metadata is rarely automatically generated by the computer system or application software; as such, embedded metadata is most frequently considered documentary evidence88.
5.0 Metadata and case law
Like digital information itself, case rulings on ESI and metadata have grown drastically as courts and judges have become more accustomed to admitting and weighing electronic evidence. RIM professionals can benefit from understanding trends of the courts such as the “principled approach” to the hearsay rule, the precedent-setting use of RIM professionals and Canadian and international standards in the authentication of evidence, and the potential for automatically-generated metadata to be adduced as real evidence.
Below, recent relevant case law has been conveniently grouped by theme or finding as it relates to the RIM profession.
Federal, provincial and territorial case law has gradually been building a body of rulings concerning different types of metadata and types of ESI evidence. In the last ten years, there has been a marked increase in cases that consider questions of electronic evidence. Between the years of 1996 – 2006, nineteen cases dealt with electronic records89. In the last ten years from 2007 – 2017, 262 cases have considered ESI, metadata or computer evidence. The treatment of metadata has become more firmly rooted in Canadian case law. This section looks at the leading cases on electronic records under the business records exception to the hearsay rule, best evidence and weight, use of standards in authentication, and computer-generated versus human-generated electronic records.
5.1 Business records as hearsay exception
A recent and leading case in British Columbia systematically applied the federal Evidence Act to several documents that had been previously ruled inadmissible by a summary trial judge in a case of an insurance claim for disability payments. Certain portions of the presented evidence were ruled inadmissible as business records exceptions to the hearsay rule; in McGarry v. Co-operators Life Insurance90, the court reconsidered the ruling and specifically looked at attachments to a witness testimony, which are both paper documents such as printed policies and quotes and as well as emails.
The majority of the British Columbia Court of Appeal went through the exhibits and used the “principled approach” to the hearsay rule cited in RS II Film Distribution v. BC Trade Development Corp91. to consider reliability. Specifically, indicators of reliability include whether the source of the information, preparer of the document, and creation date are known, and whether there is anything on the document itself that indicates it was made in the “ordinary course of business92“. The majority of the BC Court of Appeal then went through each document previously ruled inadmissible as a business record exception, they applied s.42 of the Evidence Act93 to the affidavit and its accompanying documents, and they concluded which data establish that the record is reliable (chiefly, the date it was created and whether one of the businesses involved in the case produced the record, as indicated by signatures, document headers, etc.).
The majority of the BC Court of Appeal addressed the question of emails as business records, noting that the Evidence Act of British Columbia does not discuss electronic records or provide criteria for considering them as evidence. They noted that other provinces do, however, and other provincial Evidence Acts94 outline specific concerns regarding authenticity and requirements that the submitting party provide evidence of the integrity of the electronic document system. They noted that since the emails in this case were deemed inadmissible, along with the other documentary evidence, these tests of authenticity and integrity were not performed or considered95. The admissibility of the emails cannot be determined, because these issues were not addressed in the trial case.
However, the majority determined that because all of the evidence in this case was documentary, it was feasible and practical to make a fresh assessment of the evidence, including the evidence (such as the emails) previously declared inadmissible by the summary trial judge96. The decision thereby implicitly determined that the emails are documentary evidence, despite the barriers to determining their authenticity or the integrity of the electronic document system they were created on.
This case is largely cited in other cases for the finding in paragraph 81 that if all the evidence is documentary, it is feasible for an appeal court to make a fresh assessment of the evidence in the case97.
Other cases on the topic of admitting evidence under burden of s.31 or with evidence of authenticity, integrity and identity include R. v. MacDonald 2016 ABPC 142 at para. 27, R. v J.S.M 2015 312 at para. 53-54, R. v. Soh 2014 NBQB 20 at para. 31-32, R. v. K.M. 2016 NWTSC 36 at 57-60, R. v. Bernard 2016 NSSC 358 at para. 50-58.
5.2 Best evidence, low threshold for admissibility, weight, authentication98
The three aspects of the admissibility of documents are the hearsay rule, authentication, and the best evidence rule. Documents must be adduced for the truth of their contents to be classified as hearsay and to be admissible under the business records or other exception.
There must be evidence that the document is what it purports to be (authentication rule), and that it fulfills the preference for the original of that document (best evidence rule)99. These aspects of documentary evidence have been blurred in court rulings, and, due to the generally low threshold in Canadian evidence law admissibility, any potential for error or suspect quality in the reliability of the evidence will usually go to weight, especially in civil cases100.
Several rulings in the last ten years have stated that concerns about completeness and integrity can be dealt with at trial when the trier of fact determines the appropriate weight to give the evidence. Additionally, questions about whether the presented evidence meets the best evidence rule also do not bar the evidence from admission. These questions are also resolved at the end of the trial during the process of weighting the evidence.
Some examples of these rulings are:
BL. v. Saskatchewan (Social Services)
All of these inherent frailties and features of the IEIS [Integrated Electronic Information System] records do not make them any less a record of the act, transaction, occurrence or event. The frailties may go to weight or ultimate reliability but do not exclude the records as a business record101.
R. v. Hamdan
[T]he best evidence rule has been relaxed, in part to address technological changes over the past 50 years; the standard is no longer stringent. Where the original document is not in hand, the best evidence rule does not bar admission of secondary evidence of the document, even where it may be incomplete or inaccurate. Concerns about completeness and integrity can be dealt with at trial when the trier of fact determines the appropriate weight to give the evidence102
Leading Canadian legal scholars also note that the best evidence rule has decreasing value in the modern era. Authentication, the main requirement for admissibility, is a relatively low threshold to achieve. Authors of “The Law of Evidence in Canada” write, “[t]he modern common law, statutory provisions, rules of practice and modern technology have rendered the [best evidence] rule obsolete in most cases and the question is one of weight and not admissibility.”103
Paciocco, the co-author of both Canada’s leading text in evidentiary law as well as a frequently-cited text on electronic evidence,104 notes that if a document is authenticated, it is admissible even though some of the information in the document may be inaccurate. The potential for inaccuracy is a matter of weight, not admissibility. If an electronic document may have been altered or have inaccurate metadata, the potential imprecision should not affect the admissibility of the document105. Admissibility is a threshold test, and judges prefer to admit evidence and then weight it all at the end when credentials and believability of witnesses or experts can be established better106.
Numerous recent cases have drawn on Paciocco’s articulation of the low threshold of admissibility and “antiquated best evidence” statements to admit electronic records and to consider reliability, best evidence, and questions of the integrity of the system as factors in weight at the end of the trial. For example, R. v. C.L. (2017) considered the admissibility of copy-pasted and printed-out copy of an instant messenger (IM) conversation, including the inaccurate time-stamp metadata. As documentary evidence, the judge accepted the printout as best evidence and determines that witness confirmation that it is a true reflection of the original IM conversation is sufficient authentication, noting that the low threshold for admissibility has been met.
The common law imposes a relatively low standard for authentication; all that is needed is “some evidence” to support the conclusion that the thing is what the party presenting it claims it to be. As Paciocco states, for the purposes of admissibility authentication is “nothing more than a threshold test requiring that there be some basis for leaving the evidence to the fact-finder for ultimate evaluation107.”
Similarly, in R. v. Hirsch, the majority of appeals judges denied an appeal of a criminal code conviction based on three claims, including that the documentary evidence had not been authenticated108. This included screen captures of digital photographs on a Facebook page. This court determined that due to the low threshold of authentication, it was acceptable to accept witness testimony that they saw the post or have some other reasonable basis for believing the screen capture to be what it purports to be109.
I am not persuaded by Mr. Hirsch’s arguments on authentication and the related issue of authorship. In my assessment, s. 31.1 of the Canada Evidence Act is a codification of the common law rule of evidence authentication. The provision merely requires the party seeking to adduce an electronic document into evidence to prove that the electronic document is what it purports to be. This may be done through direct or circumstantial evidence…. Quite simply, to authenticate an electronic document, counsel could present it to a witness for identification and, presumably, the witness would articulate some basis for authenticating it as what it purported to be…. That is, while authentication is required, it is not an onerous requirement110.
Other cases on the low threshold for admissibility or the “antiquated” best evidence rule include R. v. Dennis James Oland, 2015 NBQB 245 at para. 43, R. v. Clarke, 2016 ONSC 3564 at para. 53-55, R. v. Avanes et al., 2015 ONCJ 606, and the labour arbitration ruling of Thacker v. Iamaw, District Lodge 140, 2016 CanLII 62600 (BC LA) at para. 52-54.
5.3 Use of standards in authentication
Compliance with standards such as the Canadian General Standards Board, CAN/CGSB- 72.34-2017 Electronic records as documentary evidence is one of the ways to determine if electronic evidence is admissible. According to s. 31.5 of the Canada Evidence Act,111 electronic documents that are created or stored in accordance with a standard can be considered authenticated and admissible. This was also recently confirmed in case law through the Voir Dire ruling of R. v. Oler112.
- v. Oler is an impaired driving criminal case where the facts must be proven beyond reasonable doubt. In this case, the evidence of the breathalyzer records of the Calgary Police Service were ruled to be admissible. The testimony of their records manager professional provided an expert opinion as to the integrity of the recordkeeping system they were created in. The expert explained that the records were created in accordance with their procedures manual which included security protocols and quality assurance processes; and that the electronic records management system (ERMS) system contained a permanent audit trail. Further, the ERMS is a DoD 5015.02 certified record system. The court ruled that these records were made in the usual and ordinary course of the business and that all evidentiary rules of authenticity, integrity and reliability had been satisfied because they were created in compliance with CAN/CGSB-72.34-2005113. A “live” document that could be updated (was not in a fixed form) was ruled admissible as a business record but the judge noted that weight should consider that it does not meet the same CAN/CGSB-72.34-2005 standards114.
5.4 Computer-generated versus human-generated
As noted earlier, courts and judges have struggled with how to treat electronically stored information. A key distinction discussed in numerous cases is the determination of how or by whom the information was generated. If the computer information was generated automatically, the evidence is often – but not always – considered to be real evidence. Real evidence needs to be authenticated, but it does not need to meet best evidence or hearsay exception rules.
If the ESI is not automatically generated and was instead created as the result of human intervention, the evidence is generally adduced as documentary evidence and must meet the relevant admissibility criteria.
Desgagne v. Yuen (2006) was a motion seeking the production of the plaintiff’s home computer hard drive and other devices, including the electronic documents, metadata, and internet browser history stored on them115. The court addressed whether metadata is a document, noting that “[t]he information being sought does not fit the ordinary or intuitive concept of a document, electronic of otherwise116.” The data being considered was an automatically generated record of the user’s activities that was not printed nor used in the ordinary course of any business. In spite of these facts, the court noted that the metadata is “information recorded or stored by means of [a] device and is therefore a document” under the BC provincial Rules of Court under Rule 1(8)117.
In seeking to produce a hard drive, it is not necessary to determine whether the ESI is real or documentary evidence. Instead, the metadata must have probative value and be relevant to the facts of the case. In Desagne, the judge stated that metadata that was automatically generated could be considered a document but denied the production order because the electronic files and metadata was not demonstrably relevant and the usefulness of metadata and browser history do not offset privacy concerns118. This case is widely cited for the relevancy limits it places on production orders for metadata and electronic evidence.
In some cases, it is not entirely straightforward whether the data or metadata was generated by a human or by a computer. The Animal Welfare cases considered the situation of scripts. The defendants119 sought to enter evidence of databases, reports generated from SQL scripts, Excel formatted databases or generated outputs from these databases, printed graphs, and screenshots. Some of this evidence – specifically the Sales data and the Customer data that were extracted from a database using SQL scripts – was offered to the court as real evidence.
The plaintiff argued that the scripts used to generate reports show evidence of human skill and experience and were subject to error, making them subject to hearsay admissibility tests. The judge determined that the tests needed to take place on the data, not the scripts, and stated that scripts retrieve the data but do not change the data120. The data were automatically captured by the computer system and are not out-of-court statements.
Accordingly, only authentication was required for admissibility121.
A later ruling122 revealed crucial details about script creation. During this case, the questionable integrity of the database was discussed, including chain of custody. The case also considered testimonial evidence from the person who created the scripts that extracted the data being entered into evidence. The script writer admitted that she was instructed to continue working on the script until it generated favourable results to the plaintiff, and she was in the employment of the plaintiff123.
Scripts are human-created and can be tampered with to achieve a human desired outcome. In this case, the judge did not re-determine the nature of the evidence but instead used different evidence to reach his final ruling124. Ultimately, concerns on the reliability of the script-generated reports were considered during the weighting of the evidence.
Once metadata or electronic information has been determined to be real evidence, Saturley, supra considered how to sufficiently establish the admissibility of such evidence. The party offering the evidence needs to establish that the information was automatically generated. They need not give evidence that the computer information is error-free. The court held:
The first step in the admissibility analysis is to determine whether the party offering the evidence can establish on a balance of probabilities that it fits within the parameters of real evidence as discussed above. That means, it must be data collected automatically by a computer system without human intervention. It appears that this could include a threshold consideration of reliability; however, it is important to remember that reliability is primarily an issue that goes to the weight to be given the evidence and not its admissibility125.
Other cases finding automatically generated metadata or ESI to be real evidence and subject only to authentication include R. v. Nardi, [2012] BCPC 318 at para. 22, R. v. Soh, [2014] NBQB 20 at para. 31, R. v. Mondor, 2014 ONCJ 135 at para. 17-19. R. v. Bernard (2016) finds that although aspects of the evidence is automatically generated metadata, Facebook screenshots are documentary evidence (and inadmissible due to lack of authentication)126.
6.0 Conclusions
Metadata is frequently generated automatically. Indeed, automatic creation and assignment of metadata can be an indicator of a well-developed information governance system127. Computer-generated metadata easily meets the test for real evidence and can be admissible after passing the authentication test. Increasingly, Canadian courts are acknowledging that automatically generated metadata need not fulfill the evidence tests related to documentary evidence.
Records professionals, who have ideally been involved in all stages of the record life cycle, are well-placed to be able to speak on how metadata was created. To properly characterize metadata as legal evidence, RIM professionals should consider using the three-way distinction described in Underwood and Penner: system, substantive, and metadata.
In determining the type of metadata as it relates to evidence, RIM professionals can start the analysis by considering whether the metadata has been created at the system-level of the network. System metadata has multiple legal purposes. Automatically-generated system metadata can be used in authentication during a trial for both documentary and real electronic evidence. System metadata itself is most likely to be considered real, rather than documentary, evidence.
Substantive metadata can be either documentary or real evidence. Automatically captured edit tracking, for instance, may be real evidence. Substantive metadata may also be evidence of human interaction and is likely to be considered documentary evidence.
Information professionals should be ready to provide information to satisfy the admissibility and weighting rules of documentary evidence, including business records exception to the hearsay rule, authentication through metadata, and proof of integrity of the system through expert testimony or other means.
Embedded metadata has caused some confusion in courts, such as the Animal Welfare rulings. Information professionals should be ready to clearly describe how metadata such as scripts or formulas are executed without human intervention. Otherwise, embedded metadata is likely to be considered documentary evidence, and information professionals should be prepared to satisfy the documentary evidence rules.
RIM professionals interact with, create, and manage metadata in numerous tasks during the course of their work. Although the legal uses of metadata are always evolving as case law advances, RIM professionals can benefit from a solid understanding of the Canadian legal framework and recent case law rulings on the topic. Armed with this knowledge, RIM professionals will be in a better position to make decisions about the automatic generation of metadata, how best to set up metadata profiles, and how to communicate important legal distinctions with IT and others on how metadata is used in Canadian courts today.
Publication bibliography
“ABA-LawyersCanSearch Metadata.” Information Management Journal May/June (2007): 11.
Aguilar v. Immigration and Customs Enforcement Div. of U.S. Dept. of Homeland Sec., 255 F.R.D. 350 (S.D.N.Y. Nov. 21, 2008), November 21, 2008.
Alberta Evidence Act, R.S.A. c. A-18, s. 41 (1980), accessed on 2017-10-31, http://canlii.ca/t/52fmm. Animal Welfare International Inc. v. W3 International Media Ltd., 2013 BCSC 2193 (CanLII), accessed on 2017-08-30, http://canlii.ca/t/g23fg.
Animal Welfare International Inc. v. W3 International Media Ltd., 2014 BCSC 1839 (CanLII), accessed on 2017-08-30, http://canlii.ca/t/gds4d.
“Backgrounder: The Honourable Justice David M. Paciocco’s Questionnaire”. Department of Justice, Government of Canada. Last modified on April 07, 2017, https://www.canada.ca/en/department- justice/news/2017/04/the_honourable_justicedavidmpacioccosquestionnaire.html.
BL v Saskatchewan (Social Services), 2012 SKCA 38 (CanLII), accessed on 2017-08-27, http://canlii.ca/t/fqtnj.
Bryant, Alan W., Sidney N. Lederman, Michelle K. Fuerst, and John Sopinka. The law of evidence in Canada.
Markham, Ont: LexisNexis, 2009.
Canada Evidence Act. RSC 1985, c C-5, (1985), accessed on 2017-10-31, http://canlii.ca/t/52zlc. Canadian General Standards Board, CAN/CGSB 72.34-2017 Electronic records as documentary evidence.
Gatineau, Québec: Canadian General Standards Board. 2017, accessed on 2017-10-31, http://publications.gc.ca/collections/collection_2017/ongc-cgsb/P29-072-034-2017-eng.pdf.
Cook, Michael. The Management of Information from Archives. Aldershot, Hants, England, Brookfield, Vt., USA: Gower, 1986.
Currie, Robert, and Steve Coughlan. “Canada (Chapter 9).” In Electronic Evidence, 3rd edition, edited by Stephen Mason. 283–325. Lexis Nexis, 2012. https://ssrn.com/abstract=2324273.
Delisle, RJ. Evidence: principles and problems. 10th ed. Toronto: Carswell, 2010.
Desgagne v. Yuen et al, 2006 BCSC 955 (CanLII), accessed on 2017-09-01, http://canlii.ca/t/1nnpc. Duranti, Luciana. “From digital diplomatics to digital records forensics.” Archivaria 68 (Fall 2009): 39–66.
Duranti, Luciana, and Randy Preston. International research on permanent authentic records in electronic systems (InterPARES) 2: Experiential, interactive and dynamic records. CLEUP, 2008.
Duranti, Luciana, and Corinne Rogers. “Trust in Digital Records: An Increasingly Cloudy Legal Area.” Computer Law Security Review 28, no. 5 (2012): 522–31.
Duranti, Luciana, Corinne Rogers, and Anthony Sheppard. “Electronic Records and the Law of Evidence in Canada: The Uniform Electronic Evidence Act Twelve Years Later.” Archivaria 70, (Fall 2010): 95–124.
Duranti, Luciana, and Kenneth Thibodeau. “The concept of record in interactive, experiential and dynamic environments: the view of InterPARES.” Archival Science 6, no. 1 (2006): 13-68.
Evidence Act, RSO 1990, c E.23, accessed on 2017-10-31, http://canlii.ca/t/l1vl. Evidence Act, SS 2006, c E-11.2, accessed on 2017-10-31, http://canlii.ca/t/52w3h.
Force, Donald C. “From Peruvian Guano to Electronic Records: Canadian E-Discovery and Records Professionals.” Archivaria 69 (2010): 49–75.
Franks, Pat, and Nancy Kunde. “Why METADATA Matters.” Information Management Journal Sept/Oct (2006): 55–61.
Gable, Julie. “Examining metadata: Its role in e-discovery and the future of records managers.” Information Management Journal 43, no. 5 (2009): 28–32.
Gall. GL, FP Eliadis, and F Allard. The Canadian legal system, 5th ed. Scarborough, Ont: Carswell, 2004.
Halsbury’s laws of Canada: Civil Procedure. Markham, Ont.: LexisNexis, 2012. “Information Governance Maturity Model.” ARMA International, 2013.
Hummingbird v. Mustafa, 2007 CanLII 39610 (ON SC), accessed on 2017-08-27, http://canlii.ca/t/1t0tp. InterPARES 3 Project. Terminology database, accessed on 2017-08-20,
http://www.interpares.org/ip3/ip3_terminology_db.cfm.
Isaza, John. “Metadata In Court: What RIM, Legal and IT Need to Know.” ARMA International Education Foundation, Pittsburgh PA, Nov 2010.
Jenkinson, Hilary. A Manual of Archive Administration. New and Revised. London: Percy Lund, Humphries Co. 1937.
Lemieux, Victoria, Brianna Gormly, and Lyse Rowledge. “Meeting Big Data challenges with visual analytics: The role of records management.” Records Management Journal 24, no. 2 (2014): 122-141.
Mancuso, Lara. “Exploring the Potential of Naming Conventions as Metadata.” Independent study paper, University of British Columbia, 2013.
Manitoba Evidence Act, R.S.M., c. E150 (1987), accessed on 2017-10-31, http://canlii.ca/t/lb8k.
Mason, Stephen. “Authentic Digital Records: Laying the Foundation for Evidence.” Information Management Journal 41, no. 5 (Sept/Oct 2007): 32–40. http://www.arma.org/bookstore/files/Mason.pdf.
Mason, Stephen. “Proof of the Authenticity of a Document in Electronic Format Introduced as Evidence.” ARMA International Educational Foundation, Pittsburg, PA, October 2006, accessed on 2017-08-25, https://pdfs.semanticscholar.org/8ae3/d41b6c962d141ddb23640418ecaed6a0fa17.pdf.
McGarry v. Co-operators Life Insurance Co., 2011 BCCA 214 (CanLII), accessed on 2017-08-27, http://canlii.ca/t/fl636.
Owens, Scott. “Best Evidence in Canada: An Analysis of Issues and Case Law” SSHIRC project paper, University of British Columbia, 2014.
Paciocco, D. M. “Proof and progress: Coping with the law of evidence in a technological age.” Canadian Journal of Law and Technology 11, no. 2 (2015): 181–228.
Preston, Randy. “InterPARES 2 Chain of Preservation (COP) Model Metadata” (Draft report). (2009).
RS II Productions Inc. v. B.C. Trade Development Corp., 2000 BCCA 674 (CanLII), accessed on 2017-08-27, http://canlii.ca/t/1fnb1.
- v. Avanes et al., 2015 ONCJ 606 (CanLII), accessed on 2017-09-01, http://canlii.ca/t/gltb6.
- v Bernard, 2016 NSSC 358 (CanLII), accessed on 2017-08-27, http://canlii.ca/t/h3w44.
- v Clarke, 2016 ONSC 3564 (CanLII), accessed on 2017-08-27, http://canlii.ca/t/gsldq
- v C.L., 2017 ONSC 3583 (CanLII), accessed on 2017-08-27, http://canlii.ca/t/h4xxp.
- v. Hall, 1998 CanLII 3955 (BC SC), accessed on 2017-08-30, http://canlii.ca/t/1f7fx.
- v Hamdan, 2017 BCSC 676 (CanLII), accessed on 2017-08-27, http://canlii.ca/t/h3xdd.
R v Hirsch, 2017 SKCA 14 (CanLII), accessed on 2017-08-27, http://canlii.ca/t/gxq03.
- v. J.S.M., 2015 NSSC 312 (CanLII), accessed on 2017-08-27, http://canlii.ca/t/gmmml.
R v. K.M., 2016 NWTSC 36 (CanLII), accessed on 2017-08-27, http://canlii.ca/t/gs4mv.
- v. MacDonald, 2016 ABPC 142 (CanLII), accessed on 2017-08-27, http://canlii.ca/t/gt5bd.
- v. Mondor, 2014 ONCJ 135 (CanLII), accessed on 2017-09-01, http://canlii.ca/t/g6986.
- v. Nardi, 2012 BCPC 318 (CanLII), accessed on 2017-09-01, http://canlii.ca/t/fspw2.
R v. Dennis James Oland, 2015 NBQB 245 (CanLII), accessed on 2017-08-27, http://canlii.ca/t/gp3w3.
- v. Oler, 2014 ABPC 130 (CanLII), accessed on 2017-08-27, http://canlii.ca/t/g7n43.
- v. Starr, 2000 2 SCR 144, 2000 SCC 40 (CanLII), accessed on 2017-08-27, http://canlii.ca/t/525l.
R v Nde Soh, 2014 NBQB 20 (CanLII), accessed on 2017-08-27, http://canlii.ca/t/g50jc.
Rogers, Corinne. “Authenticity of Digital Records: A Survey of Professional Practice.” The Canadian Journal of Information and Library Science 39, no. 2 (2015): 97-113.
Rogers, Corinne, ed. Record Authenticity as a Measure of Trust: A View Across Records Professions, Sectors, and Legal Systems. Croatia: Department of Information and Communication Social Sciences, University of Zagreb (2015): 109-118.
Rogers, Corinne. “Virtual authenticity: authenticity of digital records from theory to practice.” PhD dissertation, University of British Columbia, 2015, accessed on 2017-08-20. https://open.library.ubc.ca/cIRcle/collections/ubctheses/24/items/1.0166169.
Rowe, Joy. “Are you ready to create digital records that last?” Preparing users to transfer records to a digital repository for permanent preservation.” Journal of the South African Society of Archivists 49 (2016): 41- 56, accessed on 2017-10-31, https://www.ajol.info/index.php/jsasa/article/view/138427.
Rowe, J. “Why Manage when you can Govern? Metadata in the Canadian Legal System.” Poster presented at annual meeting of ARMA Canada, Saskatoon, SK. (June 2013), accessed on 2017-10-31, https://open.library.ubc.ca/cIRcle/collections/graduateresearch/42591/items/1.0075797.
Rules of Civil Procedure, RRO (Ontario), Reg 194 — 1.04(1) (1990), accessed on 2017-10-31, http://canlii.ca/t/52zjn.
Sedona Canada. “The Sedona Canada Principles: 2008 CanLIIDocs 1.” The Sedona Conference Working Group 7 (WG7), Montreal, Jan 2008, fourth update (November 19, 2015), http://commentary.canlii.org/w/canlii/2008CanLIIDocs1en.
“The Sedona Principles, Third Edition: Best Practices, Recommendations Principles for Addressing Electronic Document Production: (2017 Public Comment Version).” THE SEDONA CONFERENCE, March 2017. https://thesedonaconference.org/publication/The%20Sedona%20Principle. .
The Sedona Conference Working Group. “THE SEDONA PRINCIPLES: Best Practices Recommendations Principles for Addressing Electronic Document Production.” June 2007.
Sheppard, A. F. “Records and Archives in Court.” Archivaria 19, Winter (1984): 196–203.
Shirley Williams, et al., Plaintiffs, v. Sprint/United Management Company, 464 F. Supp. 2d 1100 (D. Kan. 2006).
Swiss Reinsurance Company v. Camarin Limited, 2015 BCCA 466 (CanLII), accessed on 2017-08-27, http://canlii.ca/t/gm28z.
Thacker v Iamaw, District Lodge 140, 2016 BC LA 62600 (CanLII), accessed on 2017-08-27, http://canlii.ca/t/gtsph.
Underwood, Graham and Jonathon Penner, eds. Electronic Evidence in Canada. Toronto: Carswell, 2010. Williams v. Sprint/United Management Co., 464 F. Supp. 2d 1100 (D. Kan. 2006).
Winstanley v. Winstanley, 2017 BCCA 265 (CanLII), accessed on 2017-08-27, http://canlii.ca/t/h4v5d.
Works Cited
1An earlier version of this research was published as a poster presentation and benefitted from the feedback of conference attendees: Joy Rowe, “Why Manage when you can Govern? Metadata in the Canadian Legal System.” Poster presentation, ARMA Canada, Saskatoon, 2013. https://open.library.ubc.ca/cIRcle/collections/graduateresearch/42591/items/1.0075797.
2Luciana Duranti and Randy Preston, International research on permanent authentic records in electronic systems (InterPARES) 2: Experiential, interactive and dynamic records (CLEUP, 2008); Randy Preston, “InterPARES 2 Chain of Preservation (COP) Model Metadata” (Draft report). (2009).
3Donald Force, “Peruvian Guano to Electronic Records: Canadian E-Discovery and Records Professionals,” Archivaria 69(2010); Pat Franks and Nancy Kunde, “Why METADATA Matters,” Information Management Journal (Sept/Oct 2006); Julie Gable, “Examining metadata. Its role in e-discovery and the future of records managers,” Information Management Journal 43, no. 5 (2009); John Isaza, Metadata in Court. What RIM, Legal and IT Need to Know (Pittsburg, PA: ARMA International Education Foundation, 2010); Stephen Mason, “Proof of the Authenticity of a Document in Electronic Format Introduced as Evidence” (Pittsburg, PA: ARMA International Education Foundation, 2006); Stephen Mason, “Authentic Digital Records. Laying the Foundation for Evidence,” Information Management Journal 41, no. 5(2007).
4Luciana Duranti and Corinne Rogers. “Trust in digital records: An increasingly cloudy legal area,” Computer Law Security Review 28, no. 5 (2012); Luciana Duranti. “From digital diplomatics to digital records forensics.” Archivaria 68 (Fall 2009).
5As noted in Force, many sources on legal rulings freely reference both US and Canadian rulings (2010, 54). This paper adopts his stricter view of juridical context and strives to cite only Canadian legal sources, when possible.
6There is a technical distinction between the terms “electronic” and “digital.” Courts have largely chosen the terms “electronic record,” “ESI” (electronically stored information), and “electronic/computer evidence.” Other recent literature tends to use “digital”. In the context of this article, I use the terms ‘electronic record’ and ‘digital record’ interchangeably unless there is a reason to give a distinction. 7 A. F. Sheppard, “Records and Archives in Court.” Archivaria 19 (Winter 1984).
8Luciana Duranti, Corinne Rogers and Anthony Sheppard, “Electronic Records and the Law of Evidence in Canada: The Uniform Electronic Evidence Act Twelve Years Later.” Archivaria 70 (Fall2010):96.
9Duranti, Rogers, and Sheppard, “The Uniform Electronic Evidence Act Twelve Years Later,” 96.
10Robert J. Currie and Steve Coughlan, “Chapter 9, Canada – Electronic Evidence in Canada,” in Electronic Evidence (3rd ed), ed. Stephen Mason (LexisNexis, September 1, 2012), 288.
11Hilary Jenkinson, A manual of archive administration (New and Revised. London: Percy Lund, Humphries Co., 1937): 4.
12Michael Cook, The Management of Information from Archives (Aldershot, Hants, England; Brookfield, Vt., U.S.A: Gower, 1986): 7, 129.
13InterPARES 3 Project Terminology database. http://interpares.org/ip3/ip3_terminology_db.cfm?team=15.
14Currie and Coughlan, “Electronic Evidence in Canada,” 289. Canada Evidence Act, RSC 1985, c C-5, s.31.1 and provincial evidence statutes that have adopted the Uniform Electronic Evidence Act provisions and have similar authentication rules for electronic documents. 15 Corinne Rogers, “Record Authenticity as a Measure of Trust: A View across Records Professions, Sectors, and Legal Systems,” INFuture2015: e-Institutions – Openness, Accessibility, and Preservation (The Future of Information Sciences. Croatia: Department of Information and Communication Social Sciences, University of Zagreb, 2015): 111.
16InterPARES 3 Project Terminology database. http://interpares.org/ip3/ip3_terminology_db.cfm?team=15
17An interesting study exploring the Chain of Preservation (COP) metadata schema to identify the basic units of metadata that could be usefully contained in a file naming convention was done by Lara Mancuso, “Exploring the Potential of Naming Conventions as Metadata,” (independent study project paper, University of British Columbia, 2013).
18Rogers, “Record Authenticity”, 112.
19Rogers, “Record Authenticity”, 97.
20ARMA International, “Information Governance Maturity Model,” (2013).
21Examples of use of The Principles® in assessing organizational records maturity include Joy Rowe,” ‘Are you ready to create digital records that last?’ Preparing users to transfer records to a digital repository for permanent preservation,” Journal of the South African Society of Archivists 49 (2016): 48; Victoria Lemieux, Brianna Gormly, and Lyse Rowledge, “Meeting Big Data challenges with visual analytics: The role of records management,” Records Management Journal 24, no. 2 (2014): 135-136.
25Pat Franks and Nancy Kunde, “Why METADATA Matters,” Information Management Journal (Sept/Oct 2006): 57.
26Stephen Mason, Proof of the Authenticity of a Document in Electronic Format Introduced as Evidence (Pittsburg, PA: ARMA International Education Foundation, 2006): 6-7.
27Sedona Canada, The Sedona Canada Principles. The Sedona Conference Working Group 7 (WG7), (Montreal, 2008, fourth update 2015): 8.
28Ibid., 8.
30Rules of Civil Procedure may relate to how witnesses are examined, how affidavits may be admitted, or how long before a trial another party must be notified to produce documentary evidence, Halsbury’s laws of Canada: Civil Procedure (Markham, Ont: LexisNexis. Halsbury 2012): 289.
31“ABA-Lawyers Can Search Metadata,” Information Management Journal (May/June 2007): 11. Shirley Williams, et al., Plaintiffs, v. Sprint/United Management Company, 464 F. Supp. 2d 1100 (D. Kan. 2006). This ruling followed changes in the US Federal Rules of Civil Procedures, which were amended in 2006 to address issues of electronically stored information, or ESI.
32Hummingbird v. Mustafa, [2007] 39610 ONSC.
33The Sedona Conference Working Group, THE SEDONA PRINCIPLES: Best Practices Recommendations and Principles for Addressing Electronic Document Production, (2007): 4.
34Ibid., 60.
35These same distinctions are maintained in the March 2017 Public Comment version of the proposed updated to the Sedona Principles. THE SEDONA CONFERENCE, The Sedona Principles, Third Edition: Best Practices, Recommendations and Principles for Addressing Electronic Document Production (2017 Public Comment Version).
36John Isaza, Metadata in Court. What RIM, Legal and IT Need to Know (Pittsburg, PA: ARMA International Education Foundation, 2010). 37 This three-way distinction of metadata is frequently attributed to US Sedona Principles. In fact, although the Aguilar case did cite Sedona Principles for some of the discussion of metadata, the terms “substantive, embedded, and system” come from US District Court for the District of Maryland, Suggested Protocol Rules for Discovery of Electronically Stored Information, 25-28. This correction of sourcing is important because a key Canadian legal text, Underwood and Penner, takes up the three-way distinction of metadata and this text is cited in several Canadian cases. The Maryland protocol that Aguilar cited has now been replaced by Principles for the Discovery of ESI in Civil Cases, and it uses the two-part distinction found in US Sedona Principles: system metadata and application metadata. Sedona Commentary on Ethics Metadata notes that the court in Aguilar collapsed some of the seven distinct types of metadata defined in the Sedona Glossary into the three categories of substantive, system-based and embedded (2013, p. 6, footnote 7).
38Julie Gable, “Examining metadata. Its role in e-discovery and the future of records managers,” Information Management Journal 43, no. 5 (2009): 30.
39Isaza, Metadata in Court, 8.
404.8% of the 293 respondents had given testimony in a court proceeding, while 10.2% had been involved in a legal hold or e-discovery. Corinne Rogers, “Virtual authenticity: authenticity of digital records from theory to practice” (PhD diss., University of British Columbia, 2015), 115, https://open.library.ubc.ca/cIRcle/collections/ubctheses/24/items/1.0166169.
41Currie and Coughlan, “Electronic Evidence in Canada,” 284.
42GL Gall, FP Eliadis, F Allard, The Canadian legal system, 5th Ed (Scarborough, Ont: Carswell, 2004), 40.
43Halsbury’s laws of Canada: Civil Procedure (Markham, Ont: LexisNexis, 2012), 289.
44Gall, Eliadis, and Allard, The Canadian legal system, 41.
45Halsbury’s laws of Canada: Civil Procedure, 285.
46Ibid., 286-287.
47Halsbury’s laws of Canada: Civil Procedure, 289.
48Currie and Coughlan, “Electronic Evidence in Canada”, 284.
49Ibid., 285. British Columbia, Newfoundland, and Northwest Territories have not yet adopted a form of the coordinated electronic evidence legislation.
50Duranti, Rogers and Sheppard, “The Uniform Electronic Evidence Act Twelve Years Later,” 104-105.
51Currie and Coughlan, “Electronic Evidence in Canada”, 285. 52 Underwood and Penner, Electronic Evidence in Canada, 12-1. 53 Ibid., 13-7.
54Ibid., 13-1 to 13-2.
55RJ Delisle, Evidence: principles and problems, 10th ed (Toronto: Carswell, 2010), 411.
56Currie and Coughlan, “Electronic Evidence in Canada”, 295.
57Underwood and Penner, Electronic Evidence in Canada, 14-1.
58Saturley v. CIBC World Markets Inc [2012] NSSC 226 at para. 28.
59Currie and Coughlan, “Electronic Evidence in Canada”, 284-285.
60Ibid., 285.
61Underwood and Penner, “Electronic Evidence in Canada”, 11-3, 11-7.
62Canada Evidence Act, RSC 1985, c C-5 (1985), s.31.2 (1).
63Ibid., s.31.3-b.
64Canada Evidence Act, RSC 1985, c C-5, s.31.3-c.
65Ibid., s.31.6(1).
66Ibid., s.31.5.
67Ibid., s.31.2(2).
68Underwood and Penner, “Electronic Evidence in Canada”, 12-1.
69Ibid., 13-8 to 13-9.
70Ibid., 12-1.
71Ibid., 12-13.
72Ibid., 12-2.
73Ibid., 12-5.
74Currie and Coughlan, “Electronic Evidence in Canada”, 291. 75 Underwood and Penner, Electronic Evidence in Canada, 12-8. 76 Saturley v. World CIBC Markets [2012] NSSC 226.
77Ibid., 16.
78Underwood and Penner, Electronic Evidence in Canada, 12-9.
79Ibid.,12-9.
80Currie and Coughlan, “Electronic Evidence in Canada”, 291. In the Saturley ruling data that was automatically generated by software to register investment trading transactions was determined to be real evidence. It was not a ‘document’ and not therefore subject to the “presumption of reliability designed to satisfy the best evidence rule”.
81Underwood and Penner, Electronic Evidence in Canada, 12-15.
82Ibid., 12-10.
83Ibid., 12-13 to 12-14.
84Ibid., 12-16. This three-way distinction was initially proposed in the US Aguilar ruling, drawing on US Sedona Principles and Maryland Protocol for electronic discovery purposes, and has been extended by Underwood and Penner to apply to ESI for evidence purposes.
85Ibid., 12-17 to 12-18.
86Ibid., 12-19.
87Ibid., 12-19.
88Ibid., 12-20.
89According to the Canlii.org database, 288 cases have mentioned “electronic evidence”, “computer evidence” or “metadata” in the case rulings since 1979. Ninety-one percent of the cases have been within the last ten years (search conducted on August 30th, 2017).
90McGarry v. Co-operators Life Insurance Co, [2011] BCCA 214.
91RS II Productions Inc. v. B.C. Trade Development Corp [2000] BCCA 674 at para. 25 cites numerous rulings and quotes R. v. Starr, [2000] 2 SCR 144, 2000 SCC 40 “the Court has advanced towards what it calls a “principled approach” to the hearsay rule and instructed courts to consider necessity and reliability in each particular case, as opposed to applying “ossified rules” of evidence.”
92McGarry, BCCA 214 at para. 67.
93Canada Evidence Act, R.S.C., c. C-5, s.42 (1985).
94Manitoba Evidence Act, R.S.M., c. E150 (1987); Saskatchewan Evidence Act, R.S.S., c. S-16, ss. 55-56 (1978); Alberta Evidence Act, R.S.A. c. A-18, s. 41 (1980); and Ontario Evidence Act, R.S.O., c. E-23, s. 34.1 (1990).
95McGarry, BCCA 214 at para. 73-77.
96Ibid., at 81.
97Cases citing McGarry: Swiss Reinsurance Company v. Camarin Limited, [2015] BCCA 466 at para. 67 Winstanley v. Winstanley, [2017] BCCA 265 at para. 64.
98Scott Owen’s SSHIRC-funded study on the best evidence rule highlighted the rule as an ineffectual mechanism of admissibility in “Best Evidence in Canada: An Analysis of Issues and Case Law” (project paper, University of British Columbia, 2014).
99Currie and Coughlan, “Electronic Evidence in Canada.” 288.
100Ibid., 285.
101BL. v. Saskatchewan (Social Services) [2012] SKCA 38 at para. 41.
102R. v. Hamdan, [2017] BCSC 676 at para. 82.
103Alan W Bryant, Sidney N. Lederman, Michelle K. Fuerst, and John Sopinka, The Law of Evidence in Canada (3d) ed. (Markham: LexisNexis, 2009), 1225.
104David M. Paciocco, recent appointee as Justice on Court of Appeal for Ontario, is “considered on the Canada’s foremost experts on the laws of evidence”. The Supreme Court of Canada has referenced work he authored or contributed to in 60 cases. A primary contribution is the promotion of principled and workable legal rules, including the principled exception to the hearsay rule. “Backgrounder: The Honourable Justice David M. Paciocco’s Questionnaire,” Department of Justice, Government of Canada, last modified on April 07, 2017, https://www.canada.ca/en/department-justice/news/2017/04/the_honourable_justicedavidmpacioccosquestionnaire.html.
105D.M. Paciocco, “Proof and progress: Coping with the law of evidence in a technological age,” Canadian Journal of Law and Technology 11 no.2 (2015): 226-227.
106Paciocco, “Proof and progress”, 197.
107R. v.C.L., [2017] ONSC 3583 at para. 21.
108R. v.Hirsch, [2017] SKCA 14 at para.13.
109R. v.Hirsch, [2017] SKCA 14 at para. 21.
110R. v. Hirsch, [2017] SKCA 14 at para. 18.
11131.5 For the purpose of determining under any rule of law whether an electronic document is admissible, evidence may be presented in respect of any standard, procedure, usage or practice concerning the manner in which electronic documents are to be recorded or stored, having regard to the type of business, enterprise or endeavor that used, recorded or stored the electronic document and the nature and purpose of the electronic document. Canada Evidence Act, R.S.C., c. C-5, s.31.5 (1985).
112R. v. Oler, [2014] ABPC 130.
113The recently revised CAN/CGSB-72.34-2017 Electronic records as documentary evidence is now freely available at http://publications.gc.ca/collections/collection_2017/ongc-cgsb/P29-072-034-2017-eng.pdf.
114R. v.Oler, [2014] ABPC 130 at para. 31.
115Desgagne v. Yuen et al [2006] BCSC 955.
116Desgagne v. Yuen et al [2006] BCSC 955 at para. 29.
117Ibid., at para 29.
118Ibid., 35, 45.
119Animal Welfare International Inc. v. W3 International Media Ltd., [2013] BCSC 2193.
120Ibid., 53.
121Ibid., 53.
122Animal Welfare International Inc. v. W3 International Media Ltd., [2014] BCSC 1839 at para.340.
123Ibid., 340.
124Ibid., 346-350.
125Saturley v. CIBC World Markets Inc, [2012] NSSC 226 at para.22.
126R. v. Bernard, [2016] NSSC 358 at para.45-58.
127ARMA International, “Information Governance Maturity Model,” (2013).
Privacy-Driven RIM in Ontario’s Universities
by Carolyn Heald, Queen’s University
In a recent issue of this journal, Shan Jin, Records Analyst at Queen’s University in Kingston, Ontario, published her findings on records management practices in Canadian universities based on interviews with twenty-one institutions, the majority of which were located in Ontario. At the time of her initial research in 2014, none of the six Ontario universities with fewer than 10,000 students had a formal records management program; only one of the four universities in the 10-20,000 student category, and three of the five universities in the 20-30,000 student category had a program; all five of the universities with over 30,000 students had a formal records management program1.
“From early days,” Jin wrote, “university archival programs often assumed responsibility for records management2.” However, one key observation from her research is that newer records management programs—those established within the last decade or so—are no longer being situated within archival programs which tend to be considered academic or scholarly units, often part of the library. Rather, they are being placed squarely within the senior administration, typically within a unit dealing with university governance3. Jin pointed out that privacy legislation has had an impact on the establishment of records management programs in Ontario’s universities: four out of the nine programs were launched after universities became subject to the provincial Freedom of Information and Protection of Privacy Act (FIPPA) in June 2006. One of those programs was launched after FIPPA was amended in 2014 to include specific recordkeeping requirements4. Since Jin completed her study, even more universities in Ontario have established records management programs as a direct result of those recordkeeping amendments.
Privacy is a key driver of records management within Ontario’s universities, FIPPA in particular, but also health care privacy legislation, anti-spam legislation, and more recently, the impending impact of international privacy regulations. In my view, the pairing of the two functions is a good move: it brings a broader perspective to the management of active university information and records, offers wider capacity to navigate the challenges universities face in the increasingly digital world, and positions these information professionals to be key players in their universities’ information governance.
FIPPA and the Recordkeeping Amendments
Much of what is driving records management in Ontario’s universities are the 2014 amendments to FIPPA—the so- called recordkeeping amendments—that took effect on January 1, 20165. These new clauses were added as a direct result of the gas plants scandal that plagued former premier Dalton McGuinty’s government and which resulted in a criminal conviction for his Chief of Staff for illegally wiping government computers6.
McGuinty had decided to cancel construction of two natural gas power plants, resulting in much higher cancellation fees than he had led the public to believe. The issue was subject to review by a standing committee of the legislature, and in conducting its review, the committee requested emails from political staff in the office of the responsible Minister of Energy. The office did not comply, and it was learned that political staff made a habit of routinely deleting emails. A complaint was made to Ontario’s Information and Privacy Commissioner who launched an investigation where it was learned further that the Secretary of Cabinet had been approached by the Premier’s Chief of Staff seeking information on how to permanently delete emails and other electronic documents.
In her damning 2013 report, former Commissioner Ann Cavoukian remarked that she had “trouble accepting that this practice [i.e., routinely deleting emails] was simply part of a benign attempt to efficiently manage one’s email accounts7.” Rather, she said, “I became very concerned with the apparent lack of responsibility and accountability for records management practices within the offices of senior political leaders in this province.”8 She made several recommendations to the Ministry of Government Services and the Premier’s Office for reviewing records retention schedules, developing policies, and ensuring staff training. She also made some key recommendations for amending FIPPA9.
These amendments are framed in terms of a duty to preserve records in order to ensure a right of access. Records managers often deal with the opposite problem—over-retention—and seek to establish retention schedules so that organizations can get rid of records. Nevertheless, a perceptive records manager will recognize the amendments for what they truly are: a requirement to have in place a well- functioning records management program.
For universities, this is revolutionary. For the first time, Ontario’s universities have a legislated mandate to implement records management. Universities have never been subject to Ontario’s archives and recordkeeping legislation which applies to most other institutions covered by FIPPA (namely government ministries and a number of agencies). Now all FIPPA institutions, including government ministries, agencies, universities, hospitals, as well as municipalities and local municipal bodies covered under the Municipal Freedom of Information and Protection of Privacy Act, are required by law to follow established records retention policies and rules.
This is not to say that universities have not been subject to recordkeeping rules in the past. Like any corporate body, they must abide by laws pertaining to employment, tax, occupational health and safety, and any number of other statutes, some of which incorporate rules on the creation and keeping of records10. But to have a clear directive that universities must have in place recordkeeping measures is truly radical and those without such a program have been stepping up to ensure compliance.
The IPC’s awareness of, and engagement with, records management has been evolving ever since October 2005 when former Commissioner Cavoukian was alerted by a Toronto Star reporter that recycled patient records from a local ultrasound and x-ray clinic were swirling around downtown Toronto streets, being used as a prop for a movie shoot about 9/11. The Commissioner’s investigation and report, her first under the newly implemented Personal Health Information Protection Act, concluded amongst other things, that recycling personal health information did not constitute secure disposal as required by the Act11. This unfortunate incident first made the IPC connect the dots between information management and privacy, an understanding that has only continued to grow12.
Beyond FIPPA
FIPPA has been the key driver towards the increase in the number of records management programs in Ontario’s universities. However, it is not the only piece of privacy legislation that is having an impact on recordkeeping. Many universities are also subject to health care privacy to one degree or another.
Ontario’s Personal Health Information Protection Act (PHIPA) was enacted in 2004 to address the handling of personal health information by health information custodians. Custodians are entities that provide health care services, and in the context of a university, that could be a student health clinic, mental health counselling, athletic injury clinic, or any number of health care services offered to the broader community such as psychological assessments or physiotherapy.
PHIPA’s privacy requirements are much more stringent given the sensitive nature of the information involved, and these records must be managed properly, and retained and disposed of in accordance with appropriate records retention requirements13. Although PHIPA has not been amended to include a specific recordkeeping mandate, the IPC nevertheless has been emphasizing the importance of good records management with respect to patient records14.
Another statute with significant recordkeeping requirements is Canada’s Anti-Spam Legislation, or CASL15. This legislation came into effect on July 1, 2014 with the intention of enhancing trust in Canada’s electronic commerce activities primarily by reducing the sending of email SPAM, or commercial electronic messages (CEMs) as defined in the Act. While not a privacy statute per se, CASL is similar to privacy in that it requires an organization or individual to obtain consent—express or implied—before sending a CEM. Individuals can withdraw their consent and accordingly all CEMs must have an unsubscribe mechanism. Penalties for non-compliance can be as high as $10 million and the federal government has proven that it is not averse to levying significant fines16.
Most universities in Canada consider activities falling within their core educational mandate to be non- commercial, even if money passes hands (such as a student paying for tuition). This approach has not been tested, but the government’s investigations to date have focused on private sector bodies that clearly have a commercial basis, rather than public sector bodies. Nevertheless, the legislation includes a private right of action allowing individuals to sue senders of CEMs for alleged CASL violations. This private right of action was supposed to have taken effect on July 1, 2017, but due to numerous concerns expressed about its implications, it has been postponed indefinitely pending further study17
CASL brings with it the requirement to create and keep detailed records primarily for the purpose of tracking consents so that senders of CEMs can defend themselves in the event they are challenged with non-compliance. In 2016, the government issued an enforcement advisory notice on how to keep records of consent and the types of records expected to be kept, including “all evidence of express and implied consent (e.g. audio recordings, copies of signed consent forms, completed electronic forms) from consumers who agree to receive CEMs, documented methods through which consent was collected, policies and procedures regarding CASL compliance, and all unsubscribe requests and resulting actions18.” The House of Commons Standing Committee on Industry, Trade and Technology undertook a statutory review of CASL in 2017 and made a number of recommendations seeking clarification of many of its provisions. Ontario’s universities are amongst numerous organizations looking forward to the outcome.
Looming on the horizon is the European Union’s General Data Protection Regulation (GDPR) which will take effect on May 25, 201819. GDPR will replace the EU’s 1995 Data Protection Directive which has become out of date given the rapid technological changes experienced over the past twenty years. The GDPR applies to EU residents and significantly expands their personal privacy rights. Not every university in Ontario will be affected by the GDPR to the same extent, but likely most universities will have to grapple with its implications since it applies to entities that (a) have operations or employees in the EU, (b) offer goods or services to EU residents, or (c) monitor behaviour of EU residents, such as through online tracking. As with CASL, managing consents will be paramount because penalties for non- compliance can be as much as €20 million or 4% of global turnover. As with other privacy legislation, the proper management of personal information will be critical in order to ensure it is collected, used, disclosed, retained and disposed of in compliance with the legislation.
The privacy environment in which universities operate is becoming increasingly complex, prompting a concomitant records management imperative. Privacy depends on good information-handling, a fact being articulated with conviction by more and more privacy regulators.
Privacy and Records Management Challenges in Universities
Universities are multifaceted and unwieldy organizations. Each university is an autonomous body with its own culture but all universities have in common a few key factors: they have a diverse and largely uncontrolled clientele and workforce; they foster innovation, risk-taking, and pushing boundaries; and they are open and collaborative by design. The interplay of these three factors, especially within an increasingly digital world, makes establishing rules and limits around the handling of records and information a challenging task.
One indicator of this wild frontier is the range of devices that connect to a university’s IT infrastructure. While many organizations are only now developing their BYOD (bring your own device) policies, universities have been dealing with a BYOD environment for years. Far from studying the issue first, assessing the risks and developing policies and procedures to ensure a smooth implementation, universities have been running to keep up with the new devices that arrive on their campuses every term. Students are not restricted in what type of laptop, tablet, cellphone, or indeed any device, they bring to class and university IT departments have typically focused on modifying and upgrading their infrastructure to support this constantly changing environment. Faculty members, too, need to access the Internet and their own electronic files from many locations, on campus and off, frequently in far- flung locales, and they, too, want to use devices of their own choosing.
Not all devices are secure, and it can be difficult conveying the message that devices should be encrypted at the very least, and not used for sensitive personal information. When it comes to records management, it can be a struggle to ensure that university records are filed in a proper recordkeeping system, and that devices are wiped clean of official records when they are no longer being used by employees. If a device is stolen or lost, individuals are usually more concerned with the cost of replacement and the loss of their intellectual property rather than having caused a privacy breach or losing official records.
When it comes to innovation, universities are expected to challenge the status quo, explore new ideas, interrogate conventional wisdom, and tackle unpopular ideas. In many workplaces, the Internet can be locked down to prevent access to undesirable websites (or surfing on staff time), but no such restrictions are imposed or tolerated in a university environment. A researcher may be studying the pornography industry, or religious intolerance in the Middle East, or fake news in the United States, or any number of controversial topics. Unrestricted access to the Internet and other resources is required. New thinking and risk-taking are the order of the day, bringing the potential for connecting to unvetted and insecure external resources.
In a similar vein, universities pride themselves on being collegial, collaborative and open. Faculty members and often students as well need to engage with the national and international community of scholars, and this can happen through technology or through in-person engagements in a multitude of uncontrolled environments. The need to share documents and resources often results in the use of cloud-based tools that may or may not be properly vetted for privacy and security.
Indeed the rapid adoption of cloud computing tools has been occurring in Ontario’s universities for several years. Not only are such tools essential for research collaboration, but they are also being used for a myriad of classroom purposes to engage students and allow greater collaboration. From large- scale learning management systems to classroom clickers, online textbooks to exam-writing websites, students are constantly being directed to third-party sites and tools. Technology-enhanced learning will only continue as we expect to see the curriculum enabled through artificial intelligence, the Internet of Things, social media, gamification and virtual reality20.
But cloud tools are not just invading the classroom; they are being used for numerous other kinds of student services as well as administrative functions. There are apps and websites for pre-ordering meals in the cafeteria, reserving tickets to campus events, registering children in summer camps, fostering alumni engagement, managing student conduct, and on and on. There is simply no end to the ingenuity of software and app developers.
The upshot of all of this cloud engagement is that universities have placed their trust in commercial third parties to handle significant amounts of personal information and other confidential and sensitive data, and they continue to do so as the cloud computing environment evolves and transforms around them.
FIPPA requires universities to ensure that personal information is not collected, used, disclosed, retained or disposed of improperly and so it is imperative that universities review cloud engagements and negotiate appropriate terms before such tools are used.
In my opinion, the most baleful effect of cloud tools is only just beginning to be recognized. Within the last few years, the business model for cloud service providers has shifted: where in the past, vendors made money from selling their products, now they seek to monetize the personal information they collect from users. It is a common refrain that when it comes to cloud, you are the product, meaning that what companies really want is their users’ personal information so that it can be shared with advertising networks where companies pay to place their ads that will pop up on users’ browsers or in their social network feeds21.
Gathering people’s personal information relies on tracking users as they browse the Internet and set up accounts on various digital platforms. The companies providing the services and apps are not doing anything illegal since they describe their information practices in their terms of service and privacy policies. But such policies are lengthy and convoluted, and vendors rely on users to consent to them without reading them22. Vendors also engage in definitional gymnastics to confuse those few users who bother to read the terms:
Terms of service or end-user licensing agreements are designed to be convoluted legal documents many pages long to discourage user understanding. The interconnected nature of technology means that many devices, services, or websites transfer data with third-party companies, all of which have their own user agreements23.
Companies will claim that they are not collecting “personal information” because the data they track is not name-identified; however, collecting information about devices and browsing history for the purposes of tracking and sending people targeted advertisement based on predictive analytics clearly demonstrates that they can identify individual users, even if they do not have a name. Privacy regulators believe such data collection constitutes the collection of personal information. The federal privacy commissioner has expressed this view in a policy position on online behavioural advertising (OBA):
Taking a broad, contextual view of the definition of personal information, the OPC [Office of the Privacy Commissioner] will generally consider information collected for the purpose of OBA to be personal information, given: the fact that the purpose behind collecting information is to create profiles of individuals that in turn permit the serving of targeted ads; the powerful means available for gathering and analyzing disparate bits of data and the serious possibility of identifying affected individuals; and the potentially highly personalized nature of the resulting advertising24.
The UK’s Information Commissioner has also provided guidance on the new General Data Protection Regulation and points out that the definition of “personal data” has expanded:
The GDPR applies to ‘personal data’ meaning any information relating to an identifiable person who can be directly or indirectly identified in particular by reference to an identifier.
This definition provides for a wide range of personal identifiers to constitute personal data, including name, identification number, location data or online identifier, reflecting changes in technology and the way organisations collect information about people25.
The privacy invasiveness and power imbalance inherent in this “surveillance capitalism”26 is concerning at a societal level; however, at the more mundane level of the university privacy officer, such activity constitutes secondary use under FIPPA which requires consent. A university could simply inform its users that their personal information is being collected by the third party for this secondary purpose and ask them to agree if they wish to set up an account or download an app. However, if use of the service or app is mandatory, then consent is not appropriate and the only recourse, apart from not engaging with the vendor, is to negotiate an agreement to ensure there is no secondary use of personal information.
The privacy challenges of using cloud tools in the classroom have been gaining attention as school boards and educational authorities recognize the dangers inherent in tracking. Ontario’s Information and Privacy Commissioner has issued guidance to school boards at the K-12 level27. Similar guidance for the US higher education sector has been issued by EDUCAUSE, an association for IT professionals within the post-secondary sector28.
Cloud computing also brings with it traditional records management challenges. When engaging a cloud vendor, frequently there is little if any consideration given to appropriate recordkeeping practices. Is the vendor expected to retain the university’s official record on its servers? Will the vendor assist the university in implementing the authorized records retention schedules? Can the university get a copy of the record in a readable format when the engagement is terminated? Will the vendor permanently delete its copy of the record and any backups? These are issues that are often neglected when negotiating a contract with a vendor, yet it is important to consider them because at some point, the engagement will end.
Most Ontario universities have outsourced their email and office environment to either Microsoft or Google. Initially, it was student email that was outsourced, but it did not take long for university administrations to decide that the whole office environment could be handled by third-party service providers more efficiently. This decision was made, for the most part, without thought to records management. These tools may have abundant functionality for creating, sharing, and collaborating on documents, but they have little records management functionality as the records management profession would understand it29.
Opportunities for Information Governance
The privacy and records management challenges facing universities today highlight the value in having records management and privacy closely involved. Records management and privacy are complementary functions, each informing the other. Where a records management unit is situated is not important in itself; the success of a program depends more on the individuals involved—their grasp of the challenges, their ability to communicate those challenges and their ability to cooperate with others—than on where the program resides within the organizational hierarchy. Jin is absolutely correct in saying that “records managers must capitalize on the advantages and overcome the disadvantages of [a university’s] organizational structure in order to seek ways to improve records management services. It is important to align efforts from the records management program with other strategic partners such as archives, Information Technology (IT) security, legal department, privacy and compliance office, etc30.”
And yet, being co-located with the privacy function may open up more opportunities for records managers to participate at the information governance (IG) table, in alliance with other, better-understood functions, such as IT security. The inclusion of privacy professionals in the IG conversation is a given due to legislation and the well-understood risks inherent in a privacy breach, but the records manager is often forgotten because the negative consequences of financial and operational inefficiencies resulting from unmanaged information are not obvious until a crisis occurs. However, the records management perspective is broader than privacy, and more complementary to the IT security professional’s perspective than one might imagine.
The IT security professional focuses on the trilogy of CIA: confidentiality, integrity, and availability. The privacy professional’s domain is confidentiality of personal information and availability of records for the purposes of fulfilling an access to information request. The records manager’s focus encompasses a wider understanding of availability and confidentiality, and significantly adds integrity31. For the records manager, integrity is one of the characteristics of an authoritative record as defined in the ISO Records Management standard32. The integrity of an electronic records system is the Canadian proof standard for submitting an electronic record as legal evidence in a court of law33. The records manager can speak to CIA more broadly than the privacy professional.
The pairing of records management with privacy may be a fairly recent phenomenon for Ontario’s universities; however, Christine Ardern rightly points out that privacy and records management have both been incorporated within the broader information governance field at least since the advent of electronic records whose volume of personal information and ease of access highlighted the potential privacy risk. This realization led to the publication in 1980 of the OECD Guidelines on the Protection of Privacy and Trans-border Flows of Personal Data and drove many countries to develop their own data protection legislation34. In her article on the evolution of IG, Ardern cites a number of definitions of information governance, but I like the definition provided from the Sedona Conference Journal:
(Information Governance) means an organization’s coordinated, inter-disciplinary approach to satisfying information compliance requirements and managing information risks while optimizing information value35.
The focus on a coordinated and interdisciplinary approach calls out the reality that managing an organization’s information asset is not the responsibility of one kind of information professional with one perspective. FIPPA’s recordkeeping requirements have been the catalyst for many of Ontario’s universities to adopt a records management/privacy nexus. Perhaps the momentum can continue to drive these information professionals, in cooperation with their archives and IT colleagues, to adopt a more encompassing and interdisciplinary information governance framework.
1Shan Jin, “Records Management in Canadian Universities: The Present and the Future,” Sagesse (Winter 2017), p. 2, http://armacanada.org/images/Sagesse_Winter_2017/3._RM_in_Canadian_Universities-
The_Present Future.pdf (accessed 27 June 2017). Jin’s study of 21 universities represents approximately 20% of universities in Canada.
2Ibid., p. 1.
3Ibid., p. 4.
4Ibid., pp. 10-11.
5Information and Privacy Commissioner of Ontario, FIPPA and MFIPPA: Bill 8 – The Recordkeeping Amendments (December 2015).
6Karen Howlett, “McGuinty’s former aide Livingston found guilty of destroying documents about gas plant cancellations,” Globe and Mail (19 January 2018), https://www.theglobeandmail.com/news/national/mcguinty- aide-found-guilty-of-destroying-documents-in-gas-plant-trial/article37669957/ (accessed 20 January 2018).
7Information and Privacy Commissioner of Ontario, Deleting Accountability: Records Management Practices of Political Staff (June 5, 2013), p. 2.
8Ibid., p. 1. Numerous media stories have been published about the court case against David Livingston, the Premier’s Chief of Staff, and the deputy Chief of Staff, Laura Miller. For a story with a highly salient records management focus, see Karen Howlett, “Top McGuinty aide wasn’t trained in record keeping, court hears,” Globe and Mail (24 October 2017), https://www.theglobeandmail.com/news/national/top-mcguinty-aide-wasnt-trained-in-record-keeping-court-hears/article36710297/ (accessed 3 January 2018).
9IPC, Deleting Accountability, pp. 2-3. Note that the recommendation to create a duty to document key decisions was not included in the legislative amendments.
10See, for example, the Employment Standards Act, the Occupational Health and Safety Act, and the federal Income Tax Act. Even FIPPA itself has a requirement to retain personal information for a minimum of one year. 11 Information and Privacy Commissioner of Ontario, PHIPA Order HO-001 (October 2005).
12IPC staff regularly make presentations about privacy and records and information management; see presentations on www.ipc.on.ca. As well, the IPC issued a guidance document entitled Improving Access and Privacy with Records and Information Management (November 2016).
13In Ontario, patient information is generally retained for ten years, or ten years after the individual reaches his or her eighteenth birthday. This standard retention period is reflected in the various acts governing the regulated health professionals.
14See the IPC website (www.ipc.on.ca) for various presentations and guidance documents.
15The legislation has become known as CASL because its full title is An Act to promote the efficiency and adaptability of the Canadian economy by regulating certain activities that discourage reliance on electronic means of carrying out commercial activities, and to amend the Canadian Radio-television and Telecommunications Commission Act, the Competition Act, the Personal Information Protection and Electronic Documents Act and the Telecommunications Act. In December 2017, the House of Commons Standing Committee on Industry, Science and Technology published its report concluding its statutory review of the legislation. The first of the report’s 13 recommendations is to adopt a short title for the Act, the suggestion being the Electronic Commerce Protection Act (ECPA). See Canada, House of Commons, Canada’s Anti-Spam Legislation: Clarifications Are in Order, Report of the Standing Committee on Industry, Science and Technology (December 2017).
16Findings have included: Porter Airlines, $150,000; Rogers Media, $200,000; PlentyofFish, $48,000. See https://crtc.gc.ca/eng/com500/ut2015.htm (accessed 3 January 2018). A 2015 decision against CompuFinder with a penalty of $1.1 million was later reduced to $200,000; see http://www.slaw.ca/2017/11/15/crtc-compufinder- decision-lowers-casl-spam-penalty/ (accessed 3 January 2018).
17See the Government’s announcement: https://www.canada.ca/en/innovation-science-economic- development/news/2017/06/government_of_canadasuspendslawsuitprovisioninanti-spamlegislati.html (accessed 3 January 2018).
18The enforcement advisory was issued on July 27, 2016: https://www.canada.ca/en/radio-television- telecommunications/news/2016/07/enforcement-advisory-notice-for-businesses-and-individuals-on-how-to-keep- records-of-consent.html (accessed 3 January 2018).
19See https://www.eugdpr.org/ (accessed 3 January 2018).
20There are numerous articles about disruptive technologies in higher education. See, for example, David Wheeler, “Technology and the Imminent Disruption of Higher Education: Is Fear the Path to the Dark Side?” Academica Forum (13 January 2016), https://forum.academica.ca/forum/technology-and-the-imminent- disruption-of-higher-education-is-fear-the-path-to-the-dark-side (accessed 4 January 2018). See also Leigh M. and Thomas Goldrick, “The top 5 disruptive technologies in higher ed,” eCampus News (June 5, 2017), https://www.ecampusnews.com/disruptions-and-innovations/disruptive-technologies-higher-ed/
21There is no shortage of articles available on the Internet explaining how ad networks work to those who wish to take advantage of them. Two interesting books with a decidedly cautionary perspective are Tim Wu, The Attention Merchants: The Epic Scramble to Get Inside Our Heads (New York: Alfred A. Knopf, 2016) and Bob Hoffman, BadMen: How Advertising Went from a Minor Annoyance to a Major Menace (Bob Hoffman, 2017).
22Alex Hern, “I read all the small print on the Internet and it made me want to die,” The Guardian (15 June 2015), https://www.theguardian.com/technology/2015/jun/15/i-read-all-the-small-print-on-the-internet (accessed 26 January 2018).
23“Don’t Buy What Surveillance Capitalism is Selling,” Smith Business Insight (15 November 2017), https://smith.queensu.ca/insight/articles/don_t_buy_what_surveillance_capitalism_is_selling (accessed 26
24Office of the Privacy Commissioner, “Policy Position on Online Behavioural Advertising” (December 2015), https://www.priv.gc.ca/en/privacy-topics/advertising-and-marketing/behaviouraltargeted- advertising/bg_ba_1206/ (accessed 4 January 2018).
25United Kingdom, Information Commissioner’s Office, https://ico.org.uk/for-organisations/guide-to-the-general- data-protection-regulation-gdpr/key-definitions/ (accessed 4 January 2018).
26The term was coined by Shoshana Zuboff; see https://en.wikipedia.org/wiki/Surveillance_capitalism (accessed 26 January 2018).
27See Information and Privacy Commissioner, Online Educational Services: What Educators Need to Know (November 2016) https://www.ipc.on.ca/wp-content/uploads/2016/11/online-educational-services.pdf (accessed 26 January 2018).
28See information on learning data privacy principles on the EDUCAUSE website: https://library.educause.edu/resources/2016/12/learning-data-privacy-principles-and-recommended-practices- webinar (accessed 26 January 2018).
29For commentary on the records management challenges inherent in the Office 365 environment, see “How Office 365 challenges traditional records management practices” (27 September 2016), https://andrewwarland.wordpress.com/2016/09/27/how-office-365-challenges-traditional-records-management- practices/ (accessed 22 September 2017) and “Top 5 Office 365 Problems for Information Managers” (11 September 2017), http://cannonspark.ca/blog.html (accessed 22 September 2017).
30Jin, p. 5.
31For an interesting look at the complementarity perspectives of privacy and information security see Ken Mortensen, “CPO to CISO: Four Steps for Privacy Professionals to Get Security Savvy,” CPO Magazine (30 October 2017), https://www.cpomagazine.com/2017/10/30/cpo-ciso-four-steps-privacy-professionals-get-security-savvy/ (accessed 20 December 2017). The article does not speak to records management.
32International Organization for Standardization, 15489-1:2016, Records Management (ISO, 2016).
33Canadian General Standards Board, CAN/CGSB-72.34-2017, Electronic Records as Documentary Evidence (CGSB, March 2017).
34Christine Ardern, “From Records Management to Information Governance: A Look Back at The Evolution,”
Sagesse (Spring, 2016), p. 12, https://www.armacanada.org/index.php/canadian-rim/spring-2016-publication
(accessed 27 June 2017).
35Ibid., p. 4
